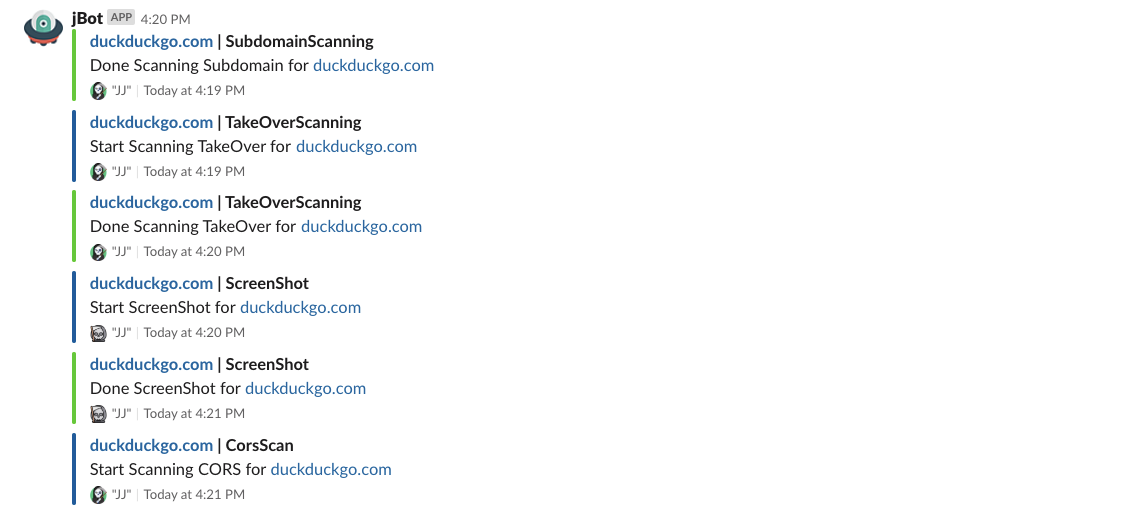
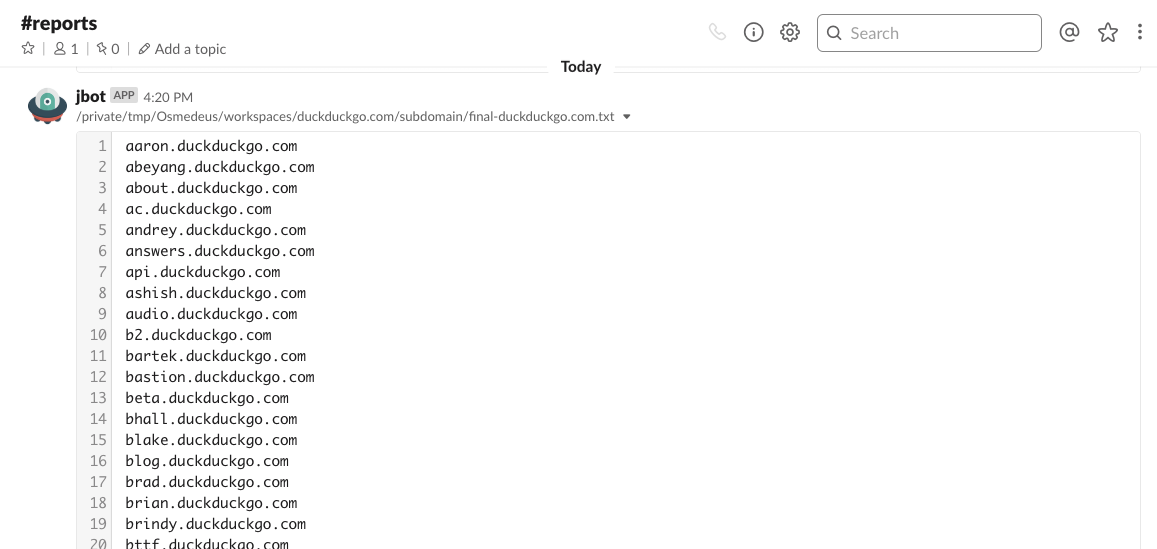
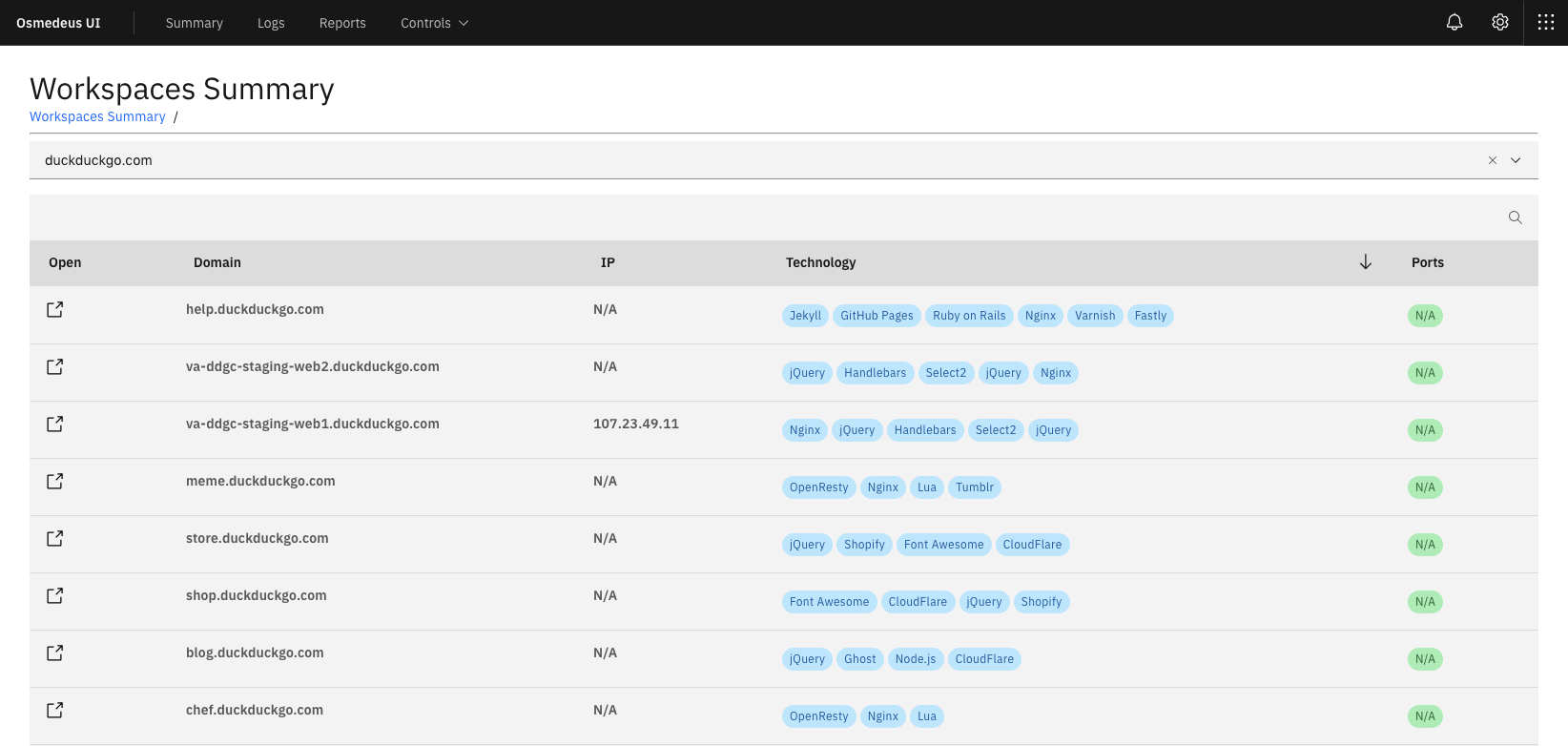
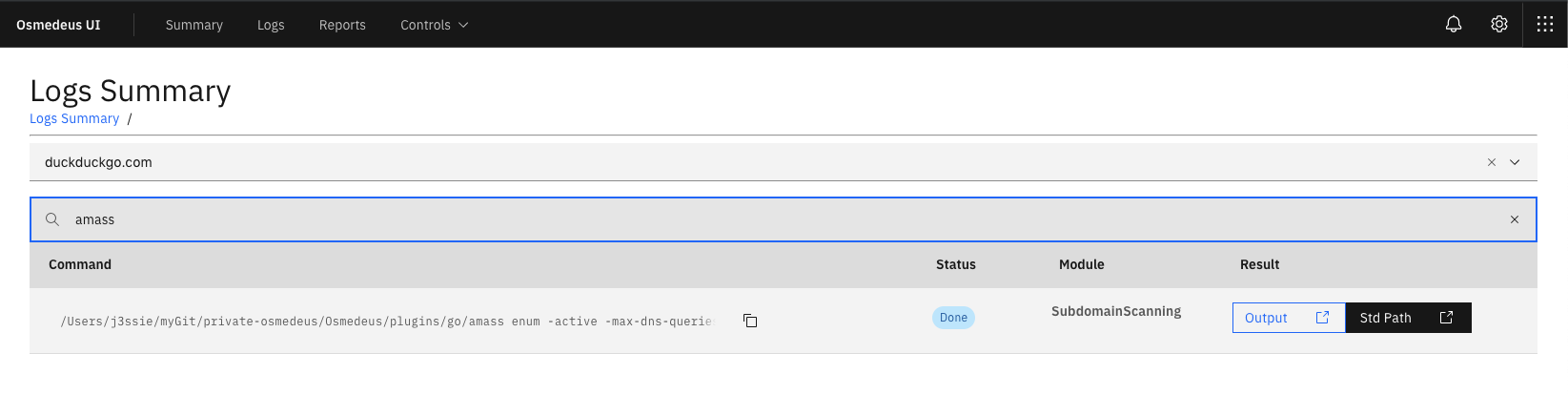
What is Osmedeus?
Osmedeus allows you automated run the collection of awesome tools to reconnaissance and vulnerability scanning against the target.
How to use
If you have no idea what are you doing just type the command below or check out the Advanced Usage
./osmedeus.py -t example.com
Installation
git clone https://github.com/j3ssie/Osmedeus
cd Osmedeus
./install.sh
This install only focus on Kali linux, check more install on Wiki page
Using Docker
Check out docker-osmedeus by mabnavarrete for docker installation and this wiki for more detail.
Features
- Subdomain Scan.
- Subdomain TakeOver Scan.
- Screenshot the target.
- Basic recon like Whois, Dig info.
- Web Technology detection.
- IP Discovery.
- CORS Scan.
- SSL Scan.
- Headers Scan.
- Port Scan.
- Vulnerable Scan.
