I was one of the 300 CNAAND recipients chosen from the 15,000 participants in the SUSE Cloud Native Foundations Scholarship Program. This repo contains a collection of project deliverables from my CNAAND course work.
A portion of project code and artifacts are stowed in secured storage to discourage improper access. For legitimate needs, please email to request access.
1. TechTrends
- Package and deploy a fully functional online news sharing website application components to Kubernetes using
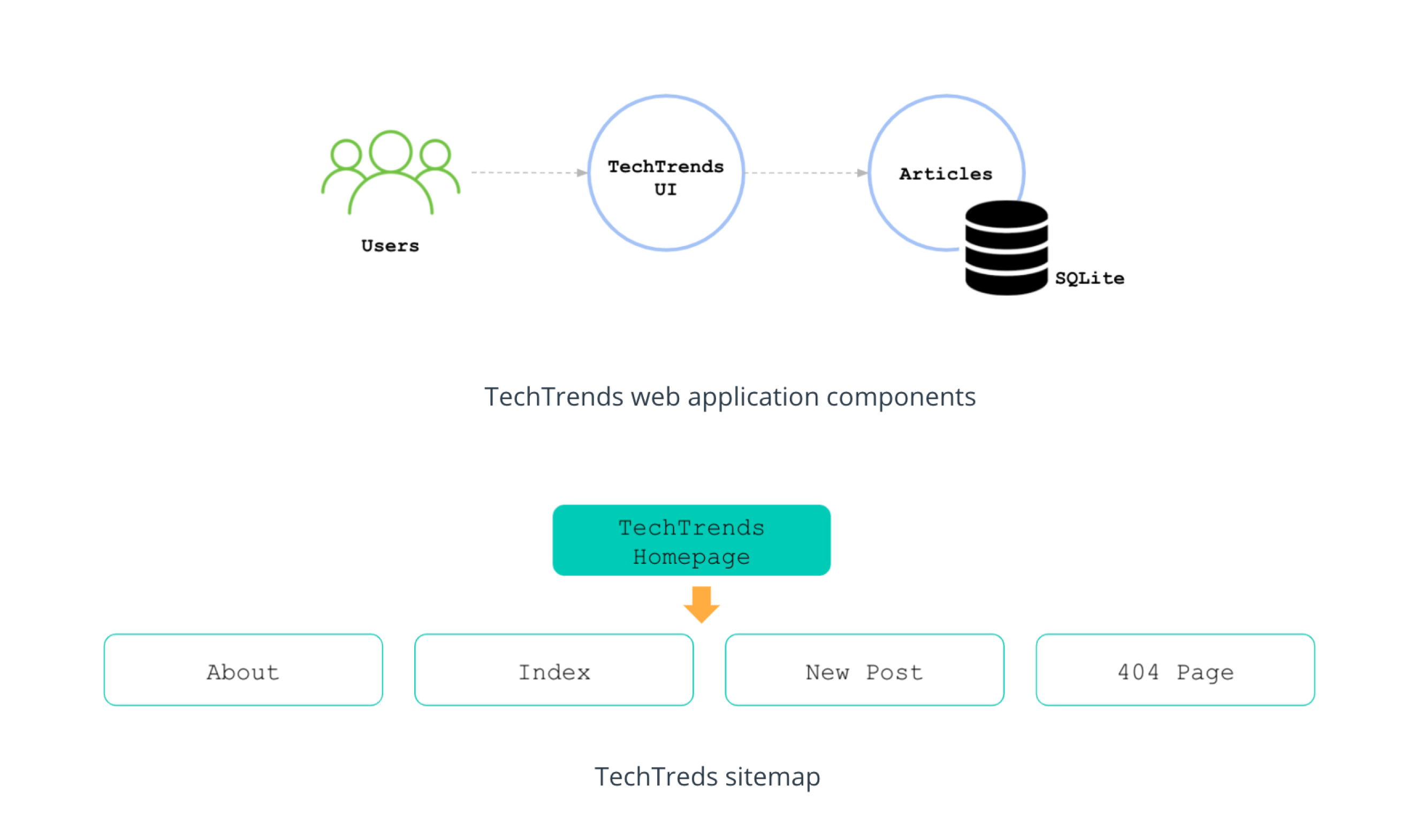
CI/CDpipeline, with Docker image build, k3s, Kubernetes declarative manifests, Helm chart and ArgoCD for staging and production environments. The web application components and site map are as shown below (Image credit: Udacity CNAAND Nanodegree):
