This workshop provides Platform Operators, Application Developers, and Application Operators with hands on experience deploying and securing multi-cloud applications utilizing Tetrate Service Bridge. Included are presentations, demos and hands on labs.
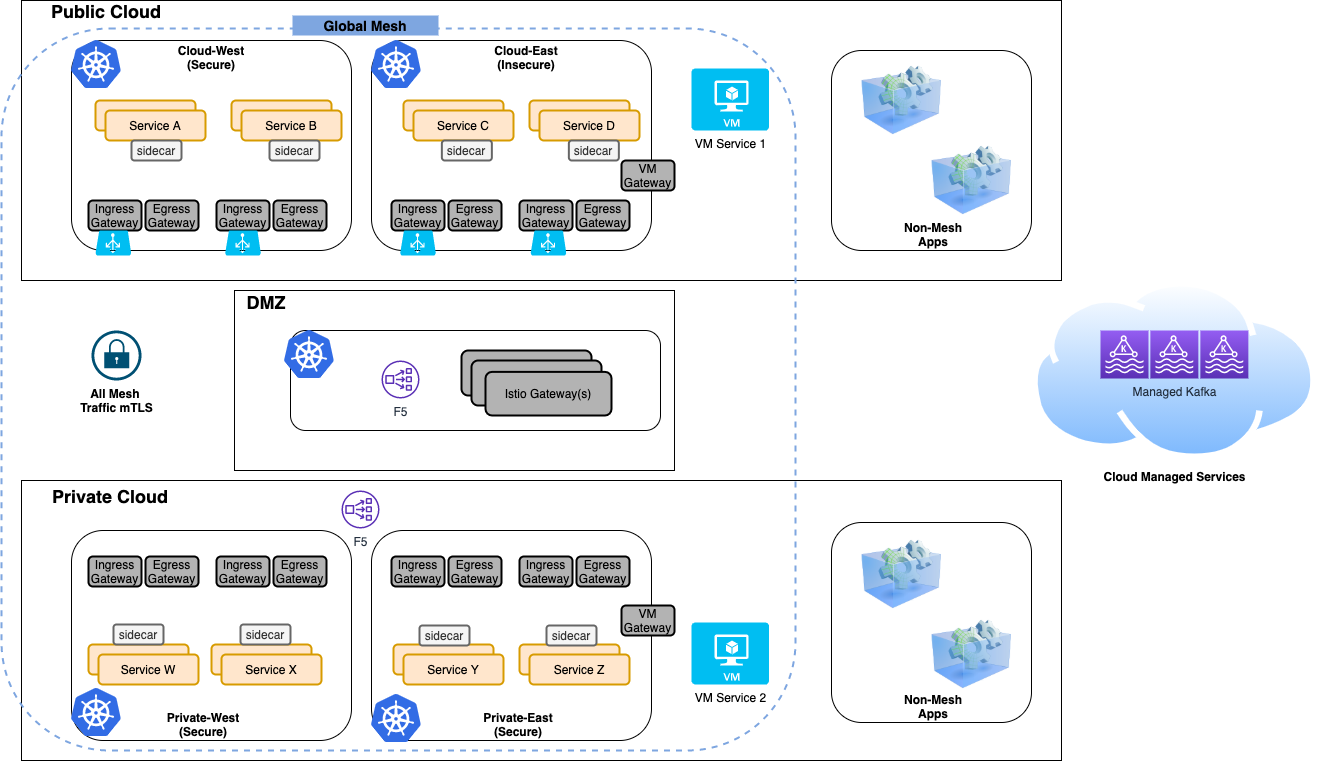
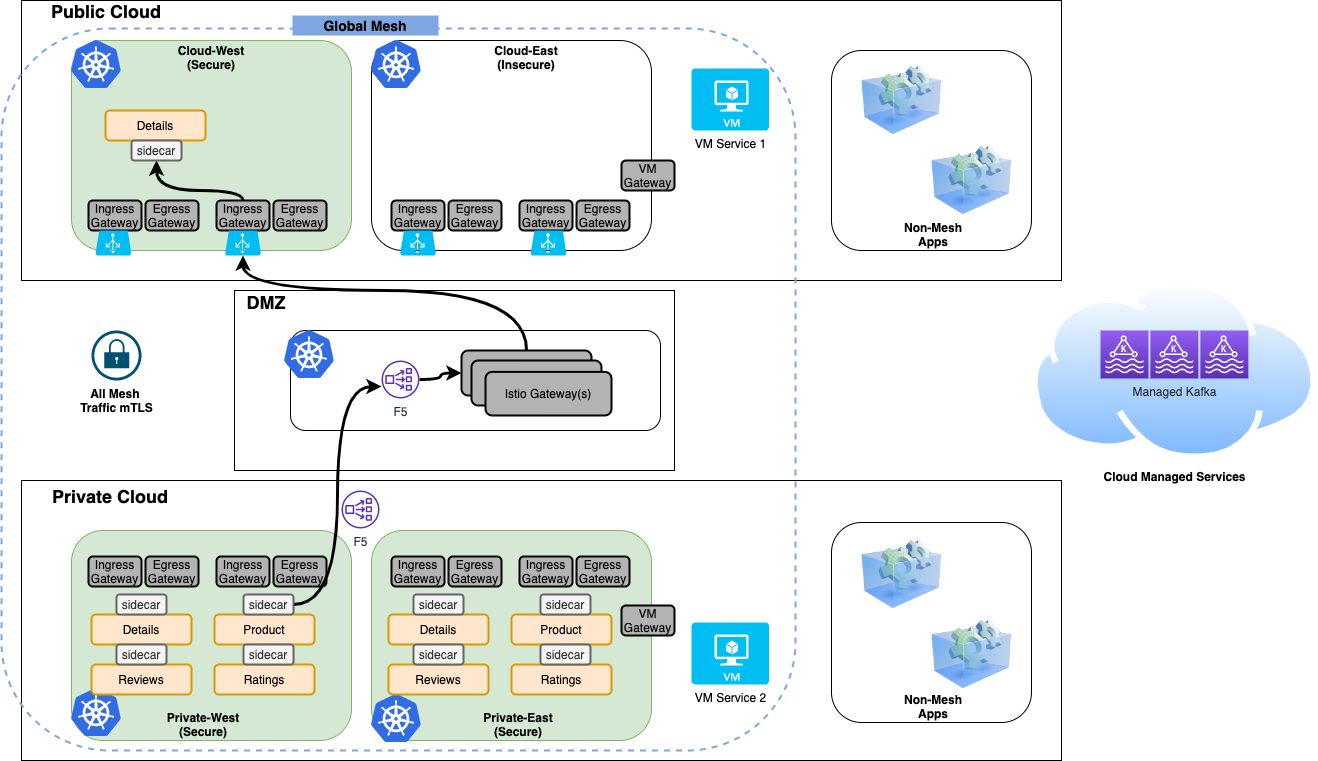
The target state infrastucture architecture is comprised of 5 Kubernetes clusters:
- 2 clusters in the public cloud one deployed in the east region and the other in west region
- 2 clusters on-premises one deployed in an east region and another in west region. Within the "east" region we will add legacy VM workloads to the env.
- One cluster deployed in a "DMZ" that facilitates a controlled point for securing communication traversing public and private clouds.
IMPORTANT: Each new exercise builds upon the preceding lab, so please do not skip around the labs!
- Deploy Applications: Lab
- Setup Multi-Tenancy: Slides Lab
- Application Config: Lab
- Security Policies: Slides Lab
- Legacy VM Workloads: Slides Lab
- Multi-Cloud & Multi-Cluster Traffic Mgmt: Slides Lab
- Envoy Filters: Slides Lab
- Application Debugging: Slides Lab
- User Authorization (JWT): Lab
The majority of the workshop will be executed via a jumpbox that has all the prerequisite CLIs installed. Using the shared google doc provided by, checkout a jumpbox by adding your name to the sheet in the Reserved Workshop User column. This shared document has TSB user/pwd and IP address for your jumpbox.
- Access jumpbox using the private key provided by tetrate:
Please run the follwoing command to change permissions for file.
chmod 400 abz.pemssh -i abz.pem ec2-user@<JUMPBOX IP ADDRESS>- Throughout the workshop you will be required to have an environment variable set in your jumpbox session named
PREFIX. This will be used to ensure your various Kubernetes objects and TSB objects have unique names. The PREFIX assigned to you is found in the shared Google docs in thePrefixcolumn of the jumpbox you checked out. Export this env var:
export PREFIX=<YOUR JUIMPBOX PREFIX>- All labs will assume you have changed directories to the workshop git directory, which has already been checked out onto the jumpbox. This is found in the
dmz-workshopdirectory. Also, it wouldn't hurt to doublecheck that you have the latest code checked out, just in case there are last minute changes that were committed after the jumpbox was created.
cd ~/dmz-workshop
git pull- The jumpbox should already be logged into each kubernetes cluster. If you receive a message that you are not logged in you can execute the 2 helper scripts on the jumpbox that will log you in.
~/login-cloud.sh
~/login-openshift.sh
- During your workshop you will be utilizing the TCTL CLI. If you receive a message that you are not logged in you can execute the helper script on the jumpbox that will log you in.
