- AWS PrivateLink Reference Architectures
This project provides reference implementations for AWS PrivateLink with an Application Load Balancer (ALB) or an Amazon API Gateway. Implementations are provided in both AWS CloudFormation and Hashicorp Terraform templates.
VPC endpoints provide secure access to a specific service, with several benefits to the end user:
- VPC endpoints provide access to a specific service without the need of using any other gateways – no need to use an Internet gateway, a NAT gateway, a VPN connection, or a VPC peering connection, reducing the risks of exposing your resources to the Internet or to other outside networks.
- Your traffic remains within Amazon's private network, reducing the risks of exposing your traffic to the Internet.
- When accessing Amazon services over VPC endpoints, you can restrict the access through a VPC endpoint to specific users, actions, and/or resources.
- You can limit access to resources provided by an Amazon service to traffic originating from a specific VPC or through a specific VPC endpoint.
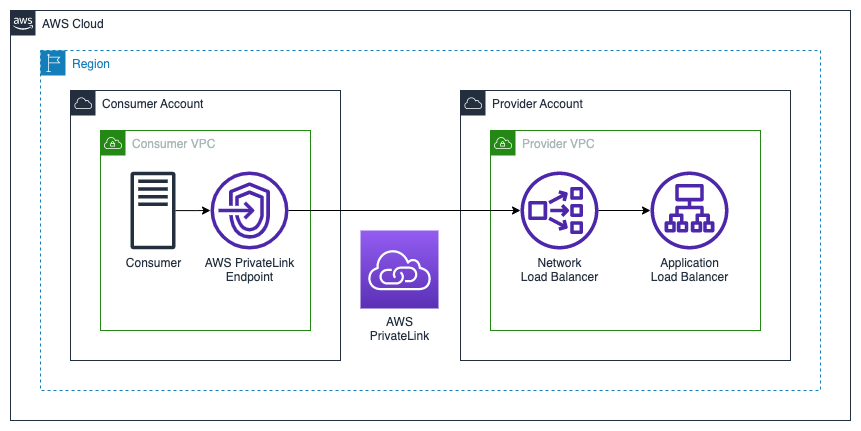
In this architecture, the provider has an existing Internet-facing ALB servicing existing consumers. The templates in this reposititory deploy a Network Load Balancer into private subnets within the same VPC and availabiilty zones (AZs) as the ALB. An NLB target group is created with the ALB as a single target. An AWS PrivateLink endpoint service is created targeting the NLB.
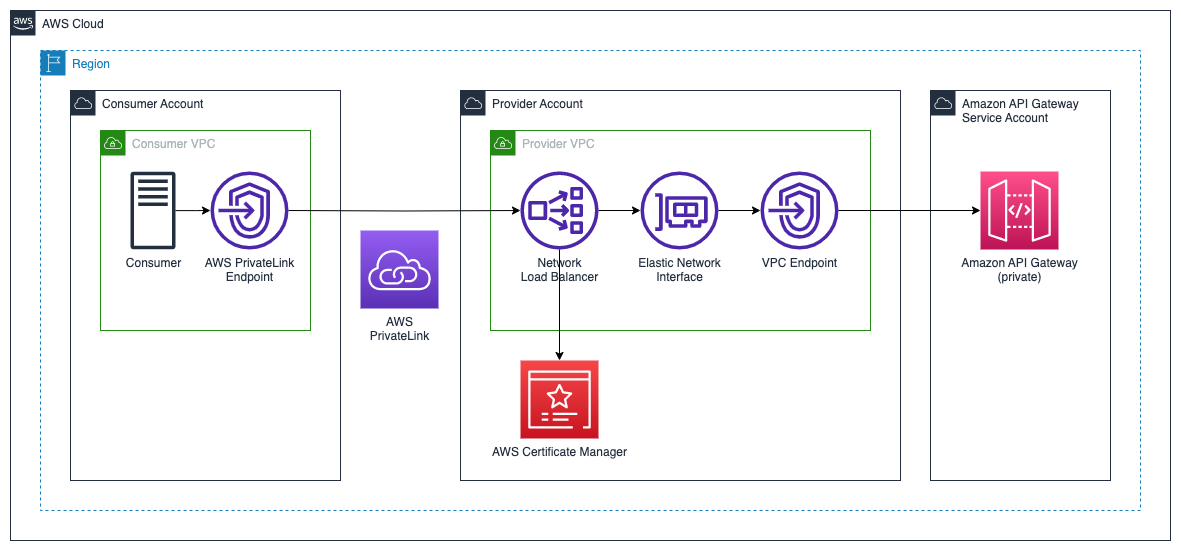
In this architecture, the provider may have an existing edge or regional API Gateway or an existing private API Gateway servicing existing consumers. A private API is required to provide connectivity through AWS PrivateLink. The templates in this repository deploy a Network Load Balancer into private subnets within the same VPC and availabiity zones (AZs) as the interface VPC endpoint for API Gateway. An NLB target group is created with VPC endpoint elastic network interfaces (ENIs) as the TLS targets. AWS Certificate Manager is used to create a TLS certificate that is associated to both the NLB and API Gateway.
- Python 3, installed
- AWS Command Line Interface (AWS CLI) version 2, installed. Please follow these instructions with how to setup your AWS credentials.
- AWS Serverless Application Model (SAM), installed
- Docker Desktop, installed
- GitHub account
- Amazon API Gateway - Amazon API Gateway is a fully managed service that makes it easy for developers to create, publish, maintain, monitor, and secure APIs at any scale.
- AWS Certificate Manager - Provision and manage SSL/TLS certificates with AWS services and connected resources.
- AWS CloudFormation - AWS CloudFormation lets you model, provision, and manage AWS and third-party resources by treating infrastructure as code.
- AWS PrivateLink - Establish connectivity between VPCs and AWS services without exposing data to the internet
- Application Load Balancer - Application Load Balancer operates at the request level (layer 7), routing traffic to targets (EC2 instances, containers, IP addresses, and Lambda functions) based on the content of the request.
- Network Load Balancer - Network Load Balancer operates at the connection level (Layer 4), routing connections to targets (Amazon EC2 instances, microservices, and containers) within Amazon VPC, based on IP protocol data.
| Parameter | Type | Default | Description |
|---|---|---|---|
| VpcId | AWS::EC2::VPC::Id | - | VPC ID |
| PublicSubnetIds | List<AWS::EC2::Subnet::Id> | - | Public Subnet IDs |
| PrivateSubnetIds | List<AWS::EC2::Subnet::Id> | - | Private Subnet IDs |
| HostedZoneId | AWS::Route53::HostedZone::Id | - | Hosted Zone ID |
| DomainName | String | - | Domain Name |
If you'd like to deploy a test application that you can then deploy the reference architectures on top of, you can follow the instructions below:
git clone https://github.com/aws-samples/aws-privatelink-reference-architectures
cd aws-privatelink-reference-architectures
sam build --use-container --parallel --cached
sam deploy --guided
Deleting the CloudFormation Stack will remove the Lambda functions, Application Load Balancer, CloudWatch Log Groups, and Amazon API Gateway.
sam delete
See CONTRIBUTING for more information.
This library is licensed under the MIT-0 License. See the LICENSE file.