This project was created with only purpose for understanding OAuth 2.0 Grant Flows. (DON'T USE IN PRODUCTION).
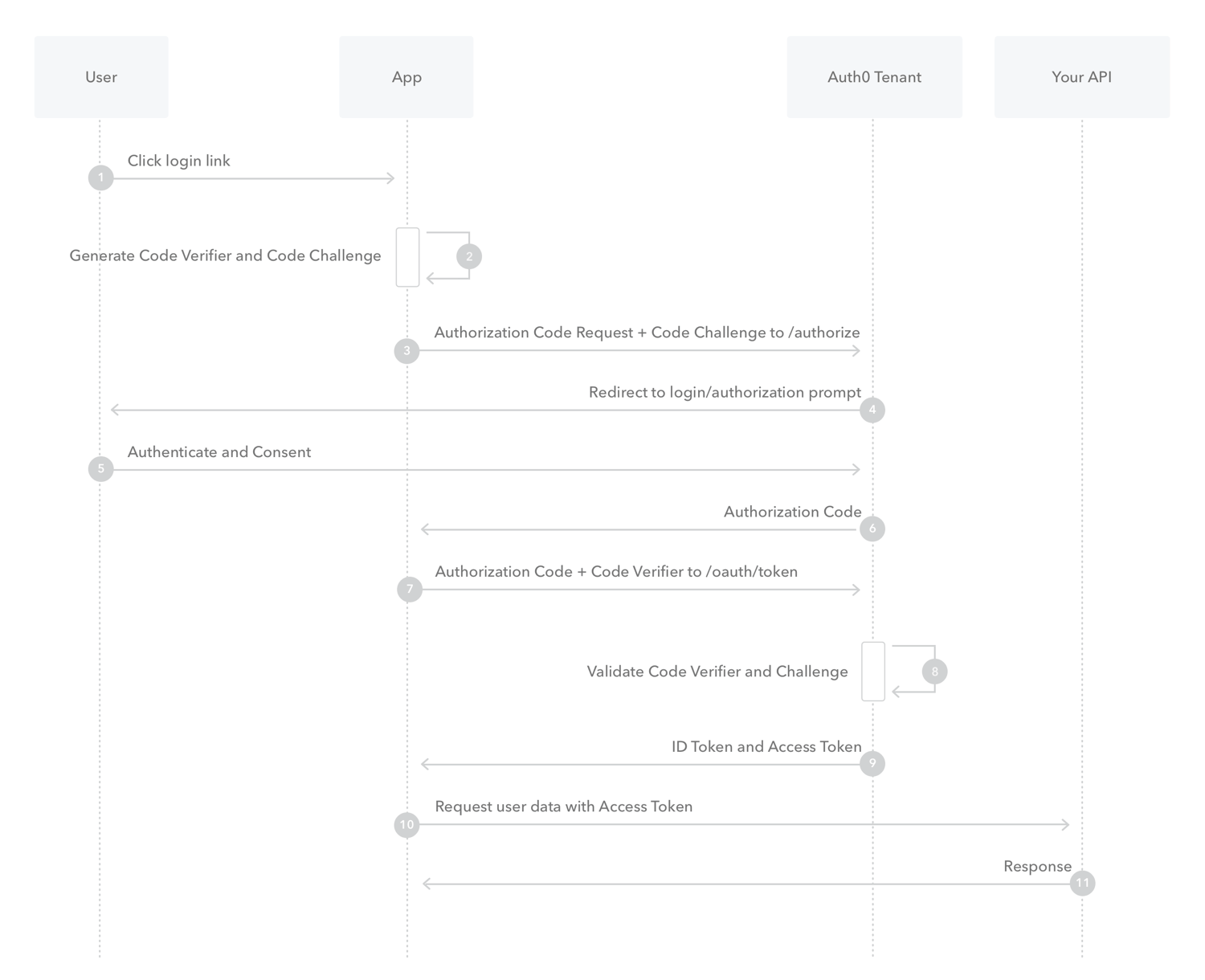
docker-compose upThe PKCE-enhanced Authorization Code Flow introduces a secret created by the calling application that can be verified by the authorization server; this secret is called the Code Verifier. Additionally, the calling app creates a transform value of the Code Verifier called the Code Challenge and sends this value over HTTPS to retrieve an Authorization Code. This way, a malicious attacker can only intercept the Authorization Code, and they cannot exchange it for a token without the Code Verifier.
You can test here: http://localhost:9094/code
Great for flow machine-to-machine (M2M) applications, such as CLIs, daemons, or services running on your back-end, the system authenticates and authorizes the app rather than a user. M2M apps use the Client Credentials Flow, in which they pass along their Client ID and Client Secret to authenticate themselves and get a token.
