Windows Kernel Explorer (you can simply call it as "WKE") is a free but powerful Windows kernel research tool. It supports from Windows XP to Windows 10, 32-bit and 64-bit. Compare to popular tools (such as WIN64AST and PCHunter), WKE is a highly customizable tool and it can run on the latest Windows 10 without updating binary files.
WKE will automatically download required symbol files if no native support for current system, 90% of the features will work after this step. For some needed data that doesn't exist in symbol files, WKE will try to get them from the DAT file (so, when new Windows 10 releases, I will upload the newest DAT file to GitHub). If there is no internet access for WKE, 50% of the features will still work. Currently, native support is available from Windows XP to Windows 10 RS3 (16299), RS4 and RS5 are fully supported by parsing symbol files and DAT file.
You can customize WKE by editing the configuration file. Currently, you can set the device name and symbolic link name of driver, and altitude of filter. You can also enable kernel-mode and user-mode characteristics randomization to avoid being detected by malware. If you rename the EXE file of WKE, then you need to rename SYS/DAT/INI files together with the same name.
Due to I don't have a digital certificate, so I have to use a leaked digital certificate from HT SRL to sign driver of WKE. I use "DSEFIX" as an alternative solution to load driver, if WKE unable to load driver, you can try to launch WKE with "WKE_dsefix.bat".
