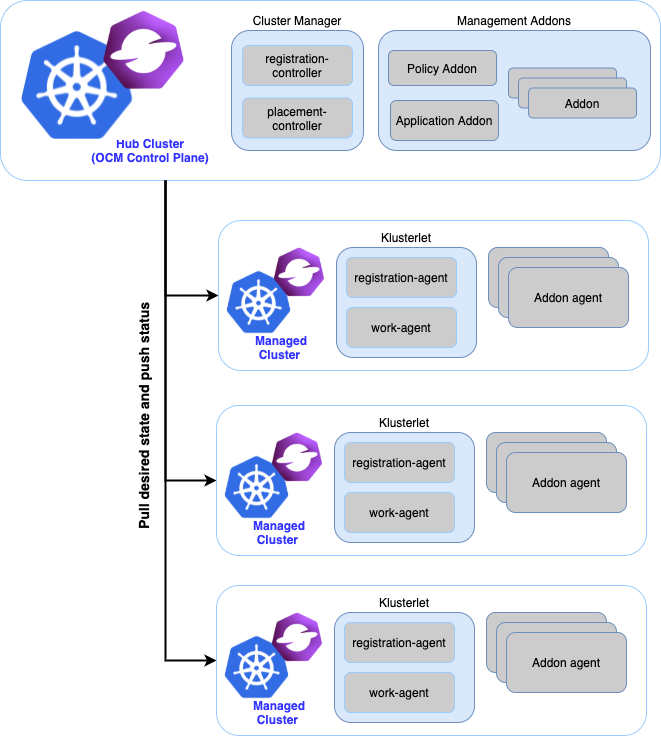
This repository explores the typical installation scenarios and relevant considerations of OpenShift Advanced Cluster Management.
Red Hat Advanced Cluster Management (ACM) allows organizations to rapidly deploy OpenShift to Cloud and On-Premise locations as well as manage the Kubernetes fleet of clusters.
The following diagram provides a high-level overview of a RHACM deployment:
When you install RHACM, the operator creates the following namespaces in the hub cluster:
-
open-cluster-management: the deployments for the main features of RHACM. -
open-cluster-management-hub: the deployments that receive data from the managed clusters. -
open-cluster-management-observability`: the RHACM observability engine (Disabled by default).
When you install RHACM, the operator creates the following namespaces in the managed clusters:
-
open-cluster-management-agent`: the deployments for theklusterletagent. -
open-cluster-management-agent-addon`: the application’s deployments, search engine, and policies engines. -
open-cluster-management-agent-addon-observability`: the observability engine’s deployments.
Are you in a hurry? Do you need a one-click script? Okay, I understand! Execute the following command:
./auto-install.shThe process of installation is not that complex, but it can be divided into two steps. First, create the namespace for ACM and install the operator. Second, create the MultiClusterHub to actually install ACM components.
You can use Red Hat Advanced Cluster Management for Kubernetes to gain insight and optimize your managed clusters.
|
ℹ️
|
Due to the requirement for persistent storage, the observability service is not enabled by default. You must configure an object store to create a storage solution. |
oc process -f openshift/11-multi-cluster-observability.yaml \
--param-file ./aws-env-vars --ignore-unknown-parameters=true \
-p DOCKER_CONFIG_JSON="$(oc extract secret/pull-secret -n openshift-config --to=-)" | oc apply -f -The multicluster engine for Kubernetes operator is the cluster lifecycle operator that provides cluster management capabilities for Red Hat OpenShift Container Platform and Red Hat Advanced Cluster Management hub clusters.
You can import new clusters from the web console or by using the command line.