Add health check and logging to the web app, leverage Github Action workflow and ArgoCD to implement a CI/CD pipeline to propage the web app through 3 kubernestes (
sandbox, staging and production) environments, enabling the app to be fully tested, validated in an orderly manner before reaching the end-users fault free.Project specification: refer to this rubric
Project code and artifact repository: click here
Tool: VirtualBox, Vagrant, Git, Python, Docker, k3s, kubernetes, Helm, ArgoCD
Artifact: github workflow file, app.py, docker_commands, k8 declarative manifests, ArgoCD deployment manifests
2. UdaConnect
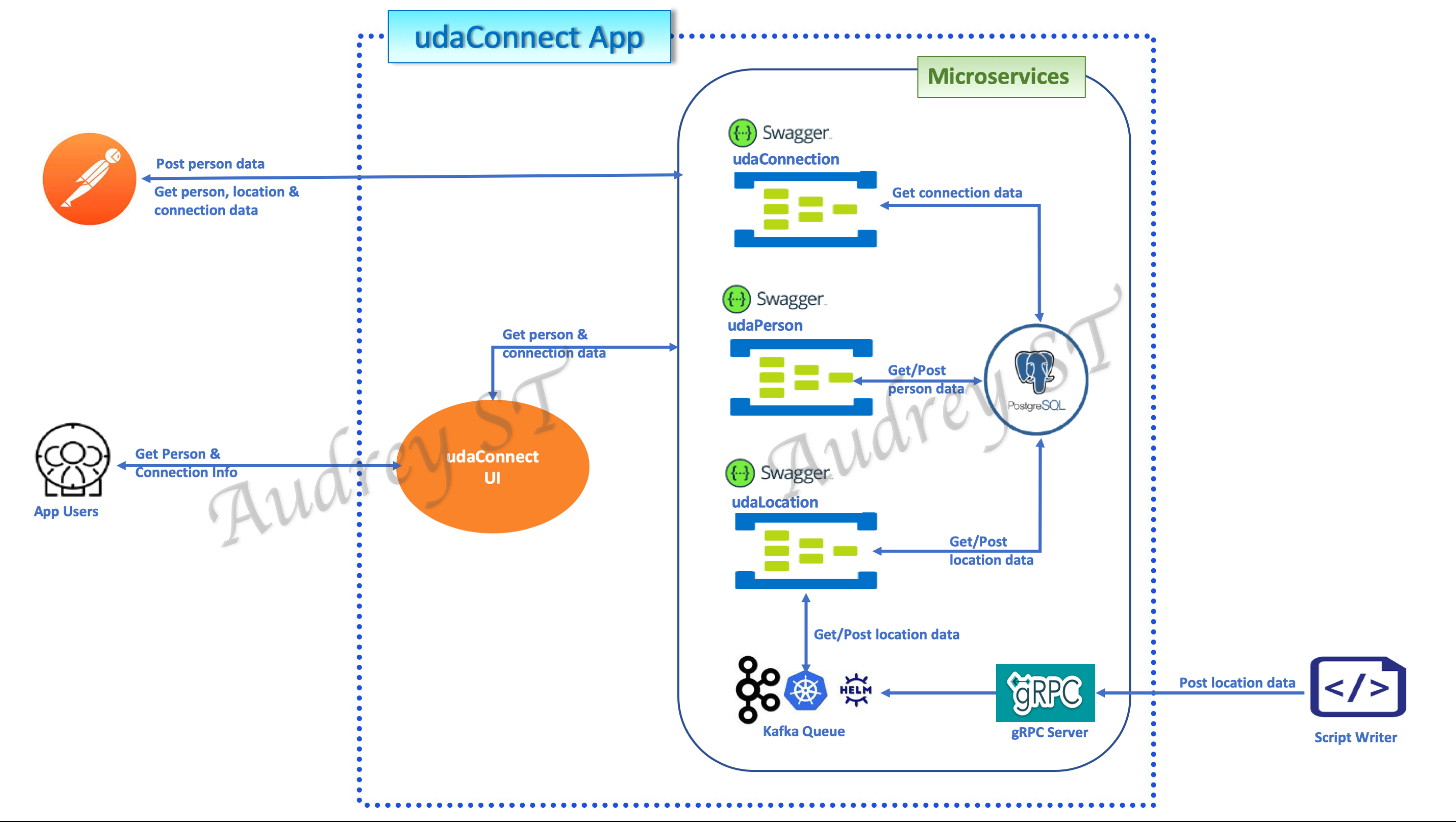
- Refactor a POC application (that ingests location data from mobile devices and identifies users in closed geographic proximity) into a microservice architecture using the appropriate message passign techniques, and deliver a MVP (Minimum Viable Product) capable of ingesting a large volume of location data. The resulting workflow is as shown below:
Refactor the monolith
udacConnectapp into microservices consist of a Person, Location and Connection API, a frontend UI, Postgres DB, Kafka and gRPC services.Project specification: refer to this rubric
Project code and artifact repository: click here
Tool: Docker, VirtualBox, Vagrant, k3s, Helm, kubectl, Python, Flask Framework, Postgres, Postman, Kafka, gRPC, OpenAPI, Swagger
Artifact: architecture diagram, architecture decisions, refactored app deployment manifests, refactored app code, postman.json
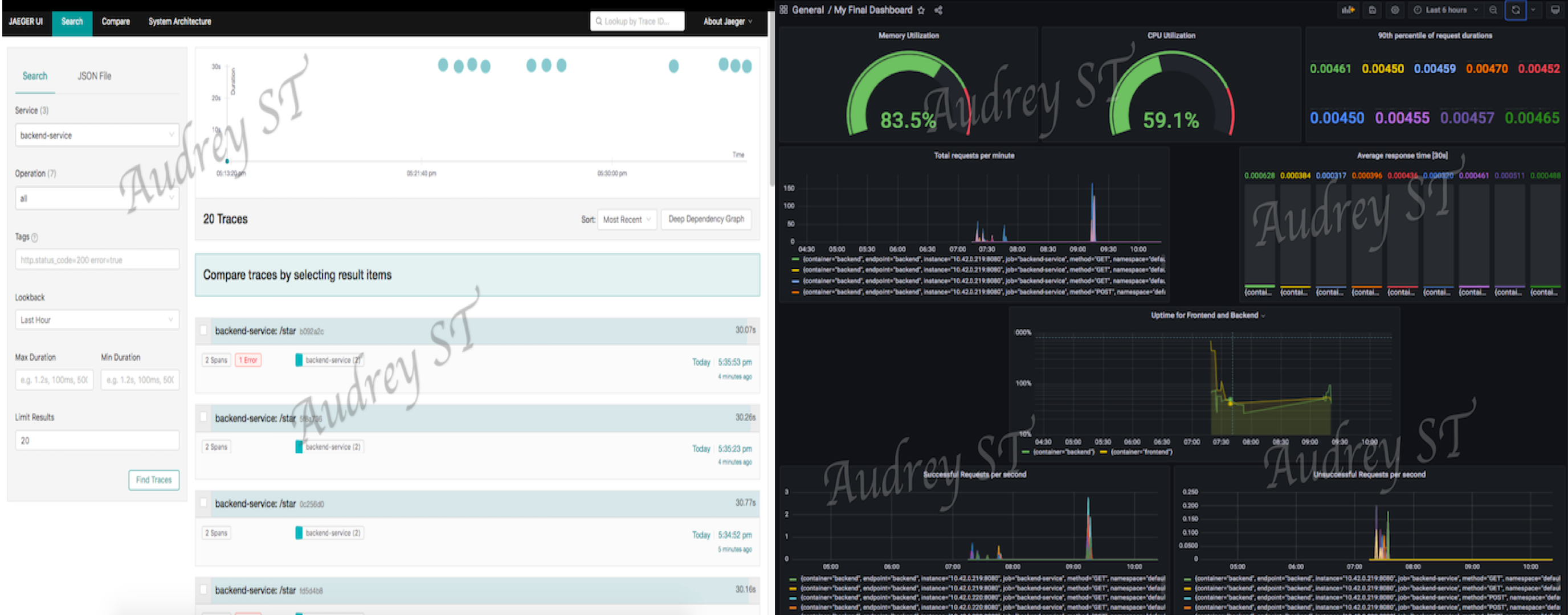
- Implement distributed tracing with Jaeger, Kubernetes resource monitoring with Prometheus and visualize the metrics with Grafana. A sample view of the artifacts is as shown below:
Utilize
Jaeger Operator, Jaeger instance, OpenTelemetry Flask InstrumentationandOpenTelemetry Jaeger Thrift Exporterto implement distributed tracing with Jaeger on Kubernetes. LeveragePrometheus, Prometheus Flask Exporterwith multiprocessing enabled for metrics collection, andGrafanato create a dashboard for the metrics.Project specification: refer to this rubric
Project code and artifact repository: click here
Tool: Docker, VirtualBox, Vagrant, k3s, Helm, Jaeger Operator, OpenTelemetry Flask Instrumentation, OpenTelemetry Jaeger Thrift Exporter, Prometheus, Prometheus Flask Exporter, Grafana, PromSQL
Artifact: service monitor manifests, app deployment manifests, README.md
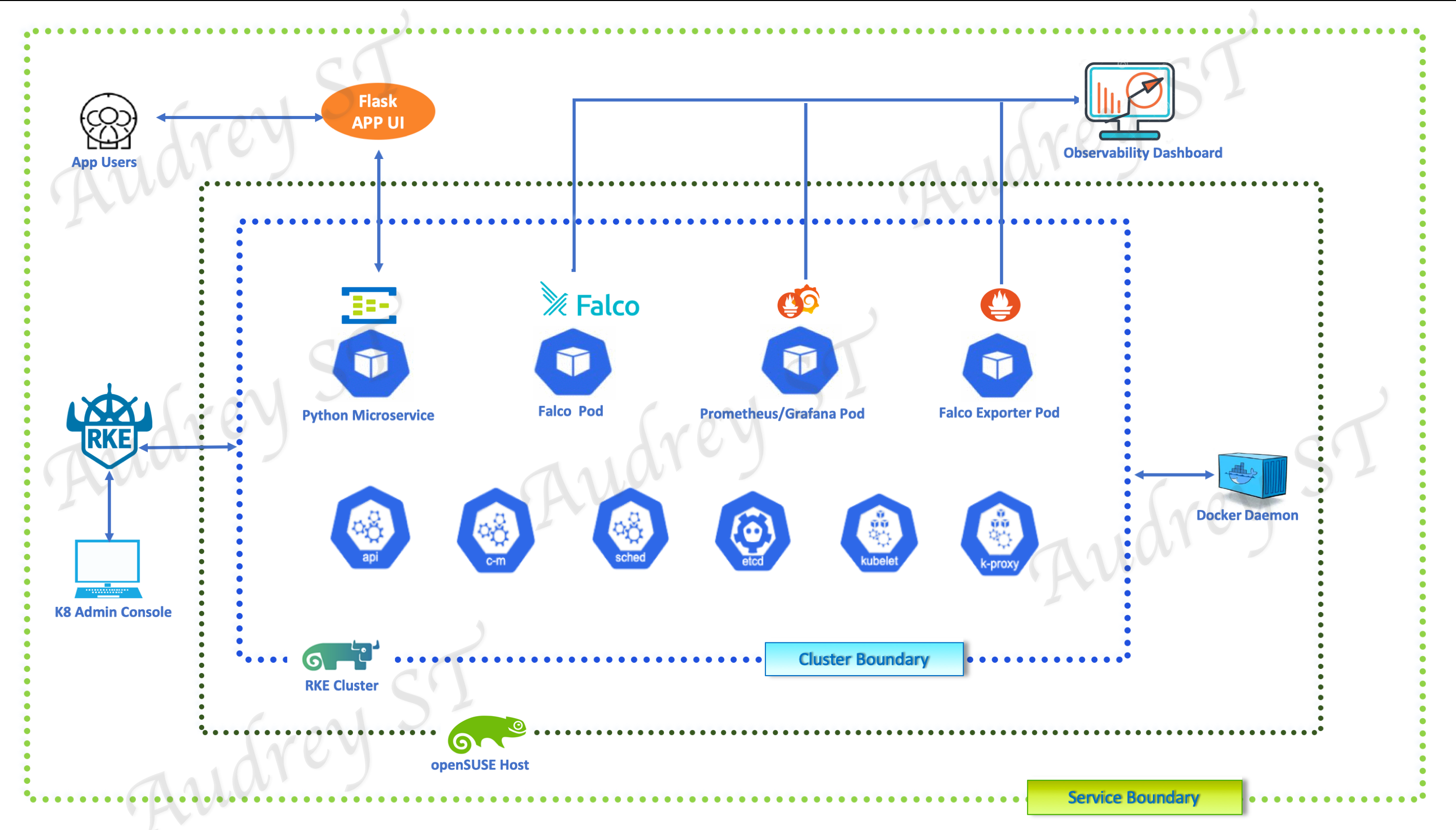
