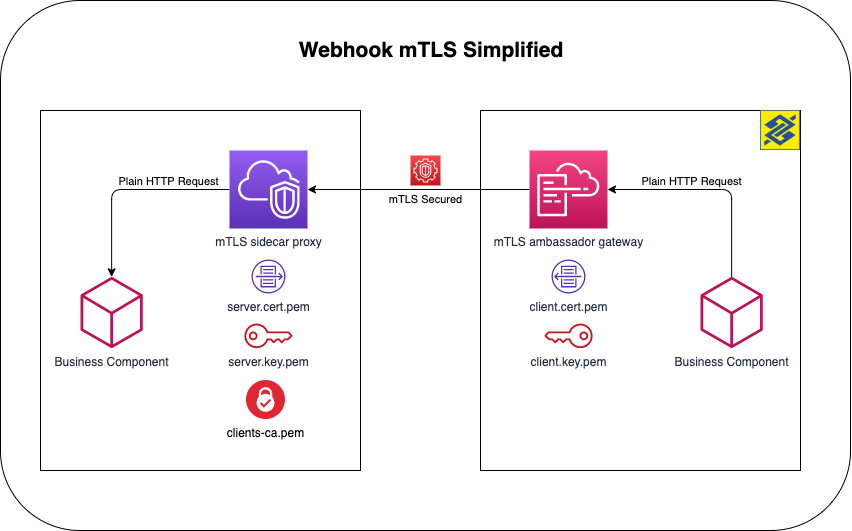
Sidecar Docker container used to authenticate using mTLS for the Open Banking and PIX API communication as client (request) or as server (webhook)
To quickly take a look at this running, download the test certificates located at the example/sidecar/server-certs to a local folder named "certs" and bring up this docker-compose:
version: "3.7"
services:
mtls-sidecar:
image: labbsr0x/api-mtls-sidecar-proxy:0.0.1
environment:
- ALLOWED_CERTIFICATE_FINGERPRINT=all
- PROXY_PASS=https://mtls-bff.free.beeceptor.com/
volumes:
- ./certs:/etc/nginx/conf.d/certs
ports:
- 443:443Then try curl without a client certificate to see a Bad Request response:
curl -k https://localhostResponse:
<html>
<head><title>400 No required SSL certificate was sent</title></head>
<body>
<center><h1>400 Bad Request</h1></center>
<center>No required SSL certificate was sent</center>
<hr><center>nginx/1.18.0</center>
</body>
</html>
And then run a curl with a valid client certificate to see the https://mtls-bff.free.beeceptor.com result proxied through the sidecar mTLS:
curl --cacert example/sidecar/server-certs/server-ca.pem --key example/client/certs/client-key.pem --cert example/client/certs/client.pem -k https://localhostResponse:
[{"title":"Clean kitchen","description":"Don't forget the are under the sink!!"},{"title":"Call Eric","description":"Remind him to do his taxes"},{"title":"Water flowers","description":"Don't forget the ones in the garden!"}]The full pattern implemented here is the sidecar-proxy and ambassador-gateway. You can check here the ambassador-gateway part.
Open https://localhost/ on your browser and you will be warned about an insecure certificate. Accept the "risks" and then check that the server returns a 400 Bad Request to the browser. That's because you have not provided a client cetificate accepted by the server.
If using Firefox, import the client certificate examples/client/certs/client.cert.p12 on the Preferences page and reload the page. The browser will now ask you which certificate you want to use. Choose the imported certificate and voilà!
Check this example on how to secure a locally running API with this Sidecar
In the example folder you have some instructions on how to build this sidecar bundling your certificates. Basically, you will create a Dockerfile with the following contents:
FROM bancodobrasil/api-mtls-sidecar-proxy:0.1.0
COPY path/to/server.pem /etc/nginx/conf.d/certs/server.pem
COPY path/to/server-key.pem /etc/nginx/conf.d/certs/server-key.pem
COPY path/to/clients-ca.pem /etc/nginx/conf.d/certs/clients-ca.pemThis way you won't need to map any volume or define environment var. The container will be built specifically for one given client.
- https://jamielinux.com/docs/openssl-certificate-authority/create-the-root-pair.html: This guide demonstrates how to act as your own certificate authority (CA) using the OpenSSL command-line tools.