Things of my MSc thesis about a firewall system for working in unsafe environments.
It's not hard to point out someone is wearing a hood, but the hood makes it harder to say who is wearing it.
- Status
- Graphics to show the concept
- Recommended hardware
- Install to Raspberry Pi
- Install to Debian
- License
- Raspberry Pi 4B
- Regular computer
- Others not tested
- Windows 10
- Linux (Raspberry Pi OS / Debian live / Parrot OS)
- Mac OS
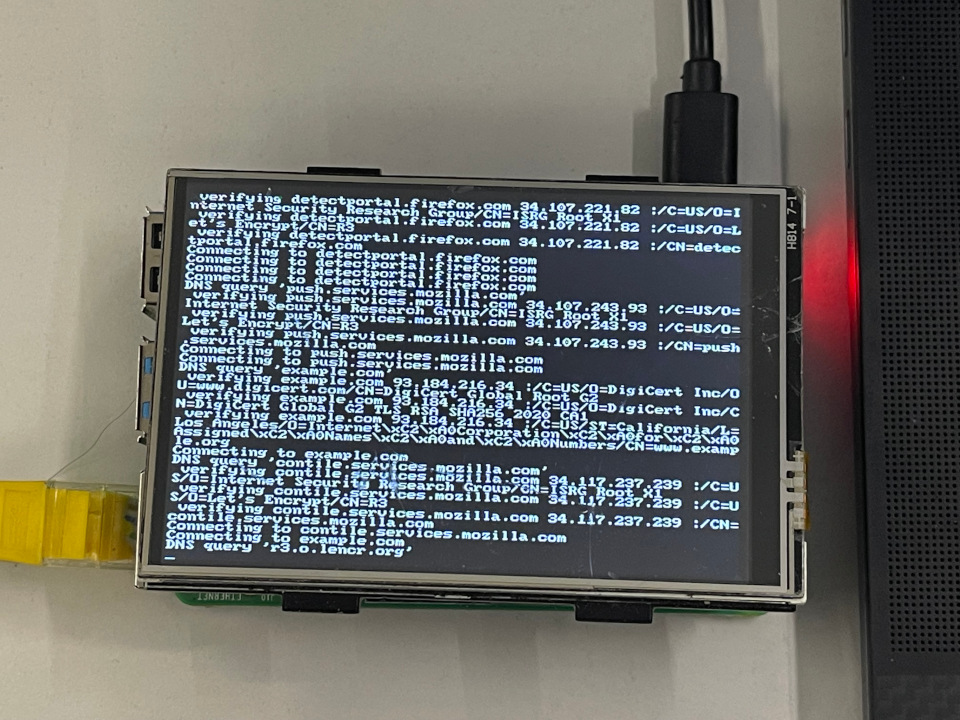
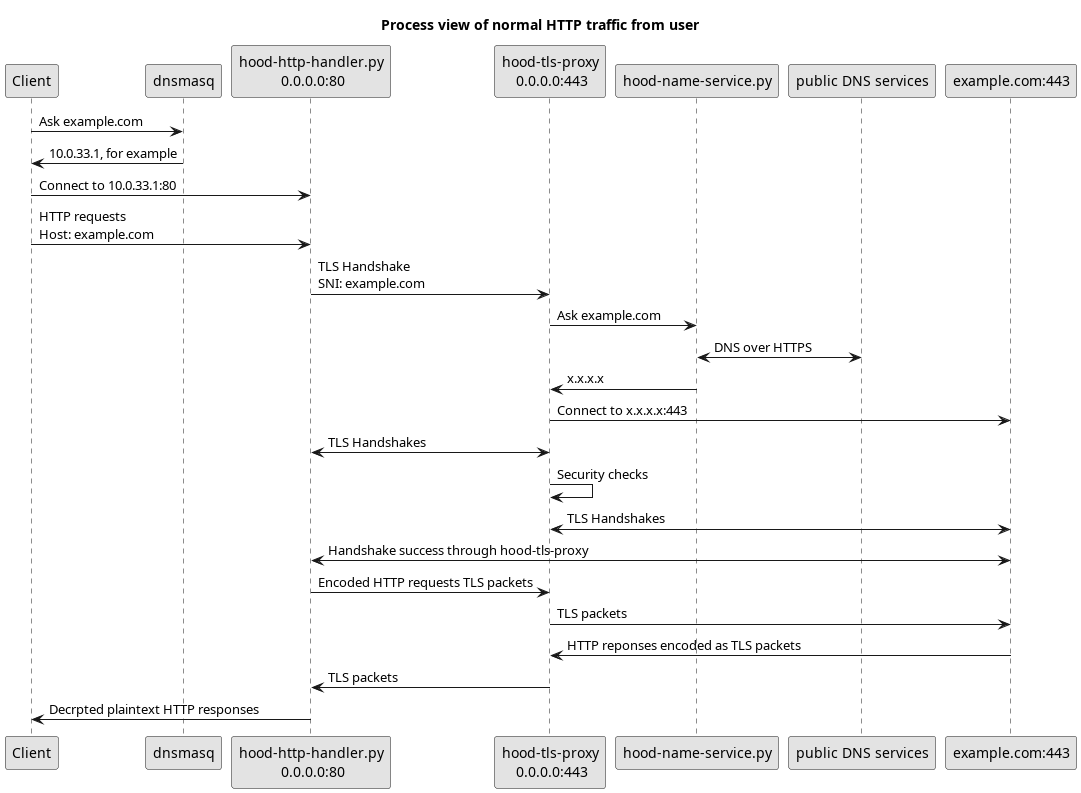
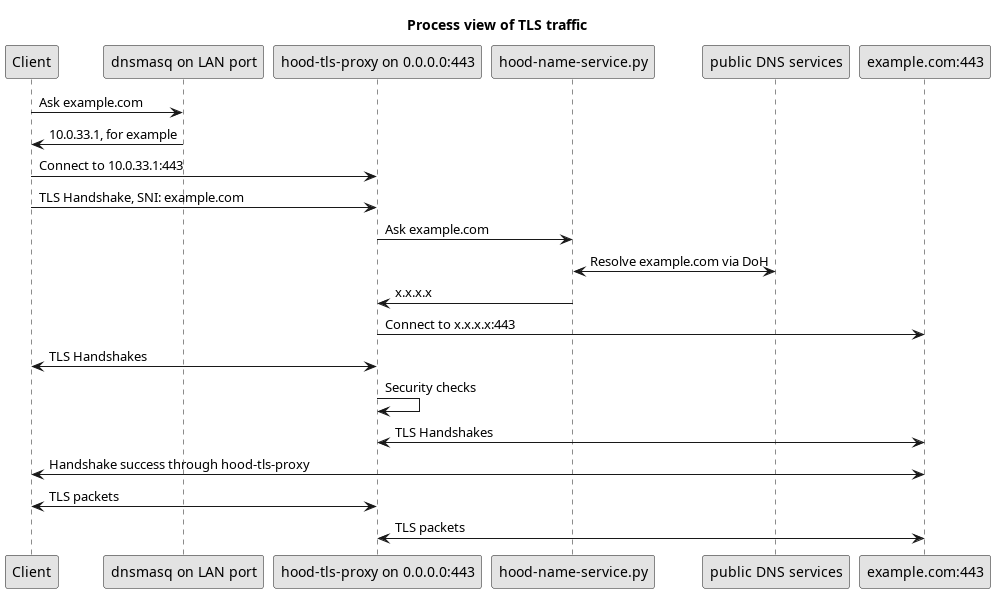
- Show realtime network activities on a screen
- Support HTTP3 QUIC
- Apply virtualization https://maimai.cn/web/feed_detail?fid=1733012779&efid=ntnLQCMgu6NRj1NgHnQ5gA
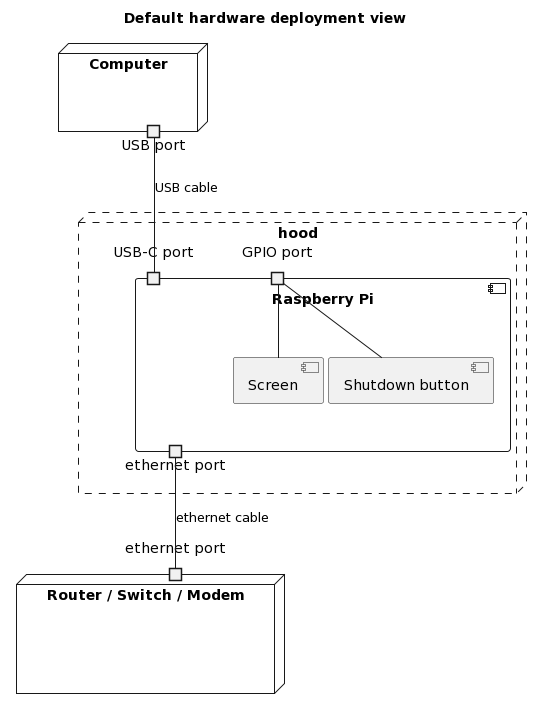
- SBC: Raspberry Pi 4B
- Screen: Waveshare 35a / Joy-IT RB-TFT3.5
If you already know how to write raspberrypi os image to a SD card, goto step 3
curl -L -O -C - https://downloads.raspberrypi.com/raspios_lite_arm64/images/raspios_lite_arm64-2023-12-11/2023-12-11-raspios-bookworm-arm64-lite.img.xzxz -c -d 2023-12-11-raspios-bookworm-arm64-lite.img.xz | sudo dd of=/dev/sdX bs=4M status=progressYou may need lsblk command to locate the device name of your SD card.
You can get it as a zip file from the Download ZIP button of the dropdown menu triggered by the Code button on the top.
Or you can use following command
git clone --depth=1 https://github.com/YongBinnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnn/hood.gitFirstly, use lsblk command to check the device name of you SD card,
Then, use following command to ensure the partitions are not mounted (replace sdX with SD card device name)
sudo umount /dev/sdX*Then, use following command to ensure the partitions are not mounted. Correct output is nothing (replace sdX with SD card device name)
mount|grep sdXThen, start to install (replace sdX with SD card device name)
cd hood/scripts
./install.sh target=sdXCommandline options available to the install script:
| Name | Default Value | Description |
|---|---|---|
| usb_tether= | 1 | Share network to computer via USB cable |
| harden_only= | 0 | Only apply hardening parts. Let the target SBC can still be used as a computer. |
| disable_wireless= | 1 | Disable WiFi and Bluetooth. |
| disable_gpu= | 1 | Disable GPU. |
| debian_live | N/A | Install to live debian environment. |
| gpio_shutdown_pin= | 21 | The GPIO pin used for shutdown the computer |
| screen_dtbo= | OMITTED | The path of the dtbo file for the screen used for the computer |
| target= | / | The target root/device to install firewall. |
| wan_port_device_path= | auto-built-in-eth | The path of the device to be used as WAN port. auto-built-in-eth means find built-in Ethernet port automatically. |
Hood firewall now is possible to be installed to debian-based Linux systems. This feature has been tested in the live environment of Parrot OS 6.0.
On boot menu, press 'e' to goto edit prompt, and then add following to the end of the 'linux' line
efi=noruntime module_blacklist=mei,bluetooth,drm,wmi,i2c_smbus,i2c_piix4,parport,cfg80211 ipv6.disable=1 toram=filesystem.squashfs
git clone --depth=1 https://github.com/YongBinnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnn/hood.gitcd hood/scripts
./install.sh debian_liveIf your are using a live environment created by an ISO image, you may want soft-reboot
sudo systemctl soft-rebootIn other situations, a regular reboot would be a better choice.
hood by Bin Yong is licensed under CC BY-NC-ND 4.0