English | 简体中文
KubeSkoop is a kubernetes networking diagnose tool for different CNI plug-ins and IAAS providers. KubeSkoop automatic construct network traffic graph of Pod in the Kubernetes cluster, monitoring and analysis of the kernel's critical path by eBPF, to resolve most of Kubernetes cluster network problems.
- Diagnose in-cluster traffic between Pod,Service,Node and Ingress/Egress Traffic.
- Cover whole linux network stack: Socket,Bridge,Veth,Netfilter,sysctls…
- Support IaaS network probe for cloud providers.
- eBPF seamless kernel monitor
- CO-RE scripts on series kernel by BTF
- export metrics to standard Prometheus metric API
- support dozens of anomy scenes recognition
- export anomy event to Grafana Loki or Web Console
- Integrating all capabilities of KubeSkoop, provides network diagnosis, event monitoring, packet capturing, latency detection, etc.
You can view the full documentation from the KubeSkoop.io.
You can quickly deploy KubeSkoop, Prometheus, Grafana and Loki to your cluster via skoopbundle.yaml.
kubectl apply -f https://raw.githubusercontent.com/alibaba/kubeskoop/main/deploy/skoopbundle.yamlNote: skoopbundle.yaml starts with the minimum number of replicas and default configurations, which is not suitable for production environments.
When installation is done, you can acess the KubeSkoop Web Console by service webconsole.
kubectl get svc -n kubeskoop webconsoleYou may need a Nodeport or LoadBalancer to acess from outside of the cluster.
Default username is admin, and password is kubeskoop.
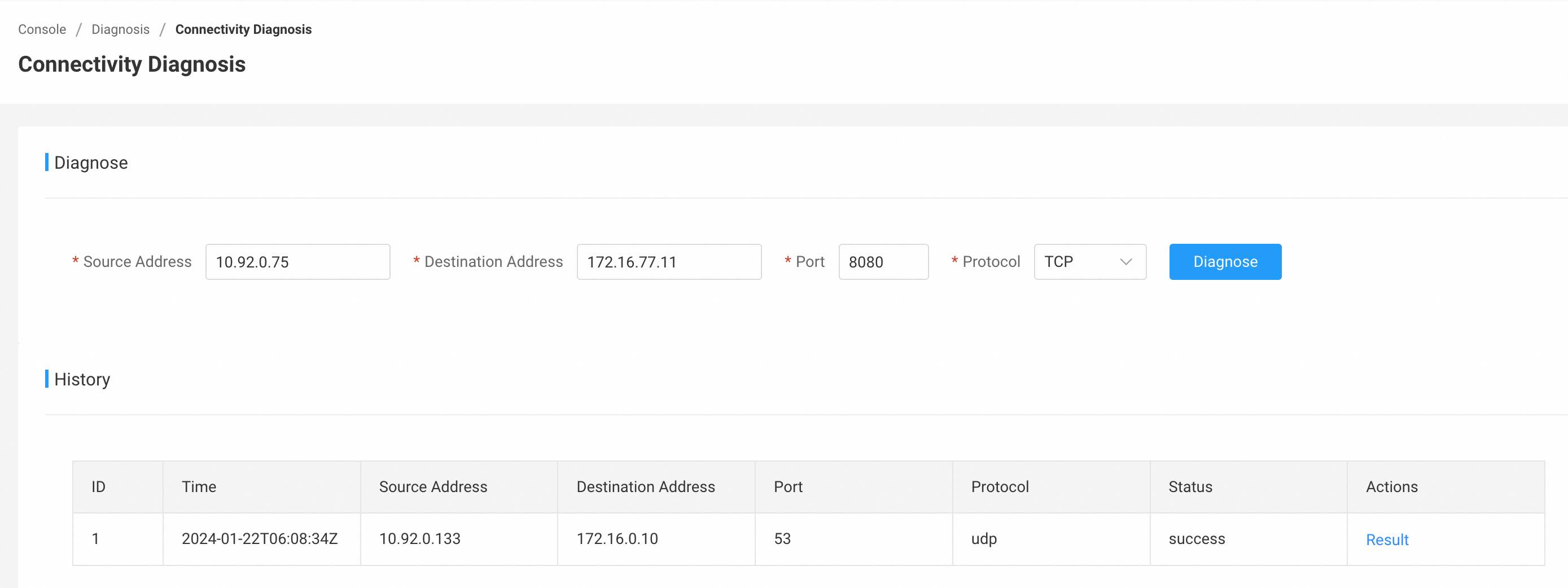
Connectivity diagnosis can be submitted through the web console.
