- Backend s3 - for remote state
- VPC
- Internet Gateway (IGW)
- Public and Private Subnets
- Security Groups, Route Tables and Route Table Associations
- IAM roles, instance profiles and policies
- An EKS Cluster
- EKS Managed Node group
- Autoscaling group and Launch Configuration
- Worker Nodes in a private Subnet
- bastion host for ssh access to the VPC
- The ConfigMap required to register Nodes with EKS
- KUBECONFIG file to authenticate kubectl using the
aws eks get-tokencommand
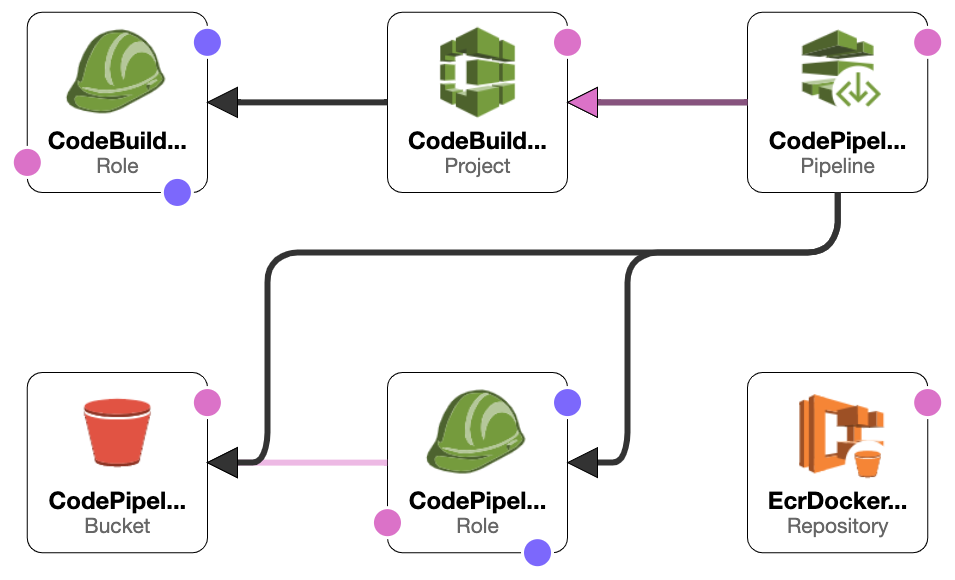
- CodePipelineGitHub
- Codepipeline
- EcrDockerRepository
- CodeBuildServiceRole
- CodePipelineServiceRole
- CodePipelineArtifactBucket
- Export the
export ACCOUNT_ID=<Account ID>> - Execute the codepipeline.sh from the root of the project. it will build up the entire infra.
buildspec.yaml. has the code build pipe actions to be executed on the every commit in the main branch of the repo. I Used a simple go api application which will return a text response deployed as K8s workload in the created cluster.
###Things can be improved:
- Auto Scaling based on based metrics.
- Encrypted communication with Let's encrypt or any other CA.
- and list will go on as in when required.
Execute destroy.sh script to nuke out the entire infra. Then execute this command to destroy the state. Caution: execute this only if the above script executed successfully
aws s3 rm s3://tf-state-cluster --recursiveCredits: This application was build with reference to this repo.