You can import existing clusters from the console for each of the available cloud providers. By default, the namespace is used for the cluster name and namespace, but you can change it.
|
ℹ️
|
Access the official documentation on how to follow the steps on the Web Console. |
After you install multicluster engine for Kubernetes operator, you are ready to import a cluster and manage it. The following template defines all the objects that you need to create to import your existing cluster.
|
ℹ️
|
Before trying to update all the values, I recommend you to check the official documentation, which will save you some time: https://access.redhat.com/documentation/en-us/red_hat_advanced_cluster_management_for_kubernetes/2.8/html-single/clusters/index#importing-managed-cluster-cli |
oc process -f openshift/20-managed-cluster.yaml \
-p MANAGED_TOKEN="" \
-p MANAGED_API="" | oc apply -f -Example values are:
-
Token:
sha256~Ds0o74XOm54aIMdVaceIHj-afmwiofam.
The policy framework provides governance capabilities to ACM-managed Kubernetes clusters. Policies provide visibility and drive remediation for various security and configuration aspects to help IT administrators meet their requirements.
Every policy requires the policy-template, PlacmentRule, and PlacementBinding templates. A policy can have one or more policy-templates, but a minimum of one policy-template is needed. The PlacementRule template specifies one cluster or set of groups for deploying the policy. As the name implies, the PlacementBinding template binds the policy to the PlacementRules.
|
💡
|
For a nice community catalog of Policies, you can check the upstream documentation. |
The policy controllers monitor whether your cluster is compliant with a policy. The policy controller also reports the policy status, which you can see on the RHACM governance dashboard.
-
Kubernetes Configuration Policy Controller: This policy controller manages, configures, and monitors Kubernetes resources.
-
Certificate Policy Controller: The certificate policy detects when a certificate is about to expire in the default namespace.
-
IAM Policy Controller: This policy controller sends notifications about IAM policy violations. The IAM policy checks for the number of users with cluster role bindings for the cluster-admin role.
-
Integrating Third-party Policy Controllers: RHACM governance supports third-party policy controllers such as gatekeeper policy controllers.
-
Custom Policy Controller: You can create a custom policy controller with the help of a governance-policy-framework repository.
The compliance operator is an OpenShift operator that employs OpenSCAP and enables an administrator to run compliance scans and provide remediation for the issues found.
ApplicationSet is a sub-project of Argo CD that is supported by the GitOps Operator. ApplicationSet adds multicluster support for Argo CD applications. You can create an application set from the Red Hat Advanced Cluster Management console.
|
ℹ️
|
If you are going to configure this setup, I recommend you to read carefully the documentation in sections 1.6.8, 1.6.9, and 1.6.10. |
First, you need to make sure that you have Openshift Gitops up and running. I recommend you to check out this other repository where I configure ArgoCD in the way that the following scripts will expect it:
-
Clone the OCP GitOps Playground repository.
-
Execute the steps detailed in the README.adoc.
The following template configures a Placement rule that handles all the OpenShift clusters and adds them to the ArgoCD instance:
oc process -f openshift/30-gitops-integration.yaml | oc apply -f -Using a Push model, The Argo CD server on the hub cluster deploys the application resources on the managed clusters. For the Pull model, the application resources are propagated by the Propagation controller to the managed clusters by using manifestWork.
|
ℹ️
|
Pull Model is Tech Preview in ACM 2.8, so we will just explore the Push alternative as of today. |
Red Hat Advanced Cluster Management for Kubernetes add-ons can improve some areas of performance and add functionality to enhance your applications.
-
Application Manager: Synchronizes applications on the managed clusters from the hub.
-
Certificate Policy Addon: Monitors certificate expiration based on distributed policies.
-
Config Policy Addon: Audits k8s resources and remediates violations based on configuration policies.
-
Governance Policy Framework Addon: Distributes policies and collects policy evaluation results.
-
IAM Policy Addon: Monitors identity controls based on distributed policies.
-
Search Collector: Collects cluster data to be indexed by search components on the hub cluster.
-
Submariner Addon: Submariner Addon for MultiCluster connectivity.
-
VolSync: VolSync (Asynchronous volume replication for Kubernetes CSI storage).