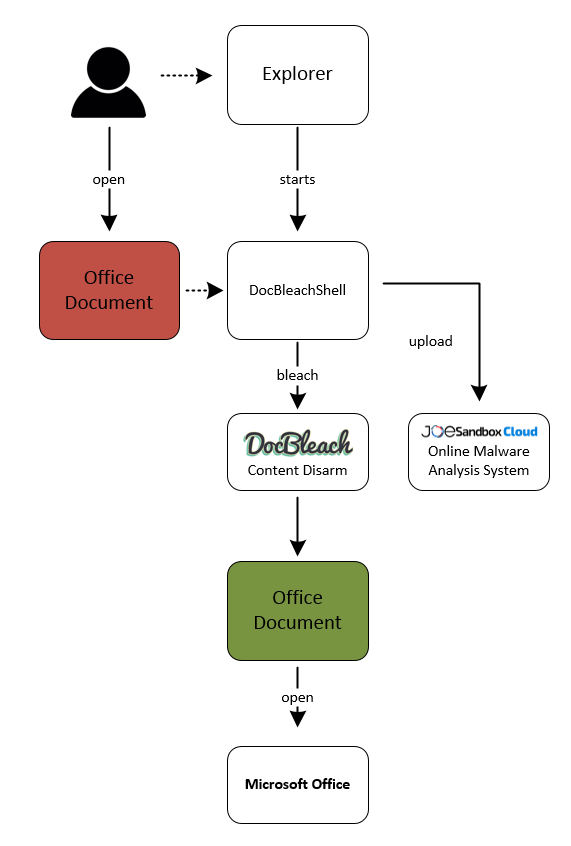
DocBleachShell is the integration of the great DocBleach Content Disarm and Reconstruction tool into the Microsoft Windows Shell Handler.
By using DocBleachShell documents are automatically disarmed before they are opened by Microsoft Word, Excel or Powershell. As a result end users which installed DocBleachShell are protected from exploits and malicious macros. DocBleachShell also comes with a Joe Sandbox Cloud integration. Successfully bleached documents are automatically analyzed by Joe Sandbox Cloud. In Joe Sandbox Cloud users can enable alerts, e.g. automated emails on detection of malicious files. With that CERTs, CIRTS or SOCs are automatically notified if their users where attacked by malicious documents.
DocBleachShell modifies the Microsoft Windows Shell Handler via the HKEY_CLASSES_ROOT\Type\shell\open\command registry key.
Code is developed in C# / .Net 4 and licensed under MIT.
- Latest Microsoft .Net Framework
- Latest Java Runtime Environment, make sure that your Java bin directory is part of the PATH environment variable.
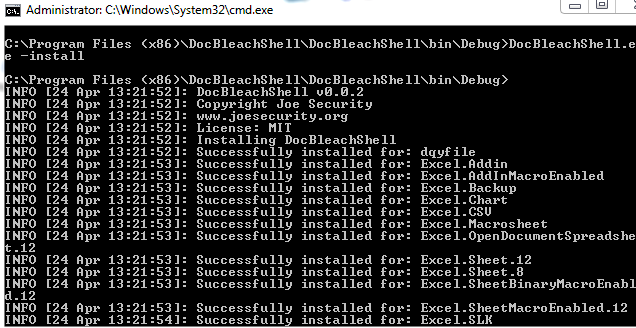
To install DocBleachShell, call DocBleachShell.exe -install from a Administrator shell:
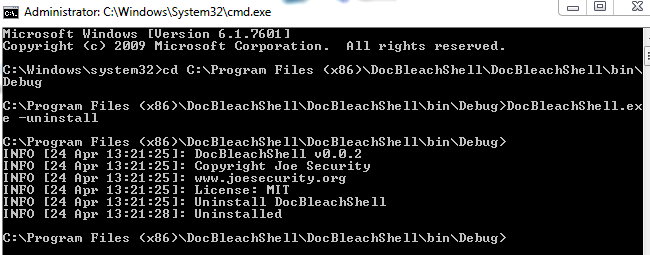
DocBleachShell will search and replace all shell handlers for Word, Excel and Powerpoint. For each registry modification a backup is made to the backup folder. After installation do not move DocBleachShell to any other path. To uninstall DocBleachShell call DocBleachShell.exe -uninstall:
Once installed opening a Office file will start DocBleachShell. DocBleachShell will then call DocBleach. DocBleach will disarm the document. Finally DocBleachShell will start Office to open the disarmed file.
DocBleachShell using Log4net. The log file is located in the main directory and named "DocBleachShell.log".
Configuration of DocBleachShell is controlled via DocBleachShell.exe.config:
<appSettings>
<add key="OnlyBleachInternetFiles" value="true"/>
...
</appSettings>By default only documents downloaded from the Internat are bleached. This is done via NTSF ADS Zone.Identifier check. You can turn of this check and bleach any document. To do so change the config "OnlyBleachInternetFiles" = false.
DocBleachShell includes an integration of Joe Sandbox Cloud. Joe Sandbox Cloud enables to deeply analyze and detect malicious files. The Joe Sandbox Cloud integration can be enabled via DocBleachShell.exe.config, by adding your API Key:
<appSettings>
...
<add key="JoeSandboxCloudAPIKey" value="addyourapikeyhere"/>
</appSettings>Once done DocBleachShell will upload any document which DocBleach has disarm. If the document was save and DocBleach did not do any disarming the document is not uploaded.
Joe Security (@joe4security - webpage)
Thank you to PunKeel for the very cool DocBleach project!