working on implementation of JWT with email OTP
- Implementation is complete
- Sliding token concept is not covered
- will update and rearrange documentation shortly
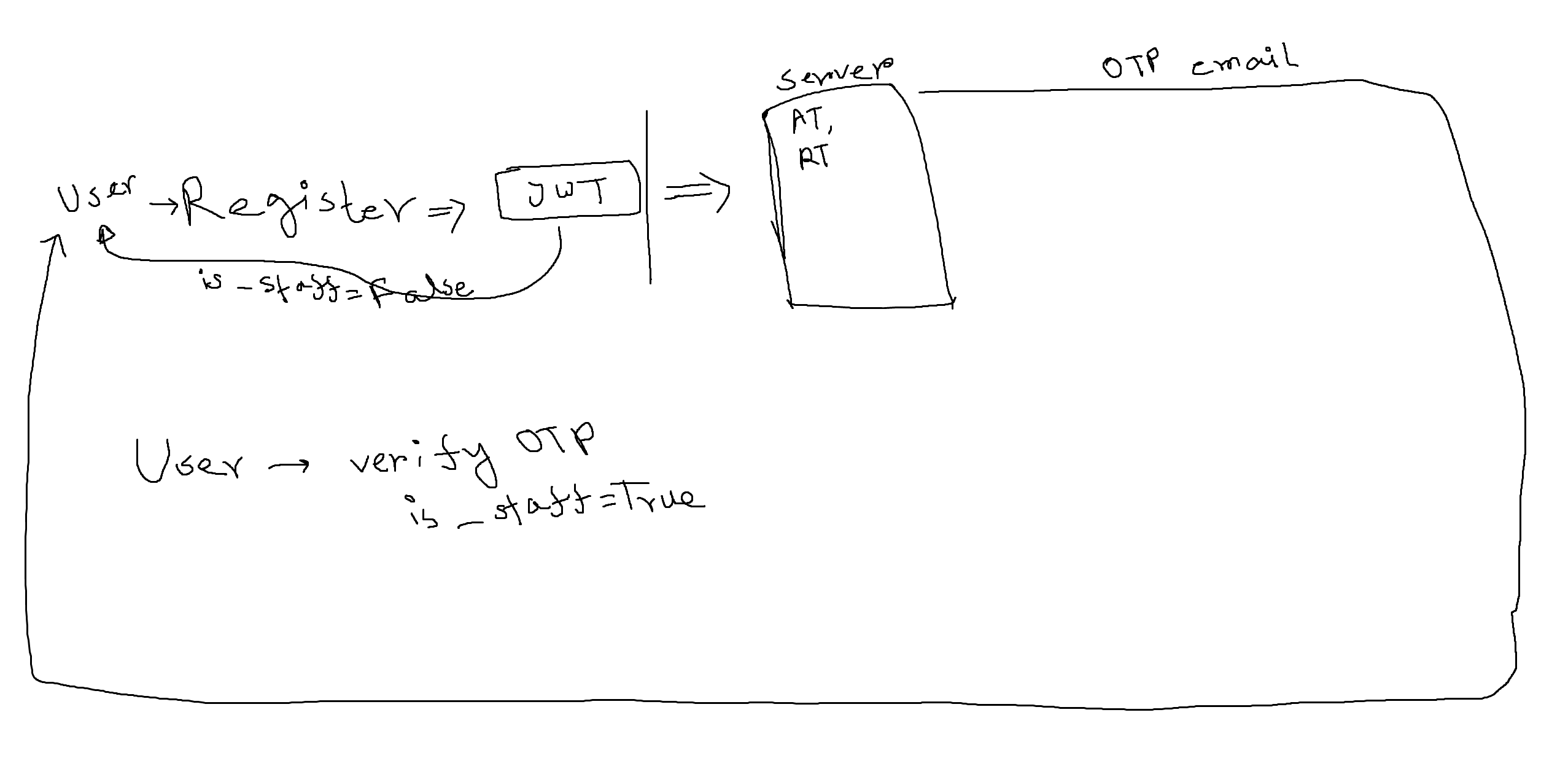
- User registers, gets an active account with ACCESS_TOKEN and REFRESH_TOKEN
- User also receives a mail with an OTP
- User goes to otp verification endpoint and verifies otp
- User gets better access
- User perform operations with protected data
- User ACCESS_TOKEN expires
- User gets new ACCESS_TOKEN and new REFRESH_TOKEN, requesting with the current REFRESH_TOKEN to refresh token endpoint
- User's old REFRESH_TOKEN gets blacklisted
- User logs out, current REFRESH_TOKEN gets blacklisted
| ACTIONS | HTTP METHODS | ENDPOINTS |
|---|---|---|
| LOGIN WITH AN ACCOUNT | POST | /api/login/ |
| VERIFY ACCOUNT WITH OTP | POST | /api/verify/ |
| REFRESH TOKEN | POST | /api/refresh/ |
| LOGOUT OF AN ACCOUNT | GET | /api/logout/ |
| REGISTER FOR AN ACCOUNT | POST | /api/register/ |