- Threat model and harden a microservice environment on a RKE cluster, implement runtime monitoring with Falco, Prometheus and Grafana. The architecture diagram below depicts the service and security boundaries of the microservice environment:
Apply container and Kubernetes cluster threat modeling techniques and toolings leanred to build a secure and hardened Microservice environment. Leverage Falco, Prometheus and Grafana to equip the environment with runtime monitoring and threat escalation measures.
Project specification: refer to this rubric
Project code and artifact repository: click here
Tool: Docker, VirtualBox, Vagrant, RKE, Helm, kubectl, Python, Grype, Falco, Falco Exporter, Prometheus, Grafana, PromSQL
Artifact: security architecture diagram, thread modeling, incident response, app.py
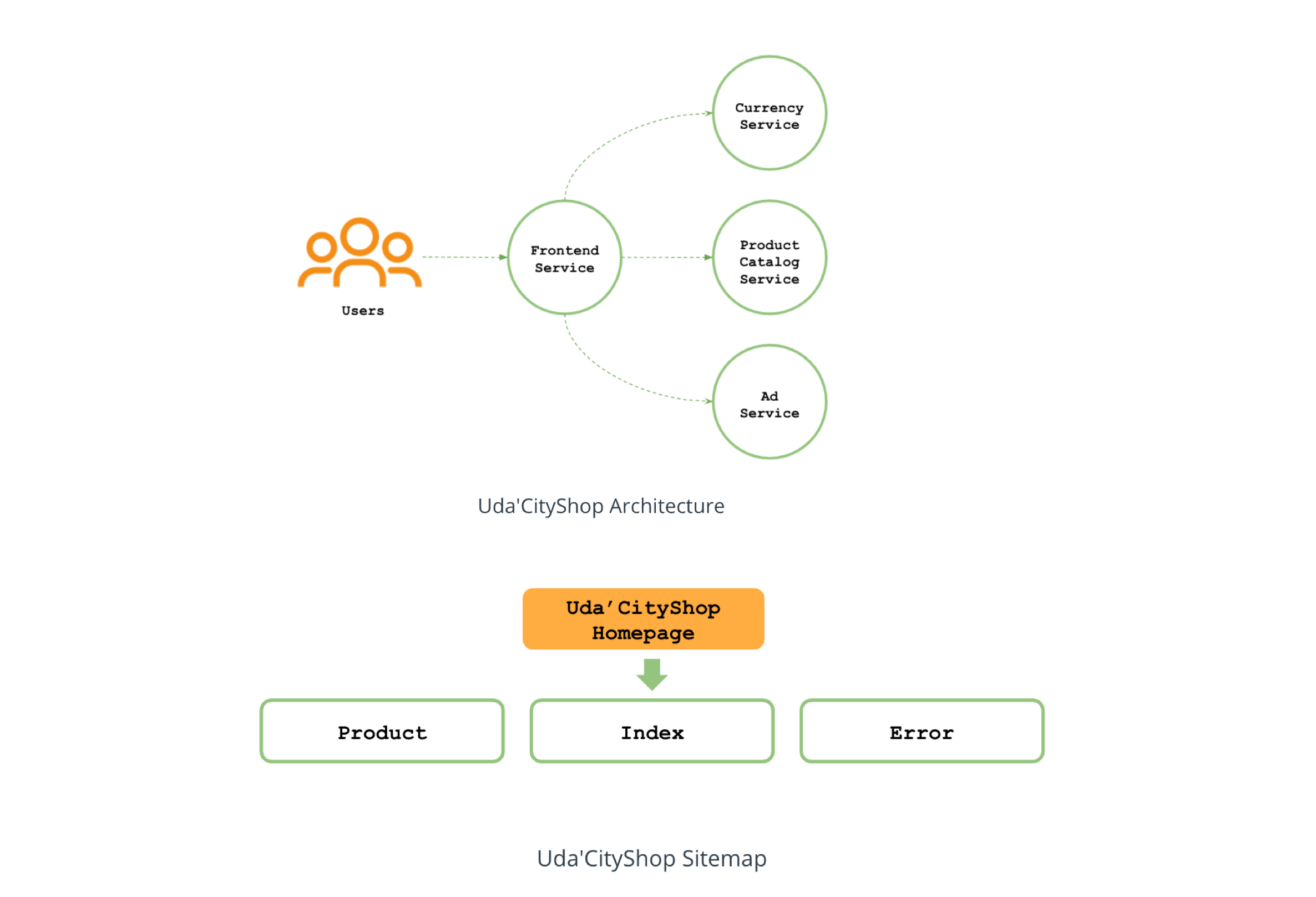
- Deploy a web application composed of multiple microservices written in different programming languages to Kubernetes using a CI/CD pipeline, observe, analyze and implement changes that would optimize the existing components. The web application components and site map are as shown below (Image credit: Udacity CNAAND Nanodegree):
Streamline deployment of the web app to non production and production Kubernetes environments using a CI/CD pipeline. Refactor the Java Ad microservice and rewrite it in Python to reduce the consumption of CPU and memory resources.
Project specification: refer to this rubric
Project code and artifact repository: click here
Tool: VirtualBox, Vagrant, Git, Python, Docker, k3s, Kubernetes, Helm, ArgoCD, gRPC, Prometheus, Grafana, PromSQL
Artifact: github workflow files, Adservice-v2 code, frontend code, grafana dashboard json, grafana nodeport yaml, argocd manifests, Kubernetes manifests, demo.proto