modules: spring-boot-starter-security, pring-boot-starter-oauth2-resource-server, spring-boot-starter-oauth2-client
- Start Red Hat Single Sign-On (keycloak)
- Create a new master realm admin user
- Create a new realm: sample
- Under sample realm, create a new user (usr/pwd): john/doe
- Create new sample realm clients:
- sample-api type: bearer-only
- sample-web type: public
- Create new client roles (for both clients):
- PRODUCT_VIEWER
- PRODUCT_MAINTAINER
- Assign role mappings for user john with recently created client roles
- Start springboot app on port 8070
rm -fr target ; mvn clean package
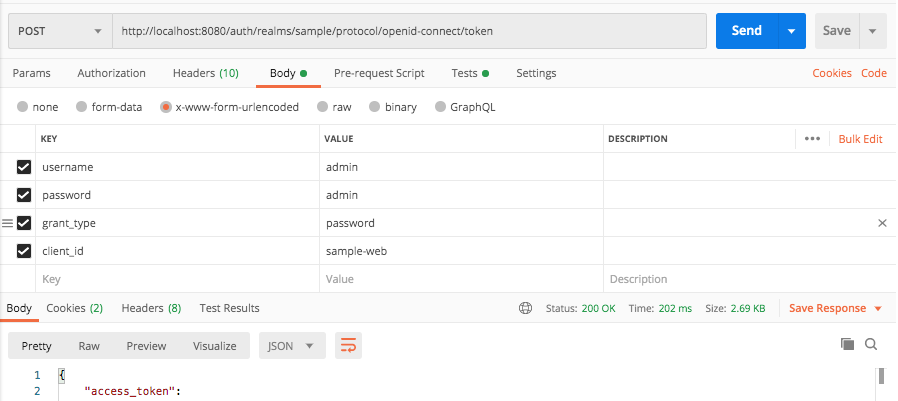
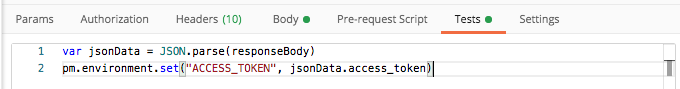
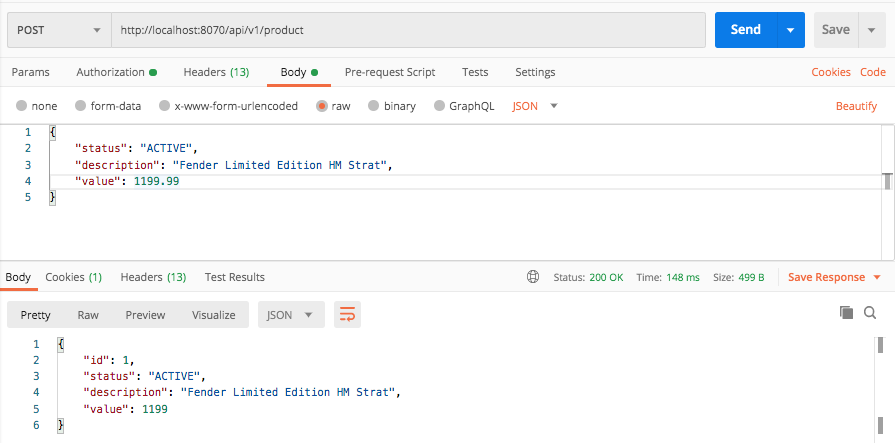
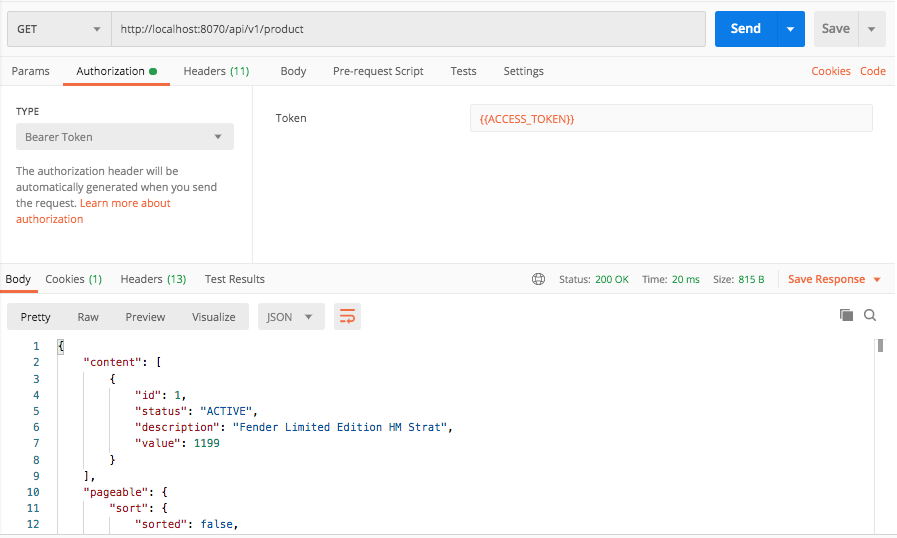
java -jar target/springboot-open-id-connect-sample-1.0-SNAPSHOT.jarTEST w/ postman:
springboot2+spring_security+keycloak.postman_collection.json
http://localhost:8070/api-docs (json)
http://localhost:8070/api-docs.yaml
https://github.com/thomasdarimont/awesome-keycloak
https://docs.spring.io/spring-security/site/docs/current/reference/html5/
https://github.com/Baeldung/spring-security-oauth
https://www.baeldung.com/spring-security-oauth-jwt
https://github.com/hotire/spring-security-basic
https://stackoverflow.com/questions/58205510/spring-security-mapping-oauth2-claims-with-roles-to-secure-resource-server-endp
https://developers.redhat.com/blog/2020/01/29/api-login-and-jwt-token-generation-using-keycloak
https://access.redhat.com/products/red-hat-single-sign-on
https://www.baeldung.com/spring-rest-openapi-documentation