~/login-tctl.sh
- Each
kubectlcommand will contain a--contextflag that will direct the API request to the correct kubernetes server. However, at times you may want to change your active kubernetes context to a specific cluster in order to execute ad-hockubectlcommands. The jumpbox haskubectxinstalled to facilitate this. You can list contexts by issuing the commandkubectxand you can change you context with the commandkubectx <CONTEXT NAME>. Valid contexts arepublic-east,public-west,private-east,private-west, anddmz.
During this workshop we will be modeling 3 different applications that allow for various architecture and security patterns that span Multi-Cluster and Multi-Cloud.
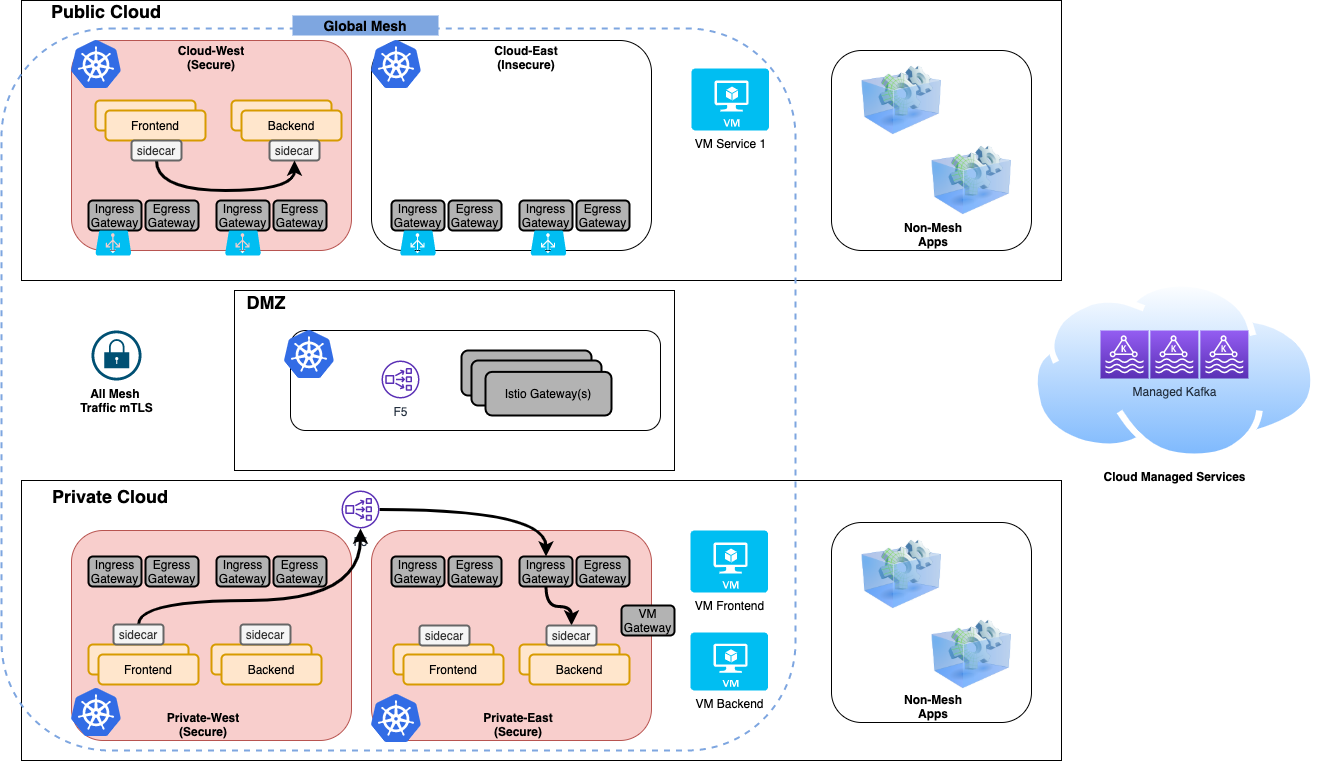
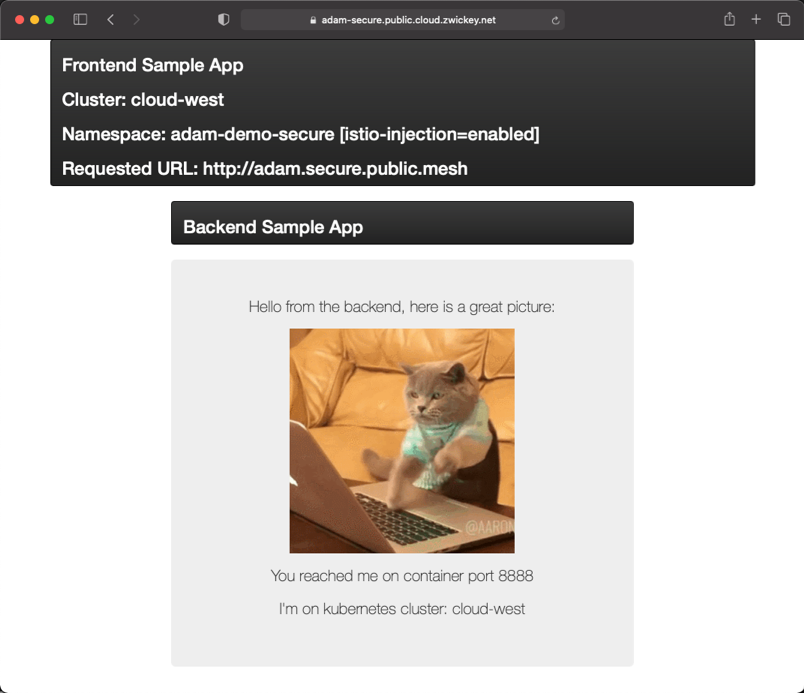
A simple frontend and backend application that allows simple testing of mesh networking and security. This application spans the Public Cloud West cluster and both on-premises clusters. This application also has VM versions of the services running in the private east region.
