This project allows you to improve the security quality of your project, by running some of the main security checks/validation in a simple way on different projects languages and you can quick integrate it in the current most popular CI/CD tools.
- Run the most essential security check/analysis in a single container
- Make ease the integration of the security tools with the most popular CI/CD tools
- Help to improve the security quality of the applications that uses it
- Git Secrets
- Dependency Check
- SSL Scanning
- SAST Code Check
- Automated Functional Penetration Testing
==WIP==
| Language | Integration Status |
|---|---|
| Java | Done |
| JavaScript | Work in progress |
| TypeScript | Work in progress |
| C# | Planned |
| Kotlin | Planned |
| Tool | Integration Status |
|---|---|
| Jenkins | Done |
| GitLab CI | Work in progress |
| Bamboo | Planned |
| Azure DevOps | Planned |
There are many ways to run all of those checks. The recommended way to run those checks is by using the "run-sec-advisor" script, however, you can run in other ways by the scratch if you want, so, following are presented the most common way to run those checks and validations (including the one using the script)
- Docker
- docker-compose
- A shell script executor (for those using Windows)
To perform the checks by using the script is a pretty simple task, you can do all of that by just running these commands:
chmod +x run-sec-advisor.sh - it will able this script to be run
./run-sec-advisor.sh - it will start the script and show you the options to run the tests
After that the script will present all the options allowed to you, so you can just type the desired option and the script will do all the action for you.
After every check a report generated by the analysis/checking performed will be stored at a folder named 'job-reports' which will be created on the current folder of this project. So you can just access the folder 'job-reports' and look for the report generated by your analysis/check.
Every report generated by the script run will have the time and date of the test execution in the report name, so you can keep the history of all the analysis and/or checks that you want.
- Docker
By following the examples below you can easily run your security checks with the usage of pure Docker.
docker run -v $(pwd)/job-reports:/opt/job-reports -it ralves20/sec-tests:1.0 sh -c "gitleaks --path <repository path> -v --report=/opt/job-reports/gitleaksreport.json" - it will run the checking for vulnerabilities and secrets of git.
bash docker run -v $(pwd)/job-reports:/opt/job-reports -it ralves20/sec-tests:1.0 sh -c "sslyze <Application's IP or DNS> --json_out=/opt/job-reports/sslyze-analysis.json" - it will run ssl/tls analysis in the application in testing.
docker run -v $(pwd)/job-reports:/opt/job-reports -it ralves20/sec-tests:1.0 sh -c "dependency-check --project '<Project Name>' --scan <repository path> --out /opt/job-reports/" - this check will search for security vulnerabilities in the dependencies used by the project in testing.
docker run -v $(pwd)/job-reports:/opt/job-reports -it ralves20/sec-tests:1.0 sh -c "docker-compose run security-tests findsecbugs -progress -html -output /opt/job-reports/findsecbug-analysis.htm <repository path>/target/*.jar" - it will perform a SAST code check in your code.
EN - it will perform an automated functional security penetration testing.
After every check a report generated by the analysis/checking performed will be stored at a folder named 'job-reports' which will be created on the current folder of this project. So you can just access the folder 'job-reports' and look for the report generated by your analysis/check.
In the case of pure docker run, every execution of the same tool will replace the last report generated by that for the new one (the most updated check), if you want to keep the older and the newer, you have to change the name of the report file that are going to be generated in every command sintax, and every command run have to be a different name for the report file, so you can keep all of them.
- Docker
- docker-compose
By following the examples below you can easily run your security checks with the usage of docker-compose.
docker-compose run security-tests gitleaks --path <repository path> -v --report=/opt/job-reports/gitleaksreport.json - it will run the checking for vulnerabilities and secrets of git.
docker-compose run security-tests sslyze <Application's IP or DNS> --json_out=/opt/job-reports/sslyze-analysis.json - it will run ssl/tls analysis in the application in testing.
docker-compose run security-tests dependency-check --project '<Project Name>' --scan <repository path> --out /opt/job-reports/ - this check will search for security vulnerabilities in the dependencies used by the project in testing.
docker-compose run security-tests findsecbugs -progress -html -output /opt/job-reports/findsecbug-analysis.htm <repository path>/target/*.jar - it will perform a SAST code check in your code.
EN - it will perform an automated functional security penetration testing.
After every check a report generated by the analysis/checking performed will be stored at a folder named 'job-reports' which will be created on the current folder of this project. So you can just access the folder 'job-reports' and look for the report generated by your analysis/check.
In the case of the docker-compose run, every execution of the same tool will replace the last report generated by that for the new one (the most updated check), if you want to keep the older and the newer, you have to change the name of the report file that are going to be generated in every command sintax, and every command run have to be a different name for the report file, so you can keep all of them.
Jenkins - (https://www.jenkins.io/)
![]()
"The leading open source automation server, Jenkins provides hundreds of plugins to support building, deploying and automating any project."
- Docker
- docker-compose
- Jenkins
- HTML Publisher (Jenkins plugin)
To integrate these security checks in your Jenkins, its pretty simple also, you have just to follow those steps:
- Access the jenkins/ folder
- Chose the Jenkinsfile example for the project language that you are going to use
- Make a copy this Jenkinsfile-example and rename that copy for "Jenkinsfile" only
- Change all the values between "< >" to the correct values in that Jenkinsfile
- Create a new job on your Jenkins and make the created job point to the Jenkinsfile that you just updated.
To run the all the validations its even easier, you have just to press the "play" icon on the Jenkins job that you just created with the pipeline.
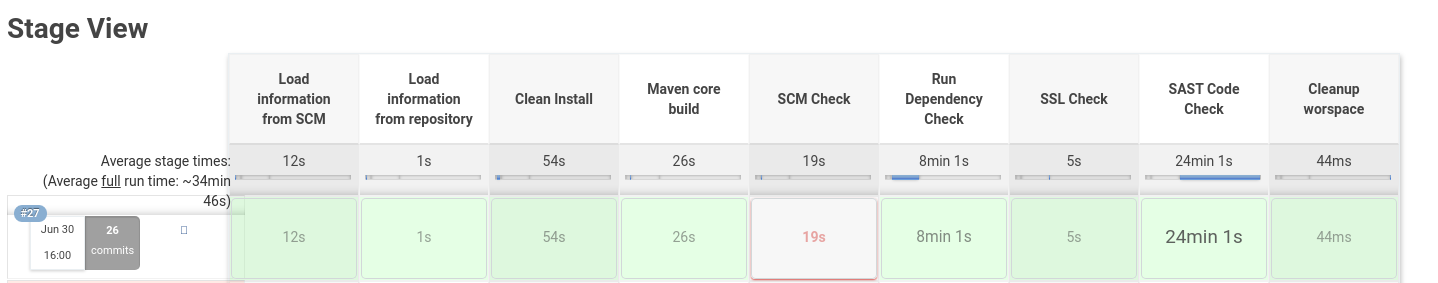
After you press the "play" all the analysis and checks will be performed, and each one of those are completely independent, which means that if a previous step of the pipeline (one of the validations) fails, all of the next validations are going to run anyway, they don't run based on the previous validation success... Once again, all of these runs are completely independent.
This image below is an example of this pipeline and it shows also that the steps are independent:
If you have configured your Jenkins HTML Publish plugin properly, each report will be showed in the left sidebar of your jenkins job. The reports are going to be show in a way similar to this one:
==WIP==