This repository contains the code for the paper Invisible Image Watermarks Are Provably Removable Using Generative AI.
If you find this repository useful, please cite our paper:
@article{zhao2023invisible,
title={Invisible Image Watermarks Are Provably Removable Using Generative AI},
author={Zhao, Xuandong and Zhang, Kexun and Su, Zihao and Vasan, Saastha and Grishchenko, Ilya and Kruegel, Christopher and Vigna, Giovanni and Wang, Yu-Xiang and Li, Lei},
journal={arXiv preprint arXiv:2306.01953},
year={2023}
}
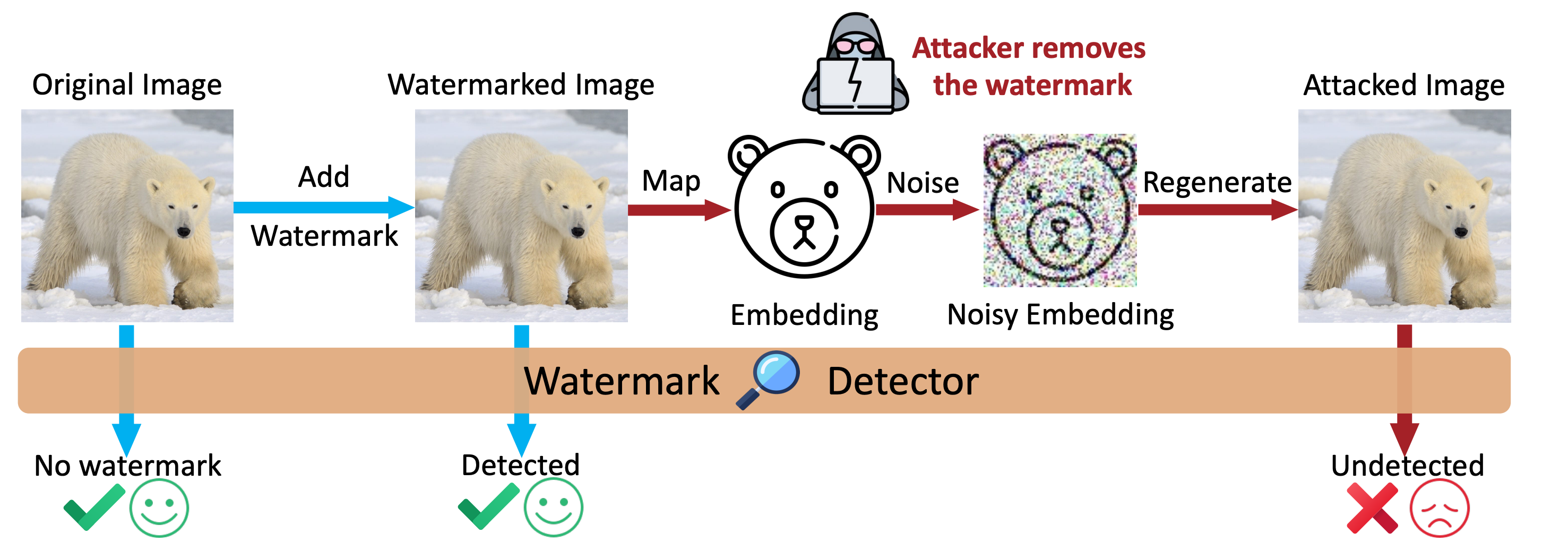
We propose a family of regeneration attacks to remove invisible image watermarks. The attack method effectively removes invisible watermarks.
Our attack first maps the watermarked image to its embedding, which is another representation of the image. Then the embedding is noised to destruct the watermark. After that, a regeneration algorithm reconstructs the image from the noisy embedding. As shown in the figure below:
First, install the dependencies:
pip install -r requirements.txtThen, run the following command to install modified diffusers
pip install -e .Then you can try the demo in demo.ipynb.
This demo attacks invisible-watermark which is used in stable diffusion.