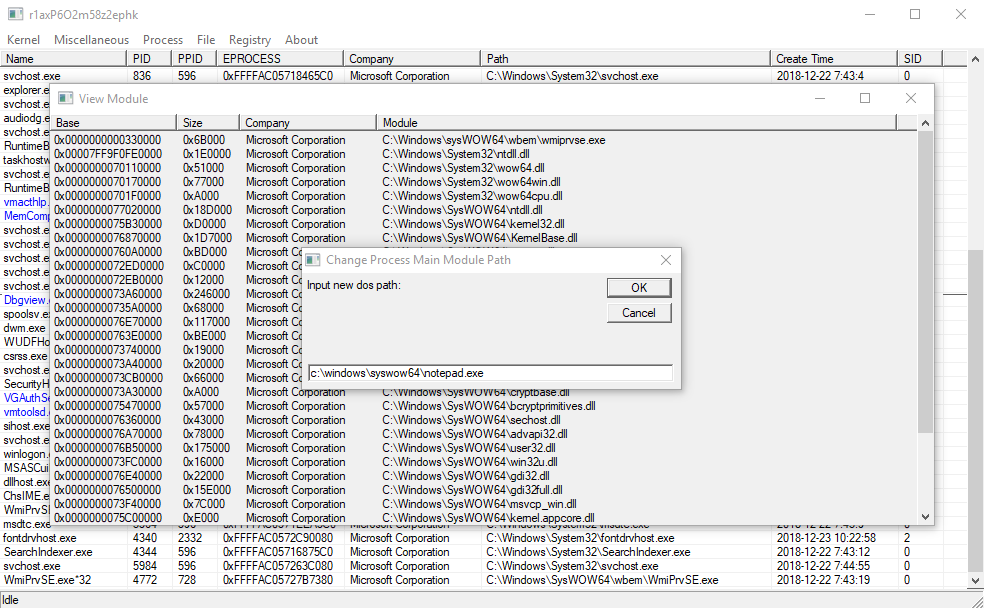
- Process management (Module, Thread, Handle, Memory, Window, Windows Hook, etc.)
- File management
- Registry management
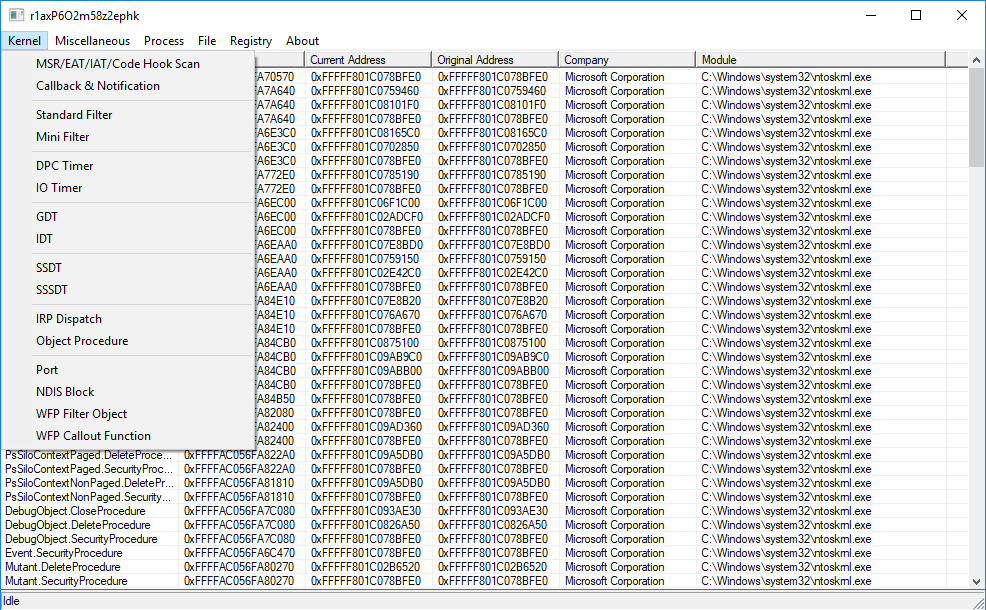
- Kernel-mode callback, filter, timer, NDIS blocks and WFP stuffs management
- Kernel-mode hook scanning (MSR, EAT, IAT, CODE PATCH, SSDT, SSSDT, IDT, IRP, OBJECT)
- User-mode hook scanning (Kernel Callback Table, EAT, IAT, CODE PATCH)
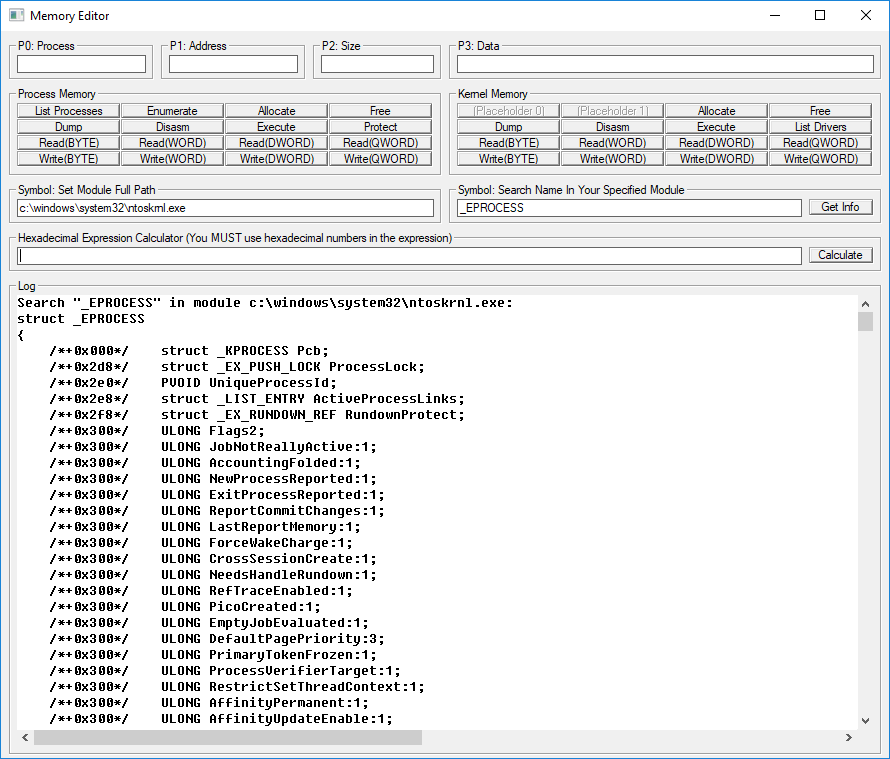
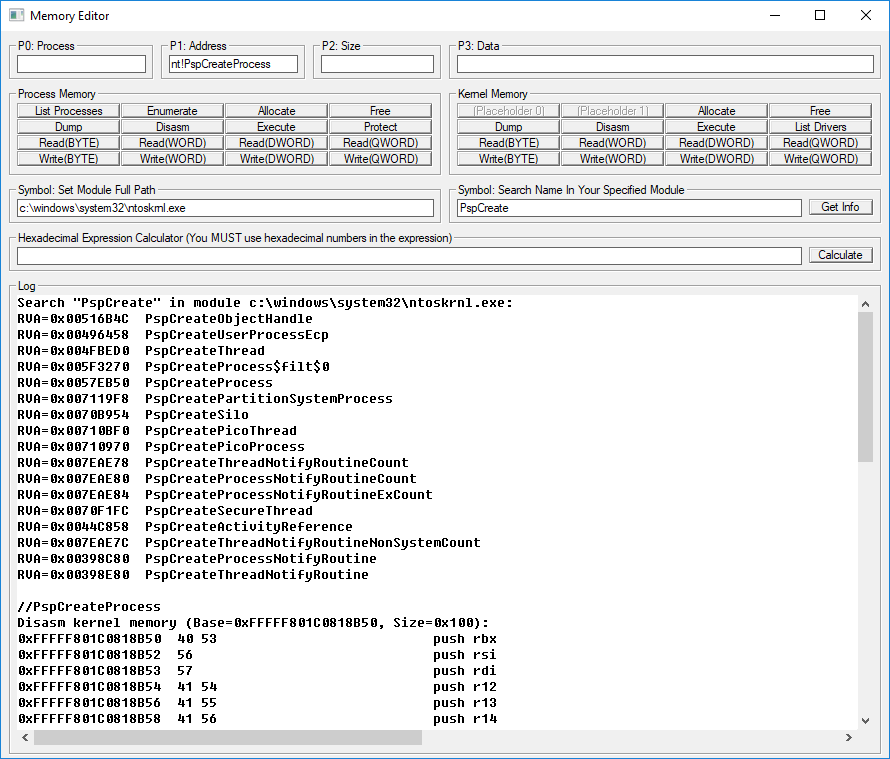
- Memory editor and symbol parser (it looks like a simplified version of WINDBG)
- Protect process, hide/protect/redirect file or directory, protect registry and falsify registry data
- Path modification for driver, process and process module
- Enable/disable some obnoxious Windows components
This is the first public version.
- Team of WIN64AST (I referenced the UI design and many features of this software)
- Team of PCHunter (I referenced some features of this software)
- Team of ProcessHacker (I studied the source code of this software, but I didn’t use it in my project)
- Author of DSEFIX (I use it as an alternative solution to load driver)
Please write EMAIL in English or German, I only reply to EMAILs that I am interested in.