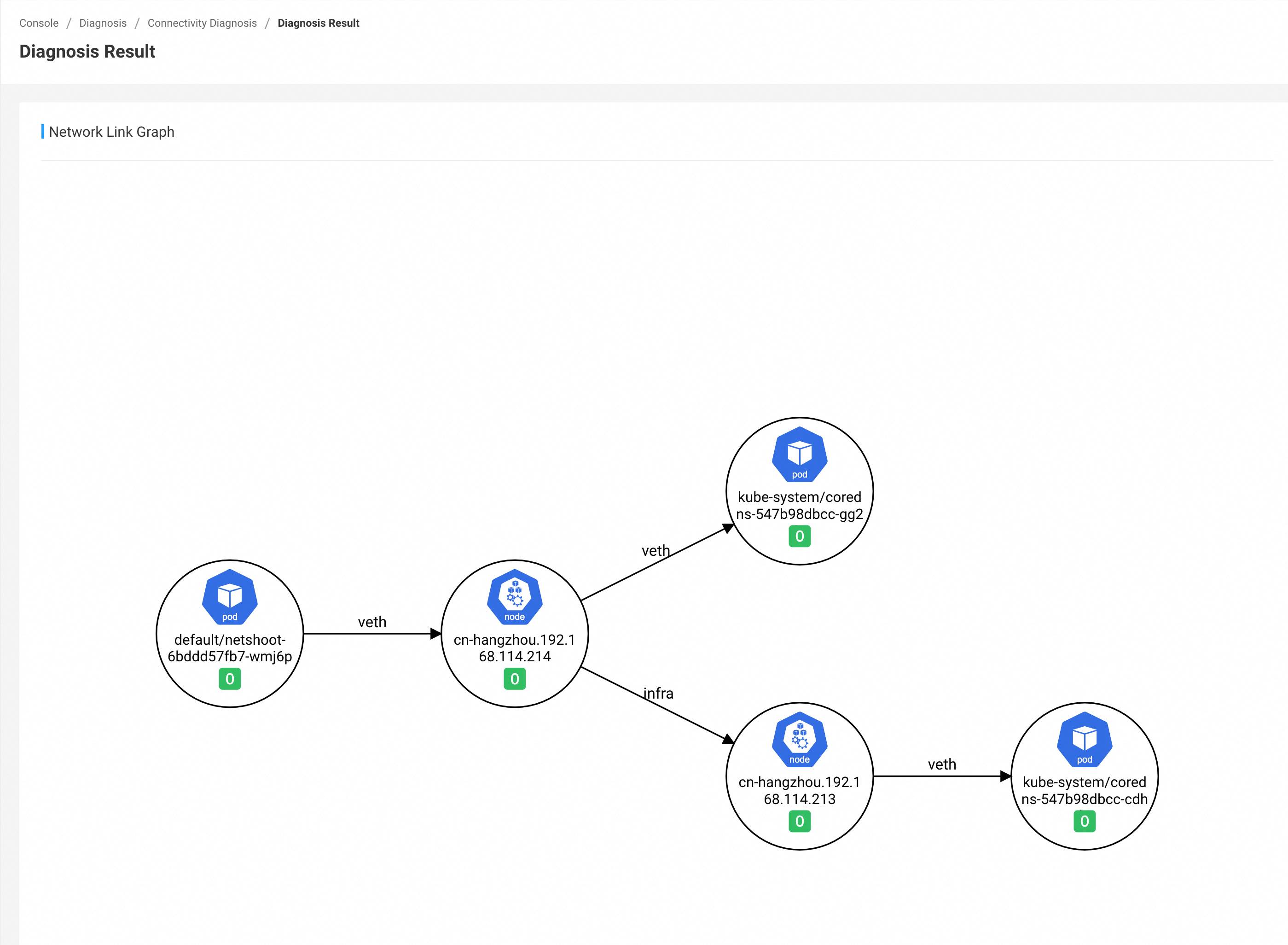
Under Diagnosis - Connectivity Diagnosis, you can enter the source address, destination address, port, and protocol for diagnosis, and click Diagnose to submit the diagnosis. After the diagnosis is complete, you can see the result in the history list.
