A Command & Control Front-end ReactJS web server that controls client malware installed on victim computers. This will let you control infected computers and see their webcam, screen, and in the future, have access to a console session.
I do not condone the use of this software for illegal purposes.
This program was written for the Association of Computing and Machinery's MangoHacks 2019. This project is my first using React, GraphQL, and 8base. I had a lot of fun at this 36-hour event!
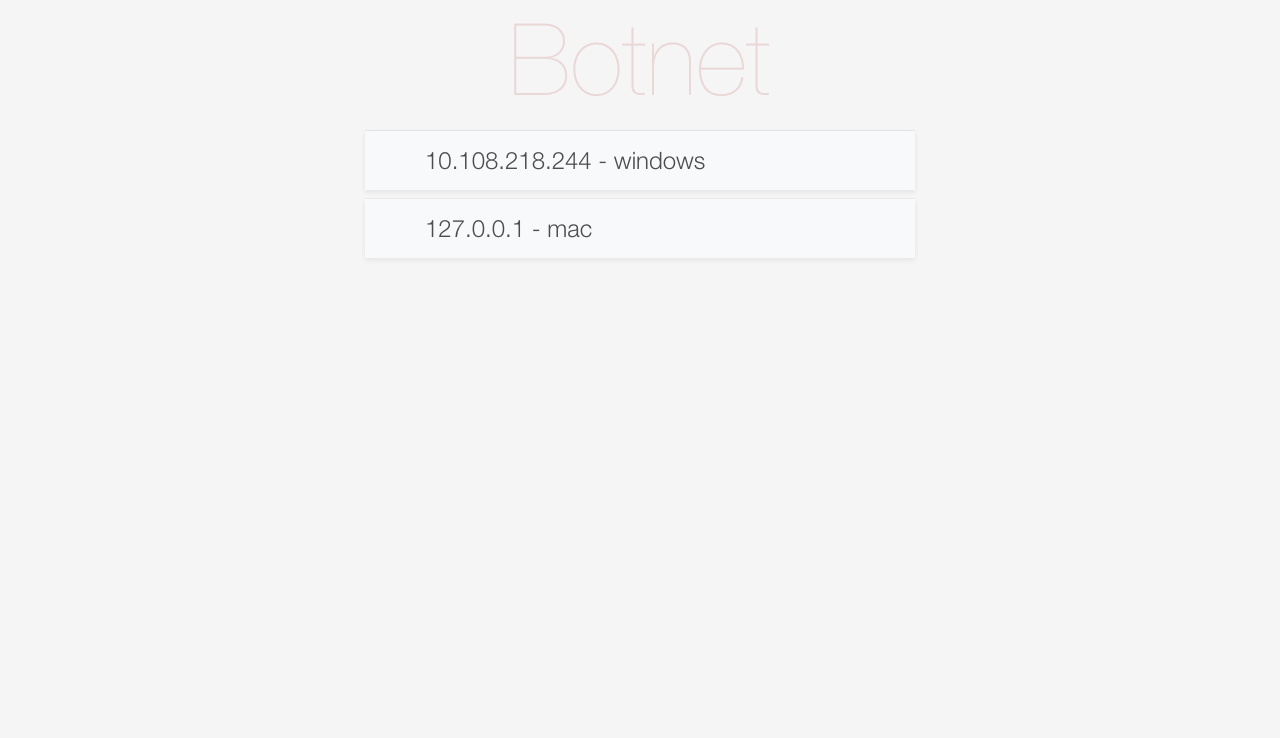
Your victim control panel will look like this:
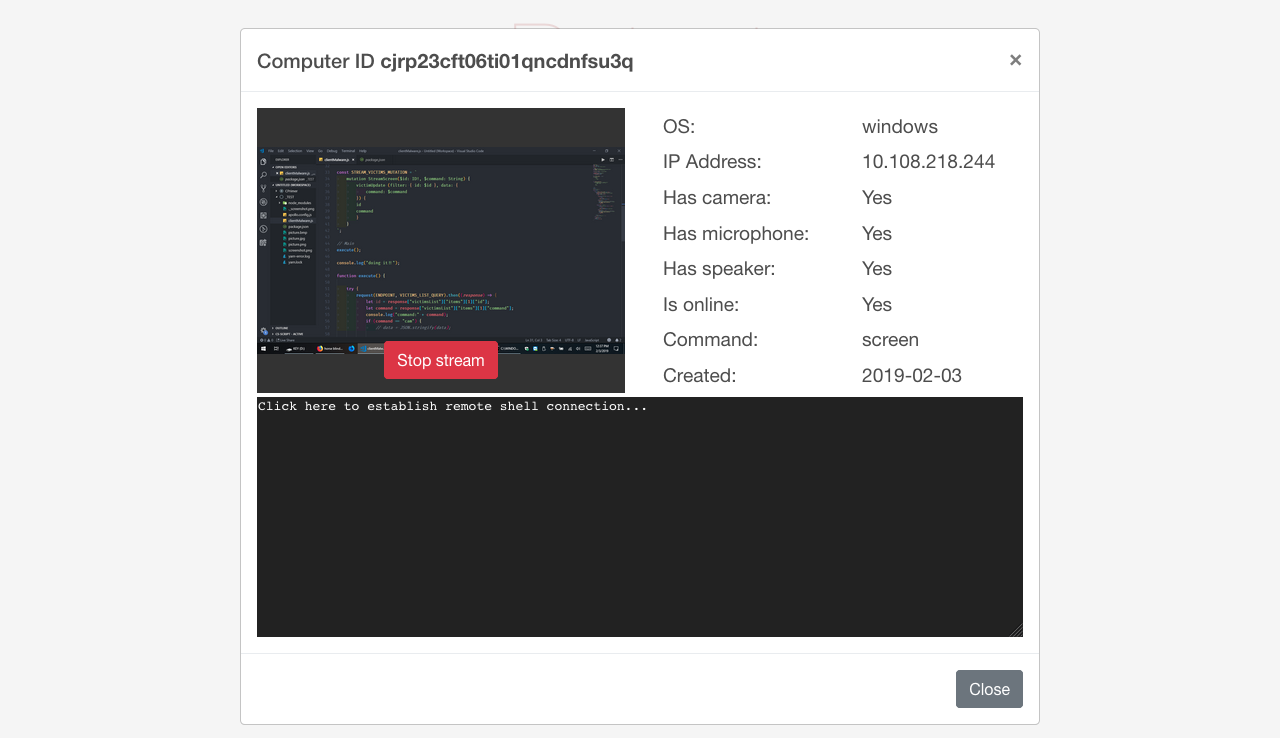
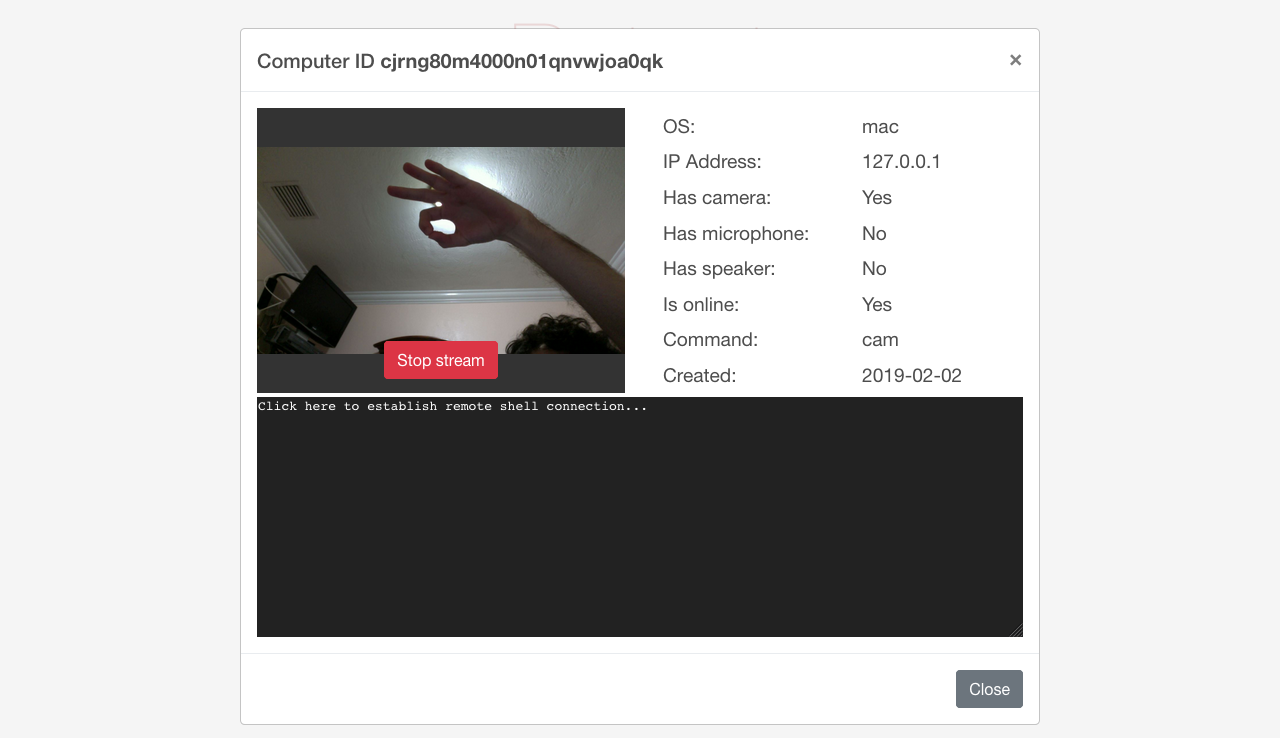
You will be able to view the screen and webcam feed of an infected machine like so:
Clone this repo with the following command to a folder onto your local machine:
git clone https://github.com/rslay/MalwareReactor-Server.gitMake sure to run npm install, or use yarn add if you prefer.
MalwareReactor makes use of a third-party service, 8base. You must create an account and generate a table with data for machines you've infected manually (this is not automatically done by clients yet) with the following schema:
table: victims
fields:
- os (text)
- ip (text)
- hasCam (bool)
- hasMic (bool)
- hasSpeakers (bool)
- online (bool)
- command (text)To run the C&C server, set your 8base GraphQL API key in the declaration of the constant ENDPOINT_URL within src/App.js, then, once you have everything set up, run the React web server with the following command at the root:
npm startIf you load up http://localhost:8080, you will see this:
Next, you'll want to also run the websocket server to share images received from the local network (at the moment only devices in the LAN can send images to the C&C due to file limitations on 8base):
node wsserver.jsThis script will constantly update the React web server with an image recieved via websocket by putting them in it's local directory.
Once the server is running, test everything by running the example malware client script using:
cd malware/
npm install # or do `yarn add` if you prefer
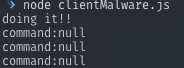
node clientMalware.jsDepending on the value you've set for command on that machine's row in 8base (you must supply the id of the machine in the response array manually, for now) you will see something like this:
You can go to the web server at http://localhost:8080 once more, and you should be able to click the Show webcam / Show screen buttons after selecting an infected computer. It will look like this in the vicitm's console:
Contact me if you're struggling to get this set up, I'd be more than happy to help.