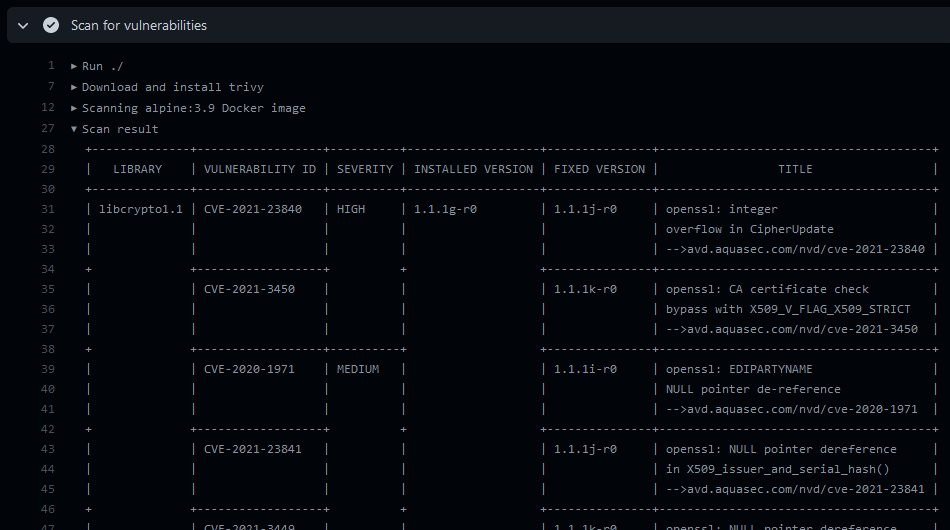
GitHub Action to check for vulnerabilities in your container image with Trivy.
name: ci
on:
push:
jobs:
scan:
runs-on: ubuntu-latest
steps:
-
name: Checkout
uses: actions/checkout@v3
-
name: Build
uses: docker/build-push-action@v3
with:
context: .
push: true
tags: user/app:latest
-
name: Scan for vulnerabilities
uses: crazy-max/ghaction-container-scan@v2
with:
image: user/app:latestname: ci
on:
push:
jobs:
scan:
runs-on: ubuntu-latest
steps:
-
name: Checkout
uses: actions/checkout@v3
-
name: Set up Docker Buildx
uses: docker/setup-buildx-action@v2
-
name: Build
uses: docker/build-push-action@v3
with:
context: .
outputs: type=oci,dest=/tmp/image.tar
tags: user/app:latest
-
name: Scan for vulnerabilities
uses: crazy-max/ghaction-container-scan@v2
with:
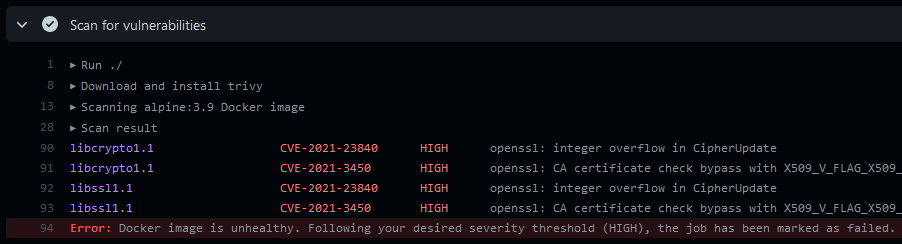
tarball: /tmp/image.tarYou can define a threshold for severity to mark the job as failed:
name: ci
on:
push:
jobs:
scan:
runs-on: ubuntu-latest
steps:
-
name: Checkout
uses: actions/checkout@v3
-
name: Build
uses: docker/build-push-action@v3
with:
context: .
push: true
tags: user/app:latest
-
name: Scan for vulnerabilities
uses: crazy-max/ghaction-container-scan@v2
with:
image: user/app:latest
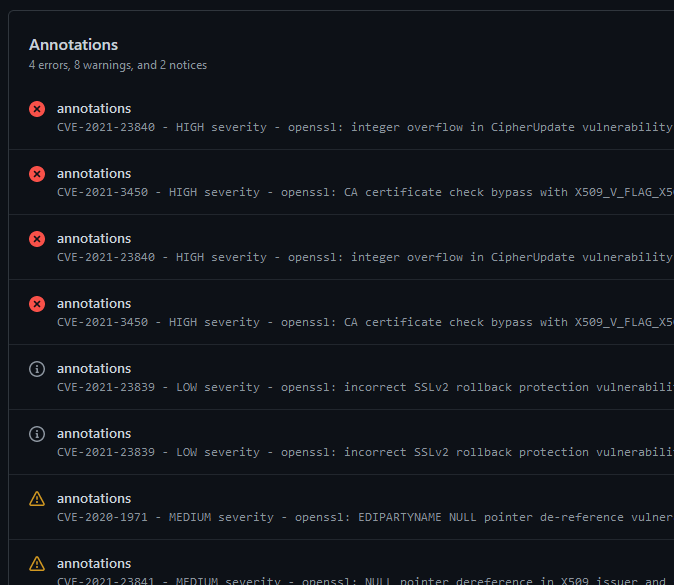
severity_threshold: HIGHThis action is also able to create GitHub annotations in your workflow for vulnerabilities discovered:
name: ci
on:
push:
jobs:
scan:
runs-on: ubuntu-latest
steps:
-
name: Checkout
uses: actions/checkout@v3
-
name: Build
uses: docker/build-push-action@v3
with:
context: .
push: true
tags: user/app:latest
-
name: Scan for vulnerabilities
uses: crazy-max/ghaction-container-scan@v2
with:
image: user/app:latest
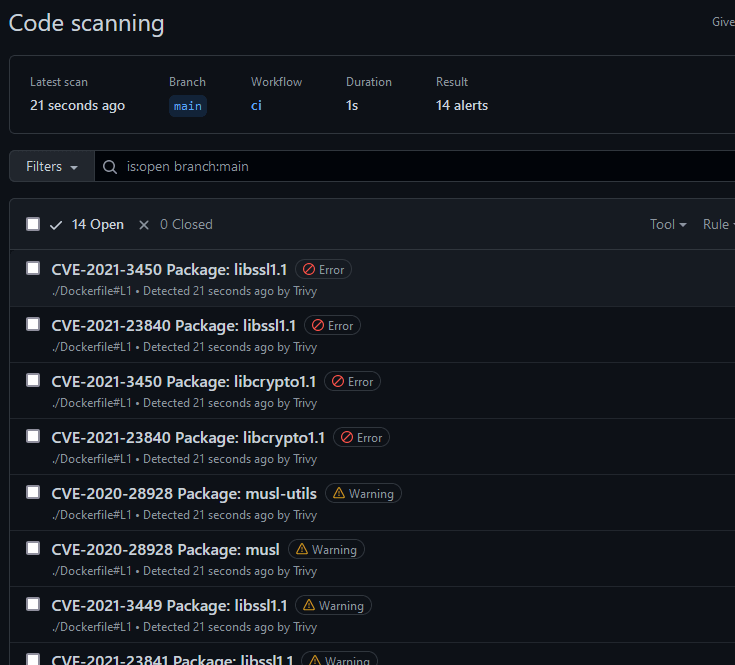
annotations: trueThis action also supports the SARIF format for integration with GitHub Code Scanning to show issues in the GitHub Security tab:
name: ci
on:
push:
jobs:
scan:
runs-on: ubuntu-latest
steps:
-
name: Checkout
uses: actions/checkout@v3
-
name: Build
uses: docker/build-push-action@v3
with:
context: .
push: true
tags: user/app:latest
-
name: Scan for vulnerabilities
id: scan
uses: crazy-max/ghaction-container-scan@v2
with:
image: user/app:latest
dockerfile: ./Dockerfile
-
name: Upload SARIF file
if: ${{ steps.scan.outputs.sarif != '' }}
uses: github/codeql-action/upload-sarif@v2
with:
sarif_file: ${{ steps.scan.outputs.sarif }}💡
dockerfileinput is required to generate a sarif report.
name: ci
on:
push:
jobs:
scan:
runs-on: ubuntu-latest
steps:
-
name: Checkout
uses: actions/checkout@v3
-
name: Set up QEMU
uses: docker/setup-qemu-action@v2
-
name: Set up Docker Buildx
uses: docker/setup-buildx-action@v2
-
name: Build and load
uses: docker/build-push-action@v3
with:
context: .
