The cert-issuer project issues blockchain certificates by creating a transaction from the issuing institution to the recipient on the Bitcoin blockchain that includes the hash of the certificate itself.
For development or testing using web requests, check out the documentation at docs/web_resources.md.
This uses bitcoind in regtest mode. This route makes many simplifications to allow a quick start, and is intended for experimenting only.
-
First ensure you have Docker installed. See our Docker installation help.
-
Clone the repo and change to the directory
git clone https://github.com/blockchain-certificates/cert-issuer.git && cd cert-issuer -
From a command line in cert-issuer dir, build your docker container:
docker build -t bc/cert-issuer:1.0 . -
Read before running!
-
Once you launch the docker container, you will make some changes using your personal issuing information. This flow mirrors what you would if you were issuing real certificates.
-
To avoid losing your work, you should create snapshots of your docker container. You can do this by running:
docker ps -l docker commit <container for your bc/cert-issuer> my_cert_issuer
-
-
When you're ready to run:
docker run -it bc/cert-issuer:1.0 bash -
Copy the blockchain certificates you issued out of the docker container to a local directory
docker cp <container for your bc/cert-issuer>:/etc/cert-issuer/data/blockchain_certificates/<your-certificate-guid>.json <path_to_local_dir>
Important: this is a simplification to avoid using a USB, which needs to be inserted and removed during the standard certficate issuing process. Do not use these addresses or private keys for anything other than experimenting.
Ensure your docker image is running and bitcoind process is started
-
Create an 'issuing address' and save the output as follows:
issuer=`bitcoin-cli getnewaddress` sed -i.bak "s/<issuing-address>/$issuer/g" /etc/cert-issuer/conf.ini bitcoin-cli dumpprivkey $issuer > /etc/cert-issuer/pk_issuer.txt -
Don't forget to save snapshots so you don't lose your work (see step 3 of client setup)
-
Add your certificate to /etc/cert-issuer/data/unsigned_certificates/.
# To use a sample unsigned certificate as follows: cp /cert-issuer/examples/data-testnet/unsigned_certificates/3bc1a96a-3501-46ed-8f75-49612bbac257.json /etc/cert-issuer/data/unsigned_certificates/ # If you created your own unsigned certificate using cert-tools (assuming you placed it under data/unsigned_certificates): cp <cert-issuer-home>/data/unsigned_certificates/<your-cert-guid>.json /etc/cert-issuer/data/unsigned_certificates/ -
Make sure you have enough BTC in your issuing address.
a. You're using bitcoind in regtest mode, so you can print money. This should give you 50 (fake) BTC:
bitcoin-cli generate 101 bitcoin-cli getbalanceb. Send the money to your issuing address -- note that bitcoin-cli's standard denomination is bitcoins not satoshis! (In our app, the standard unit is satoshis.) This command sends 5 bitcoins to the address
bitcoin-cli sendtoaddress $issuer 5 -
Issue the certificates on the blockchain
cert-issuer -c /etc/cert-issuer/conf.ini -
Your Blockchain certificates are located in
/etc/cert-issuer/data/blockchain_certificates. Copy these to your local machine, and add them to cert-viewer'scert_datafolder to see your certificates in the Certificate Viewer.
docker ps // shows the docker containerId
docker cp <containerId>:/etc/cert-issuer/data/blockchain_certificates <localPath>/cert-viewer/cert_data
While it is possible to issue one certificate with one Bitcoin transaction, it is far more efficient to use one Bitcoin transaction to issue a batch of certificates.
