Below are the available downloads for the latest version of Komiser (1.0.0). Please download the proper package for your operating system and architecture.
wget https://s3.us-east-1.amazonaws.com/komiser/1.0.0/linux/komiser
wget https://s3.us-east-1.amazonaws.com/komiser/1.0.0/windows/komiser
wget https://s3.us-east-1.amazonaws.com/komiser/1.0.0/osx/komiser
- Create an IAM user with the following IAM policy:
wget https://s3.amazonaws.com/komiser/policy.json
- Add your Access Key ID and Secret Access Key to ~/.aws/credentials using this format
[default]
aws_access_key_id = <access key id>
aws_secret_access_key = <secret access key>
region = us-east-1
- That should be it. Try out the following from your command prompt to start the server:
komiser start --port 3000 --duration 30
- Point your browser to http://localhost:3000
Use the official Komiser image:
docker run -d -p 3000:3000 -e AWS_ACCESS_KEY_ID="" -e AWS_SECRET_ACCESS_KEY="" -e AWS_DEFAULT_REGION="" --name komiser mlabouardy/komiser
| Environment Variable | Description |
|---|---|
| PORT | Server Port |
| DURATION | Server Cache Expiration (minutes) |
| AWS_ACCESS_KEY_ID | AWS Access Key |
| AWS_SECRET_ACCESS_KEY | AWS Secret Key |
| AWS_DEFAULT_REGION | AWS Region |
| AWS_PROFILE | AWS Profile (Docs) |
When using the CLI you'll generally need your AWS credentials to authenticate with AWS services. Komiser supports multiple methods of supporting these credentials. By default the CLI will source credentials automatically from its default credential chain.
-
Environment Credentials - Set of environment variables that are useful when sub processes are created for specific roles.
-
Shared Credentials file (~/.aws/credentials) - This file stores your credentials based on a profile name and is useful for local development.
-
EC2 Instance Role Credentials - Use EC2 Instance Role to assign credentials to application running on an EC2 instance. This removes the need to manage credential files in production.
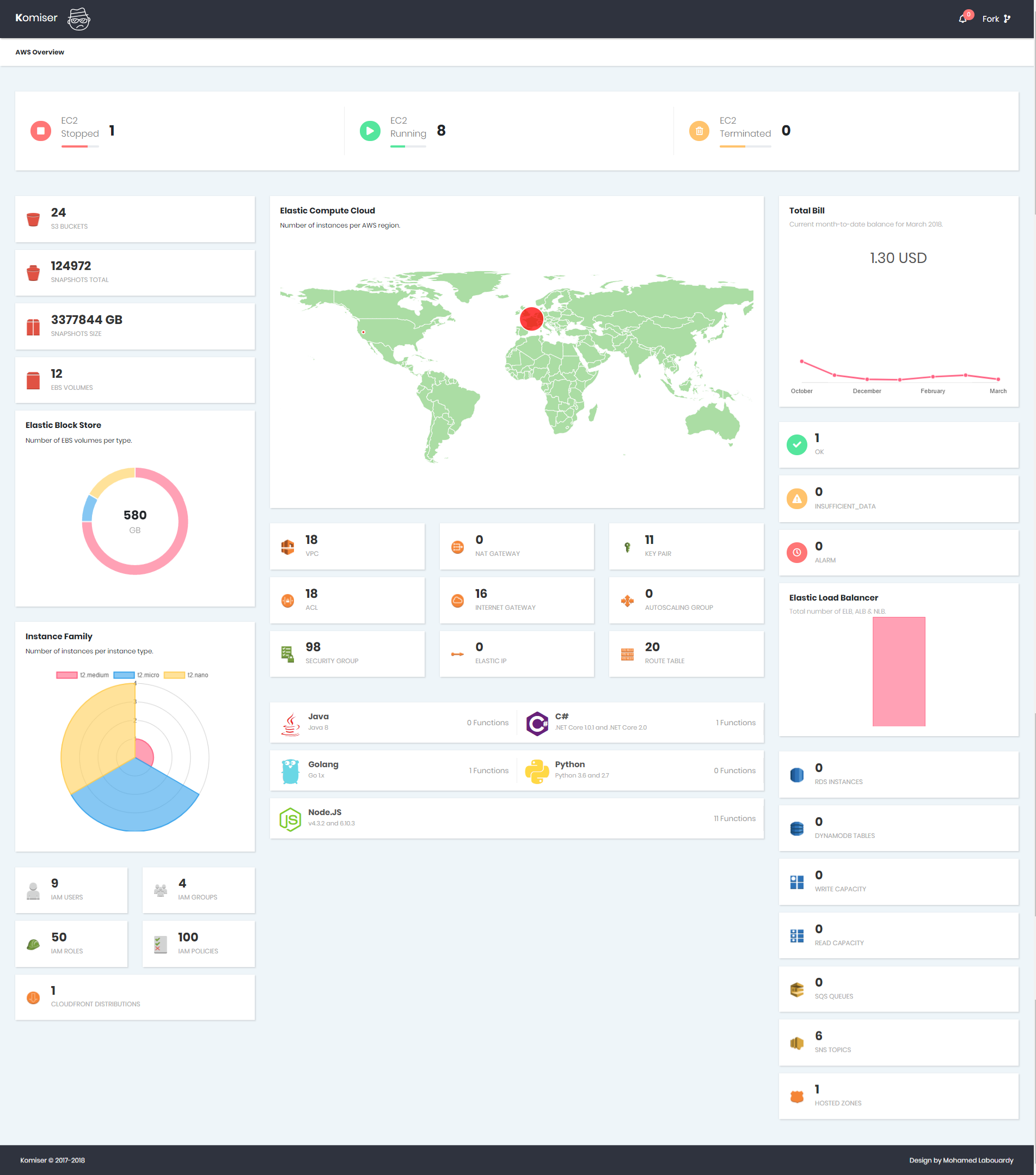
- EC2
- EBS
- Snapshots
- Security Groups
- Access Control Lists
- Autoscalling groups
- ELB
- VPC
- Key Pairs
- Nat Gateway
- Internet Gateway
- Elastic IP
- Route Table
- Billing
- Lambda Functions
- RDS
- DynamoDB
- S3
- Route53
- SQS
- SNS
- IAM
- CloudWatch Alarms
- CloudFront Distributions
- ECS
- EMR
- Kinesis
- Elastic Beanstalk
- Glacier
- EFS
- Mohamed Labouardy
Join us on Slack: https://komiser.slack.com
MIT