This repository provides a sample Go application CI/CD deployment on EKS
- Deployment Manifest File
- Create IAM Role for CodeBuild to interact with EKS
- Add the CodeBuildEKSRole role to aws-auth configmap
- Prepare buildspec.yml
- Setting Up CodePipeline
- Create IAM Policy for CodeBuild to assume CodeBuildEKSRole
Useful tools to manage EKS:
We specify the container image in the deployment manifest file deployment.yml using CONTAINER_IMAGE which will be replaced to the actual container image by the build script during build process.
Create an IAM Role for CodeBuild so that it can interact with EKS, with the following trust policy:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::<AWS_ACCOUNT_ID>:root"
},
"Action": "sts:AssumeRole"
}
]
}and the following permission
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "eks:Describe*",
"Resource": "*"
}
]
}For this example, the IAM Role will be named CodeBuildEKSRole.
Update the aws-auth configmap in kube-system namespace with
kubectl edit configmap aws-auth --namespace kube-systemand add
- rolearn: arn:aws:iam::<AWS_ACCOUNT_ID>:role/CodeBuildEKSRole
username: codebuild
groups:
- system:mastersto data.mapRoles
To specify the build commands to be run by CodeBuild, a buildspec.yml file can be created.
In summary, the commands defined in buildspec.yml will perform the following:
- Replace
CONTAINER_IMAGEin deployment manifest to the Docker image with tag - Login to Amazon ECR Registry
- Build the Docker image for the application
- Push the Docker image to the ECR Repository
