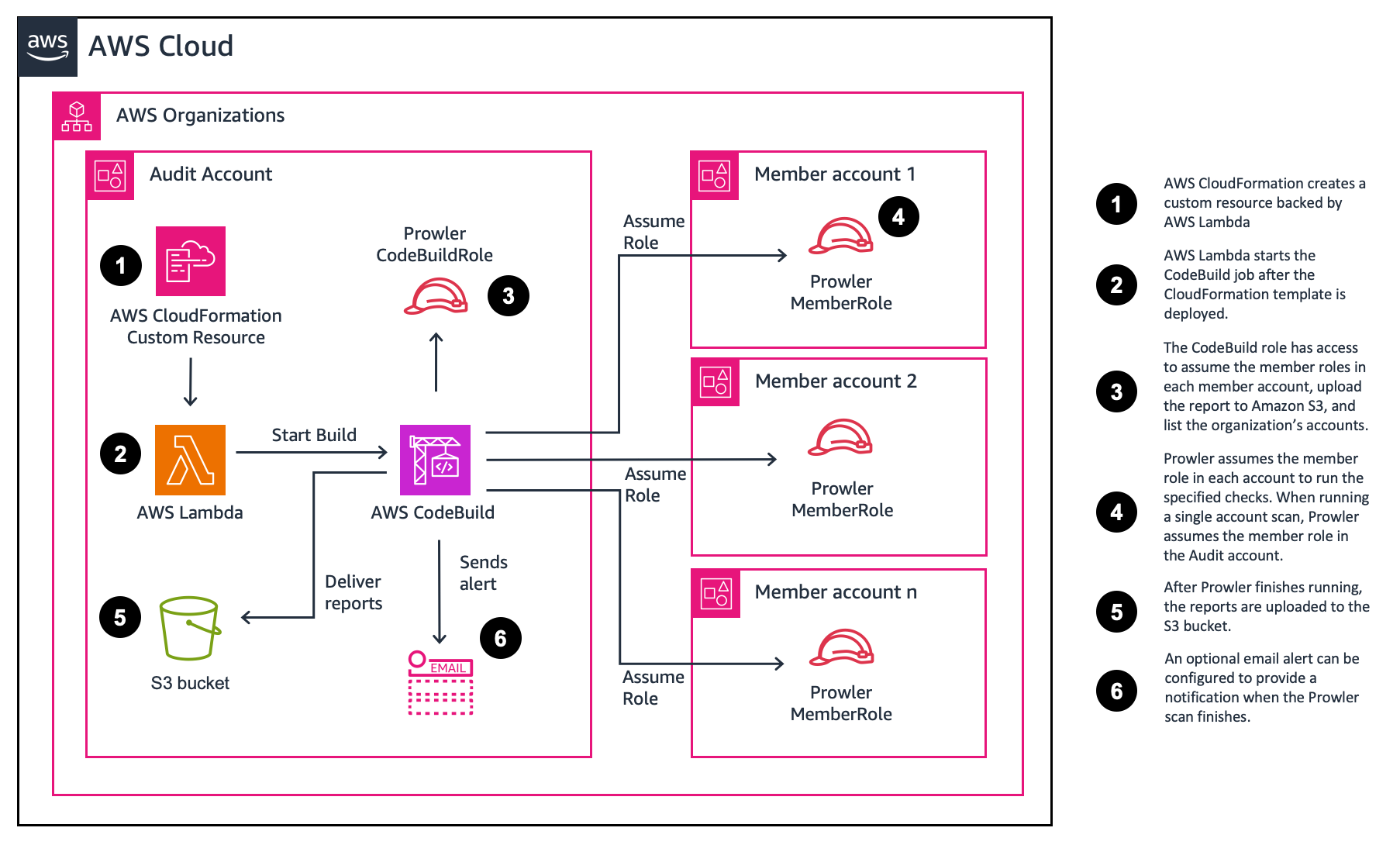
Cybersecurity remains a very important topic and point of concern for many CIOs, CISOs, and their customers. To meet these important concerns, AWS has developed a primary set of services customers should use to aid in protecting their accounts. Amazon GuardDuty, AWS Security Hub, AWS Config, and AWS Well-Architected reviews help customers maintain a strong security posture over their AWS accounts. As more organizations deploy to the cloud, especially if they are doing so quickly, and they have not yet implemented the recommended AWS Services, there may be a need to conduct a rapid security assessment of the cloud environment.
