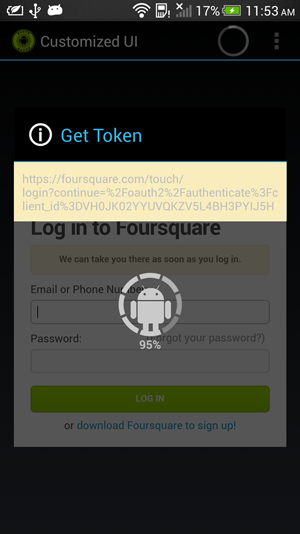
The android-oauth-client library helps you to easily add an OAuth flow to
your existing Android application. It automatically shows a customizable
Android dialog with WebView to guide the user to eventually grant you an
access token.
To help you manage access tokens, the library also includes an out-of-the-box credential store which stores tokens in SharedPreferences.
This client library is an Android extension to the Google OAuth Client Library for Java.
- Supports the following OAuth flows via the
google-oauth-java-clientlibrary:- OAuth 1.0a
- OAuth 2.0 Explicit Authorization (authorization code)
- OAuth 2.0 Implicit Authorization
- Automatically handles the OAuth flow in both
android.app.DialogFragmentandandroid.support.v4.app.DialogFragment. The dialog UI is fully customizable. - Provides an out-of-the-box credential store implementation via
SharedPreferences. - Provides sample applications that already work with popular social network services such as:
Note on OAuth flows: In general you should prefer OAuth 2.0 Implicit Authorization over OAuth 2.0 Explicit Authorization because implicit authorization does not require the client secret to be stored in the client.
Regardless of which OAuth flow you intend to incorporate into your Android
application, the android-oauth-client library can be used in 2 simple steps:
- Obtain an instance of
OAuthManagerby supplying the following 2 parameters:- An
AuthorizationFlowinstance which automatically handles the OAuth flow logic, - An
AuthorizationUIControllerwhich manages the UI.
- An
- Call one of the 3 possible
authorizemethods onOAuthManager. The call may be called from any thread either synchronously or asynchronously with anOAuthCallback<Credential>.OAuthManager.authorize10a()OAuthManager.authorizeExplicitly()OAuthManager.authorizeImplicitly()
We will go into more detail about each of the steps.
OAuthManager can be obtained by direct instantiation:
OAuthManager oauth = new OAuthManager(flow, controller);
To start the OAuth flow and obtain an access token, call one of the authorize()
methods according to the authorization flow of your choice.
You may invoke the authorize() method synchronously:
Credential credential = oauth.authorizeImplicitly("userId", null, null).getResult();
// continue to make API queries with credential.getAccessToken()
You may also invoke the authorize() method asynchronously with an OAuthCallback,
executed on a android.os.Handler of your choice.
OAuthCallback<Credential> callback = new OAuthCallback<Credential>() {
@Override public void run(OAuthFuture<Credential> future) {
Credential credential = future.getResult();
// make API queries with credential.getAccessToken()
}
};
oauth.authorizeImplicitly("userId", callback, handler);
Note that if a Handler is not supplied, the callback will be invoked on the
main thread.
Use the provided SharedPreferencesCredentialStore, which automatically
serializes access tokens to and from SharedPreferences in JSON format.
SharedPreferencesCredentialStore credentialStore =
new SharedPreferencesCredentialStore(context,
"preferenceFileName", new JacksonFactory());
An AuthorizationFlow instance may be obtained via its Builder:
AuthorizationFlow.Builder builder = new AuthorizationFlow.Builder(
BearerToken.authorizationHeaderAccessMethod(),
AndroidHttp.newCompatibleTransport(),
new JacksonFactory(),
new GenericUrl("https://socialservice.com/oauth2/access_token"),
new ClientParametersAuthentication("CLIENT_ID", "CLIENT_SECRET"),
"CLIENT_ID",
"https://socialservice.com/oauth2/authorize");
builder.setCredentialStore(credentialStore);
AuthorizationFlow flow = builder.build();
For OAuth 2.0 flows, you may wish to add OAuth scopes:
builder.setScopes(Arrays.asList("scope1", "scope2"));
For the OAuth 1.0a flow, you need to set the temporary token request URL:
builder.setTemporaryTokenRequestUrl("https://socialservice.com/oauth/requestToken");
Note that CLIENT_SECRET may be omitted and be replaced with a null value
for the OAuth 2.0 Implicit Authorization flow.
