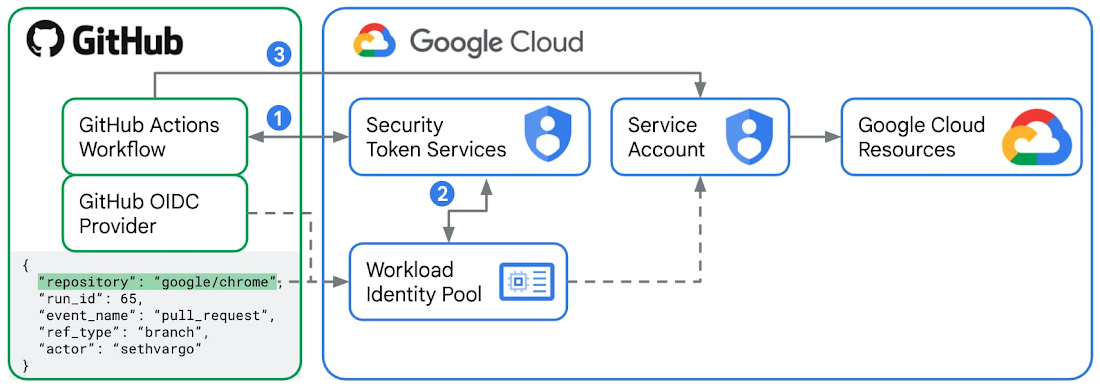
Workload Identity Federation allows secure and efficient access to Google Cloud resources from external environments like AWS, Azure, on-premises Active Directory, and deployment services such as GitHub and GitLab. Instead of using traditional service account keys, which pose security risks, it leverages IAM roles and service account impersonation for streamlined access.
Workload Identity Pools: Manage external identities, recommended to create distinct pools for different environments (development, staging, production).
Workload Identity Pool Providers: Define relationships between Google Cloud and identity providers, including AWS, Azure AD, GitHub, GitLab, Kubernetes clusters, Okta, AD FS, and Terraform.
Steps: Workload Identity Federation
Create Workload Identity Federation Pool
- Create a new Workload Identity Pool named
GitLabwith the IDgitlab - Select
OpenID Connect (OIDC)as Provider
Add Workload Identity Federation Provider to the Pool (multiple providers can be added in a pool)
-
Select
OpenID Connect (OIDC)as provider -
Write a new Workload Identity Provider named
Gitlab Testwith the IDgitlab-test -
Issuer URL:
https://gitlab.com/(with trailing slash) -
keep the default audience. (Add if needed)
NOTE:
- The address must use the https:// protocol.
- The address must not end in a trailing slash.
-
Configure the provider attributes mapping
google.subjecttoassertion.subattribute.project_pathtoassertion.project_path -
save it.
Grant permissions for Service Account impersonation
-
Create a new service account named
gitlab-test -
Grant IAM permissions
For example, if you needed to upload a file to a Google Cloud Storage bucket in your GitLab CI/CD job, you would grant this Service Account the roles/storage.objectCreator role on your Cloud Storage bucket. -
Grant the external identity permission using the following command. External identities are expressed using the principalSet:// protocol.
gcloud iam service-accounts add-iam-policy-binding gitlab-test@<gcp-project>.iam.gserviceaccount.com --role=roles/iam.workloadIdentityUser --member="principalSet://iam.googleapis.com/projects/906410504594/locations/global/workloadIdentityPools/gitlab/attribute.project_path/<gitlab-repository-path>"EXAMPLE
gcloud iam service-accounts add-iam-policy-binding gitlab-test@<gcp-project>.iam.gserviceaccount.com --role=roles/iam.workloadIdentityUser --member="principalSet://iam.googleapis.com/projects/906410504594/locations/global/workloadIdentityPools/gitlab/attribute.project_path/ankitcharolia/gitlab-workload-identity"
inputs = {
workload_identity_pool_id = "gitlab-ci"
workload_identity_pool_display_name = "gitlab-ci"
workload_identity_pool_provider_id = "terraform"
service_account_name = "gitlab-ci"
service_account_display_name = "gitlab-ci"
service_account_description = "service account for gitlab-ci"
}