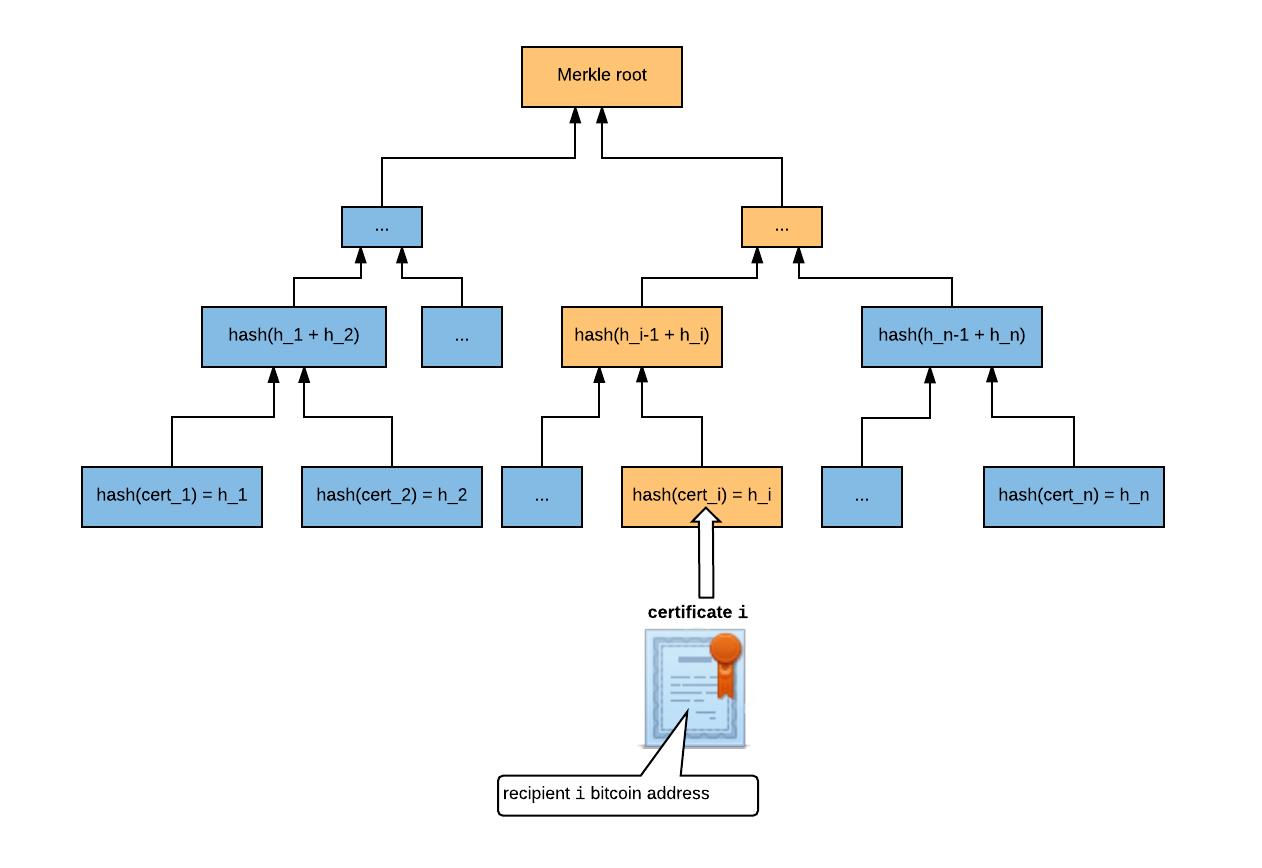
The issuer builds a Merkle tree of certificate hashes and registers the Merkle root as the OP_RETURN field in the Bitcoin transaction.
Suppose the batch contains n certificates, and certificate i contains recipient i's information. The issuer hashes each certificate and combines them into a Merkle tree:
The root of the Merkle tree, which is a 256-bit hash, is issued on the Bitcoin blockchain. The complete Bitcoin transaction outputs are described in 'Transaction structure'.
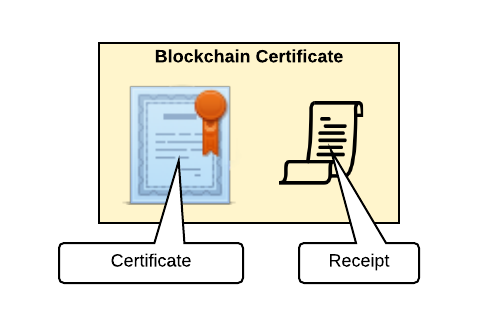
The Blockchain Certificate given to recipient i contains a 2017 Merkle Proof Signature Suite-formatted signature, proving that certificate i is contained in the Merkle tree.
This receipt contains:
- The Bitcoin transaction ID storing the Merkle root
- The expected Merkle root on the blockchain
- The expected hash for recipient
i's certificate - The Merkle path from recipient
i's certificate to the Merkle root, i.e. the path highlighted in orange above.h_i -> … -> Merkle root
The verification process performs computations to check that:
- The hash of certificate
imatches the value in the receipt - The Merkle path is valid
- The Merkle root stored on the blockchain matches the value in the receipt
These steps establish that the certificate has not been tampered with since it was issued.
The Blockchain Certificate JSON contents without the signature node is the certificate that the issuer created. This is the value needed to hash for comparison against the receipt. Because there are no guarantees about ordering or formatting of JSON, first canonicalize the certificate (without the signature) against the JSON LD schema. This allows us to obtain a deterministic hash across platforms.
The detailed steps are described in the verification process.