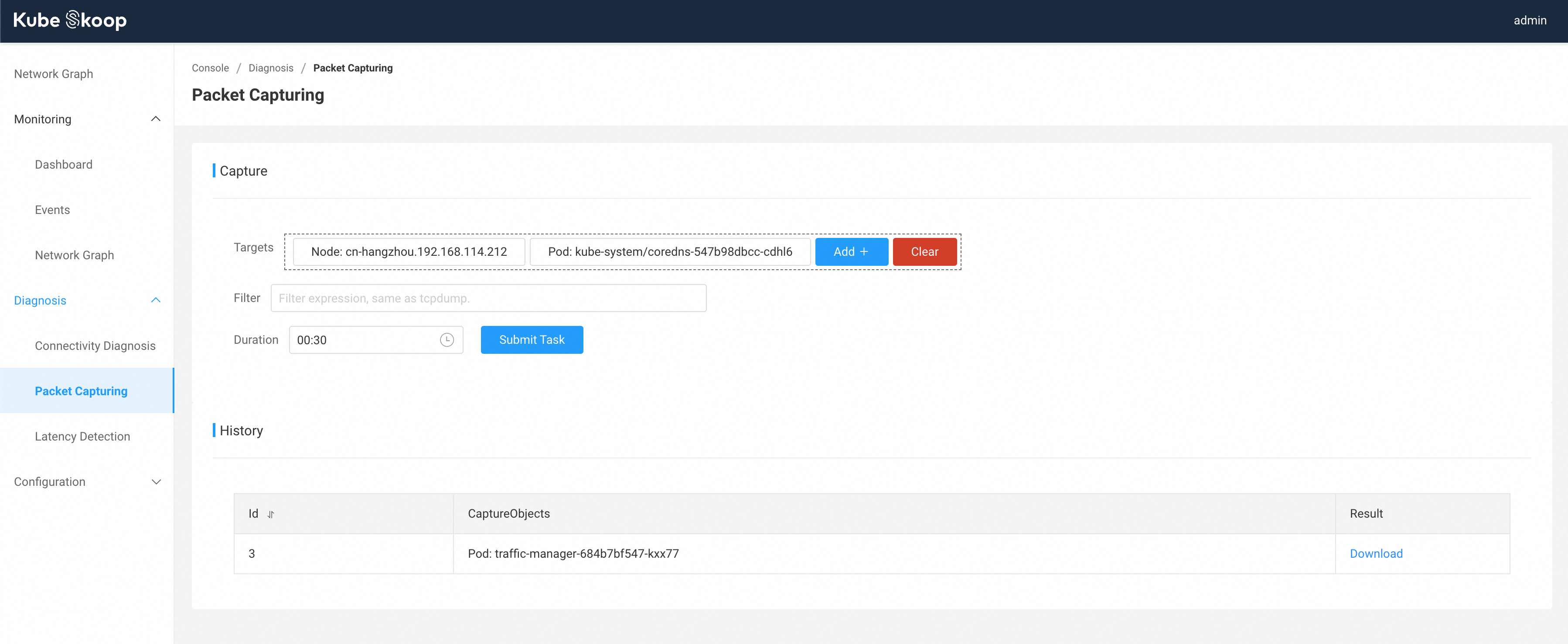
Under Diagnosis - Packet Capturing,you can perform packet capturing for node/pod in the cluster.