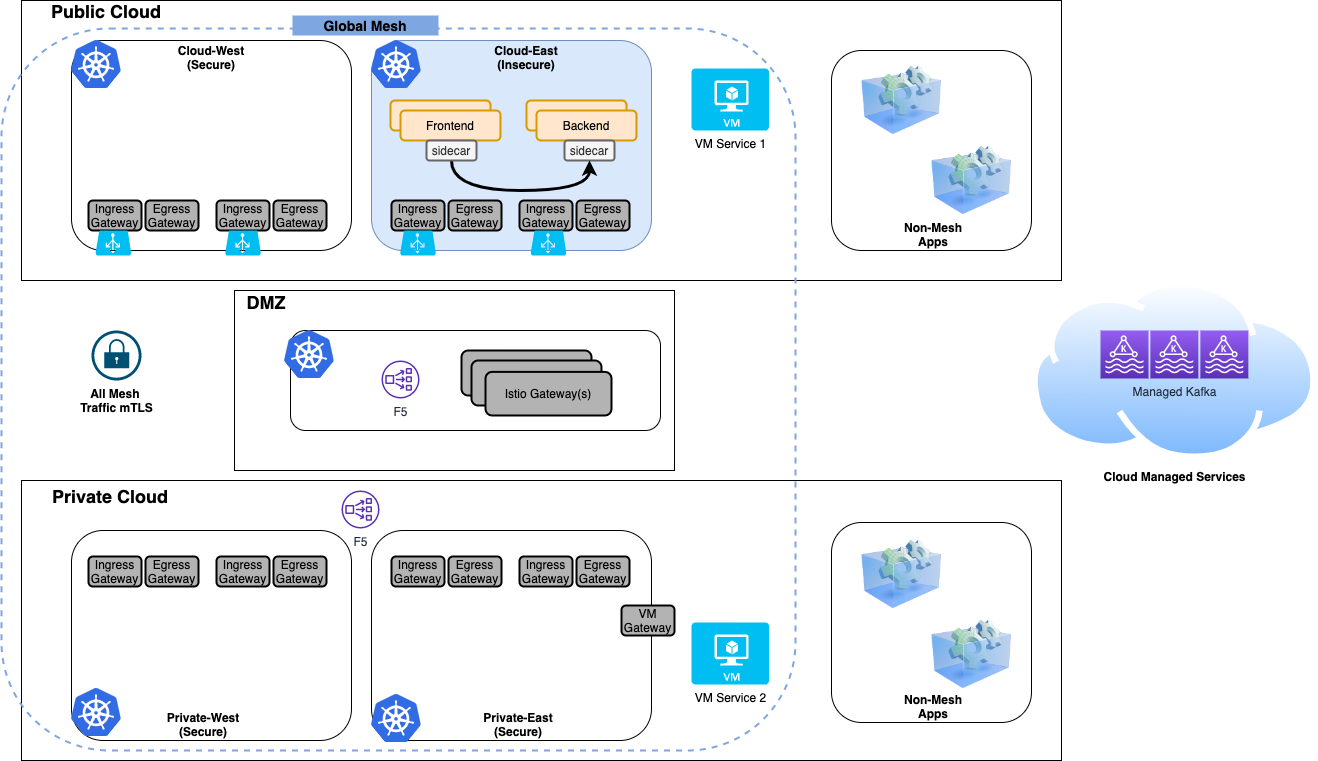
Identical application to the Secure Application, except it is only deployed into the Public Cloud East cluster, which we will utilize as the Insecure Cluster.
This is the canonical Istio demo application, Bookinfo. The microservice application displays information about a book, similar to a single catalog entry of an online book store. This application spans is fully deployed to both on-premises clusters In this manner, we can demonstrate advanced routing and service discovery patterns.