- Update kubeconfig to use the designated EKS cluster
- Apply the manifests
For documentation about build specification reference for CodeBuild: https://docs.aws.amazon.com/codebuild/latest/userguide/build-spec-ref.html
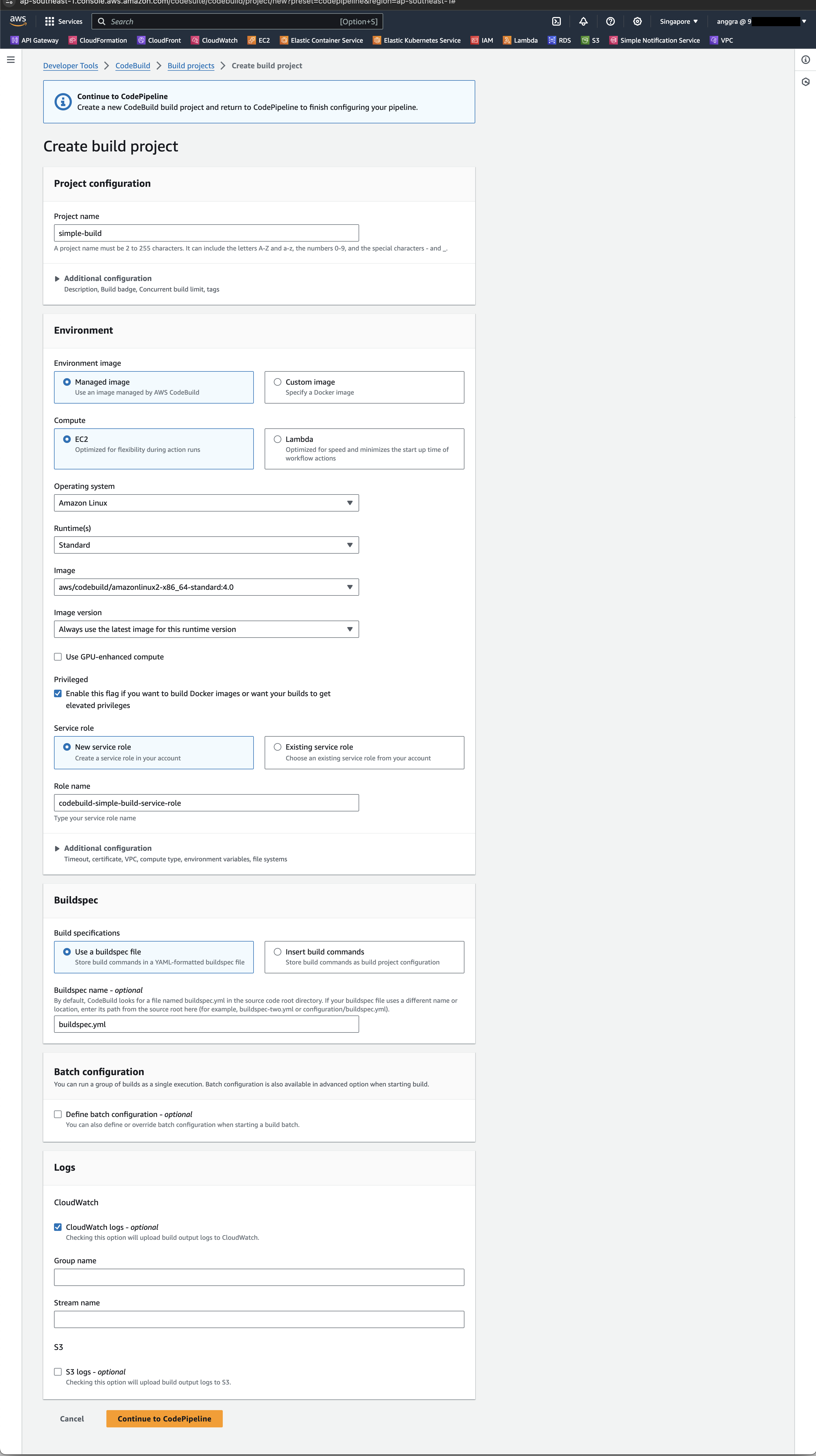
Build environment configurations:
- Environment image:
Managed image - Operating system:
Amazon Linux - Runtime:
Standard - Image:
aws/codebuild/amazonlinux2-x86_64-standard:4.0 - Privileged: ✅ Enable this flag if you want to build Docker Images or want your builds to get elevated privileges
- Service role: 🔵 New service role, in this example, the Role name is using the automatically provided name:
codebuild-simple-build-service-role - Buildspec: 🔵 Use a buildspec file, Buildspec name:
buildspec.yml
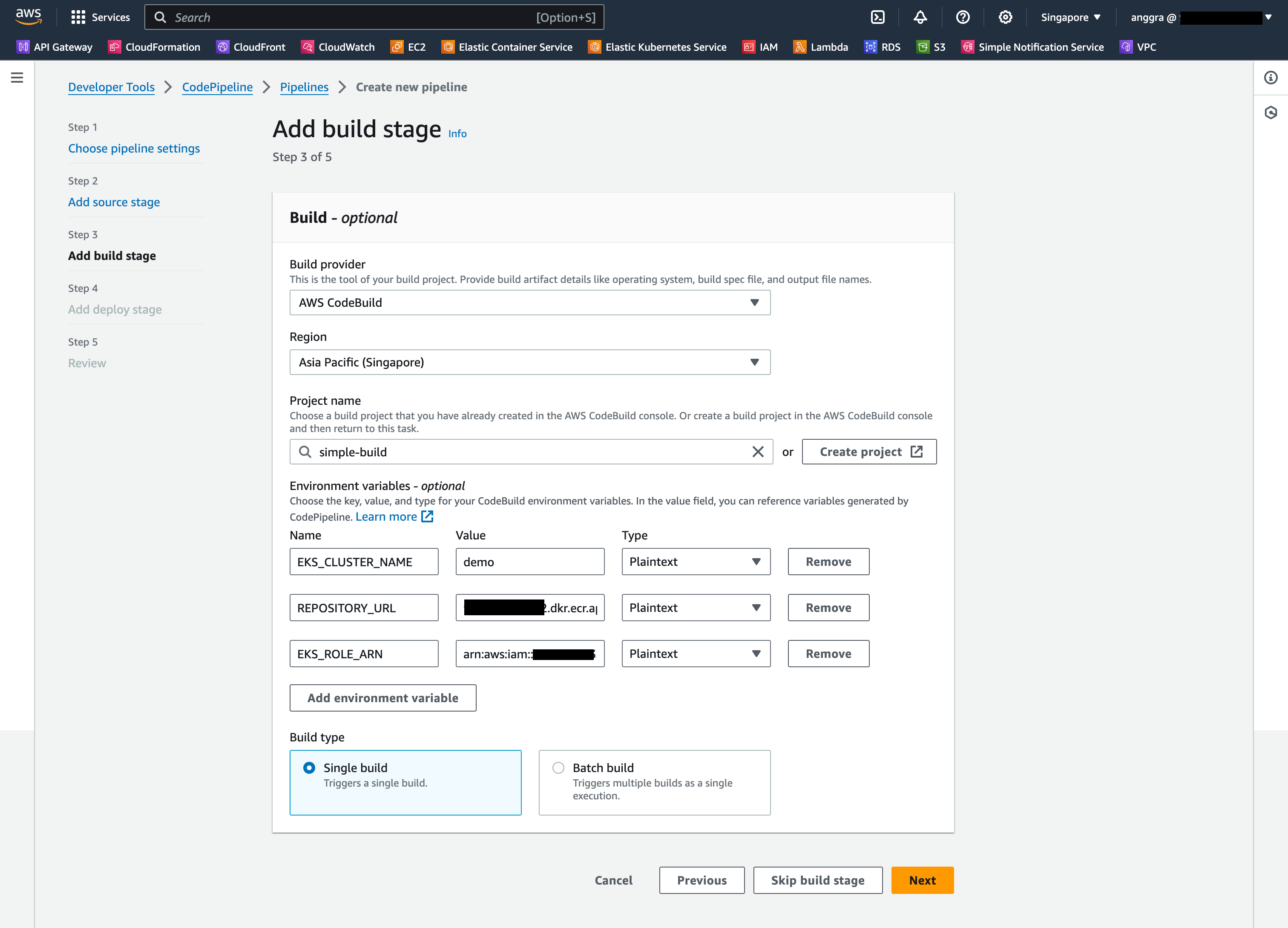
Back in the Build stage configuration of CodePipeline, provide the environment variables:
- EKS_CLUSTER_NAME
- REPOSITORY_URL
- EKS_ROLE_ARN, (
arn:aws:iam::<AWS_ACCOUNT_ID>:role/CodeBuildEKSRole)
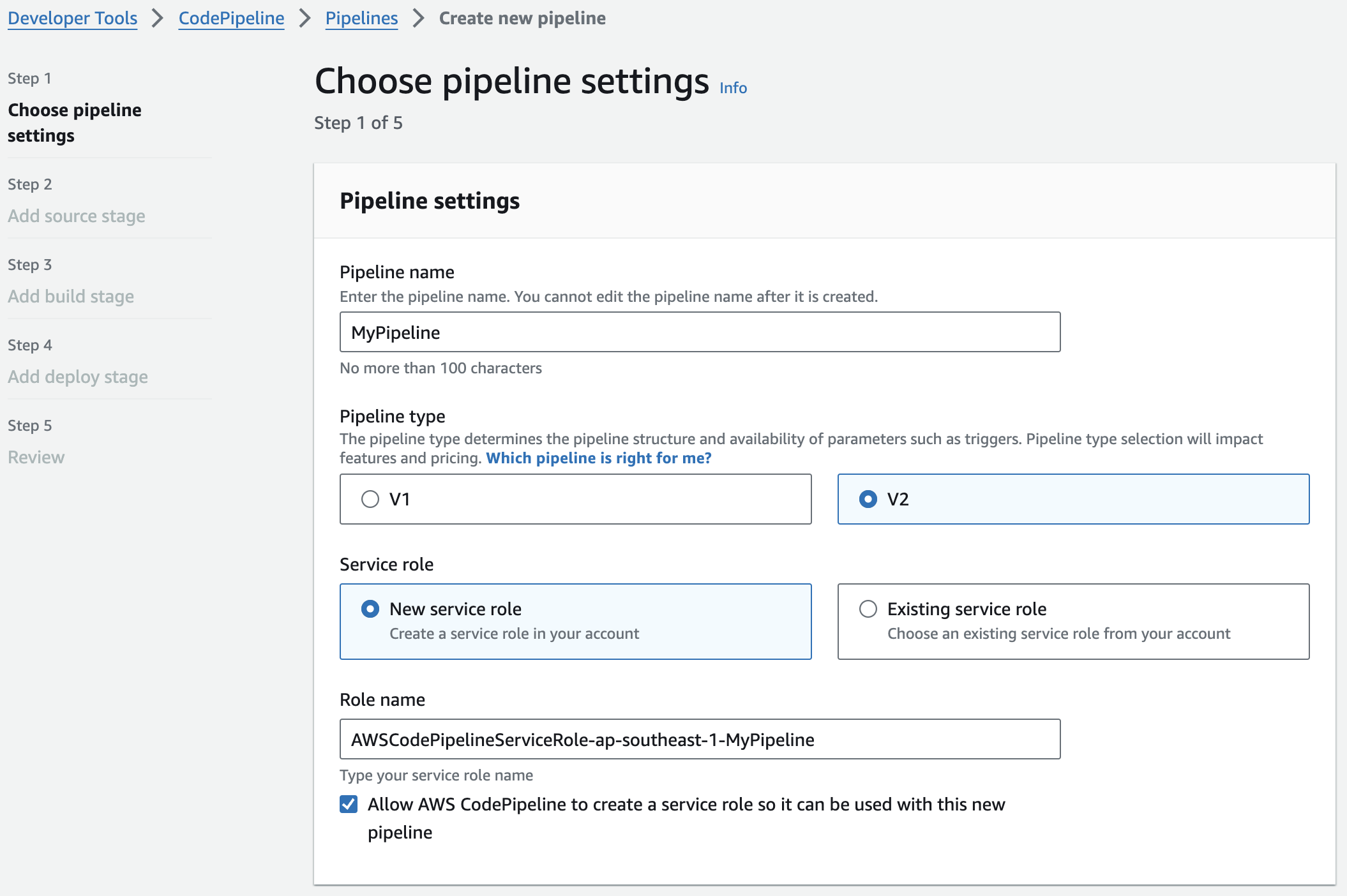
Review and then click Create pipeline.
Create an IAM Policy named codebuild-eks-sts-role with the following policy:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "sts:AssumeRole",
"Resource": "arn:aws:iam::<AWS_ACCOUNT_ID>:role/CodeBuildEKSRole"
}
]
}Attach codebuild-eks-sts-role IAM Policy to codebuild-simple-build-service-role Role.
AmazonEC2ContainerRegistryFullAccess IAM Policy may also need to be attached so that CodeBuild is able to push to the ECR registry.