We have developed an inexpensive, easy to deploy, secure, and fast solution to provide our customers with a security assessment report. These reports are generated using the open source project Prowler. Prowler performs point in time security assessment based on AWS best practices and can help quickly identify any potential risk areas in a customer’s deployed environment. If you are interested in conducting these assessments on a continuous basis, AWS recommends enabling Security Hub’s Foundational Security Best Practices standard. If you are interested in integrating your Prowler assessment results with Security Hub, you can follow the instructions in the Prowler Documentation.
Note: Prowler is not an AWS owned solution. Customers should independently review Prowler before running this solution. Any dependencies associated with Prowler should be kept up to date. This solution installs the latest version available from pip package installer.
- Overview
- Parameters
- Deployment
- Single account scan
- Multi-account scan
- Review the results
- Scan types
- Notifications
- Reporting Summary
- Frequently Asked Questions (FAQ)
- Clean Up
- Security
- License
The solution is deployed with AWS CloudFormation. When deployed, an AWS CodeBuild project and an Amazon S3 bucket to store the Prowler generated reports are created. An AWS Lambda function is then used to start the AWS CodeBuild project.
The parameter (user input) defaults will run a basic scan in a single account. However, you can choose different parameters to run more extensive scans or to scan multiple accounts. The deployment process takes less than 5 minutes to complete. The solution’s AWS CloudFormation templates are provided for review in this Github repository.
Once the template is deployed, the CodeBuild project will run. The default assessment takes around 5 minutes to complete. The time to complete a security assessment will vary depending on the number of resources and the scan options selected. At the end of the assessments the reports are delivered to the created S3 Bucket.
SATv2 can be customized by updating the CloudFormation parameters. This section summarizes the available options and provides a link to the section with more information.
| Parameter | Description | More information |
|---|---|---|
| ProwlerScanType | Specify which type of scan to perform. Selecting full without specifying different ProwlerOptions will do a full scan. To perform a specific check, choose Full and append -c to ProwlerOptions. | Scan types |
| MultiAccountScan | Set this to true if you want to scan all accounts in your organization. You must have deployed the prerequisite template to provision a role, or specify a different ProwlerRole with the appropriate permissions. | Multi-account scan |
| Reporting | Set this to true if you want to summarize the Prowler reports into a single csv and create a presentation. This is helpful when scanning multiple accounts. | Reporting Summary |
| EmailAddress | Specify an address if you want to receive an email when the assessment completes. | Notifications |
| Advanced Parameters | ||
| ConcurrentAccountScans | For multi-account scans, specify the number of accounts to scan concurrently. This is useful for large organizations with many accounts. Selecting more than three changes the size of the CodeBuild instance and may incur additional costs. | |
| CodeBuildTimeout | Set the timeout for the CodeBuild job. The default is 300 minutes (5 hours). | |
| MultiAccountListOverride | Specify a space delimited list of accounts to scan. Leaving this blank will scan all accounts in your organization. If you can't provide delegated ListAccount access, you can provide the MultiAccountListOverride parameter. | Multi-account scan |
| ProwlerOptions | Specify the parameters for Prowler. The --role and ARN will automatically be added to the end of the parameters you specify. This can also be used to specify a single check. | Full scan |
| ProwlerRole | The role that Prowler should assume to perform the scan. Change this if you want to specify your own role with different permissions. |
You can use this project to run Prowler across multiple accounts in an AWS Organization, or a single account. We provide instructions to use AWS CloudShell or the AWS console. Choose an option to get started.
| Deployment Type | AWS CloudShell | AWS console |
|---|---|---|
| Single account | Link | Link |
| Multi-account | Link | Link |
To run the Self-Service Security Assessment solution (SATv2) against a single account, follow the instructions below. You can choose to use the AWS CLI or the AWS Console.
Show steps
-
Login to your AWS account.
-
In the navigation bar, choose AWS CloudShell.
