Modern CI/CD with Anthos
Introduction
Kubernetes has given us wonderful abstraction that we can use to optimize the way we develop, deploy, and maintain software projects across multiple environments. In many cases though, Kubernetes is too complex for end users to learn and feel empowered with. To alleviate this learning curve, many teams are looking to build platform abstractions on top of Kubernetes to streamline onboarding and reduce maintenenance for software projects.
In this repository we lay out a prescriptive way to create a multi-team software delivery platform using Anthos. The platform has the following capabilities:
- Allow platform administrators to create and update best practices for provisioning apps
- Ensure App Developers can iterate independently in their own "landing zones" without interfering with each other
- Allow security teams to seamlessly implement and propagate policy across the platform
- Use GitOps for deployment
For more details, please watch this talk on Youtube.
Architecture Overview
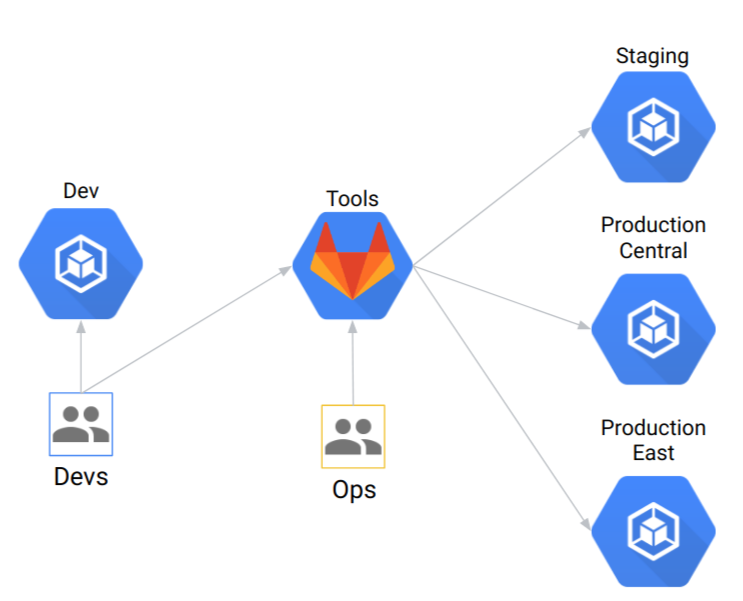
After the Quick Start you will have the following infra:
- GitLab deployed on GKE to host your source code repostitories
- 1 Dev cluster that can be used for iterative development with tools like Skaffold
- 1 Staging cluster
- 2 Production clusters in different GCP regions
Within GitLab you will have the following repo structure:
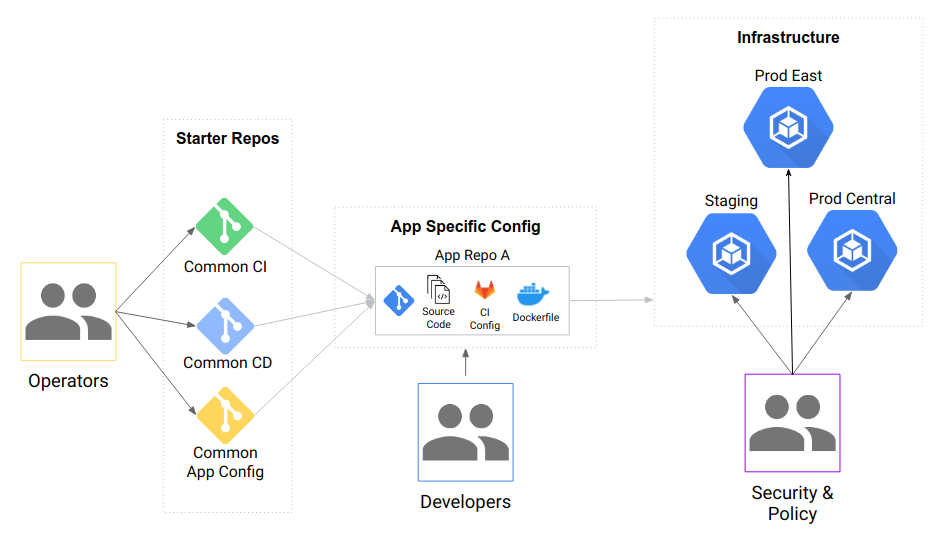
Starter repos have examples for:
- CI stages/steps
- CD methodologies
- Kubernetes configs (via Kustomize)
- An example application repo for a Go app
Pre-requisites
-
Clone this repo to your local machine.
-
Enable billing for GCP project
-
Set the
us-central1region to deploy infrastructureexport REGION="us-central1" gcloud config set compute/region ${REGION}
Build Infrastructure
-
Run the following commands to setup Cloud Build
export PROJECT_ID=<INSERT_YOUR_PROJECT_ID> gcloud config set core/project ${PROJECT_ID} export PROJECT_NUMBER=$(gcloud projects describe ${PROJECT_ID} --format 'value(projectNumber)') gcloud services enable cloudbuild.googleapis.com gcloud services enable anthos.googleapis.com gcloud services enable serviceusage.googleapis.com gcloud services enable cloudkms.googleapis.com gcloud services enable containeranalysis.googleapis.com gcloud projects add-iam-policy-binding ${PROJECT_ID} --member serviceAccount:${PROJECT_NUMBER}@cloudbuild.gserviceaccount.com --role roles/owner gcloud projects add-iam-policy-binding ${PROJECT_ID} --member serviceAccount:${PROJECT_NUMBER}@cloudbuild.gserviceaccount.com --role roles/containeranalysis.admin
-
Run Cloud Build to create the necessary resources.
gcloud builds submit --substitutions=_PROJECT_ID=${PROJECT_ID}⚠️ This operation may take up to 30 minutes depending on region. Do not close the console or connection as the operation is NOT idempotent. If a failure occurs, clean up the environment and attempt again. -
Log in to your GitLab instance with the URL, username and password printed at the end of the build. Hang on to this password, you will need it for later steps.
-
Follow the steps in the docs to go through a user journey (add, deploy, and change applications).
Important Variables
-
Take note and record the Password for your Gitlab account.
-
URL for Gitlab
echo "https://gitlab.endpoints.${PROJECT_ID}.cloud.goog"
-
User and Password for GitLab are stored in the Secrets Manager
export GITLAB_USER=$(gcloud secrets versions access latest --secret="gitlab-user")
export GITLAB_PASSWORD=$(gcloud secrets versions access latest --secret="gitlab-password")
echo "User: ${GITLAB_USER}"
echo "Password: ${GITLAB_PASSWORD}"
Clean Up
-
Remove infrastructure
gcloud builds submit --substitutions=_PROJECT_ID=${PROJECT_ID} --config cloudbuild-destroy.yaml gcloud endpoints services delete gitlab.endpoints.${PROJECT_ID}.cloud.goog gcloud endpoints services delete registry.endpoints.${PROJECT_ID}.cloud.goog
-
Unset variables (optional)
unset PROJECT_ID unset REGION
Securing the ACM repository
At this stage, you should have a working ACM installation good enough for most demos. If you want to follow production best practices, read Best practices for policy management with Anthos Config Management and GitLab.
Always leave at least one namespace defined in namespaces/managed-apps, otherwise ACM will
stop syncing.