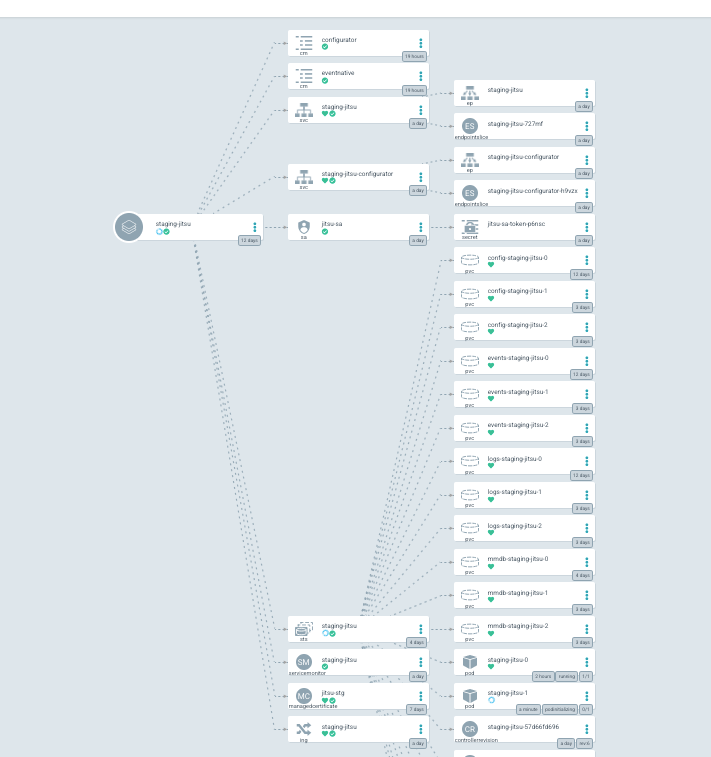
This chart assumes:
- a GKE cluster with workload identity enabled on cluster
- GCP service account annotated with the name of jitsu KSA
- To give jitsu access to GCS
- refer to terraform directory for all needed entities
Dependencies:
- Redis connection string
- This chart assumes prometheus operator is installed on the cluster
- disable monitoring in values file if not
- External DNS is installed in the cluster
- if not chart will still work
This chart creates a ManagedCertificate
- a GKE resource that will provision a TLS certificate
- assigns this certificate to an Ingress
- ( this will open jitsu server to the world - assuming google hosted zone is connected to a public dns)
Jitsu configurator is created as a ClusterIp service and can be accessed only via private IP/port forwarding
terraform directory contains all relevant resources needed for this deployment to operate on GKE
- GCP service account
- workload identity mapping
- reserved static ip
- ingress dns record set ( assuming google hosted zones are connected to a public dns )
- maxmind GCS bucket
- granting jitsu SA Object Admin role on maxmind bucket
Best install this chart using argocd
git clone git@github.com:viggin543/jitsu_helm_chart.git
# view generated k8s manifests
helm template jitsu_helm_chart/jitsu_GKE --values jitsu_helm_chart/jitsu_GKE/values.yaml --debug
# install using helm
helm install jitsu_helm_chart/jitsu_GKE --values jitsu_helm_chart/jitsu_GKE/values.yaml
# uninstall using helm
helm uninstall jitsu_helm_chart/jitsu_GKEWith slight modifications this chart can be installed on any k8s. But without the GKE good stuff ( ManagedCertificate && WorkloadIdentity )