Welcome to the Microsoft Defender for Endpoint PowerShell module!
This module is a collection of easy-to-use cmdlets and functions designed to make it easy to interface with the Microsoft Defender for Endpoint API.
I created this PowerShell module for MDATP for the following reasons:
- Advance my PowerShell skills
- Provide an easy way to interact with MDE through PowerShell because I prefer automation over manual tasks
- Windows PowerShell 5.1 (Testing for PowerShell 7 is in progress)
- have configured authorization for access by registering an application in AzureAD
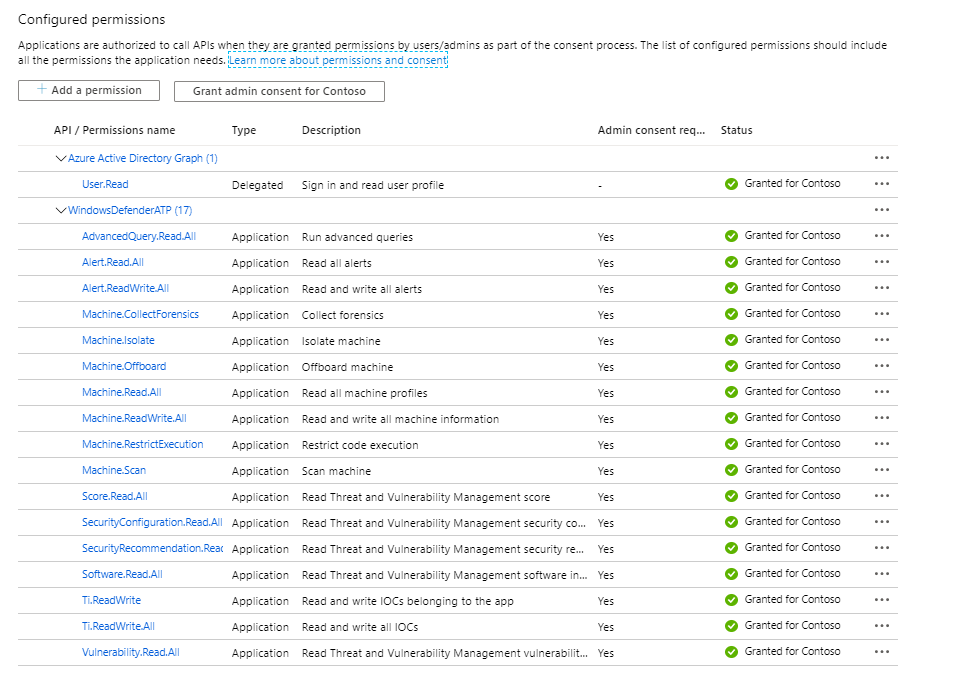
Below is an example of the App Permissions that you must grant. I will provide more details soon about the individual cmdlets and the permissions required
To get started with the module, open your PowerShell terminal and install the module from the PSGallery by running this simple command:
Install-Module PSMDATP -Scope CurrentUserWhen you have installed the module and registered the App in AzureAD, you will find a file TEMPLATE_PoshMTPconfig.json in the Module folder. Rename this file to PoshMTPConfig.json and enter your API settings. Then copy the file in the root of the Module folder.
Example:
"C:\Users\User1\Documents\WindowsPowerShell\Modules\PSMDATP"
───PSMDATP
│ │ PoshMTPconfig.json
│ │
│ └───0.0.2
│ PSMDATP.psd1
│ PSMDATP.psm1
│ TEMPLATE_PoshMTPconfig.jsonAt present the PSMDATP PowerShell module only requires the API_MDATP information
{
"API_MDATP": {
"AppName": "WindowsDefenderATPPSMDATP",
"OAuthUri": "https://login.windows.net/<YOUR TENANT ID>/oauth2/token",
"ClientID": "CLIENT ID",
"ClientSecret": "<CLIENT SECRET>"
},
"API_MSGRAPH": {
"AppName": "xMSGraph",
"OAuthUri": "https://login.windows.net/<YOUR TENANT ID>/oauth2/token",
"ClientID": "<CLIENT ID>",
"ClientSecret": "<CLIENT SECRET>"
}
}I am going to assume that you are familiar with MDATP as such and understand the consequences of triggering actions on devices. Where applicable the cmdlets support the use the -whatif parameter. Think before pressing the key!
Let's first take a look at the cmdlets included in the PSMDATP Module
get-command -Module PSMDATP | Select NameYou will see something like this
Add-MDATPDeviceTag
Add-MDATPIndicator
Get-MDATPAlert
Get-MDATPCollectionPackageUri
Get-MDATPDevice
Get-MDATPDeviceAction
Get-MDATPDeviceTag
Get-MDATPIndicator
Get-MDATPInvestigation
Get-MDATPQuery
Get-MDATPTvmRecommendation
Get-MDATPTvmVulnerability
Get-MDATPEndpointStatus
Remove-MDATPDevice
Remove-MDATPDeviceTag
Remove-MDATPIndicator
Set-MDATPAlert
Start-MDATPAppRestriction
Start-MDATPAVScan
Start-MDATPInvestigation
Start-MDATPInvestigationPackageCollection
Start-MDATPIsolation
Stop-MDATPAppRestriction
Stop-MDATPIsolation
For more details about the cmdlets included in this module check out the cmdlets documentation page
Run the following command to retrieve alerts from the past 30 days
Get-MDATPAlert -Severity HighRun the following command to list all MDATP registered devices
Get-MDATPDevice -AllIf you have an idea or want to contribute to this project please submit a suggestion
Alex Verboon Twitter
Dan Lacher Twitter
| Version | Date | Notes |
|---|---|---|
| 0.0.1 | 15.04.2020 | Initial Release |
| 0.0.2 | 03.05.2020 | Added Add-MDATPIndicator and Remove-MDATPIndictor cmdlets |
| 1.0.0 | 18.07.2020 | Added Get-MDATPTvmRecommendation and Get-MDATPTvmVulnerability |
| cmdlets, updated the API uri for the Get-MDATPAlerts cmdlet | ||
| 1.1.0 | 22.12.2020 | Added Set-MDATPAlert and Get-MDATPEndpointStatus |
| 1.1.1 | 22.11.2022 | Added generateAlert flag to Add-MDATPIndicator |
I have the following on my to-do list:
- A better solution to store the API configuration in a more secure place
Add cmdlets for TVMadded in version 1.0.0Add cmdlets to manage custom indicatorsadded in version 0.0.2- Add more query templates for advanced hunting
- Create more Module related Pester tests
I used Catesta for this project