- Seperate workspaces to store all scan output and details logging.
- REST API.
- React Web UI.
- Support Continuous Scan.
- Slack notifications.
More options
Basic Usage
===========
python3 osmedeus.py -t <your_target>
python3 osmedeus.py -T <list_of_targets>
Advanced Usage
==============
[*] List all module
python3 osmedeus.py -M
[*] Running with specific module
python3 osmedeus.py -t <result_folder> -m <module_name> -i <your_target>
python3 osmedeus.py [-t <result_folder>] -m <module_name> -I <tagets_list_file>
[*] Example command
python3 osmedeus.py -m portscan -i "1.2.3.4/24"
python3 osmedeus.py -t sample2 -m vuln -i "1.2.3.4/24"
python3 osmedeus.py -t sample2 -m dirb -I /tmp/list_of_hosts.txt
Remote Options
==============
--remote REMOTE Remote address for API, (default: https://127.0.0.1:5000)
--auth AUTH Specify auth tication e.g: --auth="username:password"
See your config file for more detail (default: core/config.conf)
--client just run client stuff in case you ran the flask server before
More options
==============
--update Update lastest from git
-c CONFIG, --config CONFIG
Specify config file (default: core/config.conf)
-w WORKSPACE, --workspace WORKSPACE
Custom workspace folder
-f, --force force to run the module again if output exists
-v, --verbose show verbose output
-q, --quick run this tool with quick routine
-s, --slow run this tool with slow routine
--debug Just for debug purpose
Demo
Disclaimer
Most of this tool done by the authors of the tool that list in CREDITS.md. I'm just put all the pieces together, plus some extra magic.
This tool is for educational purposes only. You are responsible for your own actions. If you mess something up or break any laws while using this software, it's your fault, and your fault only.
Contribute
Please take a look at CONTRIBUTING.md
Changelog
Please take a look at CHANGELOG.md
CREDITS
Please take a look at CREDITS.md