-
To download the CloudFormation template, enter the following command.
wget https://raw.githubusercontent.com/awslabs/aws-security-assessment-solution/main/2-sat2-codebuild-prowler.yaml
-
To deploy the CloudFormation template, enter the following command.
aws cloudformation deploy --template-file 2-sat2-codebuild-prowler.yaml --stack-name sat2 --capabilities CAPABILITY_NAMED_IAM
Show steps
- Download the 2-sat2-codebuild-prowler.yaml CloudFormation template.
- Navigate to the AWS CloudFormation console.
- In the navigation pane, choose Stacks.
- Choose Create stack.
- Under Specify template, select Upload a template file.
- Choose 2-sat2-codebuild-prowler.yaml you downloaded in step 1.
- Choose Next.
- For Stack name, enter sat2.
- Choose Next.
- On the Configure stack options page, choose Next.
- On the Review SAS page, select the box I acknowledge that AWS CloudFormation might create IAM resources. and choose Submit.
Self-Service Security Assessment solution (SAT) also supports multi-account scans. You must deploy a prerequisite role to each account you want to perform the scan on. To run SATv2 for multiple accounts, follow the instructions below. You can choose to use the AWS CLI or the AWS Console.
These instructions assume you already have the prerequisites for stack set operations. For more information, visit the AWS CloudFormation User Guide.
Note: StackSets don't apply to the management account. To assess the management account, deploy the 1-sat2-member-role as a CloudFormation Stack.
Show steps
-
Login to your AWS Management account.
-
In the navigation bar, choose AWS CloudShell.
-
Identify which account you will run the Prowler scan from. Customers typically use a security tooling account, or audit account. Take note of the account ID for the ProwlerAccountID parameter.
-
To download the CloudFormation template, enter the following command.
wget https://raw.githubusercontent.com/awslabs/aws-security-assessment-solution/main/1-sat2-member-roles.yaml
-
Deploy the CloudFormation template via CloudFormation StackSets. Update the following parameters:
- Replace <aws-account-id> with the account ID you will run Prowler from.
- Replace <region> with the Region you want to deploy the template to.
aws cloudformation create-stack-set --template-body file://1-sat2-member-roles.yaml \ --stack-set-name sat2-member-roles \ --permission-model SERVICE_MANAGED \ --auto-deployment Enabled=true,RetainStacksOnAccountRemoval=false \ --capabilities CAPABILITY_NAMED_IAM \ --parameters ParameterKey=ProwlerAccountID,ParameterValue=<aws-account-id> \ --region <region>
-
Use the following command to create stack instances for each account in your organization. You can target a specific OU, or the root OU. Update the following parameters:
- Replace <root-ou> with the organization root ID.
- Replace <region> with the Region you want to deploy the template to.
aws cloudformation create-stack-instances --stack-set-name sat2-member-roles \ --deployment-targets OrganizationalUnitIds='["<root-ou>"]' \ --regions '["<region>"]' \ --operation-preferences FailureTolerancePercentage=100,MaxConcurrentPercentage=100 \ --region <region>
-
Determine if you have delegated admin or a resource policy that already exists for your Prowler account. Only one option is needed and resource policy is encouraged as it is more granular.
Note: Resource policies are not available in GovCloud, so you will need to use a delegated admin.
7a. Your Prowler account might already have a delegation. You can use the following commands to check:
aws organizations list-delegated-administrators
7b. Your Prowler account might already have a resource policy. You can use the following commands to check:
aws organizations describe-resource-policy
-
If you don't have a delegated admin or a resource policy you can use the following commands to add the appropriate access.
Note: If you can't provide delegated ListAccount access, you can provide the MultiAccountListOverride parameter in the
2-sat2-codebuild-prowler template.Note: If you are using GovCloud, use step 8a to create a delegated admin. If you are using a commercial region, use step 8b to provide least privilege access to ListAccounts.
8a. Use the following command to delegate an admin if you do not already have one. Replace <aws-account-id> with the account ID you will run Prowler from.
aws organizations register-delegated-administrator <aws-account-id>
8b. Use the following commands to add a resource policy.
-
Replace <aws-account-id> with the account ID you will run Prowler from.
aws organizations put-resource-policy --content \ '{ "Version": "2012-10-17", "Statement": [ { "Sid": "Statement", "Effect": "Allow", "Principal": { "AWS": "arn:aws:iam::<aws-account-id>:root" }, "Action": [ "organizations:ListAccounts", "organizations:DescribeAccount", "organizations:ListTagsForResource" ], "Resource": "*" } ] }'
-
Note: Make sure you switched to the account you specified will run Prowler.
-
To download the template, open AWS CloudShell in the Prowler account and enter the following command.
wget https://raw.githubusercontent.com/awslabs/aws-security-assessment-solution/main/2-sat2-codebuild-prowler.yaml
-
To deploy the template in the Prowler account. Set MultiAccountScan to true to scan all the accounts in your organization.
aws cloudformation deploy --template-file 2-sat2-codebuild-prowler.yaml \ --stack-name sat2-prowler \ --capabilities CAPABILITY_NAMED_IAM \ --parameter-overrides MultiAccountScan=true
Show steps
-
Download the 1-sat2-member-roles.yaml and 2-sat2-codebuild-prowler.yaml files.
-
Deploy the CloudFormation template via CloudFormation StackSets. Update the following parameters:
- Replace <aws-account-id> with the account ID you will run Prowler from.
- Replace <region> with the Region you want to deploy the template to.
-
Navigate to the AWS CloudFormation console.
-
In the navigation pane, choose StackSets.
-
Choose Create StackSet.
-
For Permissions, leave Service-managed permissions selected.
-
Under Specify template, select Upload a template file.
-
Choose 1-sat2-member-roles.yaml you downloaded in step 1-1.
-
Choose Next.
-
For Stack name, enter sat2-member-role.
-
For Parameters, enter the following:
- ProwlerAccountID - The account ID you will run Prowler from.
-
Choose Next.
-
On the Configure StackSet options page, choose Next.
-
On the Set deployment options, enter the following:
- For Deployment targets leave Deploy to organization selected.
- For Specify regions, choose us-east-1.
- For Region Concurrency, choose Parallel.
-
Choose Next.
-
On the Review page, select the box I acknowledge that AWS CloudFormation might create IAM resources. and choose Submit.
Determine if you have delegated administrator or a resource policy that already exists for the account you wish to deploy Prowler in. It is recommended that you run Prowler from your security tooling (Audit) account. To update or verify that the audit account has permissions to ListAccounts, follow these steps.
-
Navigate to the AWS Organization console.
-
In the navigation pane, choose Settings.
-
For Delegated administrator for AWS Organizations, include the following statement.
{ "Version": "2012-10-17", "Statement": [ { "Sid": "Statement", "Effect": "Allow", "Principal": { "AWS": "arn:aws:iam::<aws-account-id>:root" }, "Action": [ "organizations:ListAccounts", "organizations:DescribeAccount", "organizations:ListTagsForResource" ], "Resource": "*" } ] }
-
Navigate to the AWS CloudFormation console in the account you will run the tool from (ProwlerAccountID).
-
In the navigation pane, choose Stacks.
-
Choose Create stack.
-
Under Specify template, select Upload a template file.
-
Choose 2-sat2-codebuild-prowler.yaml you downloaded in step 1-1.
-
Choose Next.
-
For Stack name, enter sat2-prowler.
-
In the Parameters section, for MultiAccountScan, select true.
-
You can optionally enable reporting to get a summary of all accounts in a single csv file. For Reporting, select true.
-
Choose Next.
-
On the Configure stack options page, choose Next.
-
On the Review SAS page, select the box I acknowledge that AWS CloudFormation might create IAM resources. and choose Submit.
