Amazon MSK supports multiple authentication mechanisms including IAM, SASL/SCRAM and mutual TLS (mTLS). Customers who want to use mTLS for authentication, need to use AWS Private Certificate Authority (CA) as Amazon MSK only supports AWS Private CA as a certificate authority. However, many customers already use third-party CAs such as HashiCorp Vault and others.
In this example we will show how customers using third-party CA can bring their own certificates for mTLS authentication with Amazon MSK. To achieve this goal, you will need to leverage AWS Private CA and create a new subordinate CA on AWS signed by your private CA.
You can follow the relevant documentation to create a new private subordinate CA using the console or AWS CLI. After creating a new subordinate CA, you will need to install the subordinate CA certificate signed by an external CA by following this procedure.
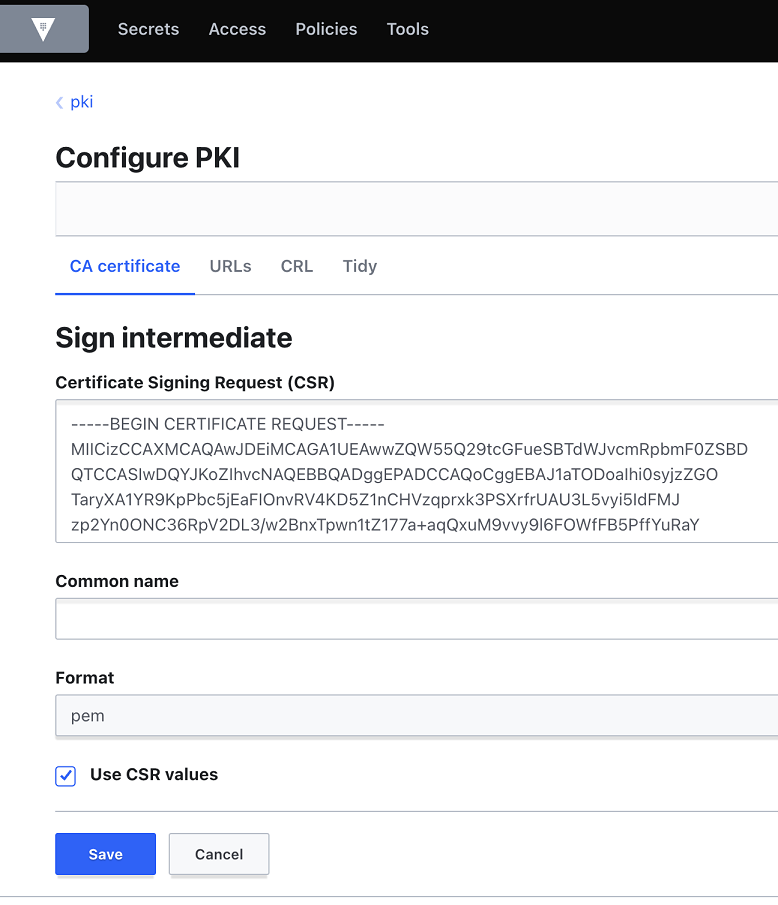
Once you have obtained the certificate signing request (CSR), and you have access to an external signing authority, you can submit the CSR to your external signing authority and obtain a signed CA certificate along with any chain certificates.
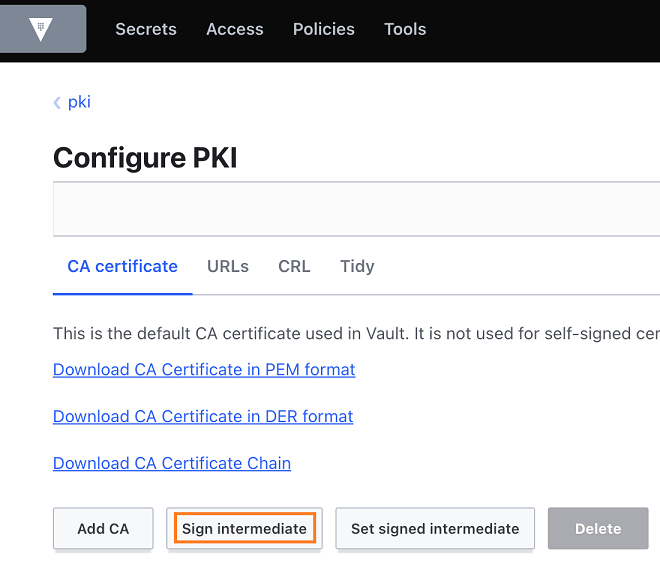
In the below example, we are using HashiCorp Vault PKI Secrets Engine as an external signing authority to obtain a signed CA certificate based on the CSR.