You can test here: http://localhost:9094/client-credentials
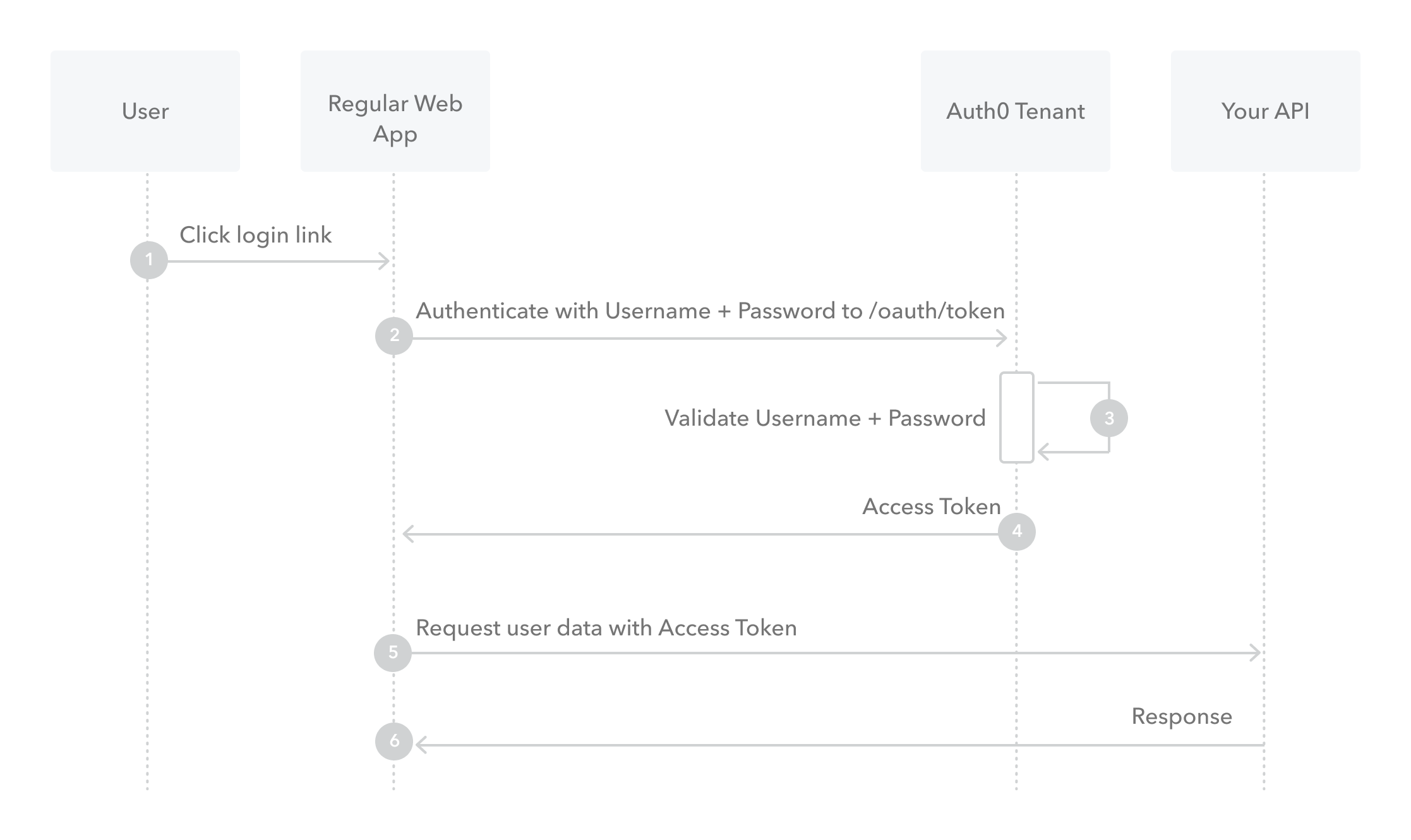
The Password grant type is a way to exchange a user's credentials for an access token. Because the client application has to collect the user's password and send it to the authorization server, it is not recommended that this grant be used at all anymore. (DEPRECATED, It's considered a Legacy Flow)
You can test here: http://localhost:9094/pwd-credentials
An OAuth Refresh Token is a string that the OAuth client can use to get a new access token without the user's interaction.
You can test here: http://localhost:9094/refresh
POST /oauth/token HTTP/1.1
Host: localhost:9094
grant_type=refresh_token
&refresh_token=xxxxxxxxxxx
&client_id=xxxxxxxxxx
&client_secret=xxxxxxxxxx