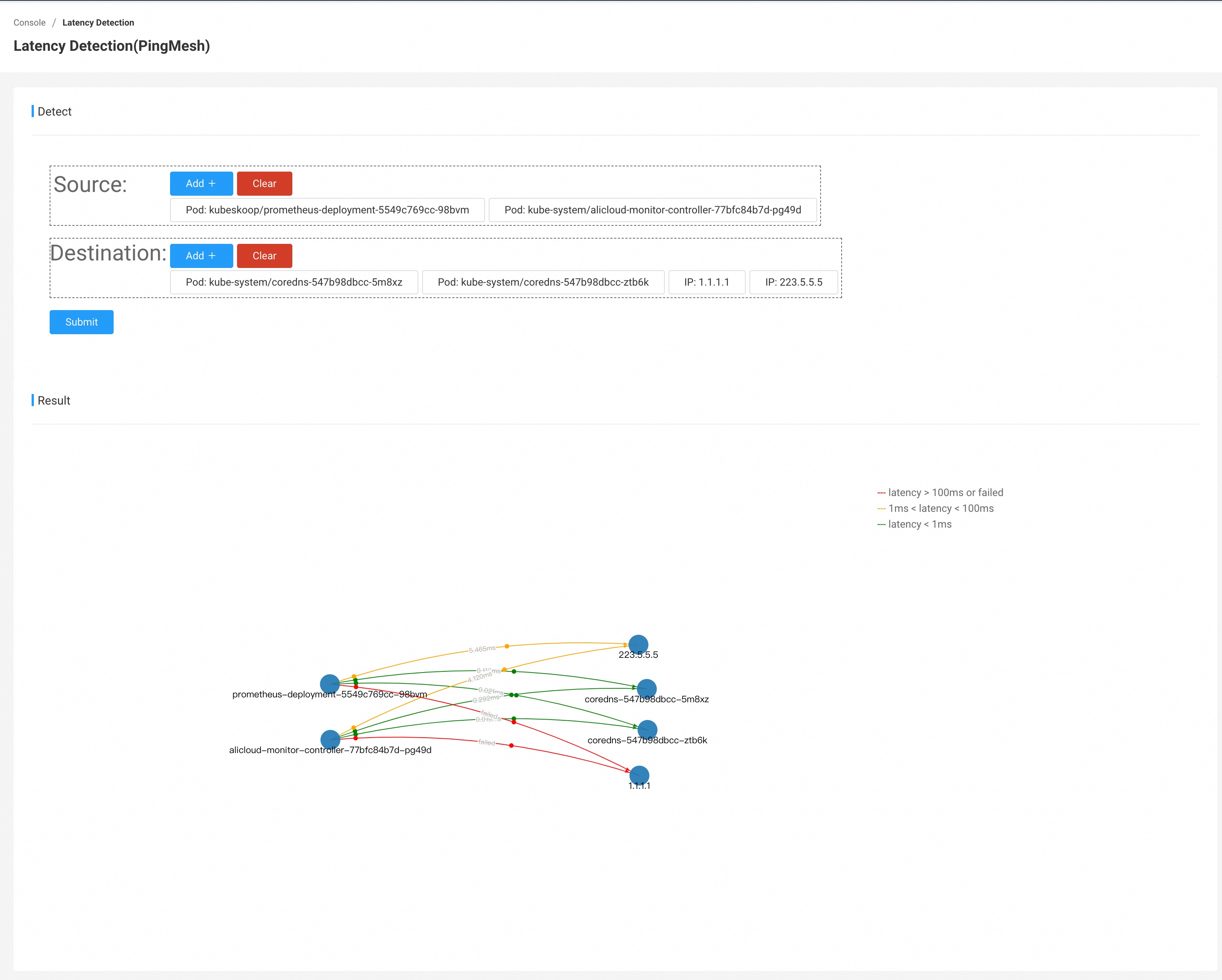
Under Diagnosis - Latency Detection,you can detect latencies between multiple nodes and pods.