| EXPERIMENT WITH AN ENDPOINT | POST | /api/experiment/ |
├─ images
│ └─ note1.png
├─ jwt_with_email_otp
│ ├─ asgi.py
│ ├─ settings.py
│ ├─ urls.py
│ ├─ wsgi.py
│ └─ __init__.py
├─ LICENSE
├─ manage.py
├─ README.md
├─ requirement.txt
└─ users
├─ admin.py
├─ api
│ ├─ serializers.py
│ ├─ urls.py
│ └─ views.py
├─ apps.py
├─ emails.py
├─ models.py
├─ tests.py
├─ views.py
└─ __init__.py
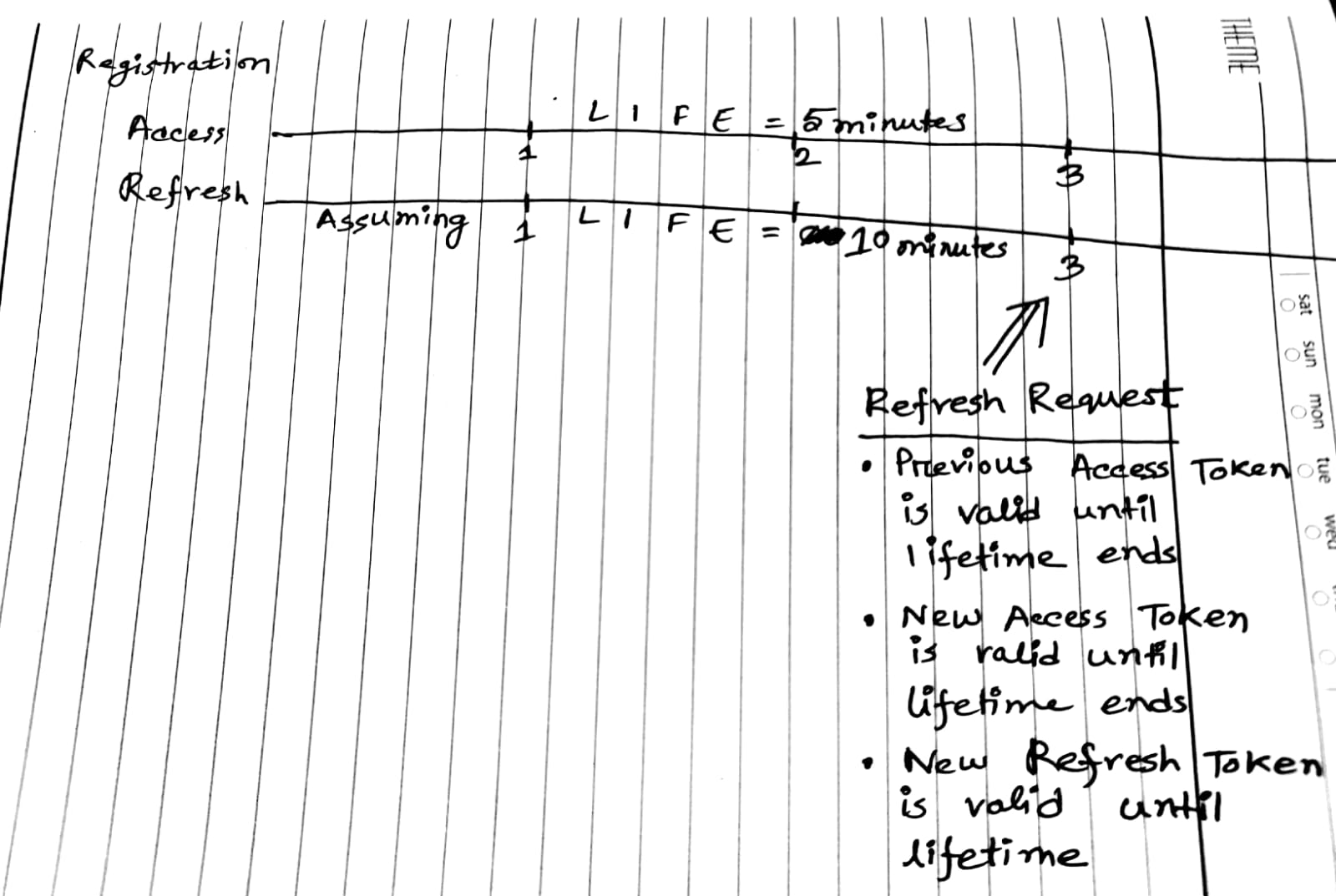
- RefreshView Endpoint sends back ACCESS_TOKEN only
- Same Refresh Token can be used to generate multiple access tokens
- Lifespan = Refresh Token Lifetime
- RefreshView Endpoint sends back both ACCESS_TOKEN and REFRESH_TOKEN
- Same Refresh Token can be used to generate multiple access tokens and refresh tokens
- Lifespan = Refresh Token Lifetime
- New Refresh Tokens have new extended lifetime
- RefreshView Endpoint sends back both ACCESS_TOKEN and REFRESH_TOKEN
- Same Refresh Token cannot be used anymore
- New Refresh Tokens can be used to generate multiple access tokens and refresh tokens