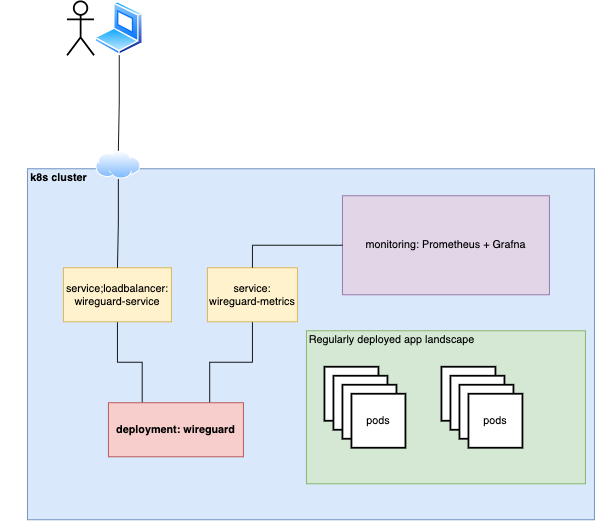
painless deployment of wireguard on kubernetes
If you are facing any problems please open an issue or join our slack channel
- IBM Cloud Kubernetes Service
- Gcore Labs KMP
- requires enable IP forwarding manually. will dig more into automating it but I was able to make it work manually.
- Google Kubernetes Engine
- requires
spec.mtu: "1380"
- requires
- DigitalOcean Kubernetes
- requires
spec.serviceType: "NodePort". DigitalOcean LoadBalancer does not support UDP.
- requires
- Self managed k3s on Hetzner
- Amazon EKS
- Azure Kubernetes Service
- ...?
- Uses userspace implementation of wireguard through wireguard-go
- Automatic key generation
- Automatic IP allocation
- Does not need persistance. peer/server keys are stored as k8s secrets and loaded into the wireguard pod
- Exposes a metrics endpoint by utilizing prometheus_wireguard_exporter
apiVersion: vpn.example.com/v1alpha1
kind: Wireguard
metadata:
name: "my-cool-vpn"
spec:
mtu: "1380"
apiVersion: vpn.example.com/v1alpha1
kind: WireguardPeer
metadata:
name: peer1
spec:
wireguardRef: "my-cool-vpn"
Peer configuration can be retreived using the following command
kubectl get wireguardpeer peer1 --template={{.status.config}} | bash
[Interface]
PrivateKey = WOhR7uTMAqmZamc1umzfwm8o4ZxLdR5LjDcUYaW/PH8=
Address = 10.8.0.3
DNS = 10.48.0.10, default.svc.cluster.local
MTU = 1380
[Peer]
PublicKey = sO3ZWhnIT8owcdsfwiMRu2D8LzKmae2gUAxAmhx5GTg=
AllowedIPs = 0.0.0.0/0
Endpoint = 32.121.45.102:51820
kubectl apply -f https://raw.githubusercontent.com/jodevsa/wireguard-operator/0.0.3/release.yaml
kubectl delete -f https://raw.githubusercontent.com/jodevsa/wireguard-operator/0.0.3/release.yaml