Warning
This guide is incomplete
This guide is intended to provide information and guidance on how to setup a private Minecraft server using WireGuard. Every effort has been made to ensure that the information presented in this guide is as accurate as possible. Despite this, it is possible that some information in this guide may be inaccurate. I encourage people reading this guide to consult relevant online sources to enhance the guides accuracy and maybe learn more along the way. I have linked the sources used in this guide in the footnotes section and suggest going there for further reading. <3
- How To Setup A Private Minecraft Server Using PiVPN and WireGuard
In this guide, I will cover how to create a private Minecraft server using PiVPN & WireGuard. This guide is meant for private Minecraft servers, using WireGuard to host a public Minecraft server is not recommended as there are better methods of doing that. If you are looking to host a public Minecraft server, consider hosting with a VPS or Paid Provider. This guide will cover everything from WireGuard basics, configuring the the operating system, deploying the minecraft server and more.
I have also uploaded a video on my YouTube channel in case you want to follow along in video format. Keep in mind that throughout the video you will have to refer back to specific parts of the guide so that you will have the most up to date information. The video also uses the recommended items and topology. For cases not covered in the video don't worry as they shouldn't differ too much from the video.
I utilized PiVPN and WireGuard when I was developing StorageSolution. StorageSolution is a full-stack application I developed that allowed the computers from CC: Tweaked to display all the items in my storage system in a nice and presentable manner using Python Textualize. I created a backend API to distribute the contents of my storage system to the frontend where the end-user could then see the items in table format. Examples online showed backend solutions using ngrok that exposed the backend to the internet. This isn't something that I really wanted since anyone could establish a websocket connection with the server, therefore to limit the server's exposure I setup a WireGuard VPN in a configuration where both the Minecraft and backend server was located within the VPN (Virtual Private Network).
Ever since then, WireGuard has been my preferred way to host my private Minecraft servers with peers. I also wanted to document the process since there are limited resources out there to help since I've been setting up these servers for a while.
I wrote this guide with beginners in mind as I suspect that most people reading this guide might be new to networking or just want a way to play with friends. This guide is the equivalent on the -vv argument flag as this guide contains much information I could possibly cram.
There is a lot of filler mixed into this guide, therefore make sure to lookout for headers that have a tailing ~ symbol.
- What is WireGuard?
- Here I explain what WireGuard is, how it works, and whether it is suitable for the task of hosting a Minecraft server. I will then try and address any concerns you might have alongside listing alternative methods you can use instead.
- Choosing Server Topology
- Setting Up The Operating System
- SSHing into your server
- Setting Up WireGuard
- Creating Key Pairs
- Distributing Key Pairs
- Creating the Minecraft Server
- DNS Configuration
- Changes
Below I have listed the prerequisite items needed in order to complete this guide. Though, the items stated is just a recommendation. There are many different ways you can configure the WireGuard server to suit your needs. Feel free to look at the Choosing Server Topology section of the guide where I go more in depth in different ways you can configure the WireGuard Server.
- Recommended
- Micro SD Card / USB Drive
- Internet Connection
- Debian Based Computer (PiVPN)
- Computer (Minecraft Server)
- Computer (To play on)
- Minimum
- Internet Connection
- Computer (PiVPN, Minecraft Server, To play on)
I know some of you might want to get straight in and skip sections in order to get this setup straight away, that's great! but, I do recommend reading the Why WireGuard? section if you are thinking of doing that as you might find that WireGuard might not be for you. If you are determined to get started good luck on your journey! :)
Before explaining what WireGuard is I think it is important to understand what a VPN generally is and the basic operations of it.
A virtual private network (VPN) is a mechanism for creating a secure connection between a computing device and a computer network, or between two networks, using an insecure communication medium such as the public Internet.1
A WAN (Wide Area Network) is a network that extends over multiple geographical regions2. An institution could deploy a WAN completely separate from the public internet, so that data sent from the hosts and servers are sent in a secure and confidential manner, this would be referred to as a private network3. Private Networks can be quite costly in where the institution would have to purchase, install and maintain their own physical network infrastructure3. Therefore, nowadays, institutions deploy VPN's to solve the same problem. VPN use the existing public internet rather than an separate independent network. To provide the confidentiality that the separate network provided, the traffic is encrypted before it is sent over the public internet3 .
WireGuard is a relatively new open source VPN solution that uses state-of-the-art cryptography. It aims to be faster and more simpler to learn than other alternatives. On the WireGuard website it states the following 5 principles4:
- Simple & Easy-to-use
- Cryptographically Sound
- Minimal Attack Surface
- High Performance
- Well Defined & Thoroughly Considered
It was specifically created for the Linux Kernel by Jason A. Donenfeld in 2015 though has spread to other platforms as well such as IOS, Android, Mac and Windows.
(See https://www.ckn.io/blog/2017/11/14/wireguard-vpn-typical-setup/ this image was also taken from the Unofficial WireGuard Documentation)
WireGuard is quite performant compared to other VPN solutions as seen above. The results are similar to the findings on the WireGuard official website. Though both of these benchmarks seem to be outdated. Though in a recent finding (2023) found here WireGuard still outperforms OpenVPN. This speed is what we want when running a minecraft server.
According to All About Cookies WireGuard is considered to be "one of the safest, most secure VPN protocol options available today."5 It also has the added benefit that it is used by popular VPN software such as NordVPN, SurfShark, CyberGhost, and MullVAD VPN.
WireGuard does have a security flaw out of the box though. When using other services such as OpenVPN you are assigned a different IP address each time you connect, though with WireGuard your IP address remains static and unchanging. "This is faster, but it means the VPN server must keep logs of your real IP address and connection timestamps."6 It should be mentioned though that the VPN providers using WireGuard circumvented this issue by modifying WireGuard with their own systems to get around this flaw6. In this guide we won't be covering that since that is likely way out of my expertise.
TODO...
TODO...
WireGuard has many advantages in the VPN space. Though should you create a WireGuard VPN for the sole purpose of hosting a Minecraft server?
The only scenario in which a VPN would help you is if you ran a VPN gateway in your network and have the Minecraft server accessible only to those with access to your VPN. The problem is, that this is way more difficult to set up, and even more difficult to set up in a secure manner. Just forwarding a port to your Minecraft server is way less likely to get you into any troubles.
https://www.ckn.io/blog/2017/11/14/wireguard-vpn-typical-setup/
This is exactly what we are doing to do in this guide. Port forwarding to your Minecraft server to the internet isn't that insecure. As long as you have a whitelist you should be fine from unexpected visitors. If you also want to go the extra step you can also disable SLP which is what was used to detect active minecraft servers in LiveOverFlow's video where he scanned the internet for open Minecraft servers.
There are very rare cases where a VPN would is valid option to use as seen in my StorageSolution example. But I think whether you want to use WireGuard to host a Minecraft server would come down to personal preference, whether you want to learn some networking skills or don't trust the Minecraft servers.
This section will list some alternatives I have found. I will first describe the functions of the alternative before delving into the similarities and differences between the alternative and our chosen method.
