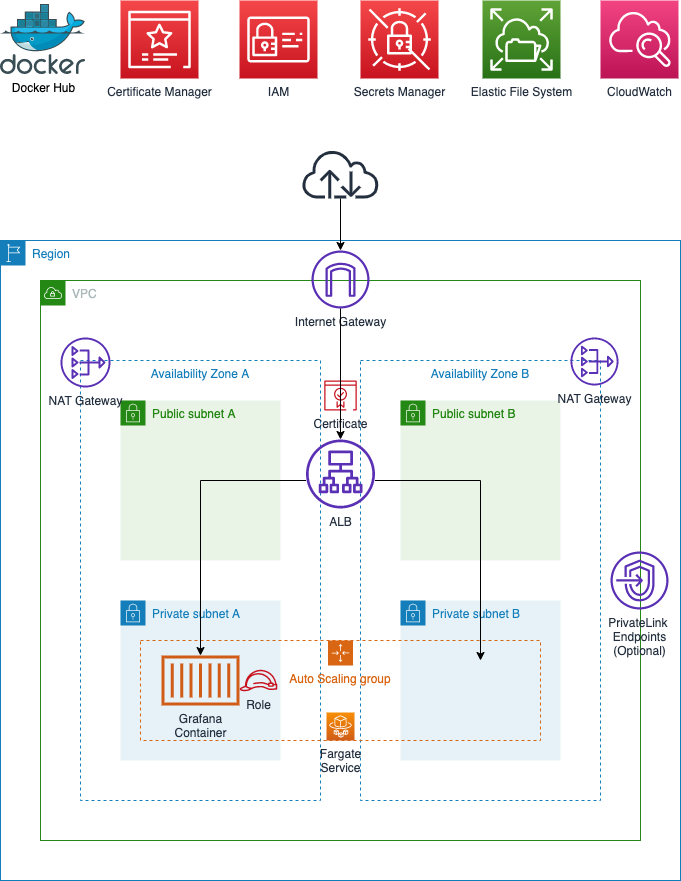
This project aims to deploy a resilient Grafana container on AWS Fargate using the Grafana Docker Image on DockerHub with no modifications/rebuilds of the container and minimal post deploy configuration of Grafana.
- The AWS CDK is used for infrastructure-as-code and deployment.
- Persistance is provided by Amazon EFS and AWS Fargate support.
- High Availability is supported but Autoscaling of the container is not provided at this point i.e. the ECS/Fargate service will ensure that only one Grafana container is online between Availability Zone A or B.
- Access for the Grafana container to CloudWatch is configured with an IAM Role, preventing the need to configure Access/Secret keys
- The initial admin password is securely generated and configured using Secrets Manager
- A TLS certificate is automatically created deployed to the Application Load Balancer using AWS Certificate Manager enabling secure HTTPS Only communication with the Grafana portal
- Optional PrivateLink endpoints can be added for increased security
This project requires that you have already registered a domain and configured a hosted zone in Route 53. Once this is completed you will need the domainName, hostedZoneId and zoneName to continue the deployment.
- Install git
- Install Node.js and NPM
- An AWS account
- AWS CLI
- AWS CLI configured
- AWS CDK
git clone https://github.com/aws-samples/aws-cdk-grafanacd aws-cdk-grafana
npm install- Deploy the project using the following command in the root of the aws-cdk-grafana folder (replacing the domainName, hostedZoneId and zoneName with the correct values for your environment)
cdk deploy --context domainName="grafana.example.com" --context hostedZoneId="Z0123456789ABCDEFGHIJ" --context zoneName="example.com"- Wait for the new service to provision (This takes 5-10 mins)
- Retrieve the admin password from Secrets Manager
- Log into Grafana (url was output by the CDK Deploy), username =
adminand use the password you retrieved from Secrets Manager - In Grafana add AWS CloudWatch as a Data Source: Configuration, Data Sources, CloudWatch, set the region to the region you wish to monitor e.g. us-east-1. Leave the other fields blank and click Save and Test.
- On the Dashboards tab you can add one of the prebuilt Dashboards, e.g. AWS Lambda.
You can test Grafana config persists past a reboot by simply terminating the task in ECS, let a new task launch (a few seconds) and then logging back into Grafana and all of your configuration of the Dashboards will have persisted.
Note changes to the Admin password in Secrets Manager will not be reflected in Grafana as this is set only once at initial deploy time.
PrivateLink endpoints can be added using the following command. This will incur additional cost for the endpoints, but will prevent CloudWatch, EFS (Elastic File System) and Secrets Manager traffic from traversing the public internet.
cdk deploy --context domainName="grafana.example.com" --context hostedZoneId="Z0123456789ABCDEFGHIJ" --context zoneName="example.com" --context enablePrivateLink=="true"See CONTRIBUTING for more information.
This library is licensed under the MIT-0 License. See the LICENSE file.