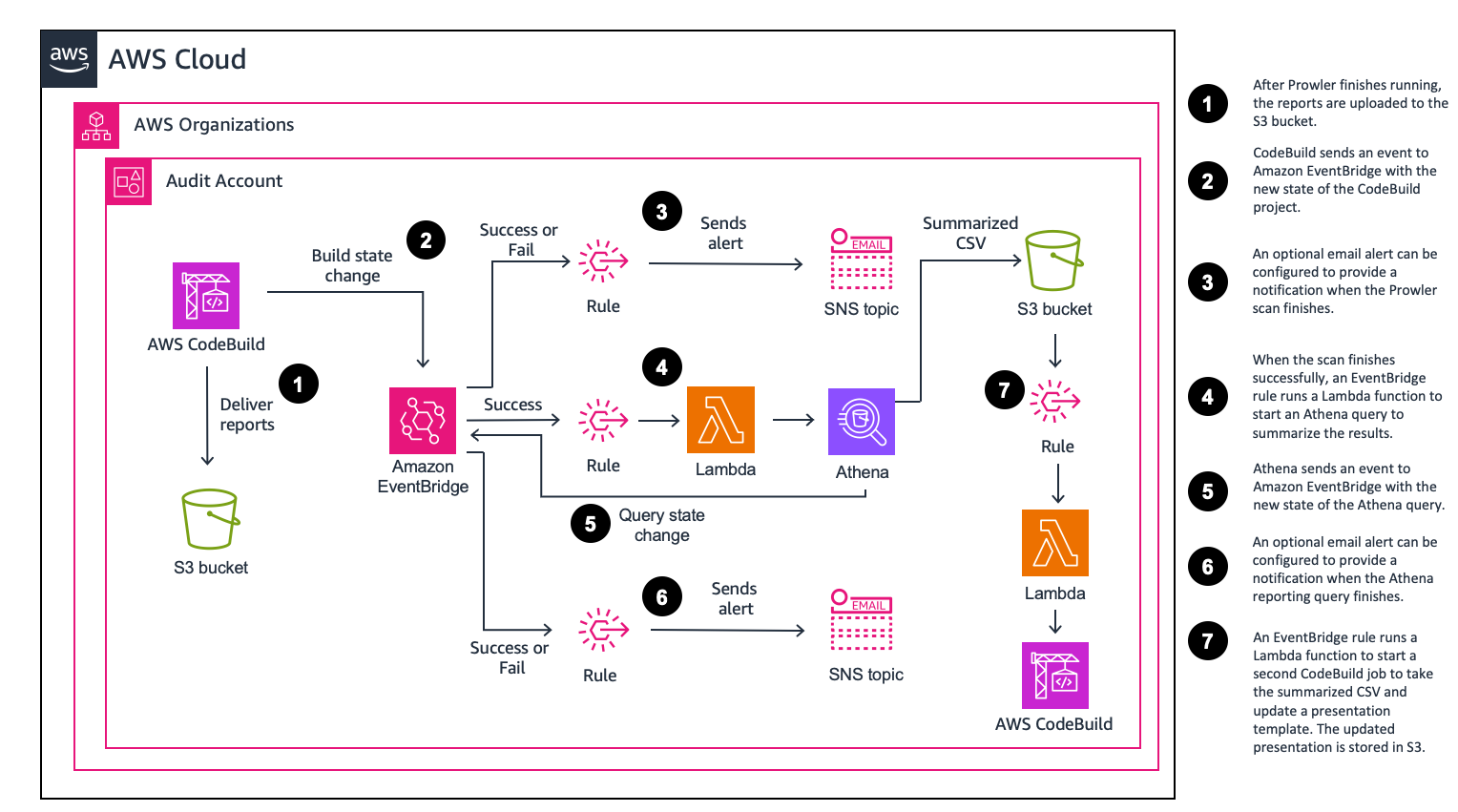
After the solution is deployed, a Lambda function starts the CodeBuild project. After the CodeBuild project is finished building, the Prowler results will be uploaded to the created Amazon S3 bucket. If you configured notifications, you will get an email when the Prowler scan is complete. If you configured reporting, you will have a consolidated csv and presentation file in the /reports folder.
If you didn't configure email alerts, you can monitor the progress from the CodeBuild console.
To review the results, follow these steps.
-
Navigate to the Amazon S3 console in the account you deployed Prowler.
-
Select the bucket that starts with sat2-prowler-prowlerfindingsbucket-
-
Choose the folder with the date and time of the scan.
-
For each account, there will be 4 file types (csv, html, json, json-ocsf) in the format
prowler-output-<aws-account-id>-<datetime>. -
Select one of the html objects.
-
Choose Open.
-
A new window will open with your report. You can use the filters to identify and prioritize the findings.
Prowler has a built in dashboard to review the results. To use the Prowler dashboard, Prowler must be installed locally and you must download the results of Prowler locally.