| Alternatives | Explanation |
|---|---|
| Port Forwarding | Port Forwarding is an application of the NAT (Network Address Translation) that reroutes communications from one pair of IP and port number combination to another through the network gateway 7. |
| OpenVPN | TODO... |
| IPSec | TODO... |
| Hamachi | TODO... |
| TwinGate | TODO... |
| Radmin VPN | TODO... |
| ZeroTier One | TODO... |
| Ngrok | TODO... |
| ESSENTIALS Mod | Essentials is a quality of life mod that allows you to host singleplayer worlds to peers. It also adds some other things that brighten the social aspects of Minecraft like cosmetics and a wardrobe feature. The Mod is available for both Forge and Fabric. As for the difference between the Essentials Mod and WireGuard it is much more simpler to setup and takes out a lot of the hassle of creating a connection. As for how essentials achieves this is unknown to me. |
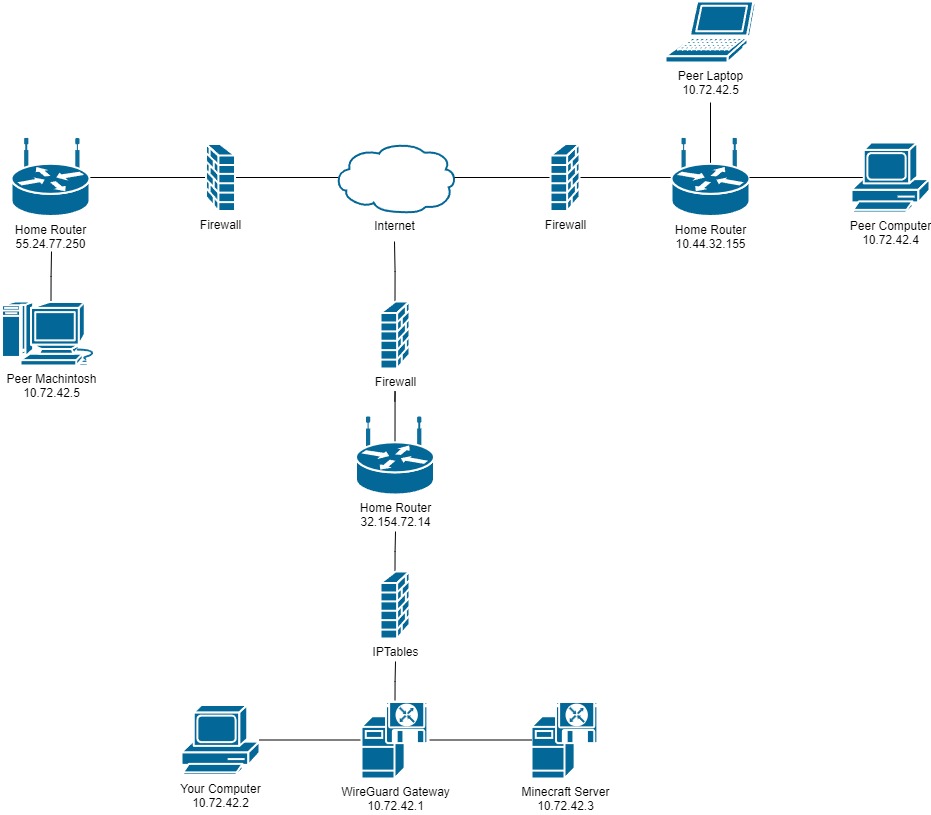
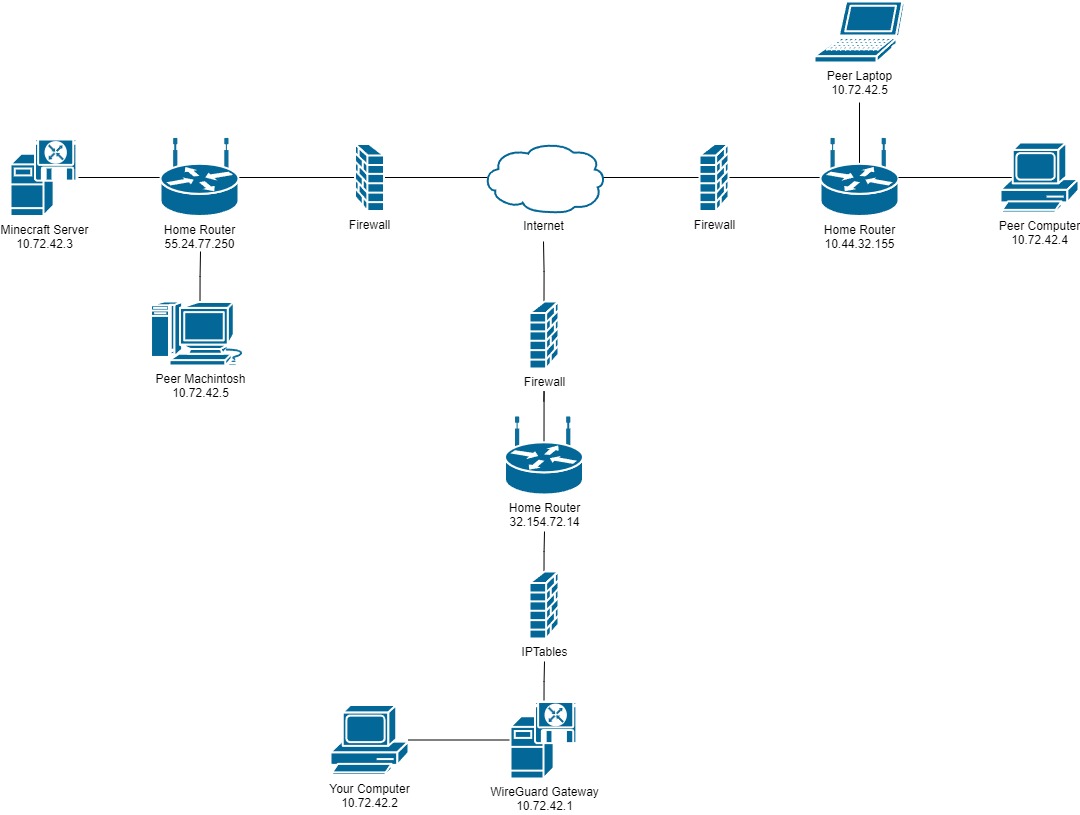
Each server topology requires different sets of prerequisites. You can choose any server topology depending on what you have available to you. For simplicity, this guide will be using the recommended configuration. This isn't a big issue, but if something in the guide deviates from your desired topology I will notify you. Below is a list of the server topologies supported by this guide:
- Recommended Configuration
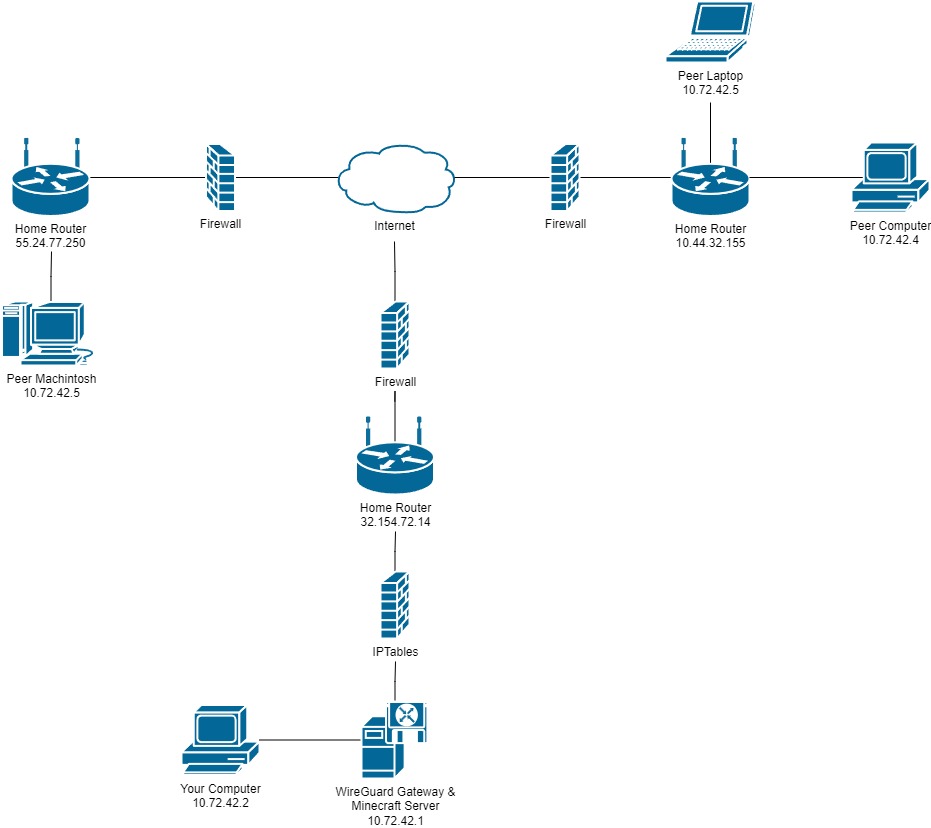
- Combined Gateway and Server Configuration
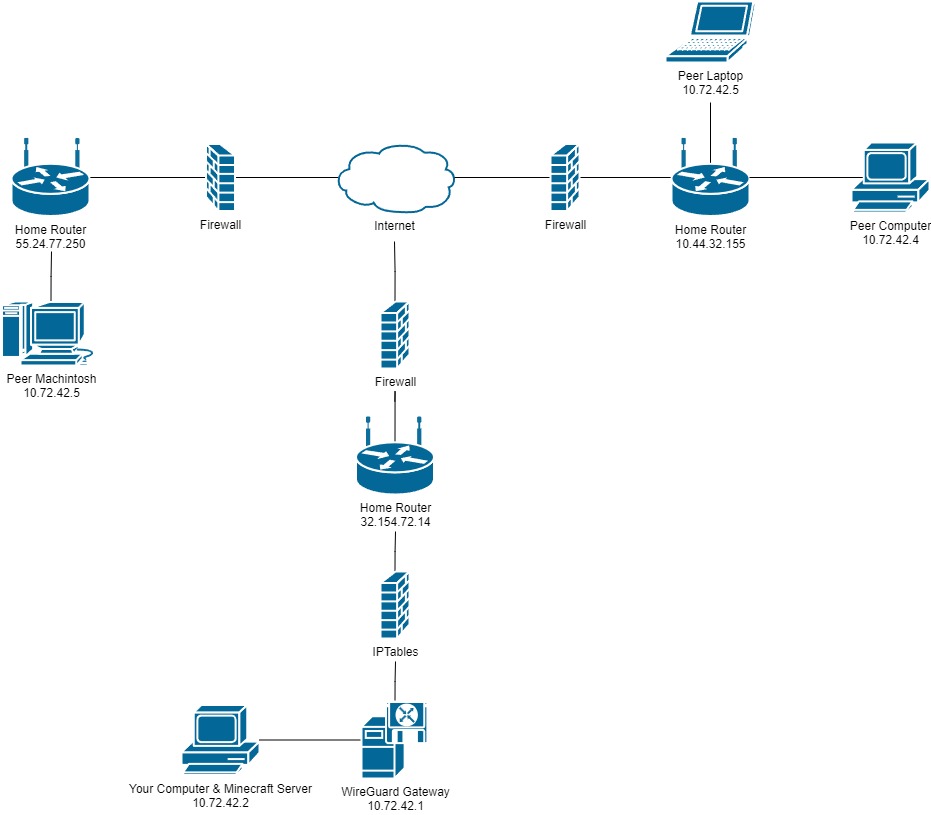
- Computer Host Configuration
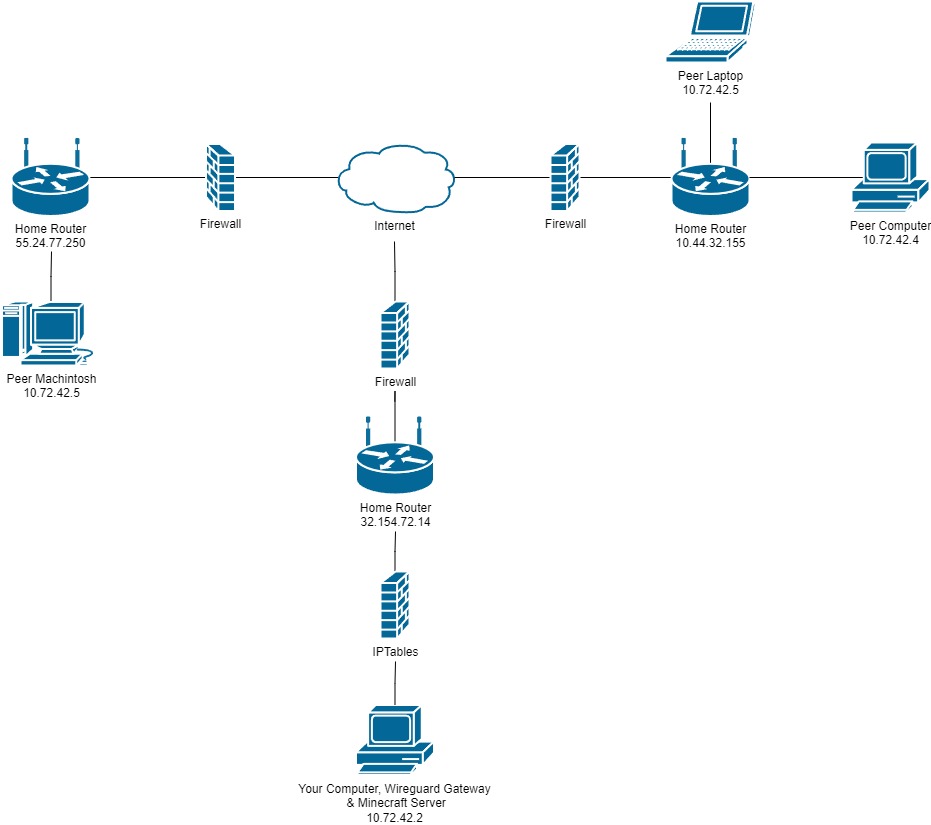
- All In One Configuration
- Separated Network Configuration
This is the recommended configuration where we have the load distributed against three different computers. You are less likely to run into any performance issues with this setup.
Prerequisites
- Internet Connection
- Debian Based Computer (PiVPN)
- Computer (Minecraft Server)
- Computer (To play on)
In this configuration the WireGuard Gateway and Minecraft server is combined. If the two servers are running on a Raspberry Pi I would advise going with a Minecraft server option that is lightweight like PaperMC or Forge with performance mods. WireGuard isn't very resource intensive from when I benchmarked it, so majority of the load will most likely be the Minecraft server.
Prerequisites
- Internet Connection
- Debian Based Computer (PiVPN & Minecraft Server)
- Computer (To play on)
Assuming you shut off your computer at night. This is a good alternative if you are not planning to have the Minecraft server running 24/7. If you have a beefy computer that can handle running the game and server this isn't a bad option.
Another cool note with this setup, you don't actually have to setup the server. Instead you can just host through LAN instead and it should work exactly the same but with less steps!
Prerequisites
- Internet Connection
- Debian Based Computer (PiVPN)
- Computer (To play on & Minecraft Server)
Prerequisites
- Internet Connection
- Computer (PiVPN, Minecraft server and Personal Computer)
Note: The computer can be any operating system, though if it isn't debian based you will not be able to take the easy route of using PiVPN and it's features and will instead have to install WireGuard manually.
This topology is more food for thought than anything, if you cannot host the Minecraft server on your local network then you are more than welcome to have that server located elsewhere.
- Internet Connection
- Debian Based Computer (PiVPN)
- Computer (Minecraft Server)
- Computer (To play on)
You want to download and install the Raspberry Pi Imager for your desired operating system. The imager is available for windows, mac, and linux. You'll also want a MicroSD readily available to use so that you can flash it onto there.
After you have installed the Raspberry Pi Imager launch the software and insert the MicroSD card into your computer.
In the imager, click on "Choose OS". Choose Raspberry Pi OS Lite. We want to choose the lite version as the desktop environment is heavy and can drain resources that we want allocated to the Minecraft/WireGuard Gateway. Depending on what Raspberry Pi you have, you'll chose either between the 32 or 64 bit variant. Since the 64 bit variant supports the Raspberry Pi 4, I will choose that.
From there we will be choosing the storage device we want to flash to. Be careful which one you choose as it will override all of the contents located on that drive.
We can customize the image by clicking the cog icon on the bottom left. Set the hostname to anything that you want, personally named mine KambrookRiceExpress5CupRiceCooker as it is a sneaky name that fits into all my other devices such as BagOfDoritos and SecretLabsGamingChair. A very important configuration step as well is configuring SSH. Password authentication will do just fine for our purposes and set a strong username and password. MAKE THE PASSWORD AND USERNAME UNIQUE AND STRONG. I cannot stress enough that SSH can be used for remote attacks so make it strong and unique.
Configure WirelessLAN to point to your router, this will make it so that you are able to connect ot the internet when you boot up your Pi. I would only really recommend you do this if you don't have an ethernet cable as you can set it through SSH using sudo raspi-config.
Configure locale settings if you have too and click then click save.
Double check that you have selected the right drive write to the drive. Wait for it to finish and then eject it from your computer.
