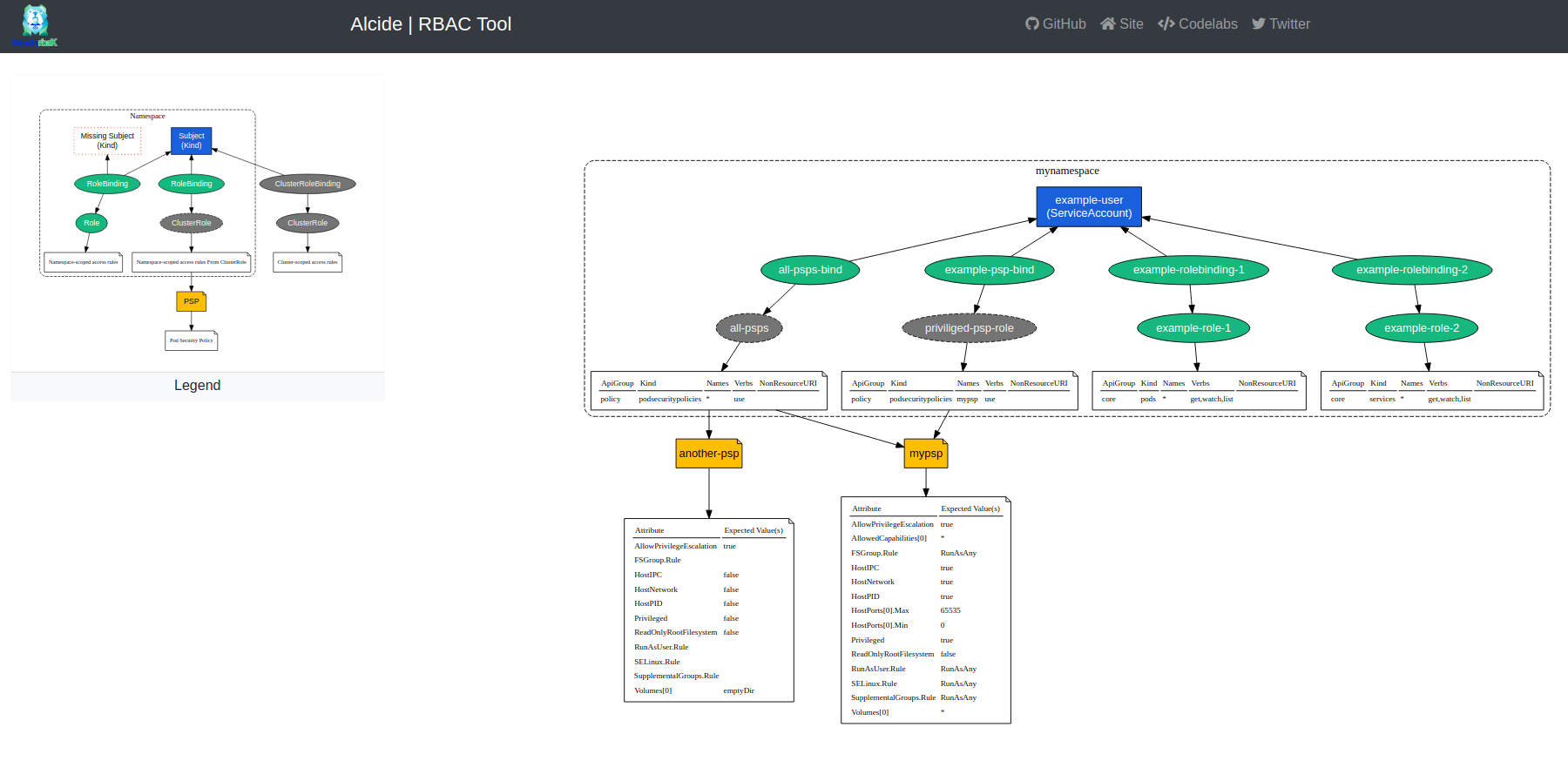
Role-based access control (RBAC) is a method of regulating access to computer or network resources based on the roles of individual users within your organization.
RBAC authorization uses the rbac.authorization.k8s.io API group to drive authorization decisions, allowing you to dynamically configure policies through the Kubernetes API.
Permissions are purely additive (there are no “deny” rules).
A Role always sets permissions within a particular namespace ; when you create a Role, you have to specify the namespace it belongs in. ClusterRole, by contrast, is a non-namespaced resource. ClusterRoles have several uses. You can use a ClusterRole to:
- define permissions on namespaced resources and be granted within individual namespace(s)
- define permissions on namespaced resources and be granted across all namespaces
- define permissions on cluster-scoped resources
If you want to define a role within a namespace, use a Role; if you want to define a role cluster-wide, use a ClusterRole.
rbac-tool simplifies querying and creation RBAC policies.
