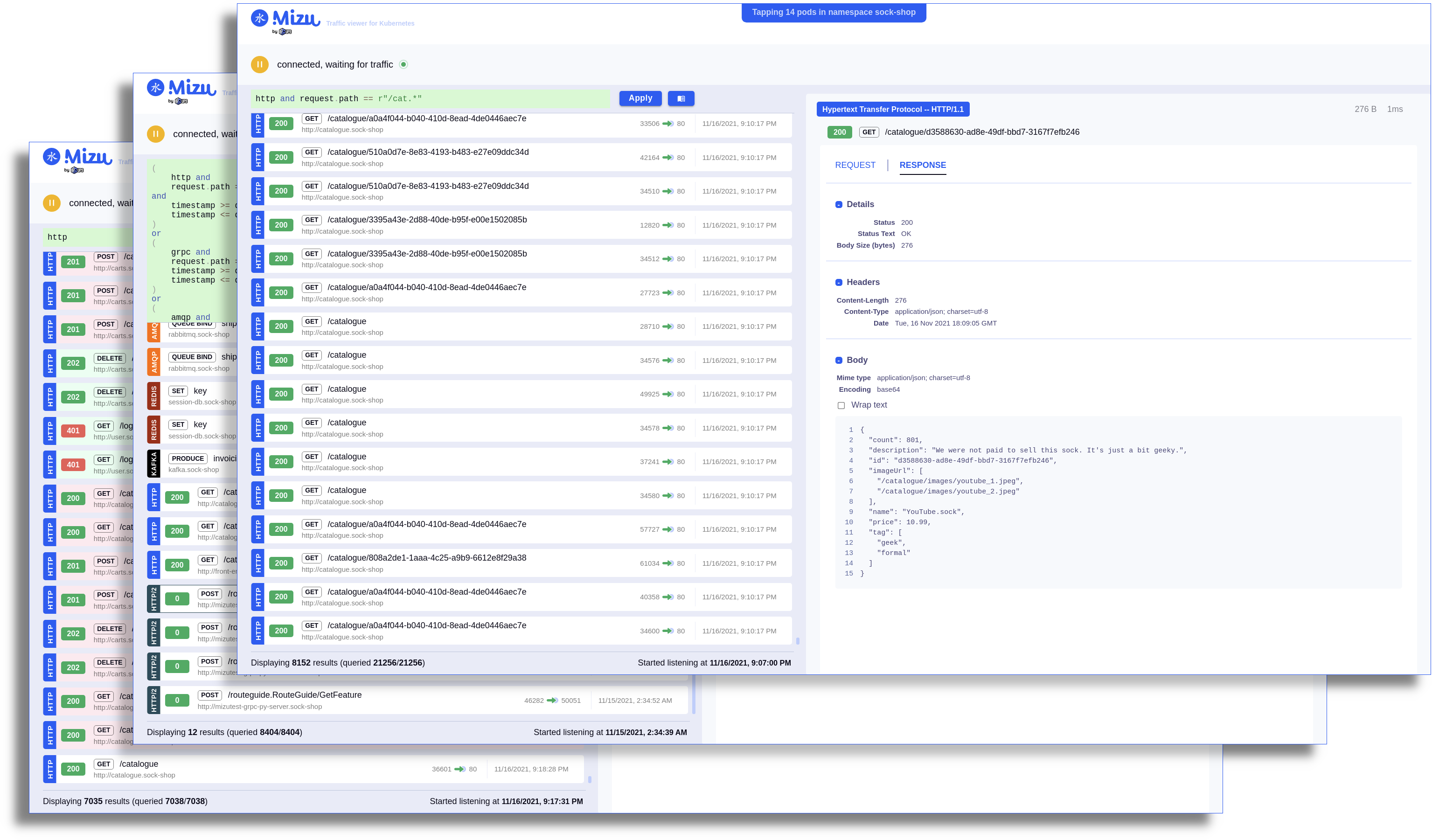
A simple-yet-powerful API traffic viewer for Kubernetes enabling you to view all API communication between microservices to help your debug and troubleshoot regressions.
Think TCPDump and Wireshark re-invented for Kubernetes.
- Simple and powerful CLI
- Monitoring network traffic in real-time. Supported protocols:
- HTTP/1.1 (REST, etc.)
- HTTP/2 (gRPC)
- AMQP (RabbitMQ, Apache Qpid, etc.)
- Apache Kafka
- Redis
- Works with Kubernetes APIs. No installation or code instrumentation
- Rich filtering
A Kubernetes server version of 1.16.0 or higher is required.