Specifically, we can use the "Sign intermediate" feature (or the corresponding CLI commands) to obtain this certificate:
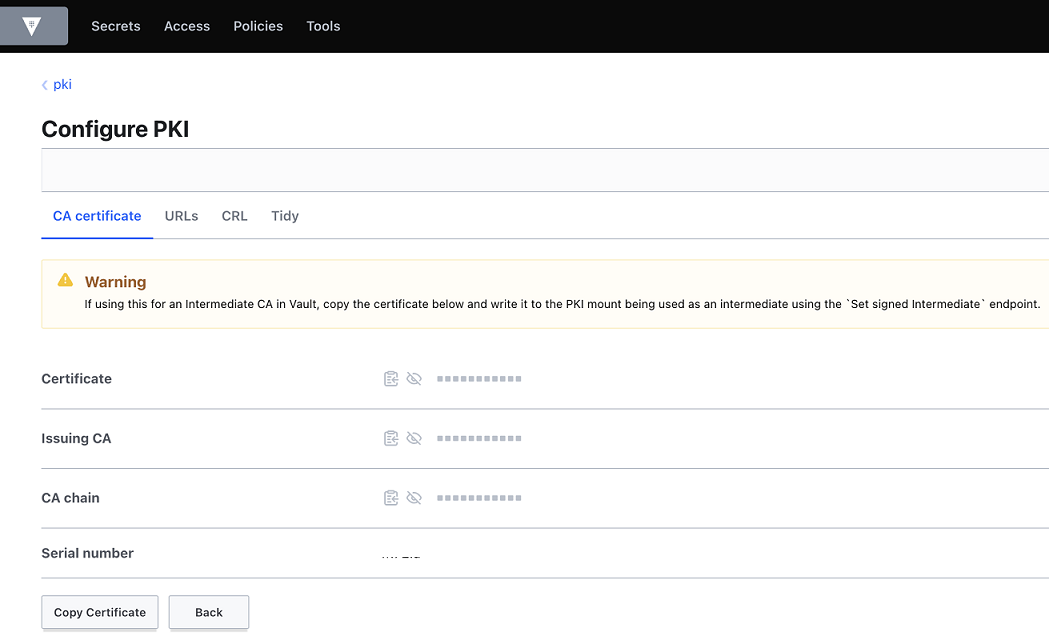
Once signed, you can copy the certificate and the CA chain, and subsequently import the private CA certificate file and the chain file into AWS Private CA.
- Go to AWS Private Certificate Authority console.
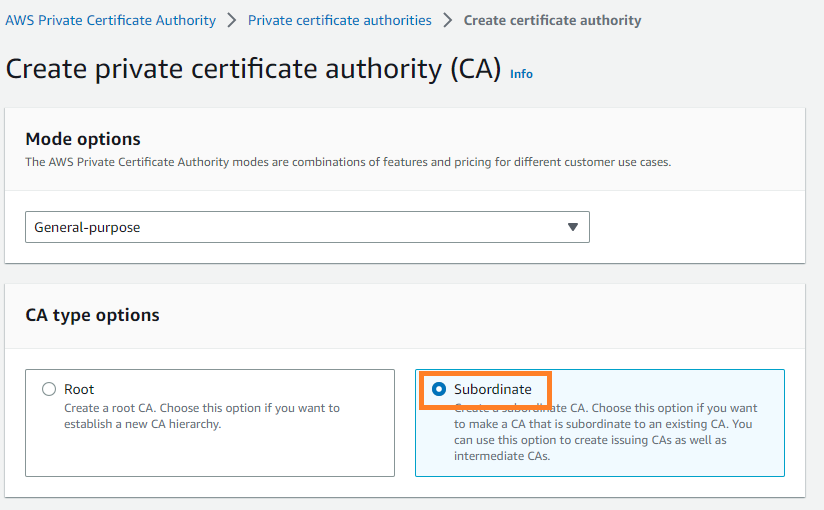
- Select Create a private CA.