In short, our method can be described using the following equation (1)
where
The embedding function
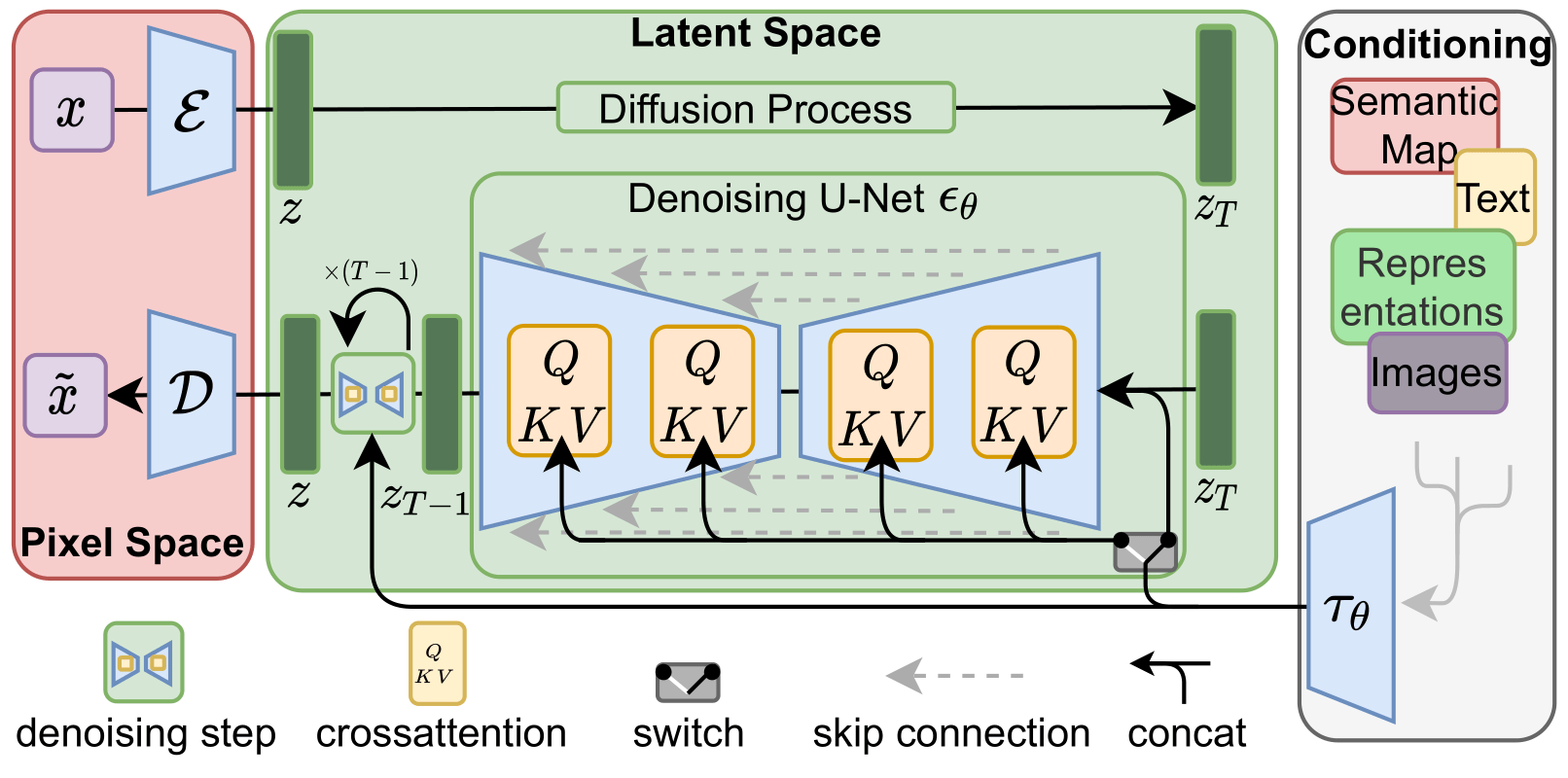
Here let's look at how Stable Diffusion can instantiate our algorithm (see this blog for more information on Stable Diffusion).
The above figure shows the architecture of Stable Diffusion.
The destructive process in our algorithm corresponds to adding noise to the image until a certain time step
where
After obtaining the noised representation