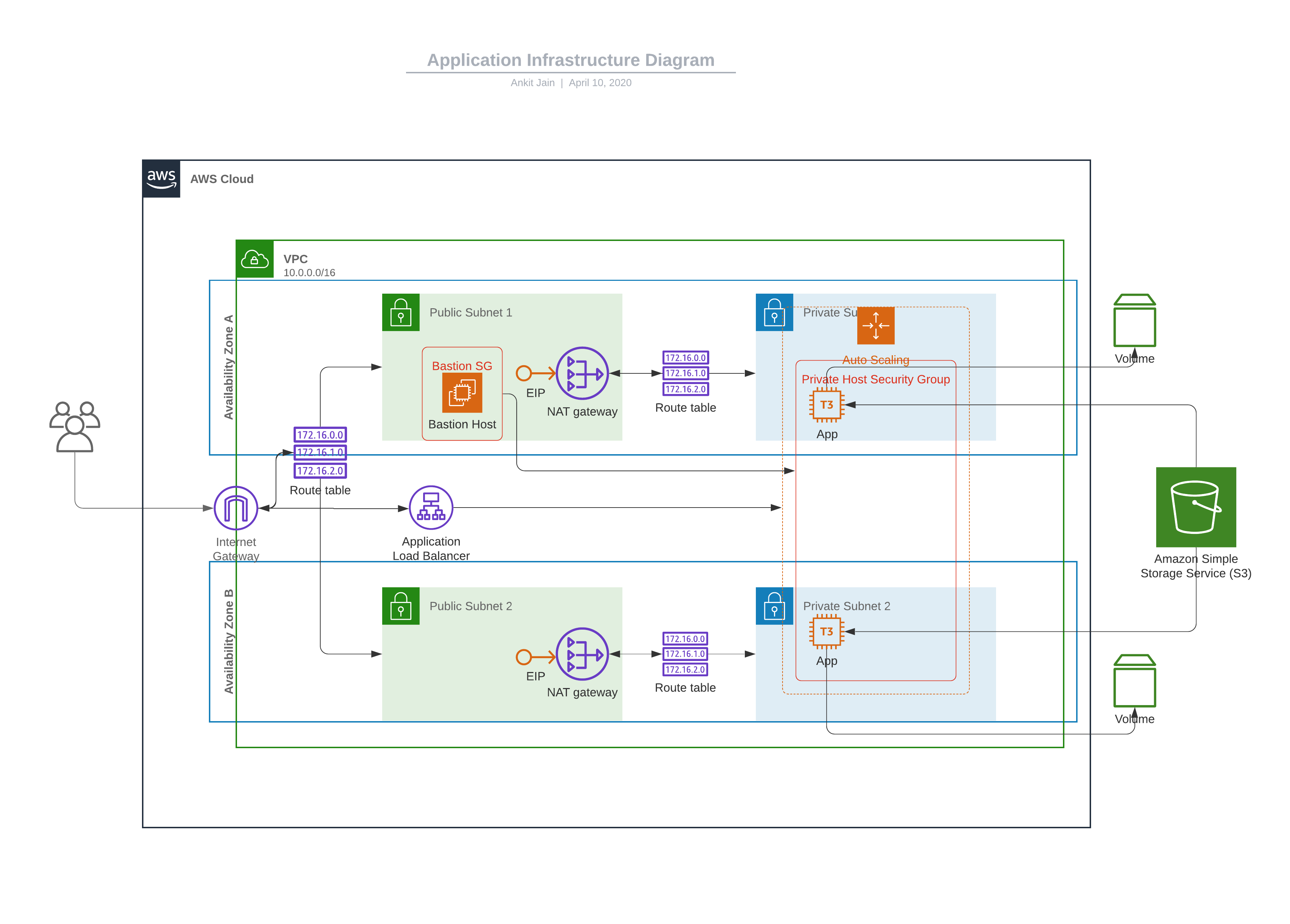
This template deploys a VPC, with a pair of public and private subnets. It deploys an internet gateway, with a default route on the public subnets. It deploys a NAT gateway and default routes for them in the private subnet. It is also creating Bastion instance with which we can ssh into private subnet instances using aws ssm.
Website Link - Udagram
For creating the network, run the network.yaml template with parameters file network.json
-
Create a network setup by running the below command.
aws cloudformation create-stack --stack-name <stack_name> --parameters file://network.json --template-body file://network.yaml
-
Delete the stack by running the below command.
aws cloudformation delete-stack --stack-name <stack_name>
For creating the sample website using Application Load Balancer attached to an Auto Scaling group and bastion host, run the server.yaml template with parameters file server.json
-
Create a server setup by running the below command.
aws cloudformation create-stack --stack-name <stack_name> --parameters file://server.json --template-body file://server.yaml --capabilities CAPABILITY_IAM
-
Delete the stack by running the below command.
aws cloudformation delete-stack --stack-name <stack_name>
- VPC
- 2 Public Subnets
- 2 private Subnets
- NAT Gateways
- Internet Gatway
- Route table for public and private subnet with asssociation.
- ALB LoadBalancer
- Launch Configuration
- Autoscaling Group
- Listerner added to ALB
- Target Group
- t2.medium instance (2 vCPU and 4 GiB of RAM) with 10GB EBS Volume
- Bastion Instance for SSH
- SSM Agent for ssh to private instances from Bastion instance.
- Outputting Loadbalance endpoint with
http://
Why you defined t2.micro instance type rather than t3.small or better?
I thought we need to use 1 vCPU and 1 GiB of RAM and using T2 over T3 is because it is less costly. As T3.medium and T2.medium has same cost but T3 class has better performance over T2 so preferring T3.