Also, CLIENT_ID and CLIENT_SECRET are called CONSUMER_KEY and CONSUMER_SECRET
in the OAuth 1.0a flow.
Use the provided DialogFragmentController, which automatically handles most
of the UI for you via an Android dialog. The DialogFragmentController has
two constructors, one taking android.app.FragmentManager and the other taking
android.support.v4.app.FragmentManager as the sole input parameter. Depending
on how you instantiate the controller, either android.app.DialogFragment or
android.support.v4.app.DialogFragment will be used.
AuthorizationUIController controller =
new DialogFragmentController(getFragmentManager()) {
@Override
public String getRedirectUri() throws IOException {
return "http://localhost/Callback";
}
@Override
public boolean isJavascriptEnabledForWebView() {
return true;
}
};
On Android it is typical to use Proguard to obfuscate and shrink code in order to reduce application size and improve security. If you are using Proguard, make sure you include the following configurations:
# Needed to keep generic types and @Key annotations accessed via reflection
-keepattributes Signature,RuntimeVisibleAnnotations,AnnotationDefault
-keepclasseswithmembers class * {
@com.google.api.client.util.Key <fields>;
}
-keepclasseswithmembers class * {
@com.google.api.client.util.Value <fields>;
}
-keepnames class com.google.api.client.http.HttpTransport
# Needed by google-http-client-android when linking against an older platform version
-dontwarn com.google.api.client.extensions.android.**
# Needed by google-api-client-android when linking against an older platform version
-dontwarn com.google.api.client.googleapis.extensions.android.**
# Do not obfuscate but allow shrinking of android-oauth-client
-keepnames class com.wuman.android.auth.** { *; }
A sample application is provided to showcase how you might use the library in a real-life Android application. In addition to default usage, the sample application also has examples for customizing the Dialog UI as well as OAuth integrations for popular social network services such as Flickr, LinkedIn, Twitter, etc.
You may also download/install the app from the Google Play Store.
Android OAuth Client is available for download from the Maven Central repository. You may also include it as a dependency by including the following coordinates:
<dependency>
<groupId>com.wu-man</groupId>
<artifactId>android-oauth-client</artifactId>
<version>0.0.3</version>
</dependency>or using Gradle
dependencies {
compile 'com.wu-man:android-oauth-client:0.0.3'
}Starting in v0.0.3, we release in the Android library AAR format as well.
The artifact coordinates are:
<dependency>
<groupId>com.wu-man</groupId>
<artifactId>android-oauth-client</artifactId>
<version>0.0.3</version>
<type>aar</type>
</dependency>You should use the included Graddle wrapper to build the project with the following command:
./gradlew clean build
The resulting jar file is located at library/build/libs/library.jar and the
aar file is located at library/build/libs/library.aar.
If you would like to contribute code to android-oauth-client you can do so through GitHub by forking the repository and sending a pull request.
In general if you are contributing we ask you to follow the AOSP coding style guidelines. If you are using an IDE such as Eclipse, it is easiest to use the AOSP style formatters.
You may file an issue if you find bugs or would like to add a new feature.
We do not have a mailing list. All questions should be asked and will be answered on StackOverflow using the android-oauth-client tag.
- David Wu - david@wu-man.com - http://blog.wu-man.com
Copyright 2013 David Wu
Copyright (C) 2010 Google Inc.
Licensed under the Apache License, Version 2.0 (the "License");
you may not use this file except in compliance with the License.
You may obtain a copy of the License at
http://www.apache.org/licenses/LICENSE-2.0
Unless required by applicable law or agreed to in writing, software
distributed under the License is distributed on an "AS IS" BASIS,
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
See the License for the specific language governing permissions and
limitations under the License.