This project is being archived as of Jan 2024. The application has been tested using CDK 2.122.0 and NodeJS 18.
- Outcome
- What are we building?
- What are the pre-requisites?
- How can I deploy the stack?
- How can I setup a site-to-site VPN?
- Let's cleanup
- Security
- License
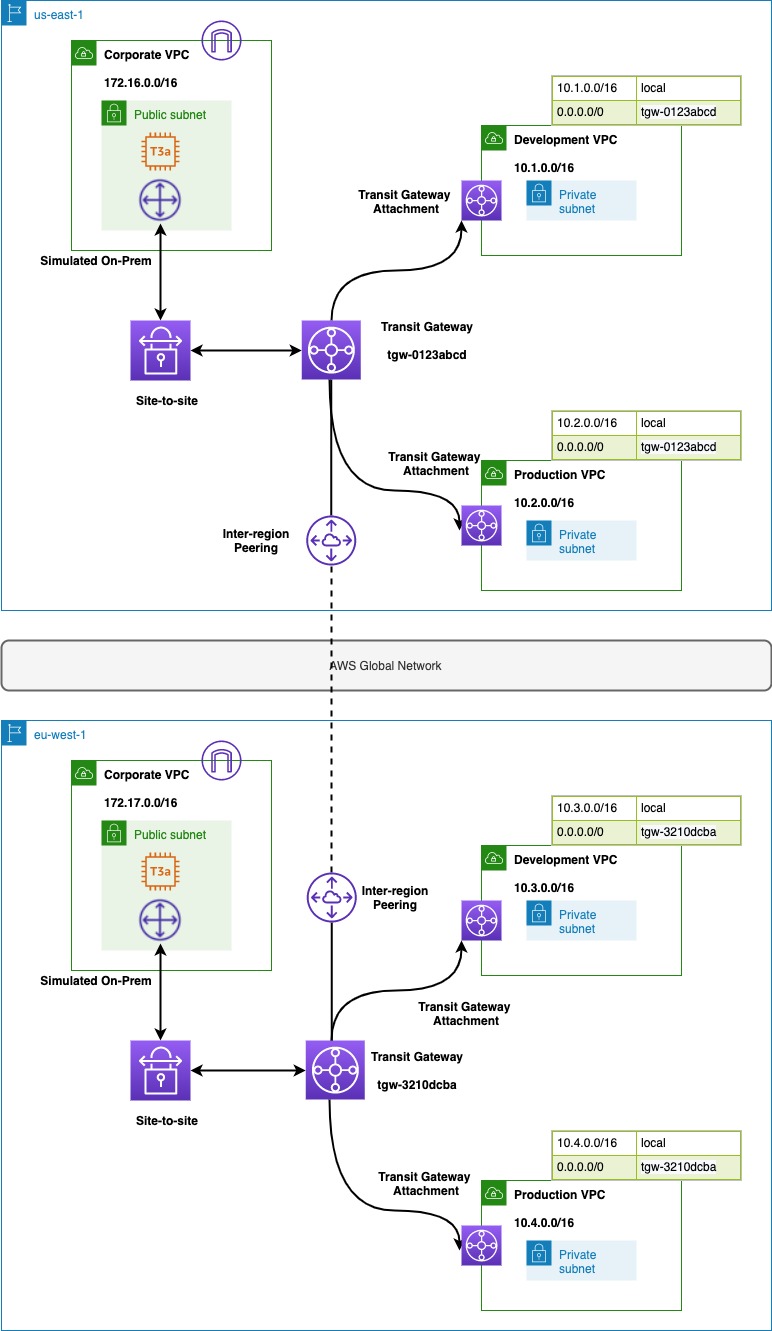
We will build a global network with development, production and on-prem networks in us-east-1
and eu-west-1. The infrastructure will be built using a combination of CDK, AWS CLI and AWS
Console.
Below routes are allowed by this architecture
| Source | Destination |
|---|---|
| DevelopmentUS | DevelopmentEU |
| ProductionUS | ProductionEU |
| DevelopmentUS | CorpUS |
| ProductionUS | CorpUS |
| DevelopmentEU | CorpEU |
| ProductionEU | CorpEU |
Note: For the on-prem simulation, we will leverage the aws-samples
- Install the following
brew install jq npm i -g -f aws-cdk@2.122.0
- You have configured AWS CLI using
aws configure - The role being used from CLI has the permissions required for resources being created by CDK
- The CDK params are stored here. Update them if needed.
- Let's build the code
npm install npm run build npm run test
We build the below resources -
- On-prem CIDR for the site-to-site VPN setup
- EIP for the site-to-site VPN
- Transit Gateway
- Customer gateway
- Site-to-site VPN
- Development VPC
- Production VPC
- Development VPC routing
- Production VPC routing
- EC2 instance in Development and Production subnets
- VPC endpoints to access EC2 via SSM
- TransitGateway routing tables
- TransitGateway attachment
- TransitGateway association and propagation
- Global network for visualize the traffic using route analyzer
The script will build the stack in us-east-1 and eu-west-1.