You must have the AWS Command Line Interface (CLI) and valid credentials. For more information, review the AWS Command Line interface user guide.
-
Install Prowler. For more information, review the Prowler installation instructions.
pip install prowler -
Get the name of the Amazon S3 bucket. The name of the bucket is in the CloudFormation console as ProwlerFindingsBucket resource. Alternatively, navigate to the S3 console and look for a bucket in the format
{stack_name}-prowlerfindingsbucket-{ID} -
Download the CSVs and compliance data from S3. If you did not run a full scan, you may not have compliance data. Replace
{bucket_name}with the name of your bucket.aws s3 sync s3://{bucket_name}/compliance/ output/compliance/ aws s3 sync s3://{bucket_name}/csv/ output/ -
Run the dashboard. Use the following command to run the dashboard. By default, it will start on http://127.0.0.1:11666/.
prowler dashboard
By default, SAT2 will run a basic scan which includes 13 checks. You can choose to run an intermediate or full check by choosing a different ProwlerScanType parameter value.
For example, a single account scan using the intermediate scan option would use this command:
aws cloudformation deploy --template-file 2-sat2-codebuild-prowler.yaml \
--stack-name sat2-prowler \
--capabilities CAPABILITY_NAMED_IAM \
--parameter-overrides ProwlerScanType=IntermediateChecks are frequently added, to see the latest checks, run prowler aws --list-checks command. An example has been provided below for each check level.
To see a list of checks, review basic checks.
- Manual check - Maintain current contact details.
- Find obsolete Lambda runtimes.
- Ensure CloudTrail is enabled in all regions
- Ensure AWS Config is enabled in all regions.
- Ensure no security groups allow ingress from 0.0.0.0/0 or ::/0 to any port.
- Check if GuardDuty is enabled
- Ensure IAM password policy require at least one lowercase letter
- Ensure IAM password policy require at least one number
- Ensure IAM password policy require at least one symbol
- Ensure IAM password policy requires at least one uppercase letter
- Ensure MFA is enabled for the root account
- Ensure access keys are rotated every 90 days or less
- Ensure there are no S3 buckets open to Everyone or Any AWS user.
To see a list of checks, review intermediate checks.
This scan will add --severity critical high to the Prowler scan options. With this selected Prowler will run all security checks that result in critical or high severity.
To see a list of checks, review full checks.
This option doesn't add any additional parameters to the Prowler scan. It will result in Prowler running 359+ checks.
You can also use the full scan to customize the scan however you would like.
For ProwlerScanType choose Full.
For ProwlerOptions, append the check. For example, to check only if GuardDuty is enabled, enter:
aws --ignore-exit-code-3 -c guardduty_is_enabled
You can optionally specify an email address in the EmailAddress parameter when you deploy the CloudFormation template. This will create an SNS topic and send an email when the CodeBuild job completes.
This may be helpful when running longer scans, or across many accounts.
For example, a single account scan with email notifications would use this command:
aws cloudformation deploy --template-file 2-sat2-codebuild-prowler.yaml \
--stack-name sat2-prowler \
--capabilities CAPABILITY_NAMED_IAM \
--parameter-overrides EmailAddress=email@domain.comWith or without the optional EmailAddress parameter set, you can view the progress in the CodeBuild console.
-
Navigate to the CodeBuild console.
-
In the navigation pane, under Build, choose Build projects.
-
Choose the Build project that begins with ProwlerCodeBuild-.
-
Under Build history, you will see the last run.
-
Optionally, you can choose Start build to run another scan with the options you choose when you deployed the solution.
You can optionally enable reporting to summarize multiple Prowler scan csv files into a single file. This may be helpful when running Prowler across multiple accounts in an AWS Organization. The reporting summary feature is off by default. To enable reporting, set the Reporting parameter to true when you deploy the CloudFormation template. This will create an Athena WorkGroup, a Glue table, and automatically run a query to consolidate the results. The summarized csv file is located in the same S3 bucket as the Prowler results in the /reports folder.
The consolidated csv file will be used to create a SHIP HealthCheck presentation. Once the csv file is written to the bucket, an EventBridge rule runs a Lambda function that starts a CodeBuild job. The updated presentation is stored in the same S3 bucket in the /reports folder.
