This sample shows how to call Azure SQL passing thru the logged in user's credentials (user_impersonation) [aka the On Behalf Flow]. This is the Azure AD versions of Windows Impersonation. This sample is ASP.Net Core 3.1.
There are 2 different examples:
- Using the older style with ConfidentialClientApplicationBuilder
- The Pre-release version of the new Microsoft.Identity.Web library
- Need to specify the Conditional Complication symbol:
newMSAL
- Need to specify the Conditional Complication symbol:
- Startup.cs - Focus on the block starting with
#if newMSAL - HomeController.cs - Calling SQL
- Register your application as Azure Active Directory Application
- For that Azure Application Registration
- Create an Application ID URI [Config (appsettings.config): AzureAd - AppIdUri]
- Under Authentication
- Under Implicit Grant, select "ID tokens"
- For a Web App, for every deployed version of the app, add a Redirect URI with the pattern of [URL]/signin-oidc.
- Under Certificates & secrets, create a secret [Config (appsettings.config): AzureAd - ClientSecret]
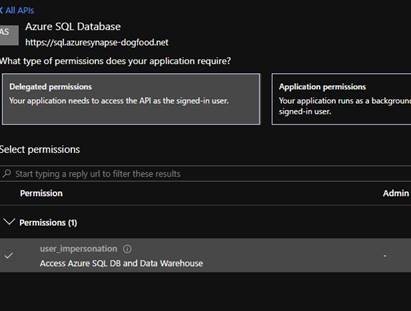
- Under API Permissions
- Add a Permission
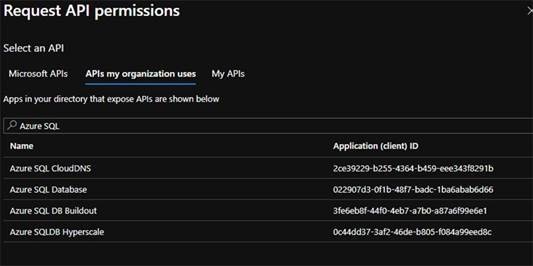
- Search "APIs my organization uses"
- You must then "Grant admin consent"
- Add a Permission
- AD Users have to be configured in SQL for correct permissions, for example if the users Azure AD Account was user@contoso.com:
CREATE USER [user@contoso.com] FROM EXTERNAL PROVIDER- You can know use user@contoso.com for Role membership and GRANT commands.
- Update the appsettings.config
- ConnectionString:
"Server=tcp:SOMESERVER.database.windows.net,1433;Initial Catalog=SOMEDB;" - AzureAd section has the various properties of an Azure AD App:
- ConnectionString:
"AzureAd": {
"Instance": "https://login.microsoftonline.com/",
"Domain": "",
"TenantId": "",
"ClientId": "",
"ClientSecret": "",
"CallbackPath": "",
"AppIdUri": ""
}