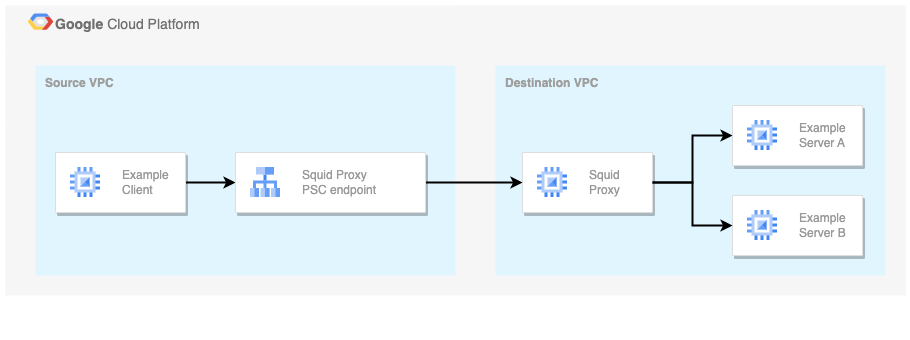
There are tons of ways to connect VPCs in Google Cloud. This example uses Private Service Connect and a Squid Proxy VM to allow Source VPC Clients to access resources in the Destination VPC.
Read the associated blog post: How To Use Squid Proxy To Access Services In Another VPC Using Private Service Connect.
Use Terraform to deploy the example setup.
-
Set the required Terraform variables
-
Deploy the example infrastructure
cd terraform terraform init terraform apply -
Try it for yourself
Log in to the client VM:
gcloud compute ssh client --tunnel-through-iap --project <project_id>
Invoke a service in the destination VPC:
curl -x http://proxy.xebia:3128 http://example-server.xebia/
Invoke an internet url via the proxy:
curl -x http://proxy.xebia:3128 https://www.google.com/
Use Terraform to destroy the example setup.
-
Set the required Terraform variables
-
Destroy the example infrastructure
cd terraform terraform init terraform destroy