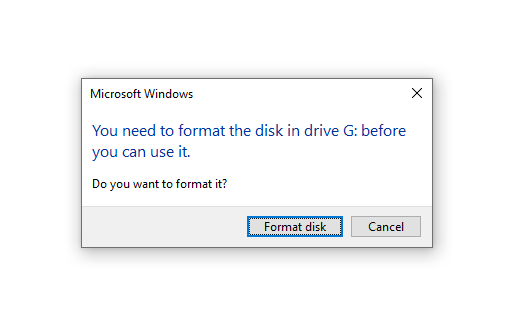
If you get an error message like below, DO NOT format it. If you have accidentally reformated the drive, just redo the steps mentioned above and you should be just fine.
for the guide this is the information that we have allocated to the Raspberry Pi
TODO...
You will first need to find the local IP address of the device that you want to SSH into. I found mine by logging into my router/default gateway at 192.168.0.1 and finding my Raspberry Pi's IP address there. To SSH into your Raspberry PI fill in the following and paste in into your terminal where xxx.xxx.xxx.xxx is the IP address of your Pi and username is the username you assigned to your Raspberry Pi, this isn't to be confused with the host name.
ssh username@xxx.xxx.xxx.xxx
It will state that the authenticity of the host cannot be established and whether you are sure you want to proceed. type yes
It will then prompt you for a password. Don't get confused when it doesn't seem to be typing anything, it's just a precautionary it takes to make sure nobody is peaking. Just type it in as you usually do and then press enter.
TADA! you are now remotely accessing your Raspberry/Debian server.
SSH into the intended computer you want to host the gateway on. The install instructions might change in future so make sure to check the PiVPN for download instructions. But as of now, this is the command to install PiVPN:
curl -L https://install.pivpn.io | bash
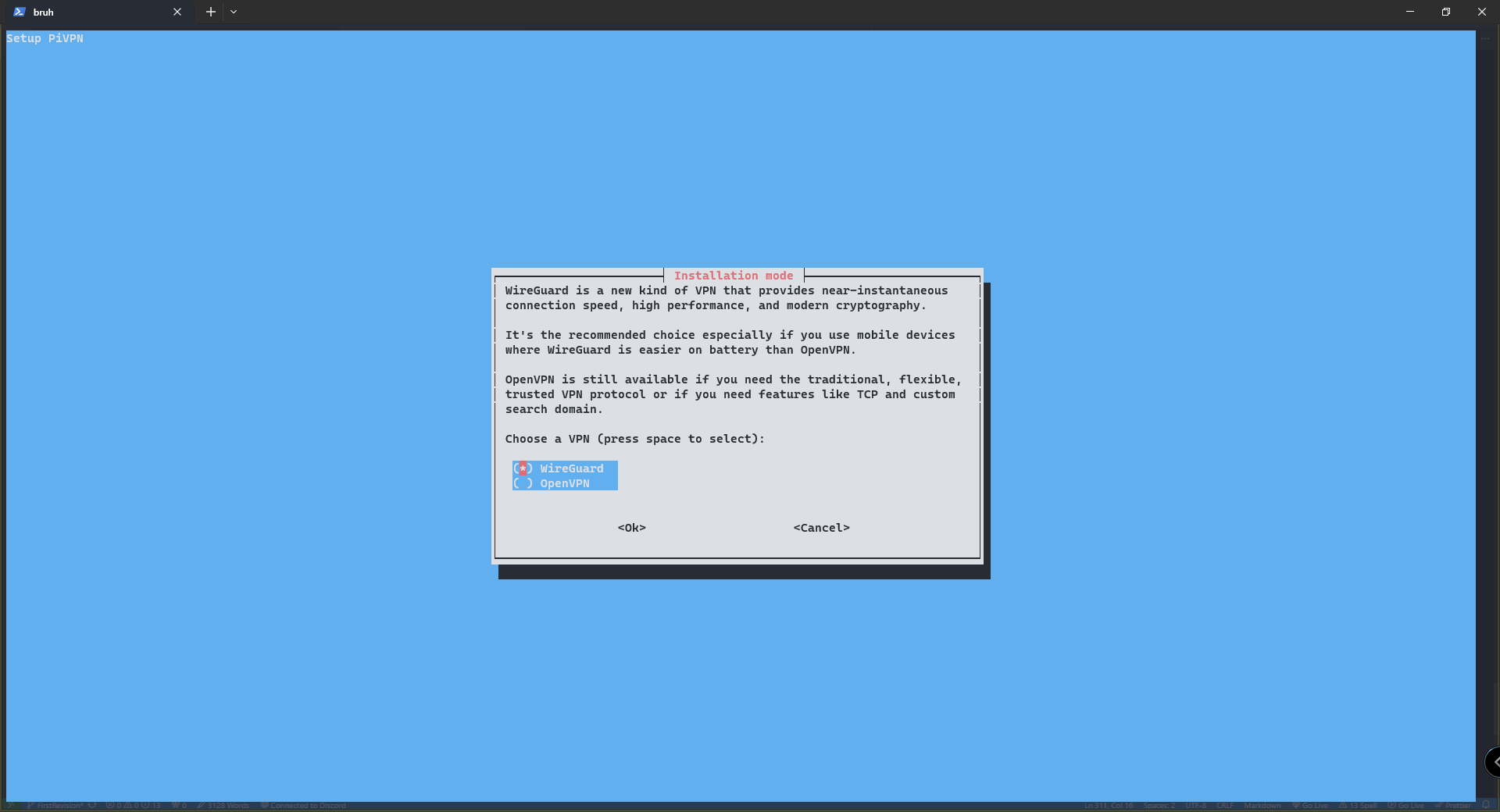
from there you will be presented with a setup wizard. Read through the instructions as is and click ok, if there is any yes or no stuff it will be listed here.
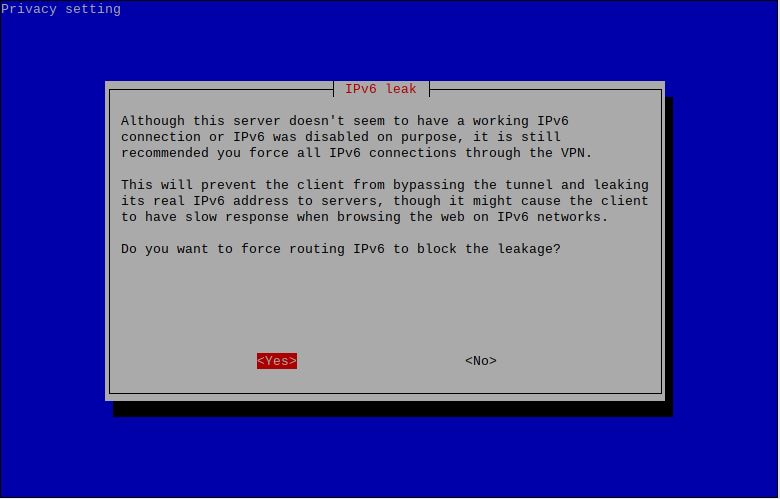
This is a result of me using VirtualBox to virtualize my Raspberry Pi during testing. If you get this message select yes.
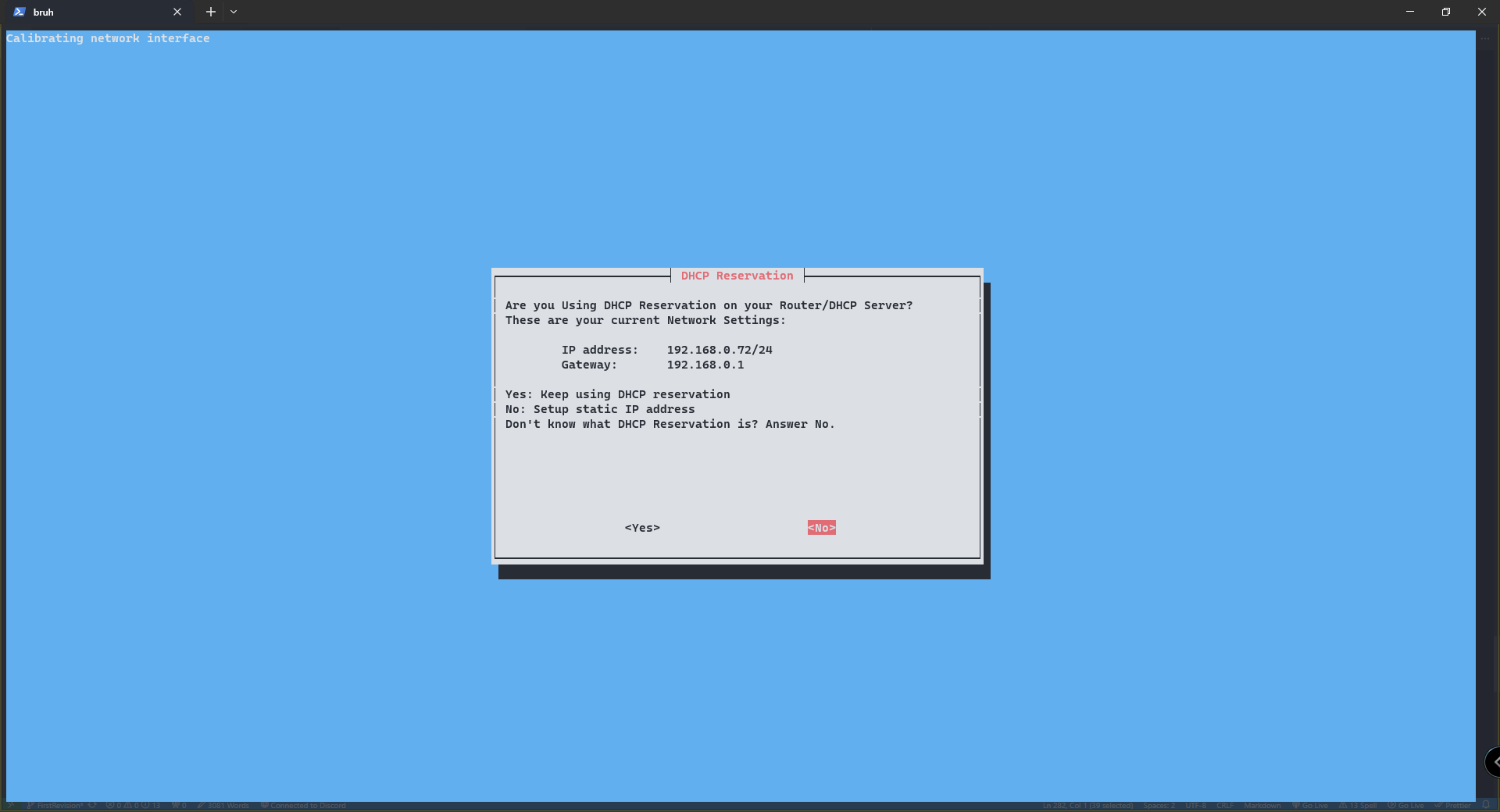
We will answer no for the sake of keeping this guide more simple. Though if you know how to reserve a IP address feel free to select yes.
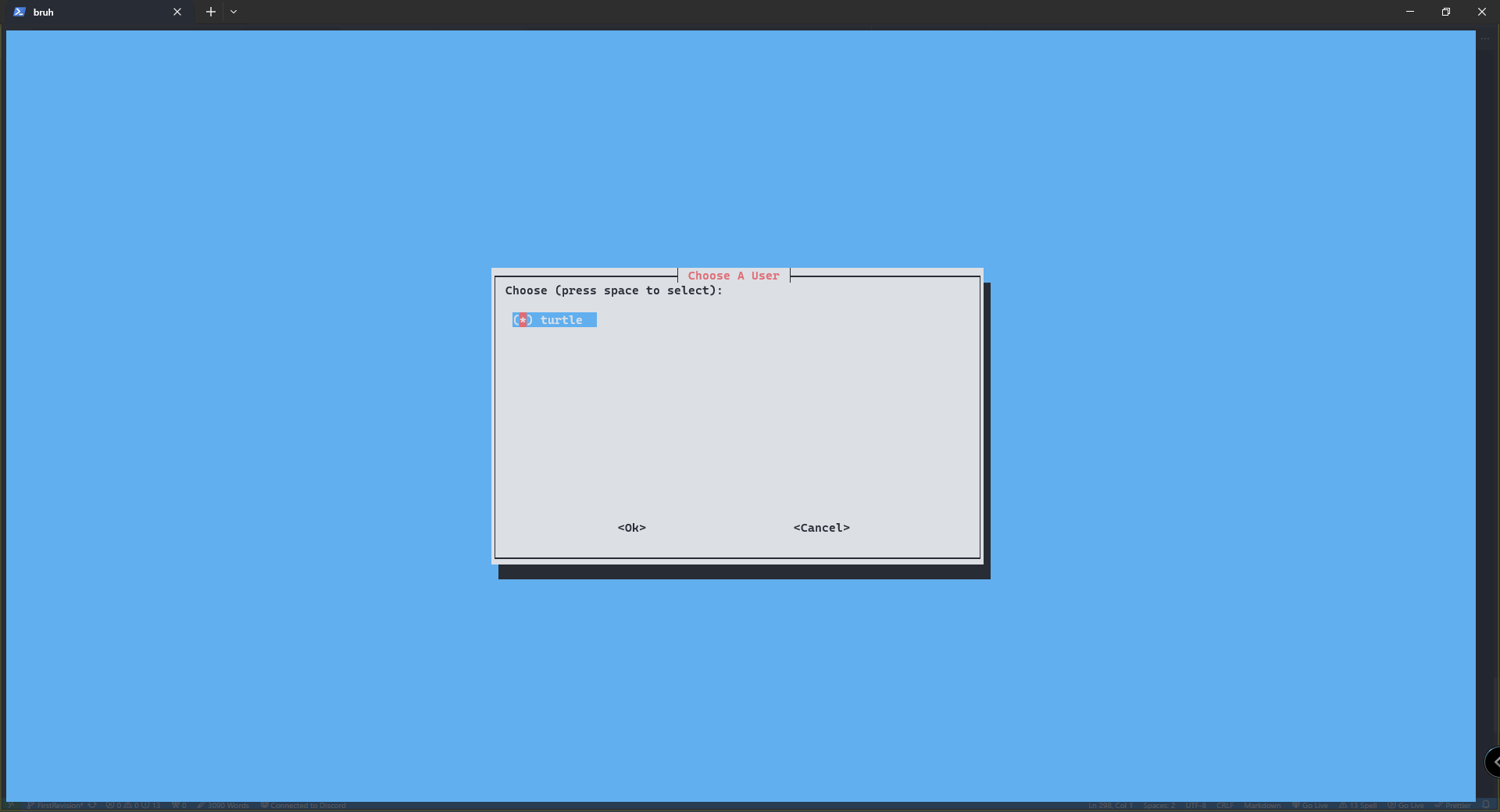 for me there is only one user. You could also create a user specifically for the purpose of holding your configurations, which is a good practice but isn't necessary.
for me there is only one user. You could also create a user specifically for the purpose of holding your configurations, which is a good practice but isn't necessary.
[UPDATE THE GUIDE TO INCLUDE SEPARATE USERS.]