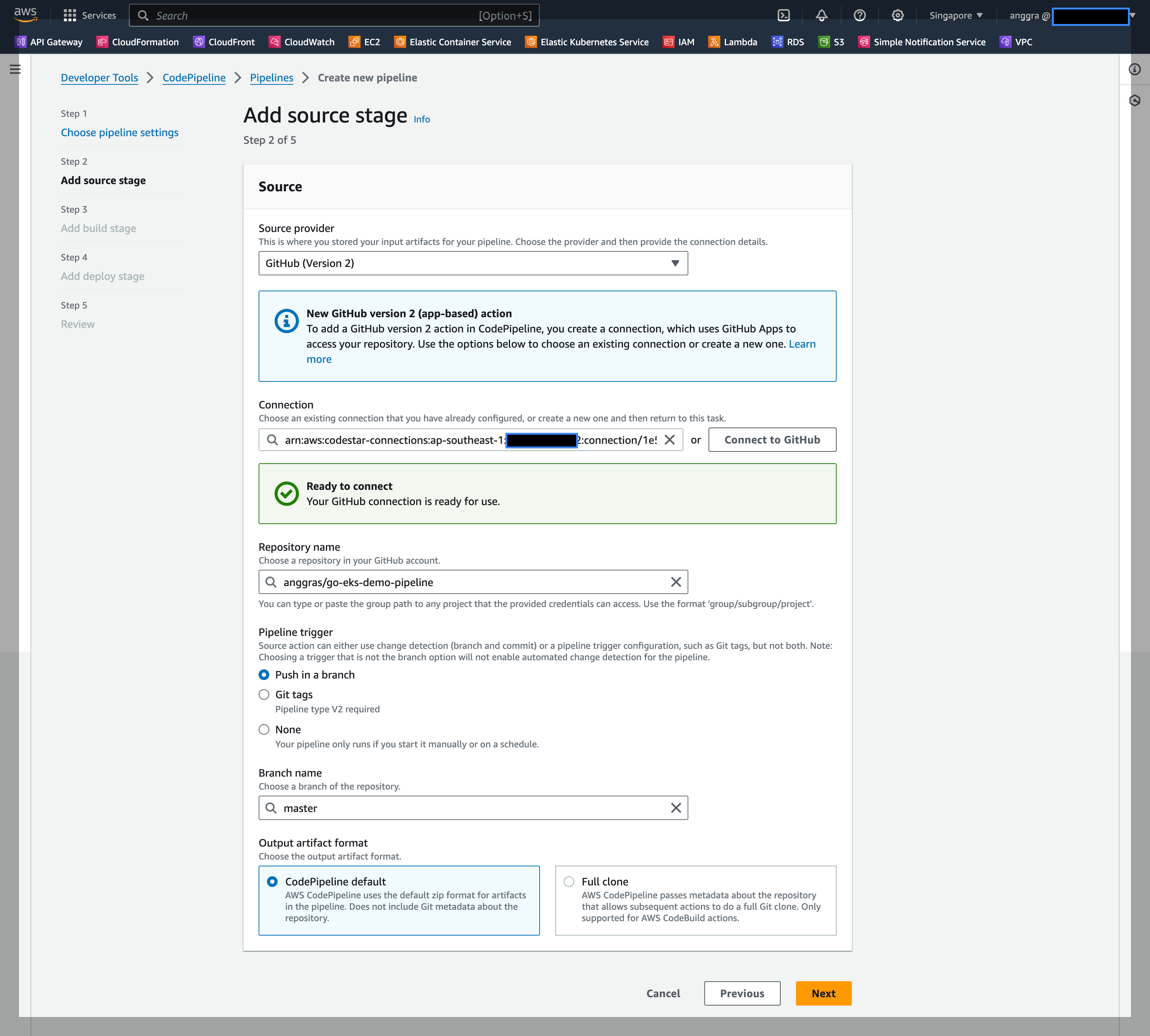
Once done, the pipeline should be ready and any commit to the master branch will trigger the pipeline process.
[^1] CI/CD Pipeline for EKS using CodeCommit, CodeBuild, CodePipeline, and Elastic Container Registry(ECR) https://devopslearning.medium.com/ci-cd-pipeline-for-eks-using-codecommit-codebuild-codepipeline-and-elastic-container-100f4b85e434
[^2] DevOps with AWS CodePipeline on AWS EKS https://www.stacksimplify.com/aws-eks/aws-devops-eks/learn-to-master-devops-on-aws-eks-using-aws-codecommit-codebuild-codepipeline/