The purpose of this repository is to demo how to ingest Amazon GuardDuty findings into Splunk Enterprise.
AWS CloudFormation template (main.yaml) will deploy Splunk Enterprise and Splunk GuardDuty Processor AWS Lambda Function.
- Splunk Enterprise subscription in AWS Marketplace
Click on the Launch Stack button below to launch the CloudFormation Stack to set up the Amazon GuardDuty to Splunk Demo in the region of your preference, by default this demo will be deployed in us-west-2 (Oregon) region.
Provide a stack name eg amazon-guardduty-to-splunk-demo.
You can launch the same stack using the AWS CLI. Here's an example:
aws cloudformation create-stack --stack-name amazon-guardduty-to-splunk-demo \
--template-body file://main.yaml \
--capabilities CAPABILITY_IAM
Once stack creation is completed, it will output the Splunk DNS Name, Username and Password under "Outputs" tab of your stack.
- Settings > Data Inputs
- Click HTTP Event Collector
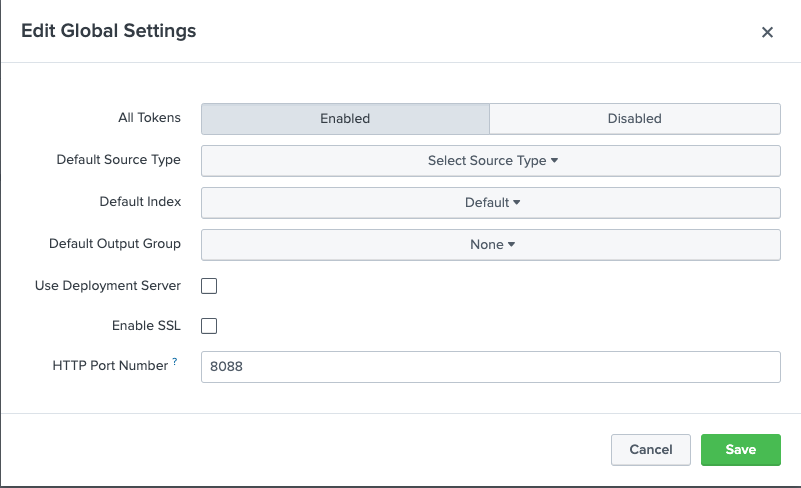
- Click Global Settings
- Disable SSL (for Demo Purposes, in production environments keep SSL enabled)
- Click Save
- Click New Token
- Give it a Name (such as splunk-guardduty-processor-token)
- Click Next
- Leave everything as default
- Click Review and Submit
- Copy your Token Value
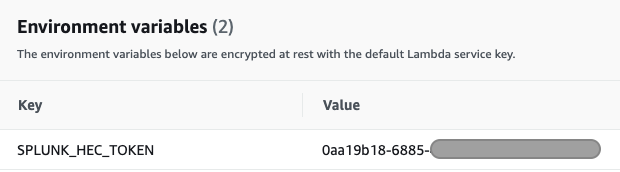
- Go to your Lambda Function
- Under Environment variables replace the value of SPLUNK_HEC_TOKEN key with your token.
Now it is time to generate some Amazon GuardDuty Findings using "Generate sample findings" button on Settings page.
Findings are automatically sent to CloudWatch Events, please wait few minutes to see the findings in Splunk.
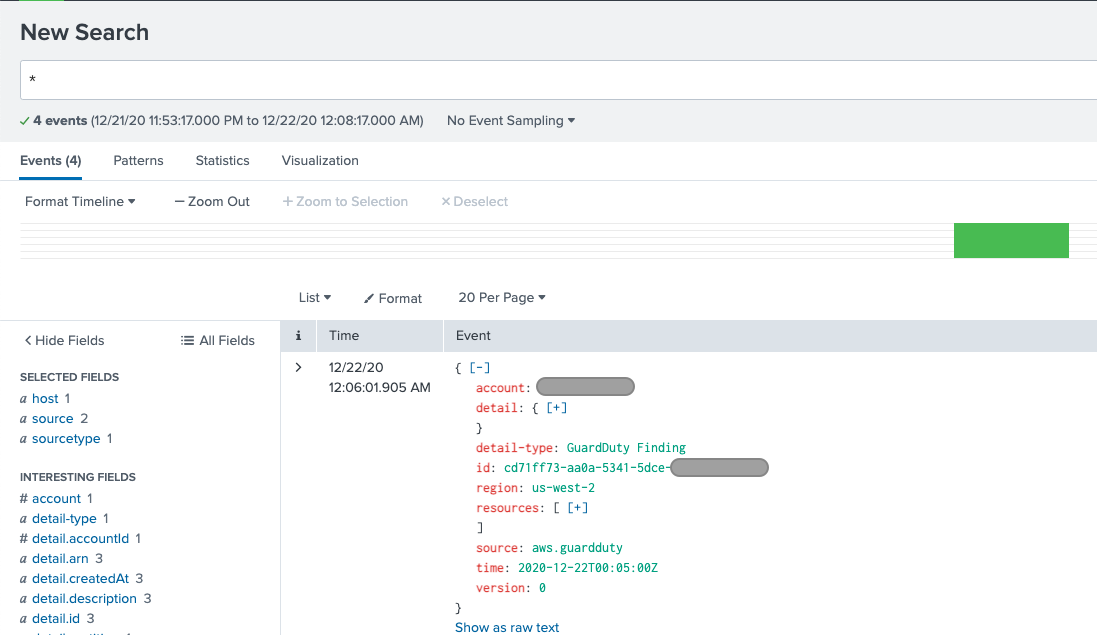
Go to Splunk search and write "*" as in the following image to search all messages in all indexes.
After completing your demo, delete AWS CloudFormation Stack using AWS Console or AWS CLI:
aws cloudformation delete-stack --stack-name amazon-guardduty-to-splunk-demo
See CONTRIBUTING for more information.
This library is licensed under the MIT-0 License. See the LICENSE file.