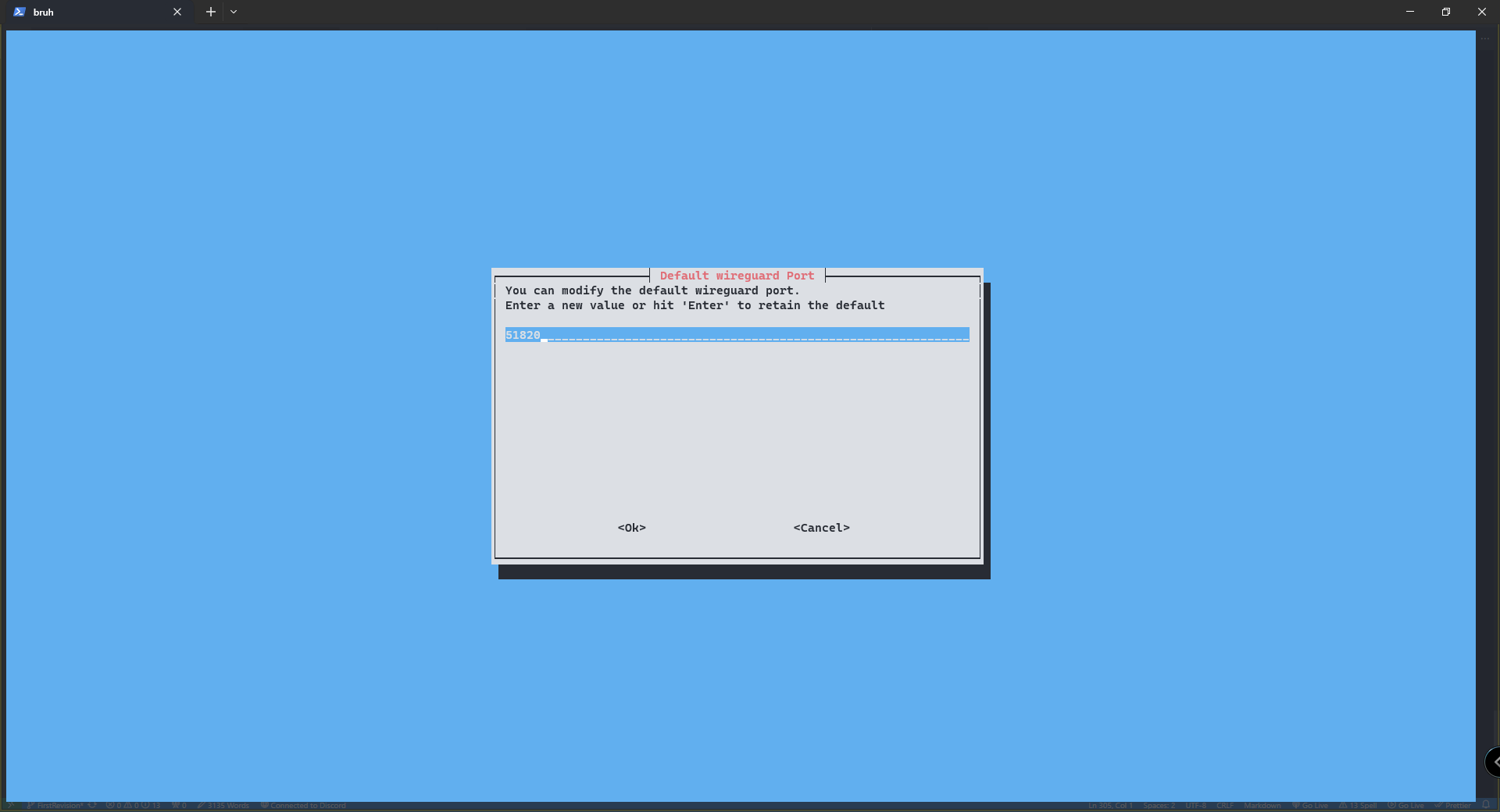 here we are assigning a port number to the server. You can actually put really any number here from 0 to 65,535 but keep in mind some IP addresses are reserved so be careful. I like going with the default port number
here we are assigning a port number to the server. You can actually put really any number here from 0 to 65,535 but keep in mind some IP addresses are reserved so be careful. I like going with the default port number 51820.
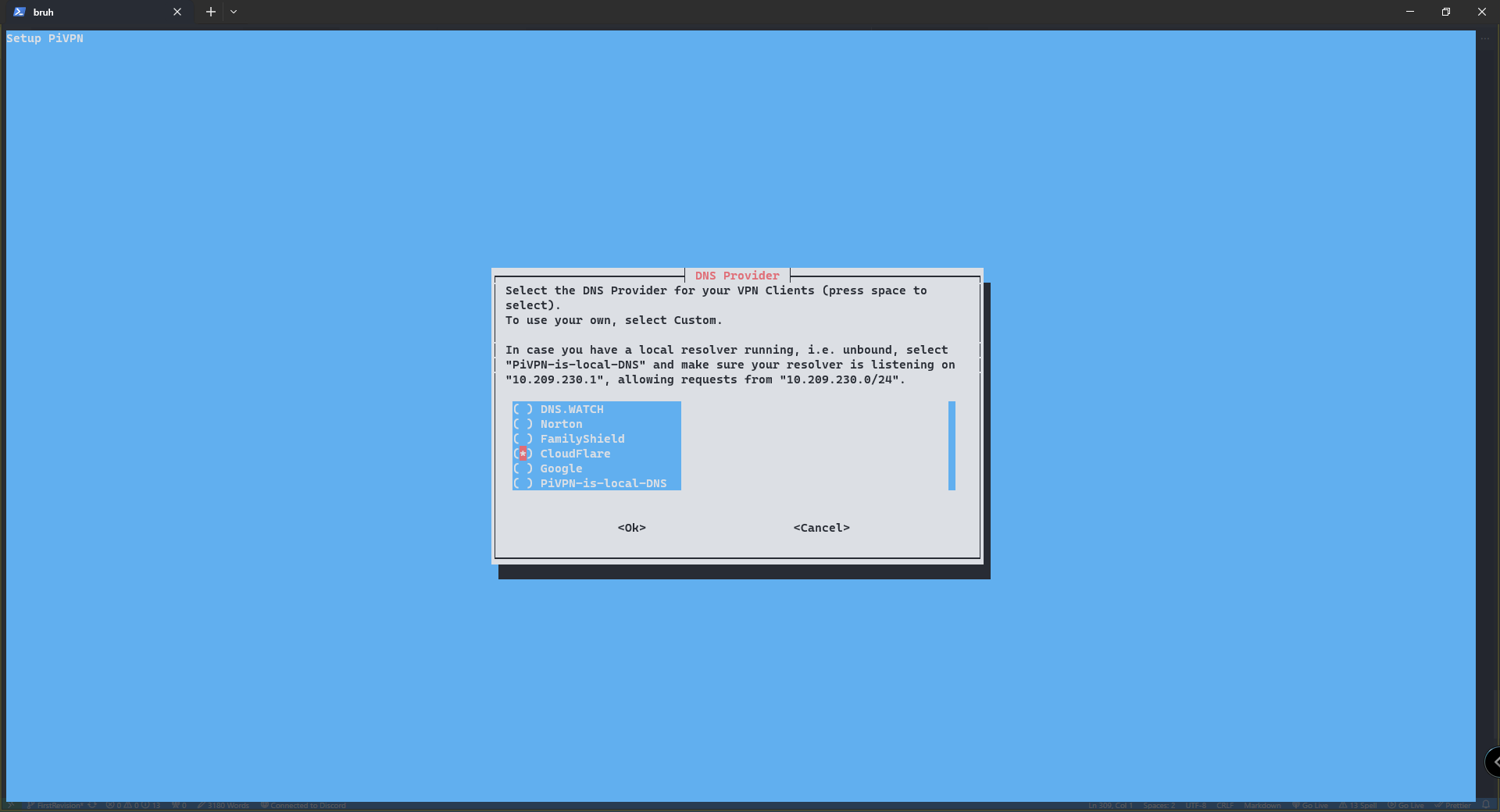 Here we are choosing our DNS provider. I like going with Cloudflare, but you can choose any one of these and you'll be fine. Apart from
Here we are choosing our DNS provider. I like going with Cloudflare, but you can choose any one of these and you'll be fine. Apart from PiVPN-is-local-DNS and custom, you might run issues.