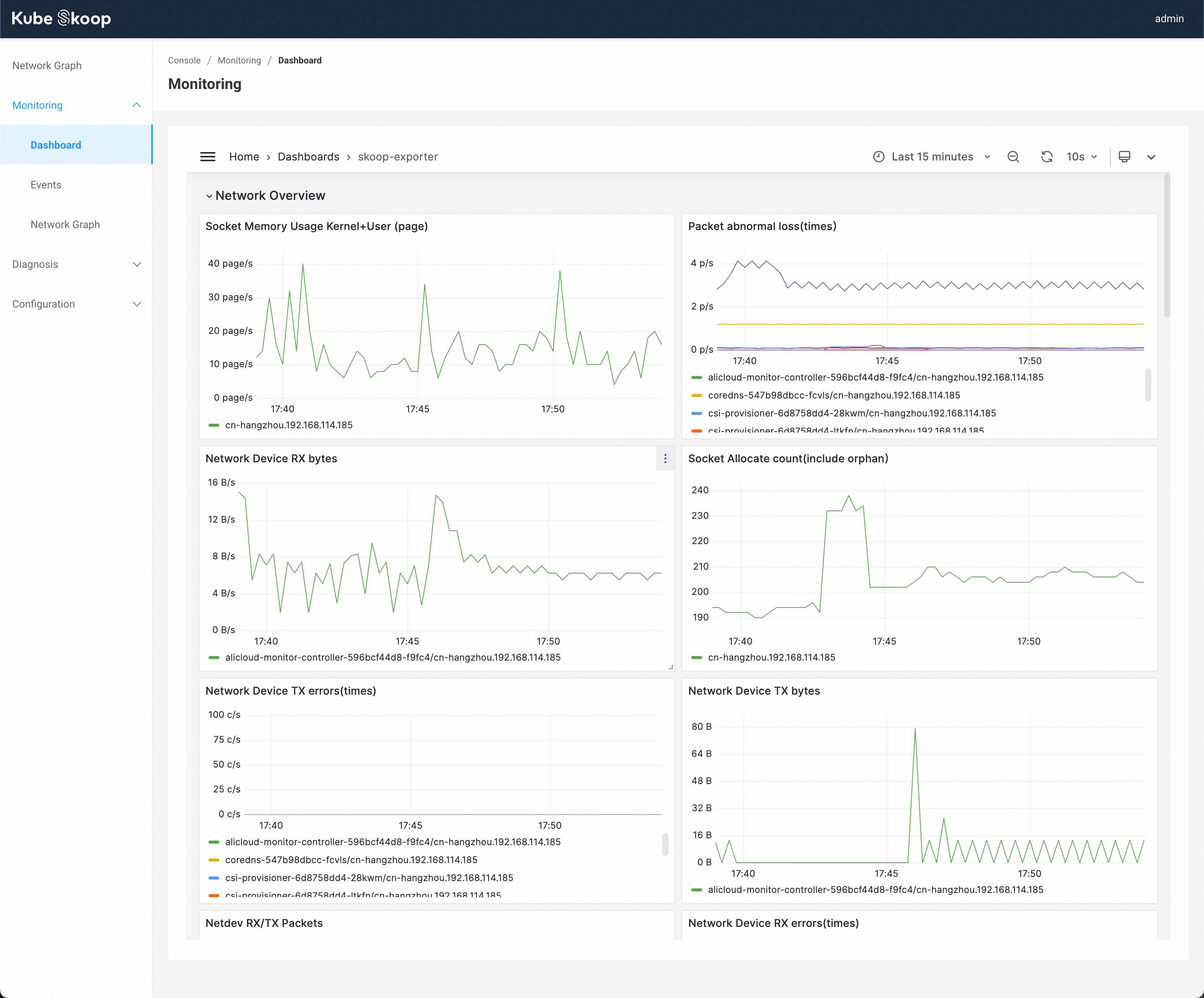
View the network permance dashboard from Monitoring - Dashboard. In the dashboard, you can check the water level of each monitor item corresponding to the time point of the performance problem.
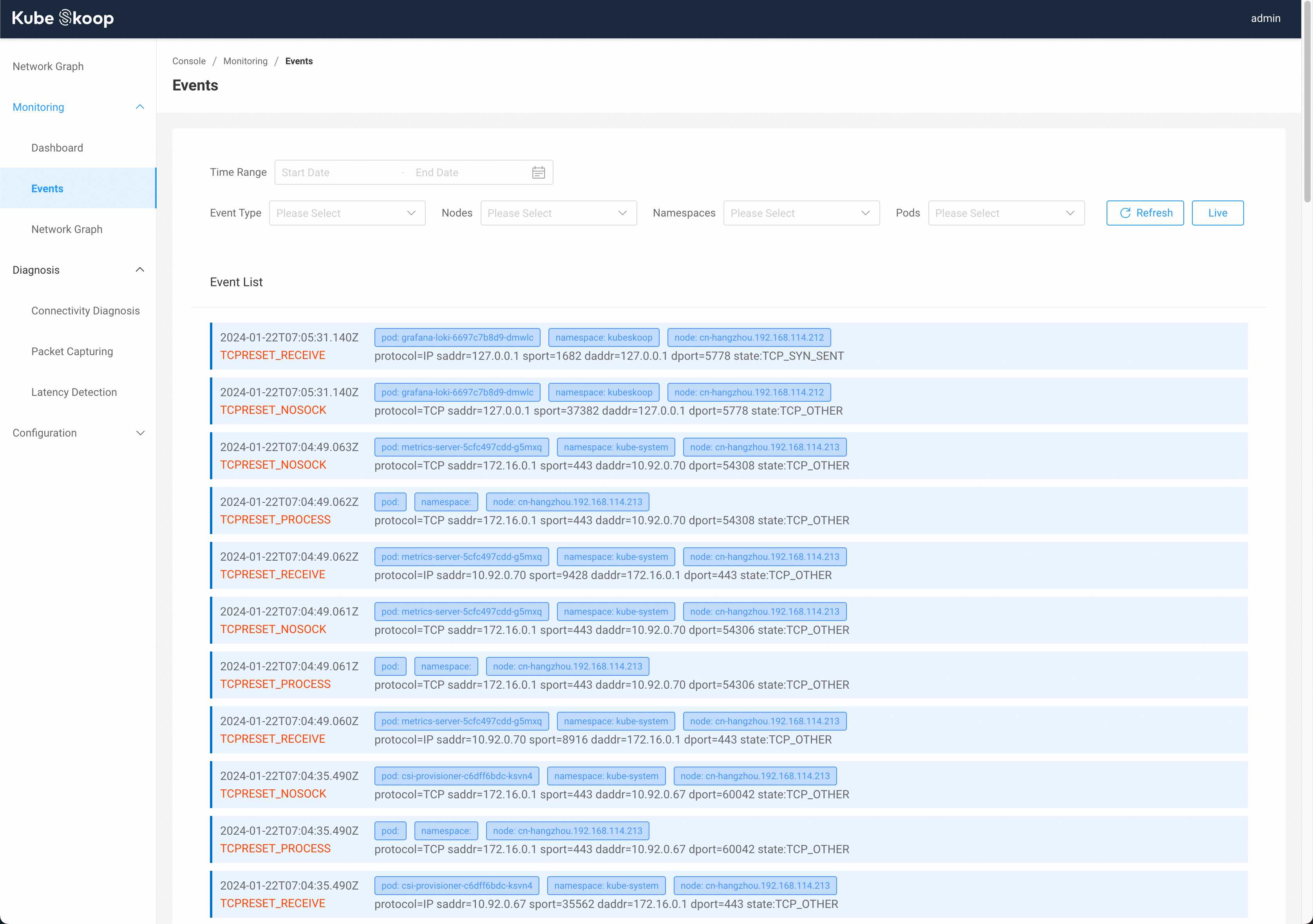
Under Monitoring - Event, you can view the anomaly events occurring within the cluster at the current time point. You can also manually select the desired time range, or filter based on event type, node, and information such as the namespace/name of the Pod where the event occurred.
Click Live on the right top to view the live event stream according to the current filters.
