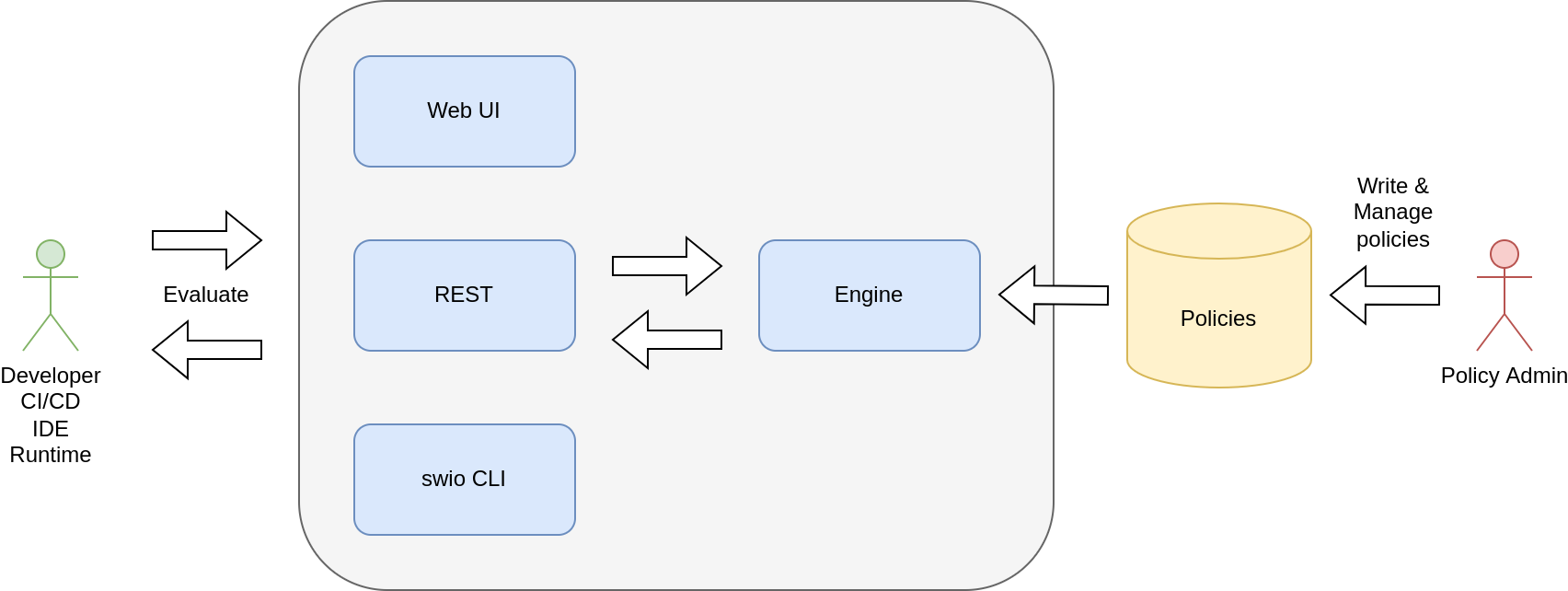
A functional type system for implementing policy inspection, audit and enforcement.
Seedwing Policy consists of components that may be combined or used standalone as part of a secure software supply chain:
- Dogma - a policy description language.
- Engine - a policy evaluation engine.
With Seedwing Policy, you can:
- Validate, destructure and inspect payload according to standards like CycloneDX, SPDX, OpenVEX, PEM and more.
- Check for permitted licenses according to organization policy.
- Check for trusted signatures against Sigstore.
- Check SBOM dependencies for vulnerabilities against OSV.
Additionally, Seedwing provides detailed explanations of the decision process.
The Seedwing engine includes core patterns to assist in policy authoring.
Some examples include:
- Sigstore
- x509
- CycloneDX
- OpenVEX
- SPDX
- Maven
- Base64
All the policies can be centrally managed in a server, or built in as part of a custom application.
Seedwing Policy is primarily concerned with software supply chain, but may be used in other contexts as well such as authorization policies for Apache Kafka.
See the documentation for more information.
To use the policy engine, download the latest released swio binary for your platform, or use one of container images.
You can also try a hosted version at https://playground.seedwing.io.
To evaluate policies:
swio eval -p <policy dir> -n mypolicy::pattern -i input.jsonTo run the HTTP server (point your browser to the http://localhost:8080 to view the console):
swio serve -p <policy dir>To benchmark policies:
swio bench -p <policy dir> -n mypolicy::pattern -i input.json -c 1000Seedwing Policy is guaranteed to compile on the latest stable Rust version at the time of release. It might compile with older versions.
See CONTRIBUTING.md
The release process is documented in RELEASE.md.
Apache License, Version 2.0 (LICENSE)