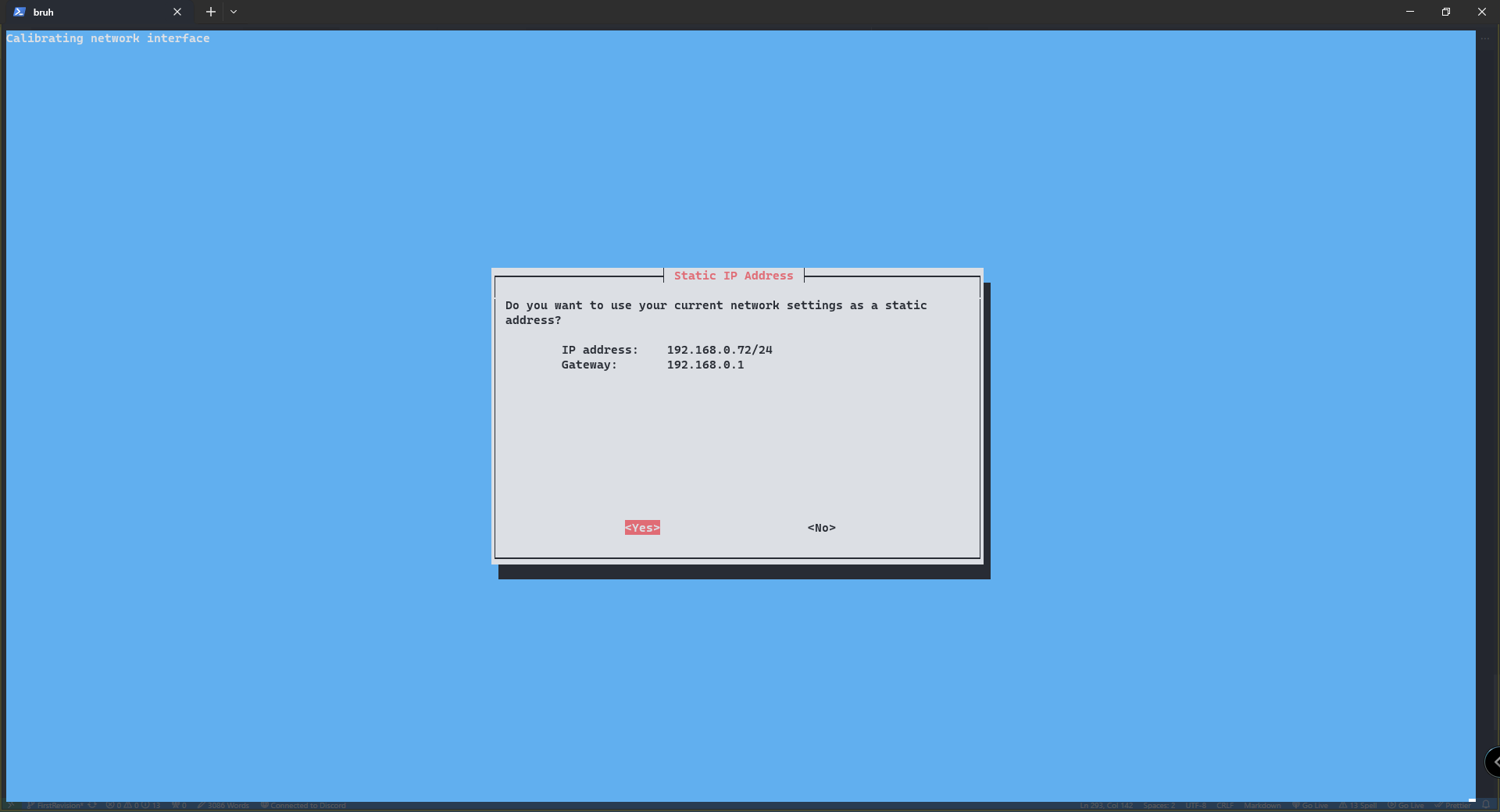
[Image Missing] Public IP or DNS: Most of you will pick public IP address.
 Reboot and you have successfully installed PiVPN!
Reboot and you have successfully installed PiVPN!
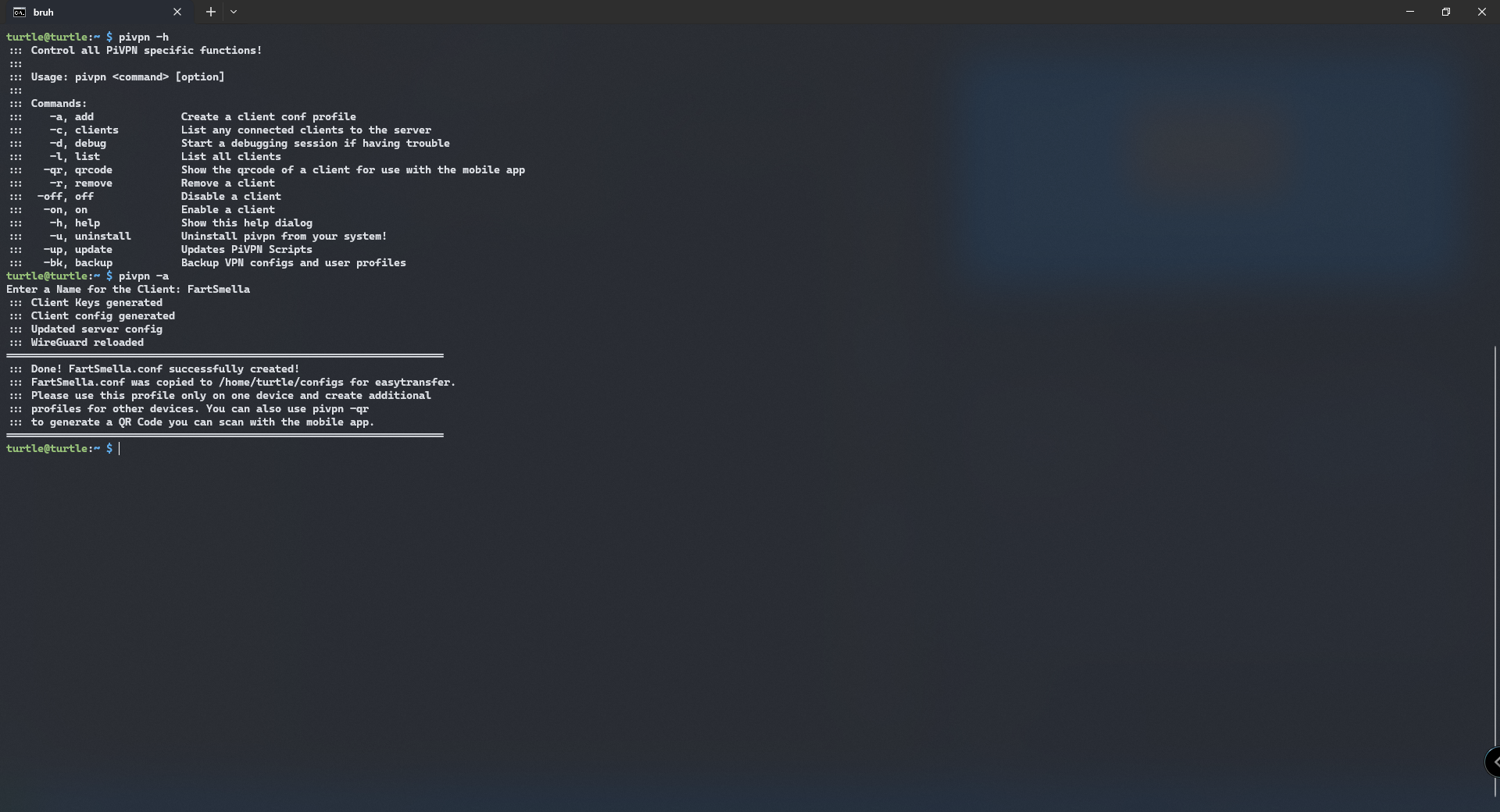
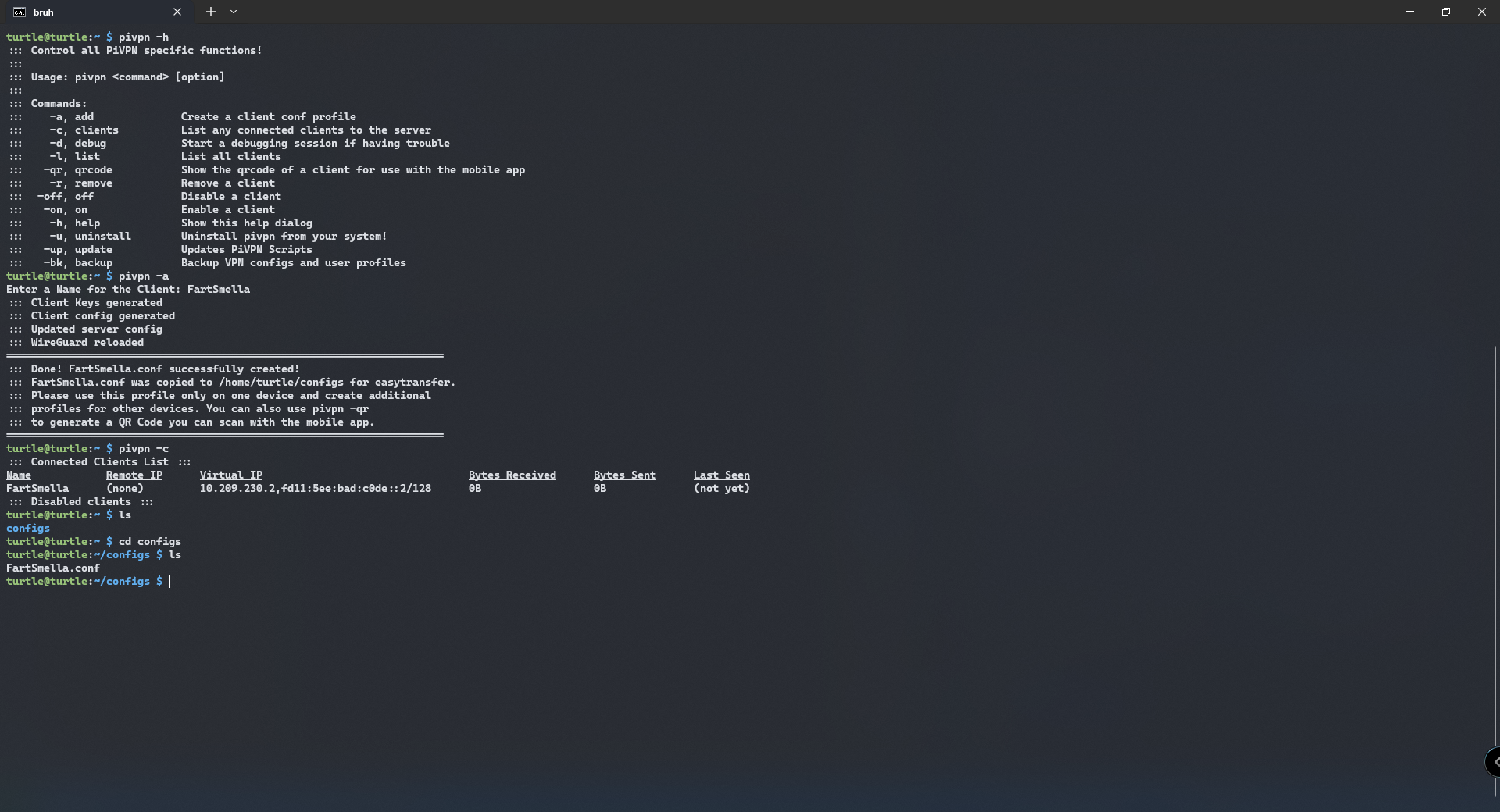
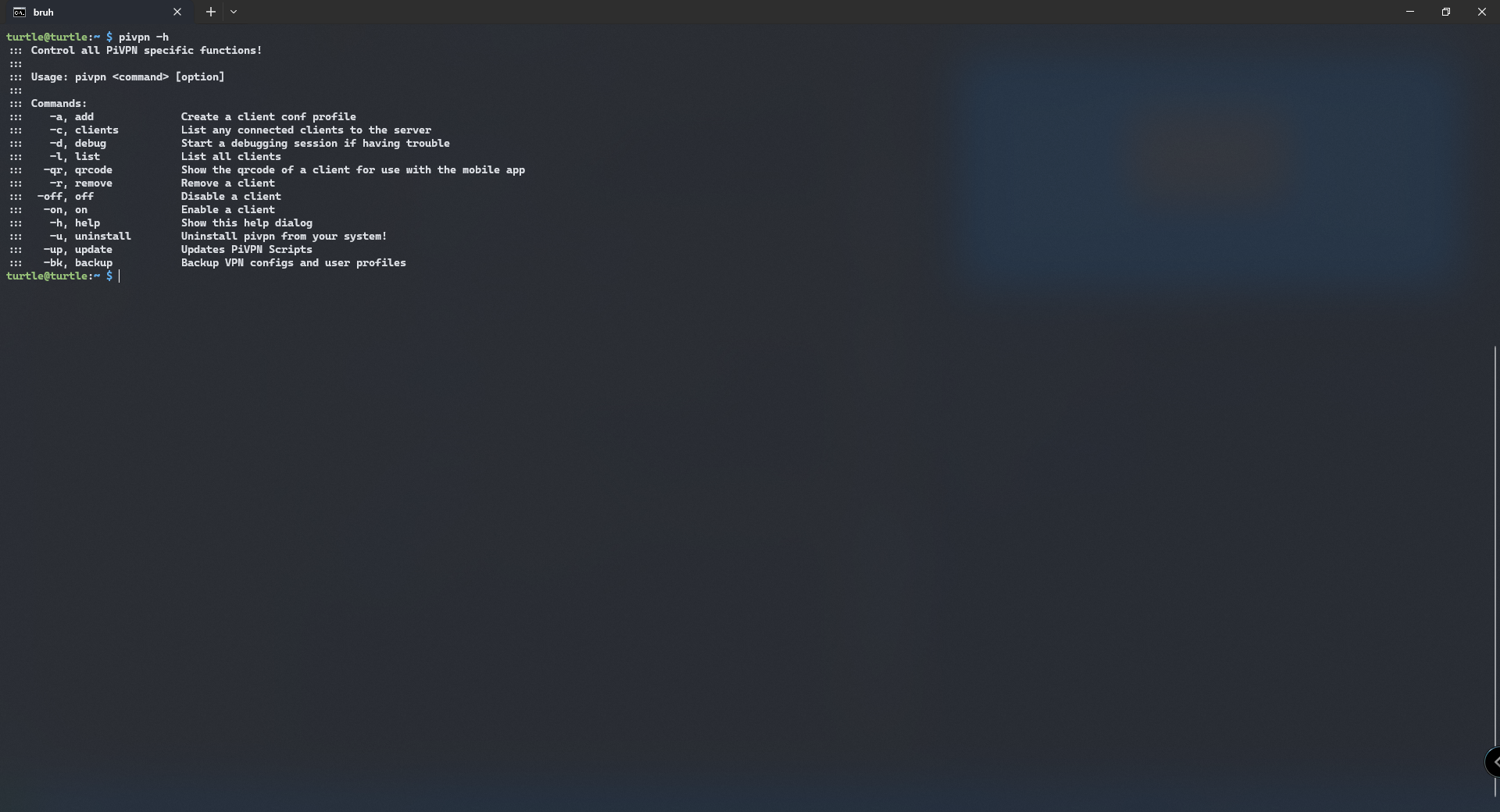
now we want to add a peer to our VPN. we view a list of commands using pivpn -h
We type in pivpn -a and a setup wizard will walk us through the instructions. We just have to input the name of our peer. To keep track of configuration files are connections, I usually assign the file with their Minecraft username. So if their username is FartSmella I would assign the .conf file with that appropriate name as seen below.
Now, a new folder has been created in your home directory. type cd configs and you can see that FartSmella.conf has been created.
you would distribute this file to others if they want to connect to your VPN. Though the default configuration of the file is kinda bad unfortunately and Users can alter the configuration of the file in order to get more access to resources. In order to prevent such a thing from occurring, we have to implement a firewall using IPTables.