How a batch is defined can vary, but it should be defined such that it changes infrequently. For example, “2016 MIT grads” would be preferred over “MIT grads” (the latter would have to be updated every year). The size of the batch is limited by the 100KB maximum transaction size imposed by the Bitcoin network. This will amount to a maximum of around 2,000 recipients per certificate batch.
One Bitcoin transaction is performed for every batch of certificates. There is no limit to the number of certificates that may be included in a batch, so typically batches are defined in logical groups such as "Graduates of Fall 2017 Robotics Class".
The transaction structure is the following:
- Input:
- Minimal amount of bitcoin (currently ~$.80 USD) from Issuer's Bitcoin address
- Outputs:
- OP_RETURN field, storing a hash of the batch of certificates
- Optional: change to an issuer address
The OP_RETURN output is used to prove the validity of the certificate batch. This output stores data, which is the hash of the Merkle root of the certificate batch. At any time, we can look up this value on the blockchain to help confirm a claim.
The Issuer Bitcoin address and timestamp from the transaction are also critical for the verification process. These are used to check the authenticity of the claim, as described in verification process.
The Quick Start assumed you are issuing certificates in Bitcoin regtest mode, which doesn't actually write to a public blockchain. To actually write your transaction, you need to run in testnet (with test coins -- not real money) or mainnet (real money).
We recommend starting in testnet before mainnet.
By default, cert-issuer does not assume you have a bitcoin/ethereum node running locally, and it uses APIs to look up and broadcast transactions. There is API support for both testnet and mainnet chains.
If you do want to use a local bitcoin node, see details about installing and configuring a bitcoin node for use with cert-issuer before continuing.
These steps walk you through issuing in testnet and mainnet mode. Note that the prerequisites and the configuration for the Bitcoin issuing and the Ethereum issuing differ.
Decide which chain (Bitcoin or Ethereum) to issue to and follow the steps. The bitcoin chain is currently best supported by the Blockcerts libraries. Follow the steps for the chosen chain.
By default, cert-issuer issues to the Bitcoin blockchain. Run the default setup script if this is the mode you want:
python setup.py install
To issue to the ethereum blockchain, run the following:
python setup.py experimental --blockchain=ethereum
See the docs here for helpful tips on creating / funding blockchain addresses: docs/testnet_mainnet_addresses
Edit your conf.ini file (the config file for this application).
issuing_address = <issuing-address>
chain=<bitcoin_regtest|bitcoin_testnet|bitcoin_mainnet|ethereum_ropsten|ethereum_mainnet|mockchain>
usb_name = </Volumes/path-to-usb/>
key_file = <file-you-saved-pk-to>
unsigned_certificates_dir=<path-to-your-unsigned-certificates>
blockchain_certificates_dir=<path-to-your-blockchain-certificates>
work_dir=<path-to-your-workdir>
no_safe_mode
# advanced: uncomment the following line if you're running a bitcoin node
# bitcoind
Notes:
- The
bitcoindoption is technically not required inregtestmode.regtestmode only works with a local bitcoin node. The quick start in docker brushed over this detail by installing a regtest-configured bitcoin node in the docker container. - The Ethereum option does not support a local (test)node currently. The issuer will broadcast the transaction via the Etherscan API.
-
Add your certificates to data/unsigned_certs/
-
If you've installed the package you can issue certificates by running:
python cert-issuer -c conf.ini
- Output
- The Blockchain Certificates will be located in data/blockchain_certificates.
- If you ran in the mainnet or testnet mode, you can also see your transaction on a live blockchain explorer.
More information on contributing to the cert-issuer codebase can be found in docs/contributing.md
The files in examples/data-testnet contain results of previous runs.
You can validate your transaction before sending by looking it up by rawtx at blockchain.info. Example:
curl 'https://blockchain.info/rawtx/45a9306dfe99820eb346bb17ae0b64173ac11cac2d0e4227c7a7cacbcc0bad31?cors=true'
For an Ethereum transaction, you'll need to use a different explorer, which might require an API key for raw JSON output. To view a transaction in a web browser, you might try something like this:
- Ethereum Mainnet: https://etherscan.io/tx/0xf537d81667c8011e34e1f450e18fd1c5a8a10c770cd0acdc91a79746696f36a3
- Ethereum Ropsten (testnet): https://ropsten.etherscan.io/tx/0xf537d81667c8011e34e1f450e18fd1c5a8a10c770cd0acdc91a79746696f36a3
If your install on Mac is failing with a message like the following, try the workaround described in this thread or the workaround described here.
fatal error: 'openssl/aes.h'
file not found
#include <openssl/aes.h>
Contact us at the Blockcerts community forum.