- Choose CA type as Subordinate.
- Update distinguished name, Key algorithm and Create CA.
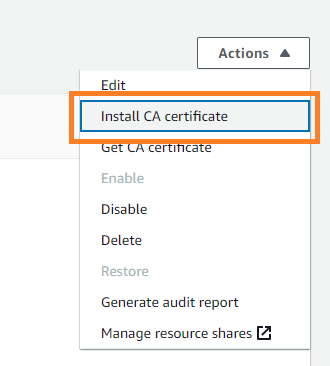
- Select the CA you created and select Install CA certificate.
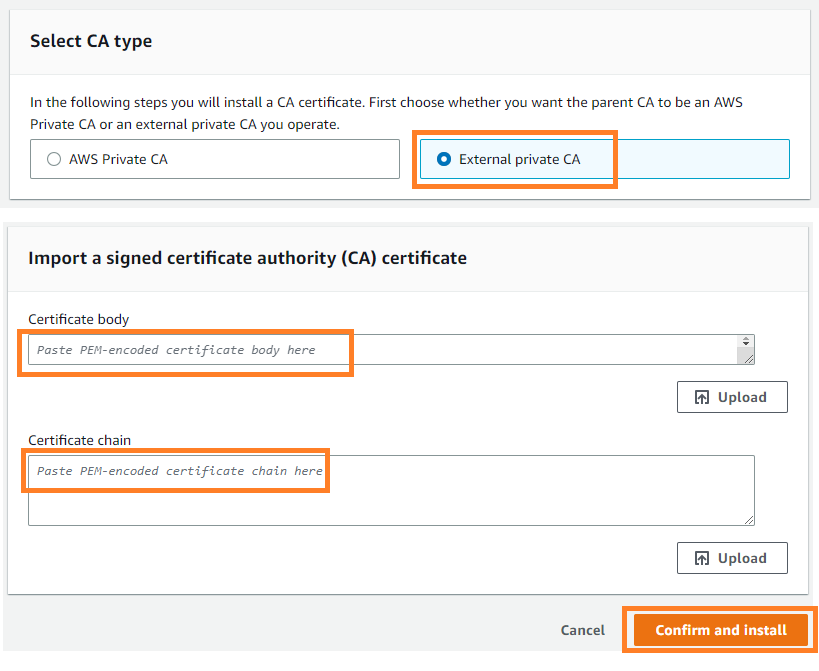
- Select External private CA as CA type, copy the certificate body and certificate chain from your private CA (in this example Hashicorp Vault).
- Select Confirm and install.
To use the CA you created earlier follow the below steps:
- Select your MSK cluster, go to Properties and Edit the Security settings.
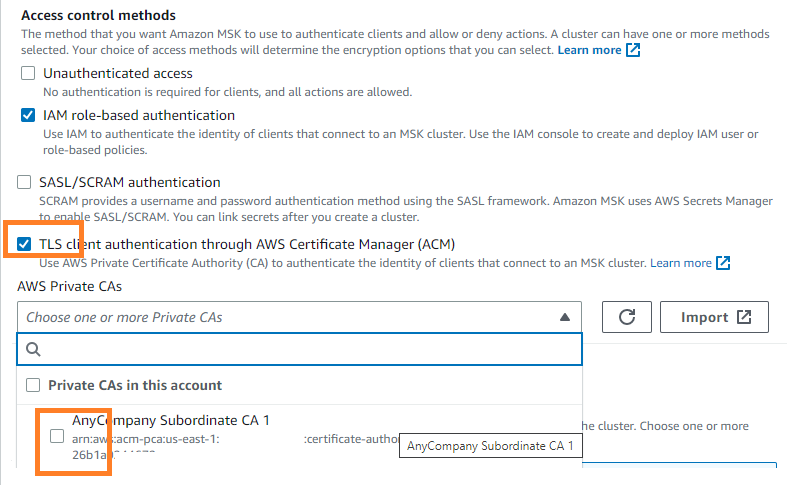
- Select TLS client authentication through AWS Certificate Manager (ACM) as access control methods and choose the Subordinate CA you created earlier and Save changes.
Once you finish updating the security settings for your MSK cluster, please follow the Mutual TLS authentication documentation to test your client.