Let's define the scope of what sort of rules we want to enable in our firewall.
- Users should be able to freely connect to port 25565
- Users should not be able to ssh into the raspberry pi
- If you want to enable ssh for certain users feel free, you can just use this command to make it happen.
iptables -A INPUT {IP-ADDRESS} -p tcp --dport 25565 -j ACCEPT- Make sure to do this above
iptables -A INPUT -i wg0 -p tcp --dport 22 -j DROPas the ordering matters.
- Users should not be able to forward requests outside of the VPN network.
Caution
The following has not been tested and acts as a placeholder, please do not use the following. `
# preup.sh
iptables -A INPUT -i wg0 -p tcp --dport 22 -j DROP
iptables -A INPUT -i wg0 -p tcp --dport 25565 -j ACCEPT
iptables -A INPUT -i wg0 -j DROP`
iptables -A FORWARD -i wg0 -o wlan0 -j DROP
please see CONTRIBUTING.md.
Footnotes
-
Kurose, J. F., & Ross, K. W., (2017) Computer Networking: A Top-Down Approach (pp. 666). Pearson Education Limited. ↩ ↩2 ↩3
-
https://www.fortinet.com/resources/cyberglossary/cia-triad ↩
-
https://www.tomsguide.com/how-to/is-the-new-wireguard-protocol-secure ↩ ↩2