Super simple passwordscanner built using PowerShell.
Scan your code, files, folders, and repos for accidentily exposed secrets using PowerShell.
-
Give a list of files to scan and we will check for any pattern matches in those files.
-
Outputs the result and metadata. (Use Get-Member to get all scan data)
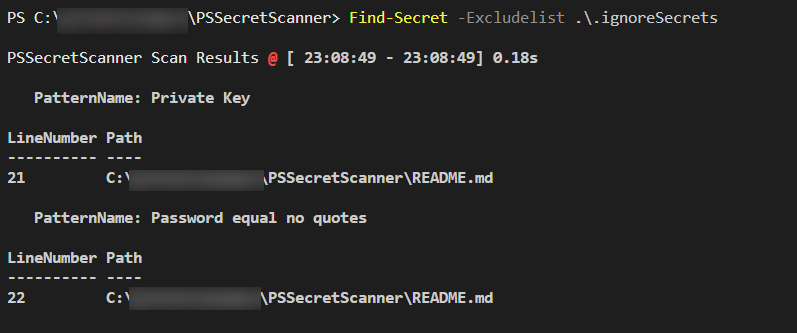
- Use an excludelist to prevent false positives, or if you really want to include secrets in your code, by creating a exclude file and passing it to the
-Excludelistparameter. Either be specific and include File, LineNumber, Pattern, or use wildcards to exclude entire files or folders.
# Comments supported
# Relative paths supported (starting with .\)
.\Docs\Help\Find-Secret.md
.\Source\config.json
# Wildcards supported. All files within this and subfolders will be excluded.
.\bin\*
# Paths to files. All matches in these files will be excluded
.\Tests\RegexPatternTests\TestCases.json
C:\MyRepo\PSSecretScanner\README.md
# Patterns on specific lines supported in the format
# <path\to\file>;<line number>;<pattern>
.\ExcludeList.csv;1;"C:\BicepLab\template.json;51;-----BEGIN RSA PRIVATE KEY-----"
C:\MyRepo\PSSecretScanner\Docs\Help\Find-Secret.md;51;"C:\MyFiles\template.json;51;-----BEGIN RSA PRIVATE KEY-----"
To have Write-SecretStatus automatically pick up and use your ignore list for all your repo, name your excludelist .ignoresecrets and put it in your repo root folder!
-
From the PSGallery, run
Install-Module PSSecretScanner -
Clone this repo, and run
Invoke-Buildto build the module localy.
I couldn't find a proper secret scanner for PowerShell so I wrote my own.
From the beginning it was just a list of regex patterns stolen from the OWASP SEDATED security scanner repo that I ran through Select-String, as I thought the OWASP tools was way to advanced for my needs, and way to hard to wrap in a powershell script.
From there it kind of grew, and hopefully it will grow even more.
- The baseline is the list found at the OWASP repo, but converted to PowerShell Regex standard (PCRE I think it's called..)
- Added
_Azure_AccountKeypattern found at Detect-secrets from YELP - Added patterns from h33tlit (thank you Simon Wåhlin for telling me)
The added underscore _ to names in the pattern list is simply to make them easier to work with in PowerShell.
Yes, even keeping it simple there are stuff I might want to add some day, or if you want to, feel free to create a PR.
- Parallelization - make it faster on huge repos.
- More filetypes! I kind of just winged it for now.