- This is a simple example of two Continuous Integration workflows created in CodeCatalyst for a Java & Spring-Boot based backend application. The application exposes one API to perform a sum between integers Calculation
- The repository includes, inside the
.codecatalyst/workloadsfolder, the definition of two CodeCatalyst workflows:build.yaml: the workflow builds the jar, performs a CodeGuru Security review, uploads it to CodeArtifact, builds the Docker images, uploads it to ECRtest.yaml: the workflow perform unit and coverage tests on code
- The purpose of this repository is to show how to create CI workflows on CodeCatalyst to perform actions for a SpringBoot Java based application
- The example project is built with Java 17 and Maven 3. Please be aware that you'll need those to run the project locally.
- You'll need to create a CodeCatalyst space, a new Project with a new Code Repository
- You'll need to connect the CodeCatalyst Space to an AWS Account selecting one or more IAM Roles. This AWS Account will be used to store Docker images (ECR) and Java Artifacts (CodeArtifact). The connection you created will be used to interact with the AWS Account Resources through proper IAM Roles.
- PLEASE NOTE: During the creation of the CodeCatalyst connection to the target AWS Account, you'll need to create a proper IAM Role that will be assumed by CodeCatalyst (or use an existing one). For this example we've used a IAM Role assigning to it the policy you can find in the file
CodeCatalystRolePolicyExample.json. This IAM policy is very permissive so please don't use it for production purposes!!
- PLEASE NOTE: During the creation of the CodeCatalyst connection to the target AWS Account, you'll need to create a proper IAM Role that will be assumed by CodeCatalyst (or use an existing one). For this example we've used a IAM Role assigning to it the policy you can find in the file
- For this particular example we're assuming:
- AWS Account ID: 123456789012
- CodeCatalyst Environment (targeting the account above) named "TestEnvironment" referencing the "CodeCatalystTestEnvironmentRole" IAM role created in account 123456789012
- You'll need to create an ECR repository and a CodeArtifact repository and properly substitute values inside
./codecatalyst/workflows/build.yaml - Instructions to create ECR repository via CLI:
aws ecr create-repository \ --repository-name rest-calculator \ --region us-east-1 - Instructions to create a CodeArtifact repository via CLI
# Creating a domain aws codeartifact create-domain --domain artifact-store-demo --region us-east-1 # Creating repository aws codeartifact create-repository --domain artifact-store-demo --domain-owner 123456789012 --repository artifact-store-demo --description "My new repository" --region us-east-1
- The files
./codecatalyst/workflows/build.yamlcontains a fake account ID (123456789012). Please replace it with your correct AWS Account ID
The project contains two CodeCatalyst workflows:
- Test Workflow (
.codecatalyst/workloads/test.yaml) - Build & Release Workflow (
.codecatalyst/workloads/build.yaml)
The main goal of this workflow is to run unit and coverage tests. The workflow is triggered by Pull Requests. Proper Success Criterias are defined for unit and coverage tests and unit and coverage reports are autodiscovered and will be available for every run.
The application project is fully based on Maven 3, and, for that reason, we use Maven commands to run those test. More specifically we're using a single Maven Wrapper (https://github.com/apache/maven-wrapper) command mvn -ntp verify.
For unit testing we leverage JUnit 5, and for coverage test we leverage Jacoco Code Coverage Library (https://github.com/jacoco/jacoco)
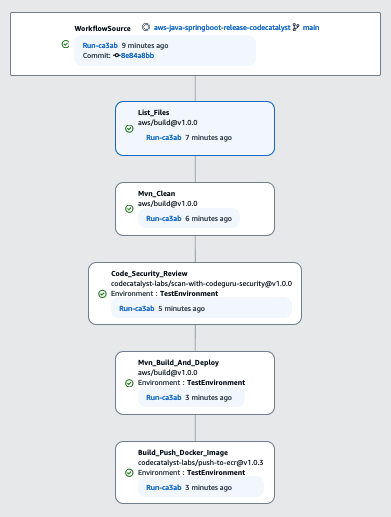
This workflow performs several steps, more specifically:
- Listing files
- Maven Cleaning
- Performs a Code Security Review (the report that will be produced will be available for each run)
- Building the jar & uploading it to CodeArtifact repository
- Building the Docker image and uploading it to ECR
- Setting up CodeCatalyst
- Getting Started with CodeGuru Security
- Getting started with CodeArtifact
- Amazon ECR User Guide
See CONTRIBUTING for more information.
This library is licensed under the MIT-0 License. See the LICENSE file.