Download the latest from the release page
curl https://raw.githubusercontent.com/alcideio/rbac-tool/master/download.sh | bashA collection of Kubernetes RBAC tools to sugar coat Kubernetes RBAC complexity
rbac-tool
Usage:
rbac-tool [command]
Available Commands:
auditgen Generate RBAC policy from Kubernetes audit events
bash-completion Generate bash completion. source < (rbac-too bash-completion)
generate Generate Role or ClusterRole and reduce the use of wildcards
help Help about any command
lookup RBAC Lookup by subject (user/group/serviceaccount) name
policy-rules RBAC List Policy Rules For subject (user/group/serviceaccount) name
version Print rbac-tool version
visualize A RBAC visualizer
who-can Shows which subjects have RBAC permissions to perform an action
Flags:
-h, --help help for rbac-tool
-v, --v Level number for the log level verbosity
Use "rbac-tool [command] --help" for more information about a command.- The
rbac-tool vizcommand - The
rbac-tool lookupcommand - The
rbac-tool who-cancommand - The
rbac-tool policy-rulescommand - The
rbac-tool auditgencommand - The
rbac-tool gencommand - Command Line Reference
- Contributing
A Kubernetes RBAC visualizer that generate a graph as dot file format or in HTML format.
By default 'rbac-tool viz' will connect to the local cluster (pointed by kubeconfig) Create a RBAC graph of the actively running workload on all namespaces except kube-system
See run options on how to render specific namespaces, other clusters, etc.
#Render Locally
rbac-tool viz --outformat dot && cat rbac.dot | dot -Tpng > rbac.png && open rbac.png
# Render Online
https://dreampuf.github.io/GraphvizOnlineExamples:
# Scan the cluster pointed by the kubeconfig context 'myctx'
rbac-tool viz --cluster-context myctx# Scan and create a PNG image from the graph
rbac-tool viz --outformat dot --exclude-namespaces=soemns && cat rbac.dot | dot -Tpng > rbac.png && google-chrome rbac.pngLookup of the Roles/ClusterRoles used attached to User/ServiceAccount/Group with or without regex
Examples:
# Search All Service Accounts
rbac-tool lookup -e '.*'# Search All Service Accounts That Contains myname
rbac-tool lookup -e '.*myname.*'rbac-tool lookup -e '^system:'
SUBJECT | SUBJECT TYPE | SCOPE | NAMESPACE | ROLE
+-------------------------------------------------+--------------+-------------+-------------+----------------------------------------------------------------------+
system:anonymous | User | Role | kube-public | kubeadm:bootstrap-signer-clusterinfo
system:authenticated | Group | ClusterRole | | system:discovery
system:authenticated | Group | ClusterRole | | system:public-info-viewer
system:authenticated | Group | ClusterRole | | system:basic-user
system:bootstrappers:kubeadm:default-node-token | Group | ClusterRole | | system:certificates.k8s.io:certificatesigningrequests:nodeclient
system:bootstrappers:kubeadm:default-node-token | Group | ClusterRole | | system:node-bootstrapper
system:bootstrappers:kubeadm:default-node-token | Group | Role | kube-system | kubeadm:nodes-kubeadm-config
system:bootstrappers:kubeadm:default-node-token | Group | Role | kube-system | kubeadm:kubelet-config-1.16
system:bootstrappers:kubeadm:default-node-token | Group | Role | kube-system | kube-proxy
system:kube-controller-manager | User | ClusterRole | | system:kube-controller-manager
...Shows which subjects have RBAC permissions to perform an action denoted by VERB on an object denoted as ( KIND | KIND/NAME | NON-RESOURCE-URL)
- VERB is a logical Kubernetes API verb like 'get', 'list', 'watch', 'delete', etc.
- KIND is a Kubernetes resource kind. Shortcuts and API groups will be resolved, e.g. 'po' or 'deploy'.
- NAME is the name of a particular Kubernetes resource.
- NON-RESOURCE-URL is a partial URL that starts with "/".
Examples:
# Who can read ConfigMap resources
rbac-tool who-can get cm
# Who can watch Deployments
rbac-tool who-can watch deployments.apps
# Who can read the Kubernetes API endpoint /apis
rbac-tool who-can get /apis
# Who can read a secret resource by the name some-secret
rbac-tool who-can get secret/some-secretList Kubernetes RBAC policy rules for a given User/ServiceAccount/Group with or without regex
Examples:
# List policy rules for system unauthenicated group
rbac-tool policy-rules -e '^system:unauth'Output:
TYPE | SUBJECT | VERBS | NAMESPACE | API GROUP | KIND | NAMES | NONRESOURCEURI
+-------+------------------------+-------+-----------+-----------+------+-------+--------------------------------------------+
Group | system:unauthenticated | get | * | - | - | - | /healthz,/livez,/readyz,/version,/version/
Leveraging JMESPath to filter and transform RBAC Policy rules.
