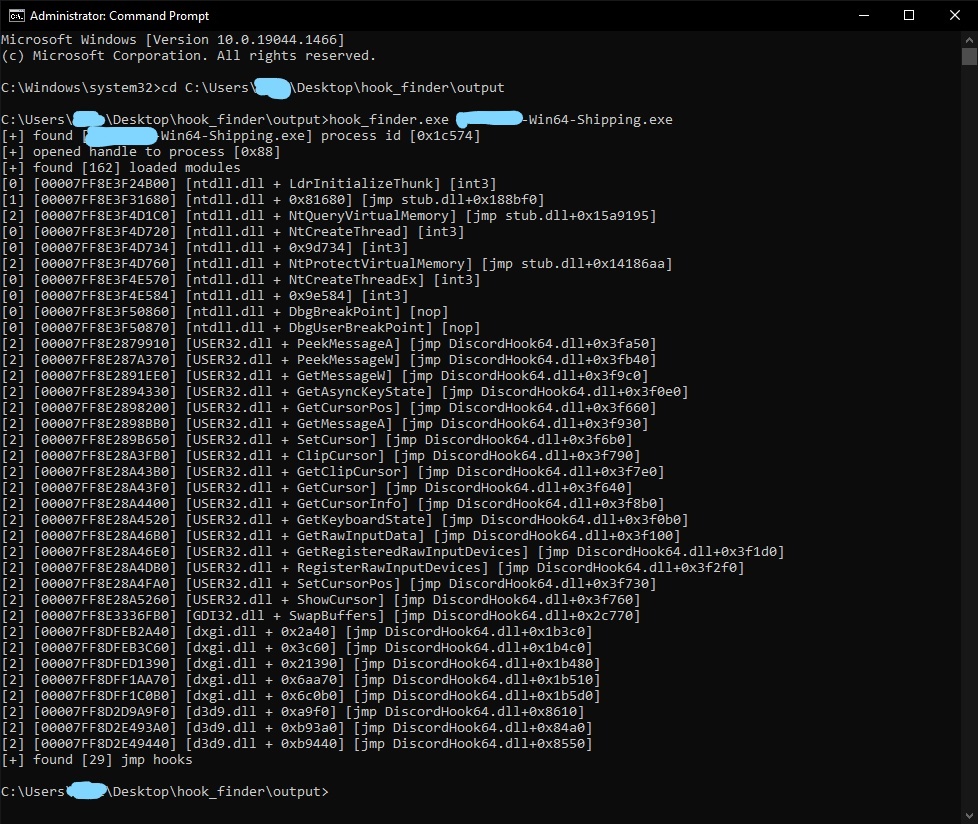
hook-scanner
Scans all modules in target process for jmp/int3 hooks dissassembles then and follows jmps to destination.
Procedure
- The process enumerates every modules .text section and dissassembles each instruction using zydis dissassembler
- The instruction is compared against the module on disk to check for patch.
- If it is a patched instruction checks if it is a jmp and proceeds to resolve the jmp destination
- If the jmp destination leads to an absolute jmp it follows it and prints the result (module + offset)
- It can be customized to decent int3 (breakpoint hooks) and other patches like nop
- Before logging gets symbol name of remote function for easier/cleaner analysis
- It can be customized to skip modules that you don't want to get scanned here
Example Usage
Note: this project was coded in 1 day so it might have some bugs (open ticket)
Usage
hook_scanner.exe process.exe