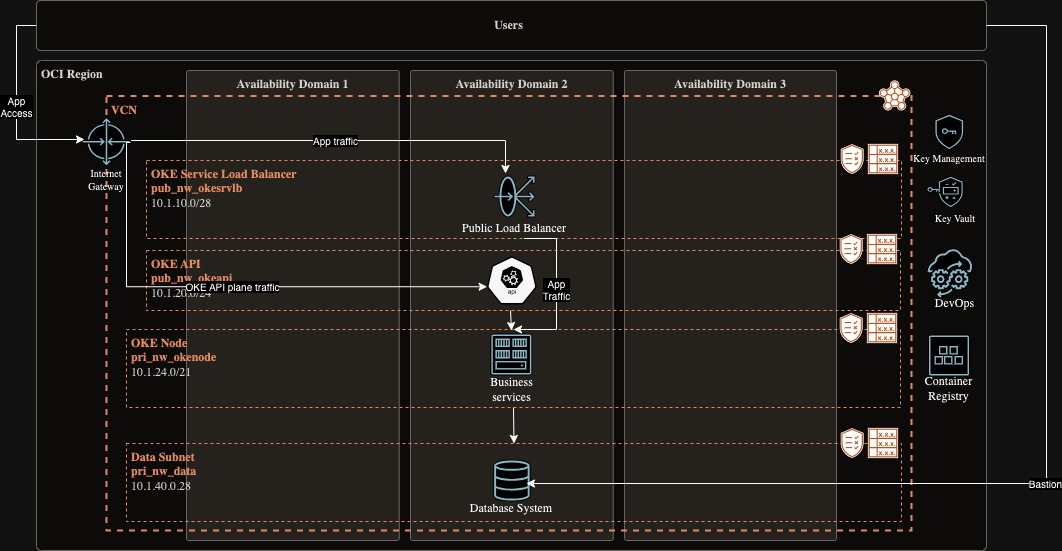
Deploy a minimalistic landing zone and foundation for containerized application deployment on Oracle Cloud Infrastructure (OCI) levearging the following cloud capabilities:
-
Compartment
-
Vault
-
Networking
-
Kubernetes
-
Database
-
Bastion
-
OCI DevOps
One will have a compartment created in a region of choice, with VCN and 3 tiers of subnets with security and route rules, OKE cluster with access to Database subnet with MySQL DB. A vault with key and encrypted credentials to access the database. A bastion setup to access the database. The OKE cluster is having Public Kubernetes API Endpoint, Private Worker Nodes, and Public Load Balancers.
The modules directory has the modules for:
| Compartment |
Root and sub-compartments |
| Vault |
Vault, Key Management & Secret |
| Networking |
VCN, Internet, NAT and Core Gateways, Subnets, Ingress/Egress Rules, Security lists and Route Tables |
| OKE |
Kubernetes Cluster |
| Database |
MySQL Database |
| Bastion |
Bastion setup for database access |
| DevOps |
Notification topic, Project, Artifact Repository, Container Registry and Code respository |
| config.tf |
consists of terraform and providers configuration. If not using the OCI Shell, please configure your OCI access key in this file or use TF_VARS. |
| terraform.tfvars |
consists the values to the configurations to be done. As a best practise, it can be moved to a different vars file as well. |
| variables.tf, main.tf and outputs.tf |
are self explanatory :) |
Login to your oracle cloud shell and clone the repository. If not using the cloud shell, modify the config.tf to include your OCI key and then execute the below:
terraform init
terraform plan
terraform applyOnce, everything is deployed, one can test the deployment with the scripts in hello-world-k8s directory. Execute to deploy Ingress controller (Nginx in this case), Hello World workload and configure the ingress controller.
Pick the external IP from the output and curl it to get the response from the pods OR try it in your favourite web browser.
./hello-world-k8s/deploy-e2e-hello-world.shOnce your tests are done, time for cleanup! Execute the below script
./hello-world-k8s/remove-e2e-hello-world.shIf you have got a suggestion, add it here via a MR or even better, make the change and raise a MR
-
✓ Removal of local blocks where possible
-
✓ Restructure variable for code repesitories in DevOps module
-
✓ Inclusion of some output variables
-
❏ Restructure variable for the DevOps module
-
❏ Variable for availability_domain in OKE module
-
❏ Simplify oke_node_pool_image_id for OKE Nodes
OCI Terraform team has done a great job in creating reference architectures for various patterns of Landing Zones in OCI but they are all for large scale, enterprise wide implementations and landing zones should be like that indeed. If one is interested in deploying in a limited scale, I found the engineering effort to be comparatively high to tailor it down and also in the future from a maintenance and operations standpoint. You might want to deploy in limited scale when your contractual construct or service models with which you serve your target customer varies and does not allow you the full play but you still want to have some standards with the right industry practises and secure.
Well, since I was getting acquainted to Oracle Cloud Infrastructure (OCI), found some good resources online: