Since Apple has released their AirTag product, I have noticed several instances of these cheap tracking devices used in nefarious purposes [1] [2].
In order to avoid false positives, currently iOS devices will check for nearby unknown AirTags when reaching a known location, such as the owner's hosue [Adam Catley]. To me, this seems too little too late.
The goal of the project is to detect nearby airtags in disconnected or lost modes.
If you find an unkown AirTag, please follow the instructions listed here: https://support.apple.com/en-us/HT212227
You can also remove the battery of the AirTag by following the steps listed here: https://support.apple.com/en-us/HT211670
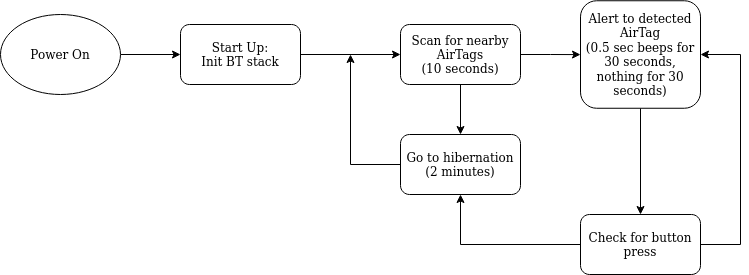
My initial thoughts for the flow of the program In order to keep the power requirements down, designed the program to search for nearby AirTags for 30 seconds every 2.5 minutes. After searching for AirTags the ESP will turn off the BLE radio and enter deep sleep.- Detect AirTags using GAP packets.
- Count the number of nearby AirTags.
- GPIO alerts. (For buzzer or LED.) (Testing required)
- [OBD2] Detect if the car is on -- power saving feature.
- Design development circuit board.
- Design application specific circuit boards.
See Adam Catley's comprenesive tear down and reverse engineer for more info on AirTags.
The AirTag has several states. The two that we are concerned about are Disconnected and Lost Mode. In these two states, the AirTag is boadcasting it's identity for nearby iOS devices to detect. The iOS device will then report the public key in the AirTag's broadcast to the FindMy network.
Luckily, we can also detect these broadcasts using any BLE device. In this specific case, I am using the ESP32.
The BLE Generic Access Profile (GAP) is used to provide information to BLE hosts on what the client device is.
| Byte # | Value | Description |
|---|---|---|
| 0 | 0x1E | Advertising data length: 31 (the maximum allowed) |
| 1 | 0xFF | Advertising data type: Manufacturer Specific Data |
| 2-3 | 0x004C | Apple's company identifier (Actuall order in packet is 4C 00) |
| 4 | 0x12 | Apple's payload type to indicate a FIndMy Network broadcast |
| 5 | 0x19 | Apple payload length (31 - 6 = 25 = 0x19) |
| 6 | 0x10 | Status byte |
| 7-31 | Varies | Contains the public key used to identify the AirTag's owner within the FindMy Network. Changes daily. |
Since the portion of the packet that contains the identification data is encrypted and changes on a daily basis, we won't be able to track specific AirTags. That is out of the scope of this project.
The only information we need to detect if there is an AirTag is the information in the packet header (Bytes 0-6).
Once the basic functionality is implemented software, I plan to move on to creating several circuit boards that allow for integration into a vehicle:
- OBD II port
- 12V Aux power
- USB powered
- Maybe a keychain type device
It'd be interesting to see if someone could modify the firmware of an AirTag to be able to alert to other nearby AirTags in Disconnected or Lost mode.