Download Mizu for your platform and operating system
- for MacOS - Intel
curl -Lo mizu \
https://github.com/up9inc/mizu/releases/latest/download/mizu_darwin_amd64 \
&& chmod 755 mizu
- for Linux - Intel 64bit
curl -Lo mizu \
https://github.com/up9inc/mizu/releases/latest/download/mizu_linux_amd64 \
&& chmod 755 mizu
SHA256 checksums are available on the Releases page
Pick one from the Releases page
- Find pods you'd like to tap to in your Kubernetes cluster
- Run
mizu tapormizu tap PODNAME - Open browser on
http://localhost:8899or as instructed in the CLI - Watch the API traffic flowing
- Type ^C to stop
Run mizu help for usage options
To tap all pods in current namespace -
$ kubectl get pods
NAME READY STATUS RESTARTS AGE
carts-66c77f5fbb-fq65r 2/2 Running 0 20m
catalogue-5f4cb7cf5-7zrmn 2/2 Running 0 20m
front-end-649fc5fd6-kqbtn 2/2 Running 0 20m
..
$ mizu tap
+carts-66c77f5fbb-fq65r
+catalogue-5f4cb7cf5-7zrmn
+front-end-649fc5fd6-kqbtn
Web interface is now available at http://localhost:8899
^C
$ kubectl get pods
NAME READY STATUS RESTARTS AGE
front-end-649fc5fd6-kqbtn 2/2 Running 0 7m
..
$ mizu tap front-end-649fc5fd6-kqbtn
+front-end-649fc5fd6-kqbtn
Web interface is now available at http://localhost:8899
^C $ kubectl get pods
NAME READY STATUS RESTARTS AGE
carts-66c77f5fbb-fq65r 2/2 Running 0 20m
catalogue-5f4cb7cf5-7zrmn 2/2 Running 0 20m
front-end-649fc5fd6-kqbtn 2/2 Running 0 20m
..
$ mizu tap "^ca.*"
+carts-66c77f5fbb-fq65r
+catalogue-5f4cb7cf5-7zrmn
Web interface is now available at http://localhost:8899
^CMizu can optionally work with a config file that can be provided as a CLI argument (using --set config-path=<PATH>) or if not provided, will be stored at ${HOME}/.mizu/config.yaml
In case of partial configuration defined, all other fields will be used with defaults
You can always override the defaults or config file with CLI flags
To get the default config params run mizu config
To generate a new config file with default values use mizu config -r
It is possible to change the kubeconfig path using KUBECONFIG environment variable or the command like flag
with --set kube-config-path=<PATH>.
If both are not set - Mizu assumes that configuration is at ${HOME}/.kube/config
Some users have permission to only manage resources in one particular namespace assigned to them
By default mizu tap creates a new namespace mizu for all of its Kubernetes resources. In order to instead install
Mizu in an existing namespace, set the mizu-resources-namespace config option
If mizu-resources-namespace is set to a value other than the default mizu, Mizu will operate in a
Namespace-Restricted mode. It will only tap pods in mizu-resources-namespace. This way Mizu only requires permissions
to the namespace set by mizu-resources-namespace. The user must set the tapped namespace to the same namespace by
using the --namespace flag or by setting tap.namespaces in the config file
Setting mizu-resources-namespace=mizu resets Mizu to its default behavior
For detailed list of k8s permissions see PERMISSIONS document
User-agent filtering (like health checks) - can be configured using command-line options:
$ mizu tap "^ca.*" --set tap.ignored-user-agents=kube-probe --set tap.ignored-user-agents=prometheus
+carts-66c77f5fbb-fq65r
+catalogue-5f4cb7cf5-7zrmn
Web interface is now available at http://localhost:8899
^C
Any request that contains User-Agent header with one of the specified values (kube-probe or prometheus) will not be captured
This feature allows you to define set of simple rules, and test the traffic against them. Such validation may test response for specific JSON fields, headers, etc.
Please see TRAFFIC RULES page for more details and syntax.
An OAS/Swagger file can contain schemas under parameters and responses fields. With --contract catalogue.yaml
CLI option, you can pass your API description to Mizu and the traffic will automatically be validated
against the contracts.
Please see CONTRACT MONITORING page for more details and syntax.
By default, mizu will be accessible via local host: 'http://localhost:8899', it is possible to change the host, for
instance, to '0.0.0.0' which can grant access via machine IP address. This setting can be changed via command line
flag --set tap.proxy-host=<value> or via config file:
tap proxy-host: 0.0.0.0 and when changed it will support accessing by IP
Mizu can be run detached from the cli using the install command: mizu install. This type of mizu instance will run
indefinitely in the cluster.
For more information please refer to INSTALL STANDALONE