If you need to use different regions, please update the deploy.sh
Note: The transit gateway peering and acceptance is handled in the shell script
./bin/scripts/deploy.sh- Follow the steps provided here - https://github.com/aws-samples/vpn-gateway-strongwswan
- The previous stack has set up the below resources
- Transit Gateway
- Customer Gateway
- Site-to-Site VPN
- EIP
- Below commands will return the EIP allocationID and Transit Gateway ID
- This demo was tested with Pre-Shared Key-Based Authentication
export AWS_DEFAULT_REGION=us-east-1
aws cloudformation describe-stacks --stack-name TransitGatewayPeeringDemo --query 'Stacks[*].Outputs[?ExportName==`eipAllocationId`].OutputValue' --output text
aws cloudformation describe-stacks --stack-name TransitGatewayPeeringDemo --query 'Stacks[*].Outputs[?ExportName==`TransitGatewayId`].OutputValue' --output text
export AWS_DEFAULT_REGION=eu-west-1
aws cloudformation describe-stacks --stack-name TransitGatewayPeeringDemo --query 'Stacks[*].Outputs[?ExportName==`eipAllocationId`].OutputValue' --output text
aws cloudformation describe-stacks --stack-name TransitGatewayPeeringDemo --query 'Stacks[*].Outputs[?ExportName==`TransitGatewayId`].OutputValue' --output text
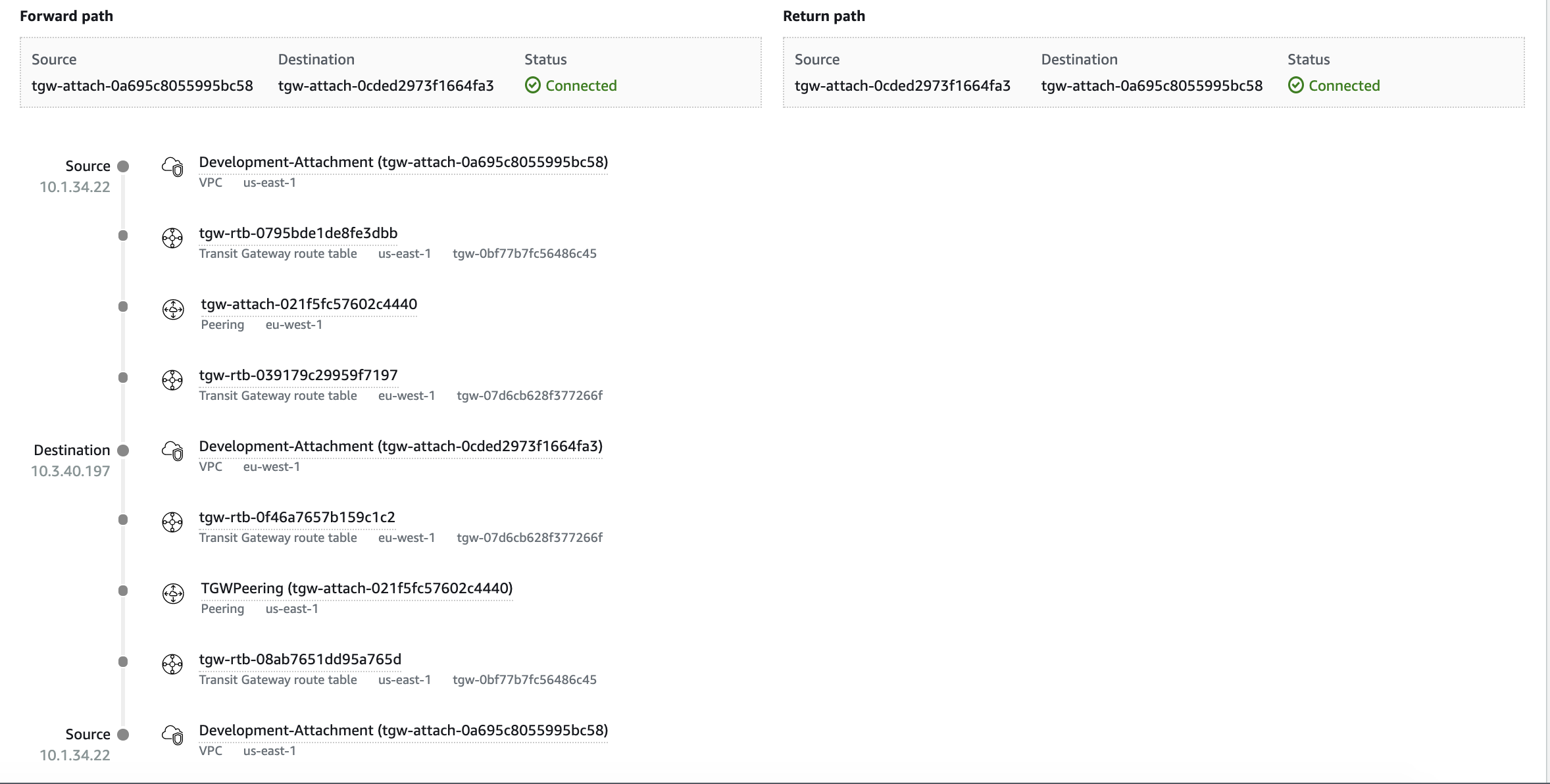
Note: You can verify the traffic flow using the Route Analyzer from Global Network
./bin/scripts/destroy.shSee CONTRIBUTING for more information.
This library is licensed under the MIT-0 License. See the LICENSE file.