For example: Who Can Read Secrets
rbac-tool policy-rules -o json | jp "[? @.allowedTo[? (verb=='get' || verb=='*') && (apiGroup=='core' || apiGroup=='*') && (resource=='secrets' || resource == '*') ]].{name: name, namespace: namespace, kind: kind}"
Generate RBAC policy from Kubernetes audit events. Audit source format can be:
- Kubernetes List Object that contains Audit Events
- Newline seperated Audit Event objects Audit source can be file, directory or http URL.
rbac-tool auditgen -f audit.logThis command is based on this prior work.
Examples would be simplest way to describe how rbac-tool gen can help:
- Generate a
ClusterRolepolicy that allows to read everything except secrets and services - Generate a
Rolepolicy that allows create,update,get,list (read/write) everything except secrets, services, ingresses, networkpolicies - Generate a
Rolepolicy that allows create,update,get,list (read/write) everything except statefulsets
rbac-tool generate RBAC Role or RBAC ClusterRole resource while reducing the use of wildcards, and support deny semantics for specific Kubernetes clusters.
rbac-tool reads from the Kubernetes discovery API the available API Groups and resources, which represents the "world" of resources.
Based on the command line options, generate an explicit Role/ClusterRole that avoid wildcards by expanding wildcards to the available "world" resources.
Examples generated against Kubernetes cluster v1.16 deployed using KIND.
Generate a
ClusterRolepolicy that allows to read everything except secrets and services
rbac-tool gen --deny-resources=secrets.,services. --allowed-verbs=get,listGenerate a
Rolepolicy that allows create,update,get,list (read/write) everything except secrets, services, networkpolicies in core,apps & networking.k8s.io API groups
rbac-tool gen --generated-type=Role --deny-resources=secrets.,services.,networkpolicies.networking.k8s.io --allowed-verbs=* --allowed-groups=,extensions,apps,networking.k8s.ioGenerate a
Rolepolicy that allows create,update,get,list (read/write) everything except statefulsets
rbac-tool gen --generated-type=Role --deny-resources=apps.statefulsets --allowed-verbs=* Generate a
Rolepolicy that allows create,update,get,list (read/write) everything except secrets, services, networkpolicies in core,apps & networking.k8s.io API groups
rbac-tool gen --generated-type=Role --deny-resources=secrets.,services.,networkpolicies.networking.k8s.io --allowed-verbs=* --allowed-groups=,extensions,apps,networking.k8s.ioapiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
creationTimestamp: null
name: custom-role
namespace: mynamespace
rules:
- apiGroups:
- ""
resources:
- events
- componentstatuses
- podtemplates
- namespaces
- replicationcontrollers
- persistentvolumes
- configmaps
- persistentvolumeclaims
- resourcequotas
- limitranges
- nodes
- bindings
- serviceaccounts
- pods
- endpoints
verbs:
- '*'
- apiGroups:
- extensions
resources:
- ingresses
verbs:
- '*'
- apiGroups:
- apps
resources:
- replicasets
- daemonsets
- deployments
- controllerrevisions
- statefulsets
verbs:
- '*'
- apiGroups:
- networking.k8s.io
resources:
- ingresses
verbs:
- '*'Generate Role or ClusterRole resource while reducing the use of wildcards.
rbac-tool read from the Kubernetes discovery API the available API Groups and resources,
and based on the command line options, generate an explicit Role/ClusterRole that avoid wildcards
Examples:
# Generate a Role with read-only (get,list) excluding secrets (core group) and ingresses (extensions group)
rbac-tool gen --generated-type=Role --deny-resources=secrets.,ingresses.extensions --allowed-verbs=get,list
# Generate a Role with read-only (get,list) excluding secrets (core group) from core group, admissionregistration.k8s.io,storage.k8s.io,networking.k8s.io
rbac-tool gen --generated-type=ClusterRole --deny-resources=secrets., --allowed-verbs=get,list --allowed-groups=,admissionregistration.k8s.io,storage.k8s.io,networking.k8s.io
Usage:
rbac-tool generate [flags]
Aliases:
generate, gen
Flags:
--allowed-groups strings Comma separated list of API groups we would like to allow '*' (default [*])
--allowed-verbs strings Comma separated list of verbs to include. To include all use '* (default [*])
-c, --cluster-context string Cluster.use 'kubectl config get-contexts' to list available contexts
--deny-resources strings Comma separated list of resource.group
-t, --generated-type string Role or ClusteRole (default "ClusterRole")
-h, --help help for generateIf you think you have found a bug please follow the instructions below.
- Please spend a small amount of time giving due diligence to the issue tracker. Your issue might be a duplicate.
- Open a new issue if a duplicate doesn't already exist.
If you have an idea to enhance rbac-tool follow the steps below.
- Open a new issue.
- Remember users might be searching for your issue in the future, so please give it a meaningful title to helps others.
- Clearly define the use case, using concrete examples.
- Feel free to include any technical design for your feature.
- Your PR is more likely to be accepted if it focuses on just one change.
- Please include a comment with the results before and after your change.
- Your PR is more likely to be accepted if it includes tests.
- You're welcome to submit a draft PR if you would like early feedback on an idea or an approach.