If you specify an email address while reporting is enabled, you will get a second email when the Athena query is finished.
For example, a multi-account scan with reporting and email alerts enabled would use this command:
aws cloudformation deploy --template-file 2-sat2-codebuild-prowler.yaml \
--stack-name sat2-prowler \
--capabilities CAPABILITY_NAMED_IAM \
--parameter-overrides MultiAccountScan=true Reporting=true EmailAddress=email@domain.comA saved query is created as an example. This query counts the checks that failed across all the accounts assessed. To review and run the query, follow these steps:
-
Navigate to the Amazon Athena console.
-
Choose the workgroup that begins with sat2-prowler-*.
-
Choose the Saved queries tab.
-
Select the query you want to run by choosing the ID.
-
Choose Run to run the query.
- Is there a cost?
- This solution is designed to run within AWS Free Tier.
- For Amazon CodeBuild, customer's get 100 build minutes per month.
- For customers that have already exceeded free tier with CodeBuild, S3, and Lambda, this solution costs less than $1 to run.
- Is this a continuous monitoring and reporting tool?
- No. This is a one-time assessment, we recommend customers use AWS Security Hub for continuous assessments.
- Does this integrate with GuardDuty, Security Hub, CloudWatch, etc.?
- No. You can follow the instructions in this blog to integrate Prowler and Security Hub.
- How do I remediate the issues in the reports?
- Generally, the issues should be described in the report with readily identifiable corrections. Please follow up with the public documentation for each tool (Prowler) as well. If this is insufficient, please reach out to your AWS Account team or AWS Support to help you understand the reports and work towards remediating issues.
- What findings does Prowler report for SATv2?
Check Mitigation Check if Lambda functions invoke API operations are being recorded by CloudTrail. CloudTrail is an AWS account level configuration. CloudTrail should be enabled independent of SATv2. Enable termination protection for Cloudformation Stacks SATv2 is intended to be ran for a point in time, and then deleted. If the Stack is terminated, the findings are still retained in the S3 bucket. Check if CloudWatch log groups are protected by AWS KMS. Log group data is always encrypted in CloudWatch Logs. By default, CloudWatch Logs uses server-side encryption for the log data at rest. Customer managed KMS key is not configured to save on costs. Check if CloudWatch Log Groups have a retention policy of specific days. Log group retention is set to 7 days by design. This check looks for Log groups with retention less than a year. Check if S3 buckets have KMS encryption enabled. All Amazon S3 buckets have encryption configured by default, and objects are automatically encrypted by using server-side encryption with Amazon S3 managed keys (SSE-S3). Customer managed KMS key is not configured to save on costs. Check if S3 bucket MFA Delete is not enabled. Prowler assessment results can be regenerated and do not require MFA delete. Check if S3 buckets have object lock enabled Prowler assessment results can be regenerated and do not require S3 object lock. Check if S3 buckets have server access logging enabled Prowler assessment results do not require server access logging.
After you run the solution, you should delete the CloudFormation Stacks to remove resources that are no longer needed. The S3 bucket with the Prowler scan results will remain.
To remove the security assessment solution from your account, follow these steps.
-
Navigate to the AWS CloudFormation console in the account you ran the tool from (ProwlerAccountID).
-
In the navigation pane, choose Stacks.
-
Choose the sat2-prowler Stack.
-
Choose Delete.
If you deployed the member role StackSet to scan multiple accounts, follow these steps.
-
Navigate to the AWS CloudFormation console in the account you created the member role StackSet.
-
In the navigation pane, choose StackSets.
-
Choose the sat2-member-roles StackSet.
-
Choose Actions, then Delete stacks form StackSet.
-
Specify the same AWS OU ID when you created the StackSet.
-
For Specify regions, choose Add all regions.
-
Choose Next, and Submit.
After change finishes, you can delete the StackSet.
-
Choose the sat2-member-roles StackSet.
-
Choose Actions, then Delete StackSet.
If you want to remove the Amazon S3 bucket with the scan results, follow the steps in the Amazon S3 user guide to delete the objects and bucket. If you run the solution again, a new S3 bucket will be created for your results.
See CONTRIBUTING for more information.
This project is licensed under the Apache-2.0 License.