load: true
tags: user/app:latest
-
name: Scan for vulnerabilities
id: scan
uses: crazy-max/ghaction-container-scan@v2
with:
image: user/app:latest
dockerfile: ./Dockerfile
-
name: Build multi-platform and push
uses: docker/build-push-action@v3
with:
context: .
platforms: linux/amd64,linux/arm64
push: true
tags: user/app:latestFollowing inputs can be used as step.with keys
| Name | Type | Description |
|---|---|---|
trivy_version |
String | Trivy CLI version (default latest) |
image |
String | Container image to scan (e.g. alpine:3.7) |
tarball |
String | Container image tarball path to scan |
dockerfile |
String | Dockerfile required to generate a sarif report |
severity |
String | Report vulnerabilities of provided level or higher (default: UNKNOWN,LOW,MEDIUM,HIGH,CRITICAL) |
severity_threshold |
String | Defines threshold for severity |
annotations |
Bool | Create GitHub annotations in your workflow for vulnerabilities discovered |
Following outputs are available
| Name | Type | Description |
|---|---|---|
json |
File | JSON format scan result |
sarif |
File | SARIF format scan result |
If you want the scan to include the Dockerfile, you'll need to checkout the repository and give the job:
permissions:
contents: readIf you want to upload the SARIF report to GitHub Security, you'll need to add these permissions to the job:
permissions:
actions: read
security-events: writeIf you receive this error, it likely means you're using a private repository and trying to upload SARIF reports, which requires a org admin to enable Advanced Security for the repository.
If you encounter this error, you probably have a huge image to scan so, you may need to free up some space in your runner. You can remove the dotnet framework for example that takes around 23GB of disk space:
-
name: Remove dotnet
run: sudo rm -rf /usr/share/dotnet
-
name: Scan for vulnerabilities
uses: crazy-max/ghaction-container-scan@v2
with:
image: user/app:latestThis error is caused by the timeout of the trivy command. You can increase
the timeout by setting TRIVY_TIMEOUT environment variable:
-
name: Scan for vulnerabilities
uses: crazy-max/ghaction-container-scan@v2
with:
image: user/app:latest
env:
TRIVY_TIMEOUT: 10mYou may encounter this issue if you're using github.repository as a
repo slug for the image input:
Error: 2021-11-30T09:52:13.115Z FATAL scan error: unable to initialize a scanner: unable to initialize a docker scanner: failed to parse the image name: could not parse reference: ghcr.io/UserName/myimage:latest
To fix this issue you can use our metadata action to generate sanitized tags:
-
name: Docker meta
id: meta
uses: docker/metadata-action@v4
with:
images: ghcr.io/${{ github.repository }}
tags: latest
-
name: Build and push
uses: docker/build-push-action@v3
with:
context: .
push: true
tags: ${{ steps.meta.outputs.tags }}
-
name: Scan for vulnerabilities
id: scan
uses: crazy-max/ghaction-container-scan@v2
with:
image: ${{ fromJSON(steps.meta.outputs.json).tags[0] }}
dockerfile: ./DockerfileOr a dedicated step to sanitize the slug:
-
name: Sanitize repo slug
uses: actions/github-script@v6
id: repo_slug
with:
result-encoding: string
script: return 'ghcr.io/${{ github.repository }}'.toLowerCase()
-
name: Build and push
uses: docker/build-push-action@v3
with:
context: .
push: true
tags: ${{ steps.repo_slug.outputs.result }}:latest
-
name: Scan for vulnerabilities
id: scan
uses: crazy-max/ghaction-container-scan@v2
with:
image: ${{ steps.repo_slug.outputs.result }}:latest
dockerfile: ./DockerfileWant to contribute? Awesome! The most basic way to show your support is to star the project, or to raise issues. If you want to open a pull request, please read the contributing guidelines.
You can also support this project by becoming a sponsor on GitHub or by making a Paypal donation to ensure this journey continues indefinitely!
Thanks again for your support, it is much appreciated! 🙏
MIT. See LICENSE for more details.