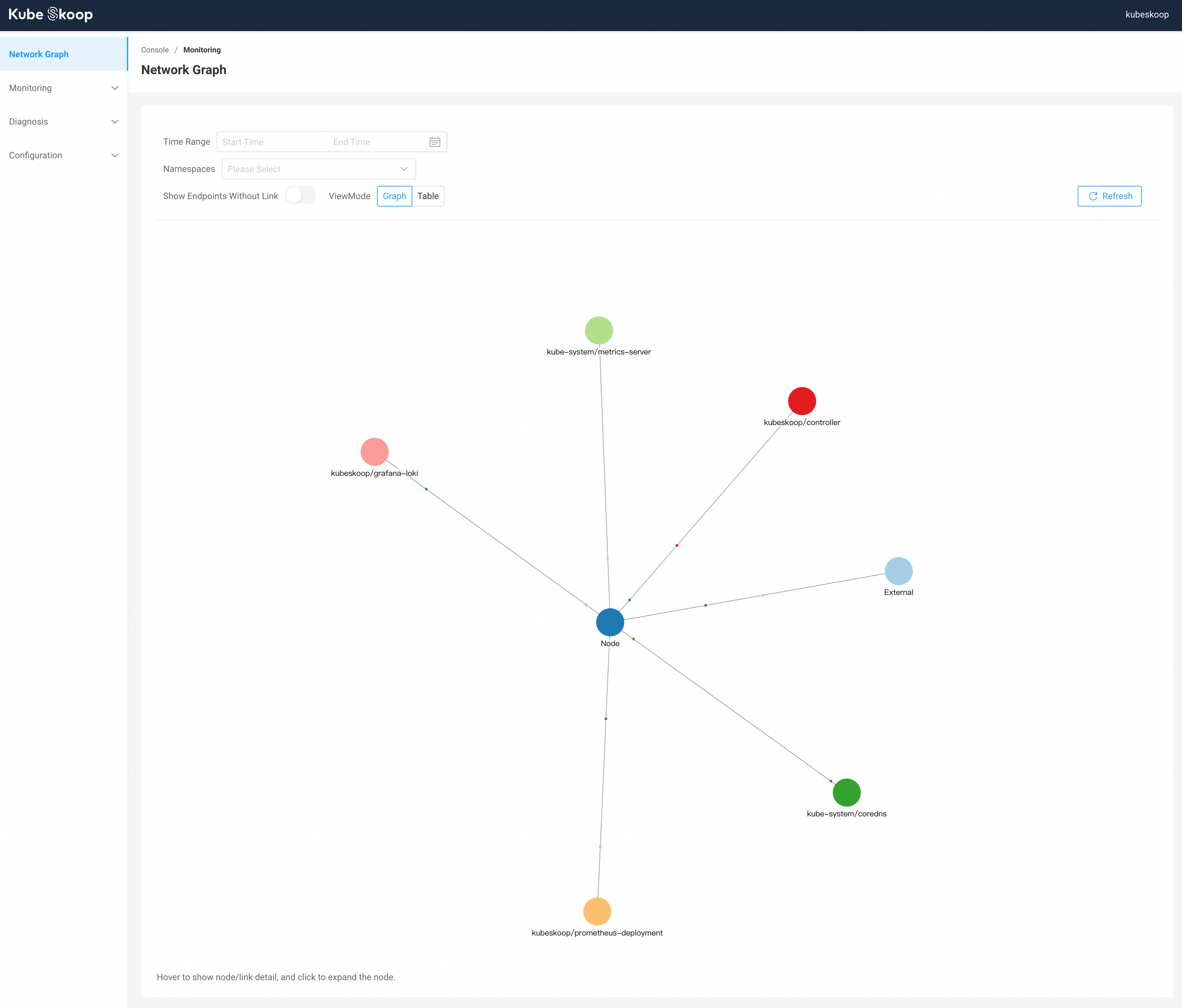
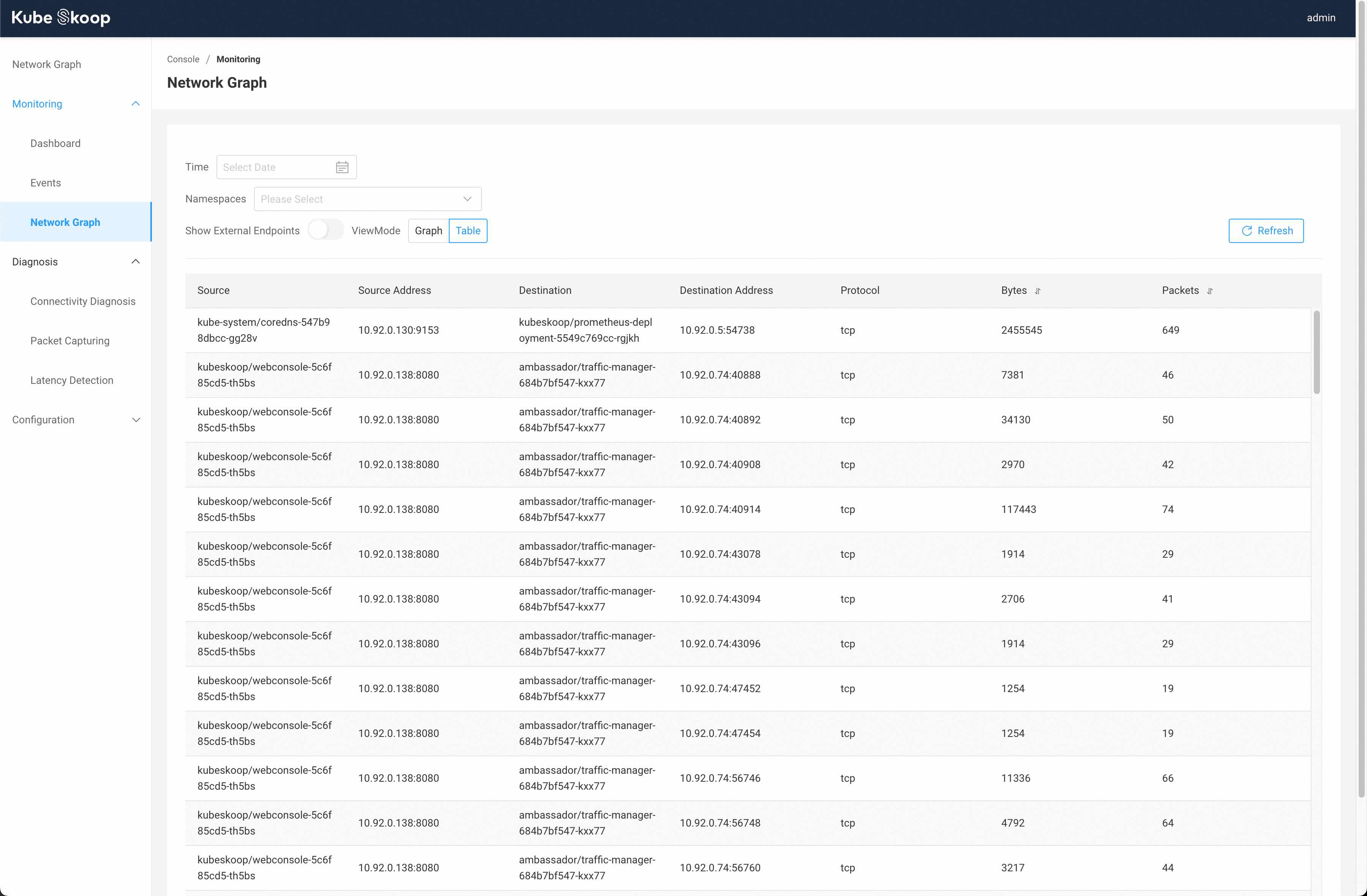
Under the homepage or Monitoring - Network Graph, you can see the actual network link graph in the cluster, with time and namespaces. You can also switch view mode to Table to view each connection.
Feel free to open issues and pull requests. Any feedback is much appreciated!
This project exists, thanks to all the people who contributed.
- DingTalk Group ID(26720020148)
Most source code in KubeSkoop which running on userspace are licensed under the Apache License, Version 2.0.
The BPF code in /bpf directory are licensed under the GPL v2.0 to compat with Linux kernel helper functions.
Please report vulnerabilities by email to kubernetes-security@service.aliyun.com. Also see our SECURITY.md file for details.